
Staying Ahead: Your Guide to Current Security Threats and Vulnerabilities
The digital world is constantly evolving, and staying informed about the latest security threats and vulnerabilities is crucial for both individuals a...
152 posts in this category

The digital world is constantly evolving, and staying informed about the latest security threats and vulnerabilities is crucial for both individuals a...

Discover how Open Policy Agent (OPA) is transforming policy enforcement in modern software development. This guide explores OPA's capabilities in mana...

Discover insights and practical tips in this comprehensive guide about What Are The Compliance Requirements For Data Breach Notifications.
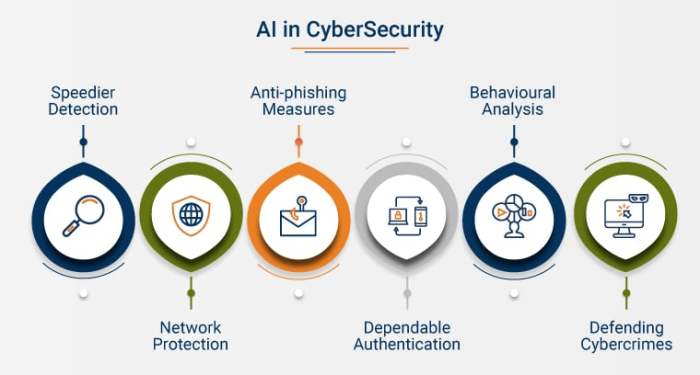
This article explores the vital integration of threat intelligence into cloud security operations, a crucial step in defending against modern cyber th...

In today's evolving digital landscape, cloud security certifications are crucial for professionals seeking to validate their expertise and advance the...
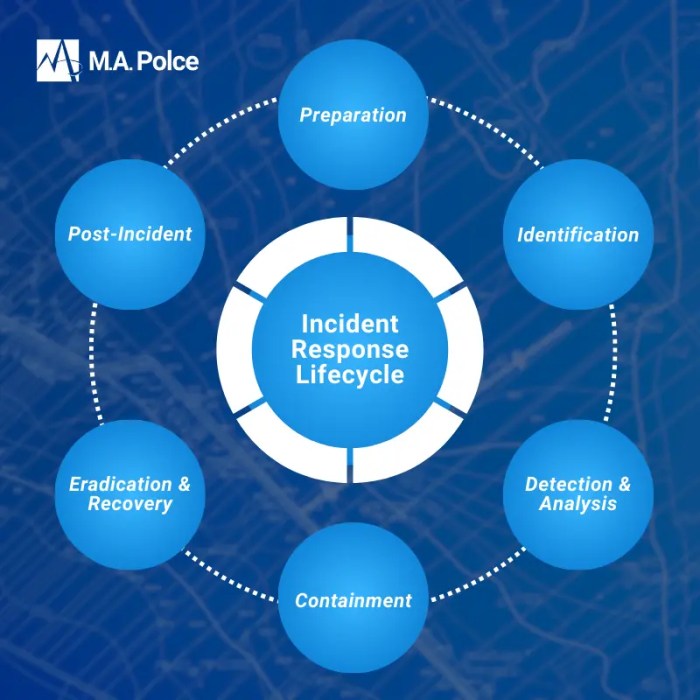
In the face of ever-evolving cyber threats, tabletop exercises are vital for strengthening an organization's incident response capabilities. These dyn...
This comprehensive guide delves into the critical aspects of secure logging and monitoring within cloud environments, exploring its fundamental concep...

This article delves into the critical security challenges inherent in serverless computing, covering everything from authentication and authorization...

This comprehensive guide provides a detailed overview of securing the Kubernetes control plane, covering essential aspects from authentication and aut...

Safeguarding your digital assets requires vigilant monitoring for unauthorized file changes. This article explores the critical importance of detectin...

This article provides a comprehensive analysis of proactive versus reactive security strategies, detailing their core principles, advantages, and limi...

Navigating HIPAA compliance in the cloud requires a strategic approach that addresses data security, access controls, and disaster recovery. This comp...