
SOC 2 Compliance in the Cloud: A Comprehensive Guide
Navigating SOC 2 compliance in a cloud environment requires a strategic approach, and this article provides a comprehensive guide. It covers essential...
152 posts in this category

Navigating SOC 2 compliance in a cloud environment requires a strategic approach, and this article provides a comprehensive guide. It covers essential...

In today's complex regulatory environment, establishing a robust data retention policy is crucial for compliance and minimizing potential risks. This...

This article provides a comprehensive overview of Static Application Security Testing (SAST), exploring its core principles, role within the Software...

In today's digital world, the Chief Information Security Officer (CISO) is a vital strategic leader, tasked with protecting an organization's data and...
Protecting your organization from internal cybersecurity risks is paramount. This guide, "How to Detect and Respond to Insider Threats," offers a comp...
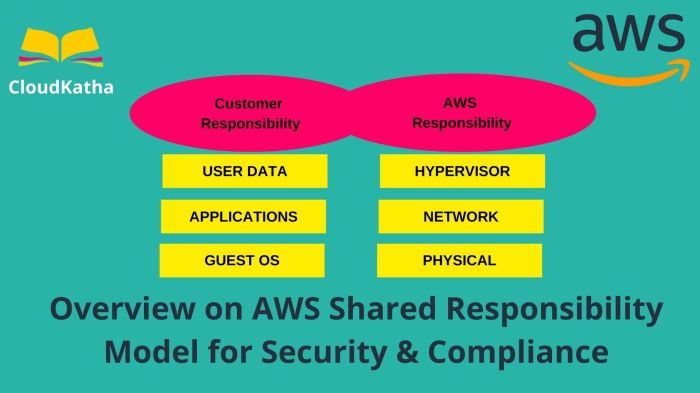
The shared responsibility model is a critical framework in cloud security, outlining the security obligations of both the cloud provider and the custo...
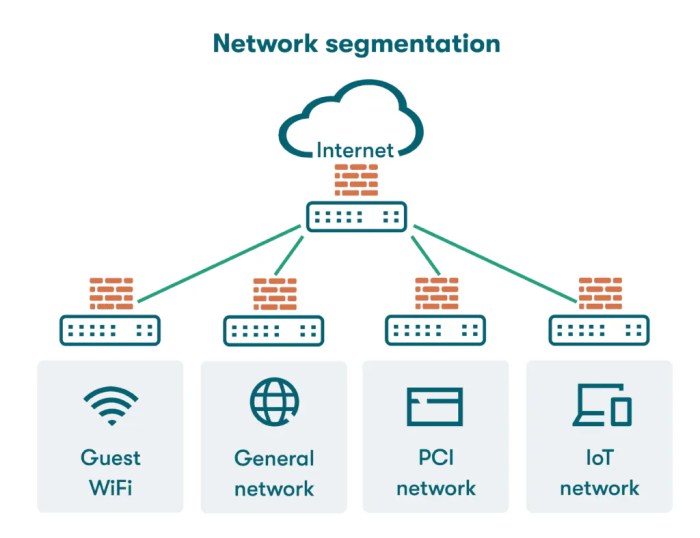
This comprehensive guide provides a deep dive into network segmentation, a crucial strategy for bolstering your organization's security posture. From...

This article delves into the critical process of de-provisioning user accounts, explaining its definition, triggers, and the vital role it plays in bo...
In today's cloud-centric world, understanding Data Loss Prevention (DLP) solutions is critical for safeguarding sensitive information. This article pr...

This comprehensive guide explores the critical concepts of data anonymization and pseudonymization, essential practices for protecting sensitive infor...

Handling Data Subject Access Requests (DSARs) is a critical component of GDPR compliance. This comprehensive guide offers a clear and detailed roadmap...
Protecting sensitive API keys and tokens is crucial for maintaining application security and preventing costly data breaches. This article provides a...