Preparing for a Cloud Security Audit: A Comprehensive Guide
Navigating a cloud security audit can seem daunting, but this comprehensive guide provides a clear roadmap for preparation and success. The article me...
152 posts in this category

Navigating a cloud security audit can seem daunting, but this comprehensive guide provides a clear roadmap for preparation and success. The article me...

This comprehensive guide details the essential skills required to excel as a Cloud Security Engineer, covering core technical competencies like networ...

Effectively securing your cloud infrastructure requires a deep understanding of both Security Groups and Network ACLs. This comprehensive guide delves...

A Business Continuity Plan (BCP) is essential for any organization seeking to minimize disruption and maintain operational resilience in the face of u...
Protecting sensitive information is paramount in today's data-driven world, and this comprehensive guide provides a deep dive into implementing effect...
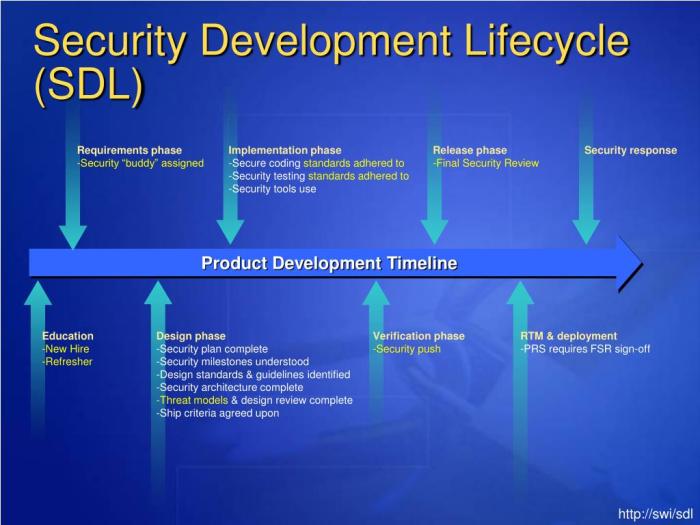
"Shifting security left" is a critical strategy for modern software development, emphasizing the integration of security practices early in the develo...
Managing resources across multiple cloud providers like AWS, Azure, and GCP introduces complex challenges for consistent security and access control d...
Configuration drift in security settings poses a significant threat, potentially weakening your defenses through unnoticed changes. Proactively monito...
This comprehensive article delves into the critical role of tokenization in modern data security, exploring its core concepts, operational mechanisms,...
In an era defined by digital interconnectedness, cyber insurance has become a critical safeguard for businesses facing persistent online threats. This...

This guide provides a comprehensive roadmap for establishing robust threat hunting capabilities, essential for proactively identifying and mitigating...

Enhance your cybersecurity strategy by learning how to set up a honeypot, a valuable tool designed to attract and analyze potential attackers. This gu...