
Implementing Runtime Security for Containerized Applications
This article provides a comprehensive overview of runtime security for containers, emphasizing its critical role in protecting containerized applicati...
152 posts in this category

This article provides a comprehensive overview of runtime security for containers, emphasizing its critical role in protecting containerized applicati...
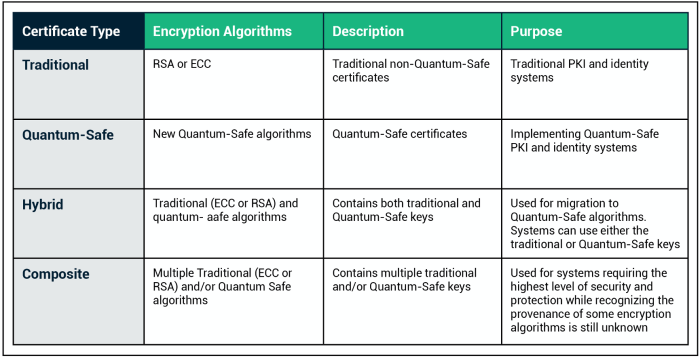
Explore the groundbreaking field of quantum cryptography and its revolutionary impact on cybersecurity in this comprehensive article. From fundamental...

Navigate the complex legal landscape of cloud computing with this comprehensive guide. This article delves into critical areas like data privacy regul...

Safeguarding your cloud environment begins with a thorough vulnerability assessment. This guide provides a structured approach to identifying and miti...
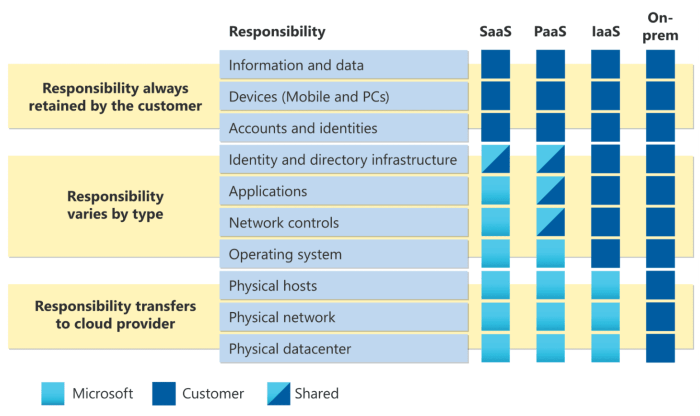
This article explores the critical need to protect "data in use," delving into the inherent security risks and challenges associated with active compu...

Safeguarding a data lake environment requires a multi-faceted approach. This article provides a comprehensive guide to securing your data lake, coveri...

This article provides a comprehensive overview of the Common Vulnerabilities and Exposures (CVE) database, detailing its purpose, structure, and the r...

In the ever-evolving digital world, File Integrity Monitoring (FIM) serves as a crucial security layer, vigilantly protecting your data and systems fr...

This article explores the pivotal role of service meshes in securing modern, microservices-based application architectures. It highlights how service...
In the face of escalating cyber threats, protecting web applications is more critical than ever. This article delves into the essential function of We...

This comprehensive guide delves into the MITRE ATT&CK framework, providing a roadmap for understanding its structure and leveraging its capabilities t...

This article provides a comprehensive overview of cloud-native security services, exploring their core concepts, key components, and numerous benefits...