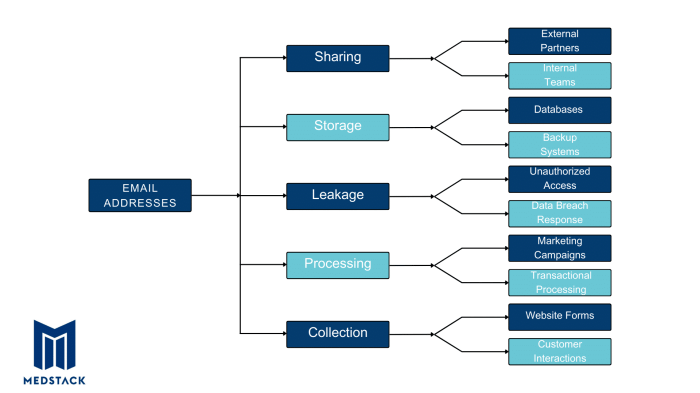
GDPR Data Residency and Sovereignty: Technical Controls for Compliance
This article explores the critical technical controls necessary for organizations to comply with GDPR regulations concerning data residency and sovere...
152 posts in this category

This article explores the critical technical controls necessary for organizations to comply with GDPR regulations concerning data residency and sovere...

In the ever-evolving cloud environment, safeguarding your digital assets is critical, and Cloud Infrastructure Entitlement Management (CIEM) tools off...

In the digital age, the integrity and admissibility of digital evidence are paramount for successful investigations. This article delves into the cruc...

This comprehensive article explores the evolving landscape of cloud security, addressing current threats and vulnerabilities while examining the impac...

Managing third-party contractor access is a crucial element of robust cybersecurity. This guide outlines essential strategies for securely granting ac...

This article provides a comprehensive overview of Cloud Access Security Brokers (CASBs), outlining their core functions, architecture, and key feature...
Handling cardholder data in the cloud necessitates adherence to Payment Card Industry Data Security Standard (PCI DSS) compliance. This guide provides...
Facing an increasingly complex cyber threat landscape, security operations teams need efficient solutions. This article explores how Security Orchestr...
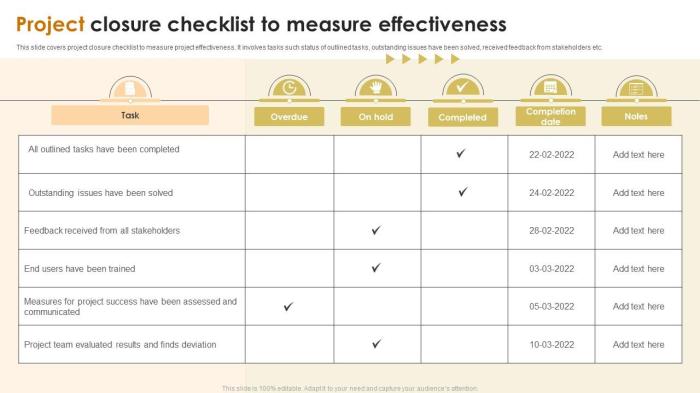
In today's evolving threat landscape, measuring the effectiveness of your security program is paramount. This guide provides a structured approach to...

The NIST Cybersecurity Framework is a widely adopted, voluntary standard designed to help organizations proactively manage and reduce cybersecurity ri...

This comprehensive article delves into Runtime Application Self-Protection (RASP), exploring its fundamental concepts, architecture, and operational m...
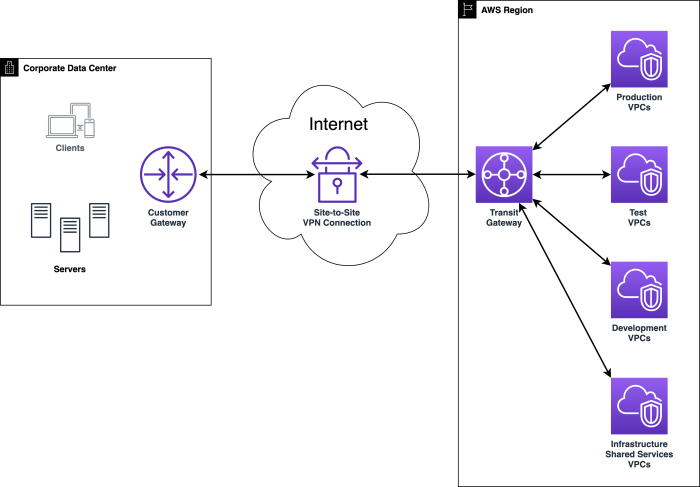
Understand the critical role of Virtual Private Networks (VPNs) in securing modern corporate communications. This article explores the core functional...