
Designing Scalable Cloud Applications: A Comprehensive Guide
This comprehensive guide delves into the critical aspects of designing scalable cloud applications, covering architectural patterns, platform selectio...
175 posts in this category

This comprehensive guide delves into the critical aspects of designing scalable cloud applications, covering architectural patterns, platform selectio...

Navigating the complexities of cloud compliance is critical for modern businesses. This guide provides a comprehensive overview of designing a robust...
Cloud architecture design, while offering great potential, is riddled with potential pitfalls that can undermine your cloud strategy. This article ide...

This article delves into the "Leaky Abstraction" anti-pattern in software development, exploring its definition, characteristics, and common manifesta...
Reference architectures serve as vital blueprints for complex system design and implementation. This article outlines the essential components of a ro...

APIs are fundamentally reshaping modern architecture by enabling seamless communication and data exchange between different software applications. Thi...

To thrive in today's dynamic digital environment, your cloud architecture needs to be ready for the future. This guide offers a comprehensive strategy...
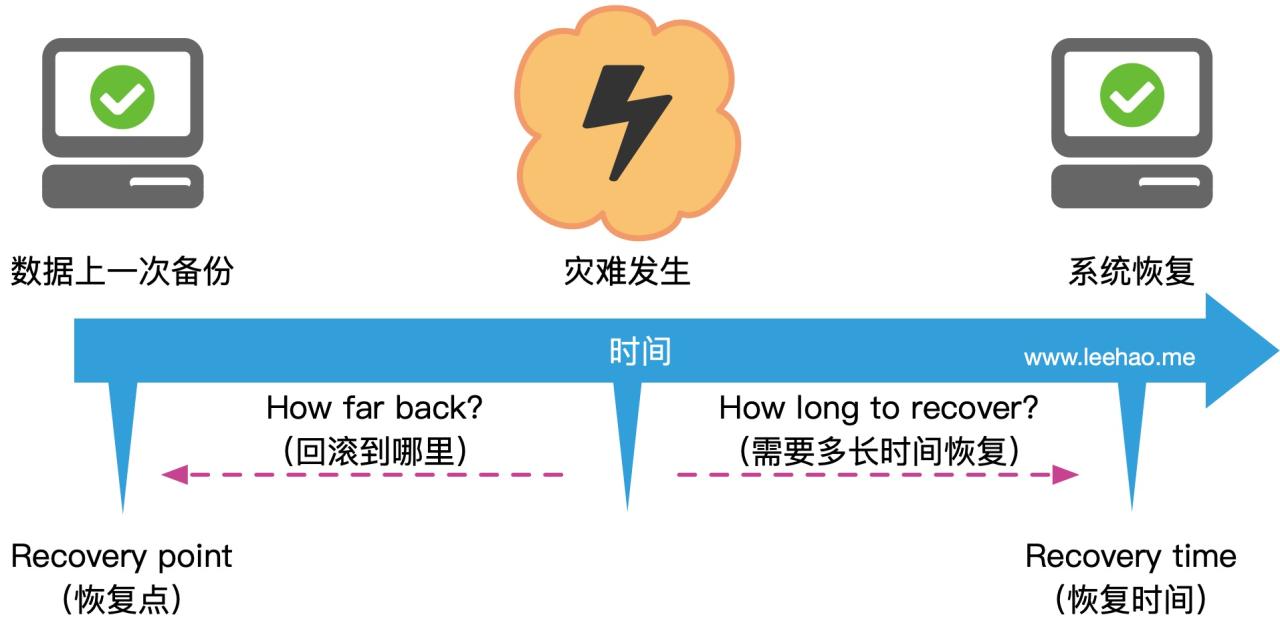
This article delves into the critical differences between Recovery Point Objective (RPO) and Recovery Time Objective (RTO), essential metrics for effe...

Building a real-time data processing architecture is essential for applications requiring immediate insights. This guide explores the critical aspects...

This article provides a comprehensive roadmap for enterprises seeking to develop a successful cloud strategy. It covers essential steps like infrastru...

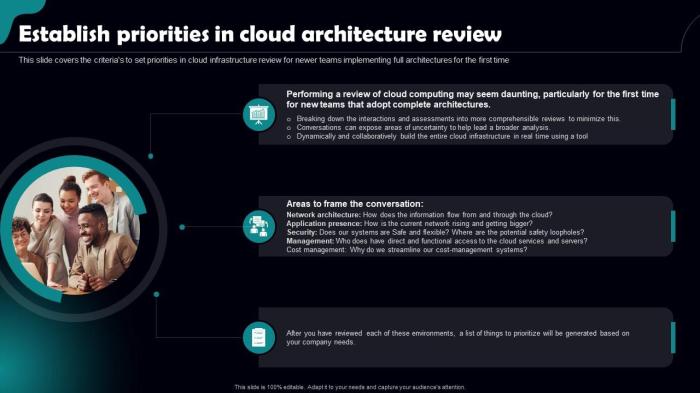
Cloud architecture reviews are essential for achieving peak performance, security, and cost efficiency within your cloud environment. This comprehensi...
This article explores the critical challenges inherent in microservices architectures, such as network latency, security vulnerabilities, and complex...