
FedRAMP Authorization: A Guide to Cloud Security for Government
This comprehensive guide provides a detailed overview of FedRAMP, the critical security authorization program for cloud services used by the U.S. gove...
152 posts in this category

This comprehensive guide provides a detailed overview of FedRAMP, the critical security authorization program for cloud services used by the U.S. gove...

This article comprehensively explores the "Right to Be Forgotten," a critical aspect of data privacy laws, detailing its origins, legal frameworks, an...
Want to strengthen your organization's digital defenses? This guide offers a comprehensive approach to conducting a security architecture review, prov...
Managing security across a multi-cloud environment requires a strategic approach to avoid fragmentation and ensure consistent protection. This guide o...

This article delves into the OWASP Top 10, the definitive guide to web application security risks. It provides a comprehensive overview of the most c...
This article offers a comprehensive guide to negotiating robust security provisions within your cloud service level agreement (SLA). It covers critica...
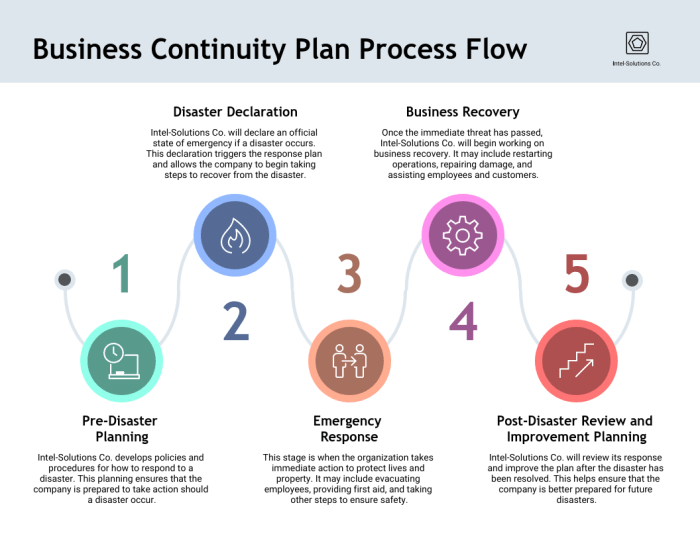
This comprehensive guide explores the essential integration of Business Continuity Planning (BCP) and Disaster Recovery (DR), providing a roadmap to e...
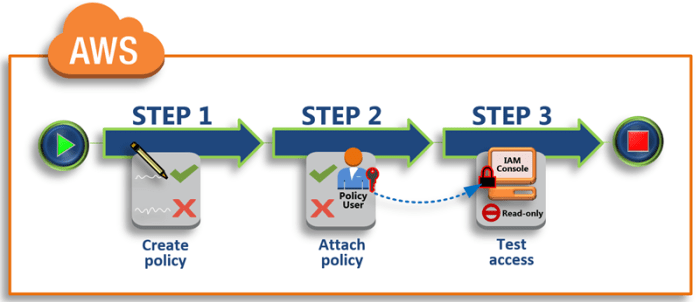
This comprehensive guide delves into the world of Identity and Access Management (IAM) policies, explaining their crucial role in securing access to y...

This article provides a comprehensive overview of the roles and responsibilities within a Security Operations Center (SOC), crucial for modern cyberse...
User Lifecycle Management (ULM) and provisioning are crucial for security, operational efficiency, and compliance within any organization. This guide...

This article delves into the critical practice of Continuous Compliance Monitoring (CCM) in cloud environments, explaining its core concepts and showc...

The cloud offers significant advantages, but it also presents new vulnerabilities to malware and ransomware attacks. This article outlines essential s...