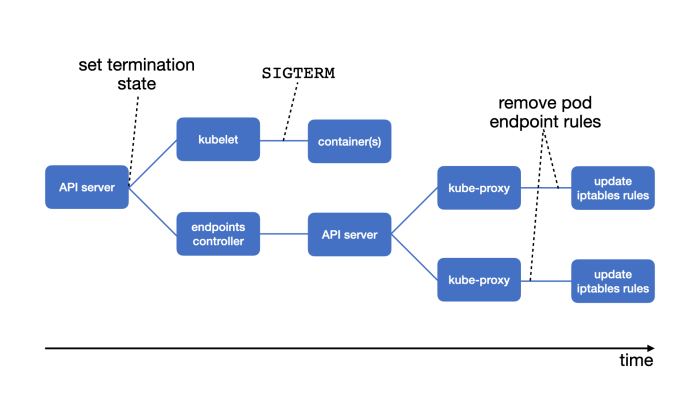
Kubernetes Network Policies: Securing Your Clusters with Fine-Grained Control
Kubernetes Network Policies act as cloud-native firewalls, providing essential security for containerized applications within your clusters. This arti...
167 posts in this category

Kubernetes Network Policies act as cloud-native firewalls, providing essential security for containerized applications within your clusters. This arti...
Cloud-native development offers significant advantages for businesses seeking agility, delivering faster deployment cycles, enhanced scalability, and...

Building an Internal Developer Platform (IDP) can significantly streamline your software development lifecycle and empower your teams. This comprehens...
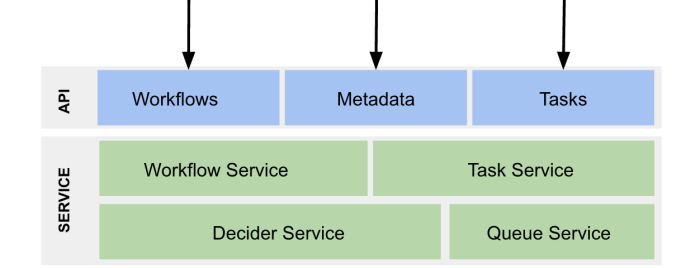
Navigating the complexities of microservices is crucial for building robust and scalable applications. This article provides a comprehensive guide, co...

This comprehensive guide dives deep into the art of crafting efficient and secure Dockerfiles, covering crucial aspects from base image selection and...

Understanding "lead time for changes" is fundamental to efficient software development. This critical metric tracks the entire lifecycle of a change,...
This article delves into the often-overlooked cost of context switching for software developers, exploring its definition, various types, and the fact...
This comprehensive article meticulously examines the crucial differences between unit testing and integration testing, offering a clear understanding...
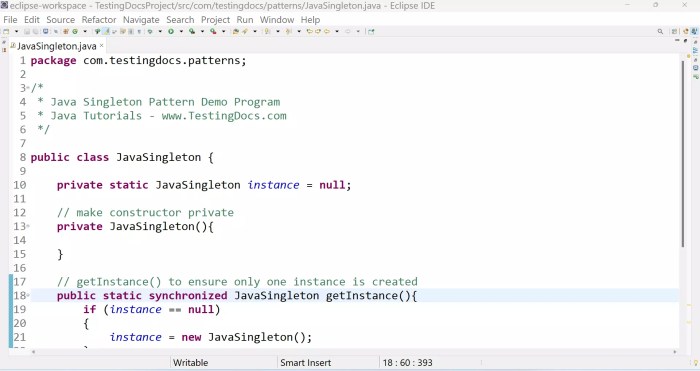
The Singleton pattern provides a method for controlling object instantiation, ensuring only one instance of a class exists with global access. While t...

This comprehensive guide, "What Is A Cloud Native Application Explained," provides a deep dive into the world of cloud native development, outlining i...
This comprehensive guide offers a deep dive into containerizing Python web applications, exploring the benefits and core concepts of containerization....

Effectively managing database migrations within a CI/CD pipeline is crucial for efficient and reliable software deployments. This article provides a c...