Selecting the Right Cloud Migration Services Partner: A Comprehensive Guide
Navigating a cloud migration requires careful consideration, and choosing the right partner is essential for success. This guide provides a structured...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Navigating a cloud migration requires careful consideration, and choosing the right partner is essential for success. This guide provides a structured...

This comprehensive guide explores the critical aspects of securing serverless applications and functions, covering everything from authentication and...

This comprehensive guide provides a crucial roadmap for securing Infrastructure as Code (IaC) templates, addressing the inherent security challenges o...
This comprehensive article explores the expansion of FinOps beyond the cloud, addressing the application of its principles across on-premise infrastru...
Cloud architecture demands a strategic approach to ensure optimal performance and efficiency. This guide outlines key principles for designing, optimi...
Navigating a cloud migration requires a robust DNS strategy to ensure seamless operation and optimized performance. This comprehensive guide delves in...

Serverless applications, despite their scalability benefits, require robust strategies for managing sensitive data like API keys and database credenti...

Effectively managing cloud costs requires robust reporting practices, and this article provides a comprehensive guide to establishing them. It delves...

Safeguarding your cloud environment begins with a thorough vulnerability assessment. This guide provides a structured approach to identifying and miti...
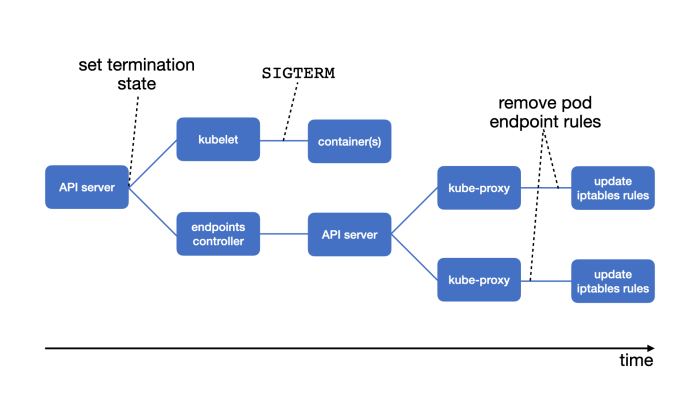
Kubernetes Network Policies act as cloud-native firewalls, providing essential security for containerized applications within your clusters. This arti...
Artificial intelligence is rapidly transforming the cybersecurity landscape, offering powerful new tools for threat detection, incident response, and...

In the digital age, the integrity and admissibility of digital evidence are paramount for successful investigations. This article delves into the cruc...