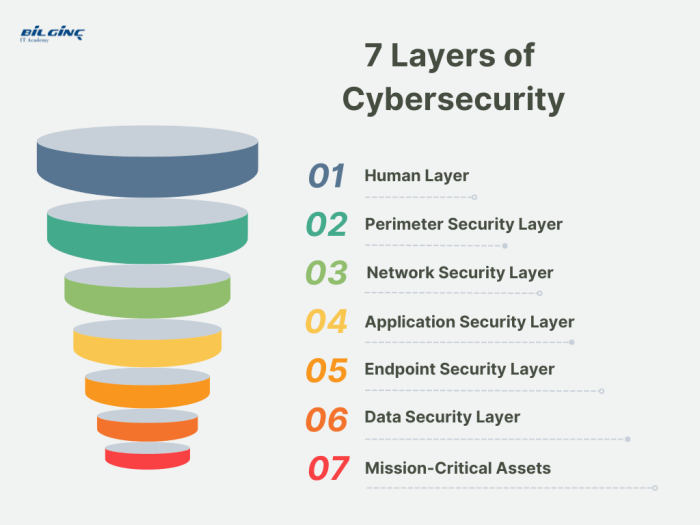
Defense in Depth: A Comprehensive Guide to Cybersecurity Strategy
Defense in depth is a critical cybersecurity principle that emphasizes a layered approach to security, acknowledging that no single measure is impenet...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Defense in depth is a critical cybersecurity principle that emphasizes a layered approach to security, acknowledging that no single measure is impenet...
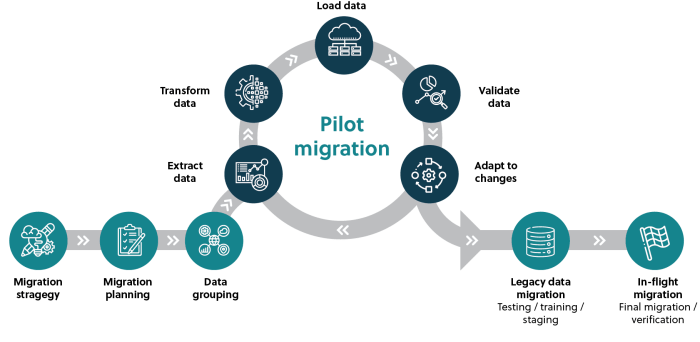
Cloud migration is a critical undertaking requiring a specialized team to navigate the complexities of modern cloud platforms. This process demands a...
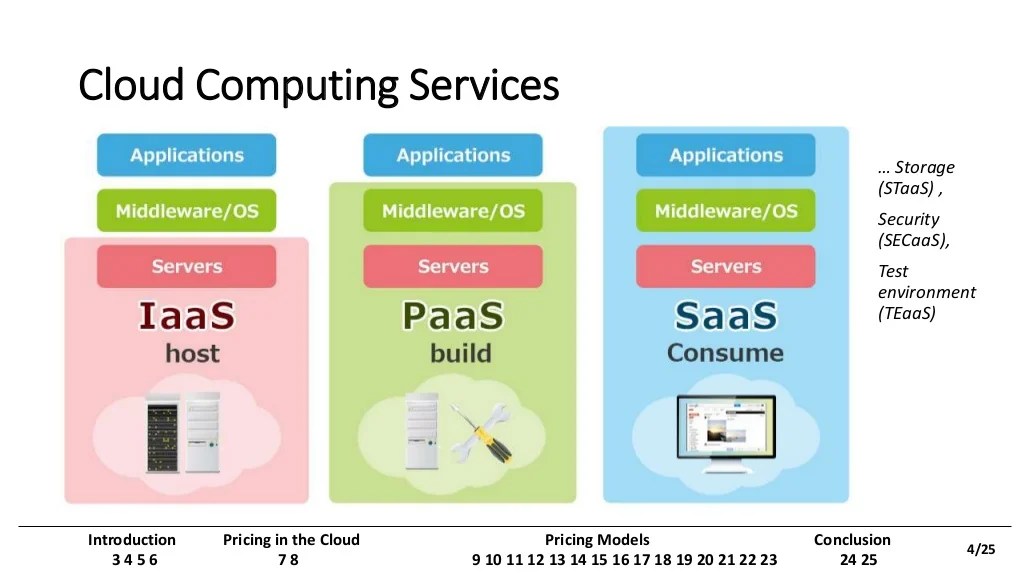
Understanding internal cloud service costs is crucial for efficient resource management. A rate card functions as a price list for your internal cloud...
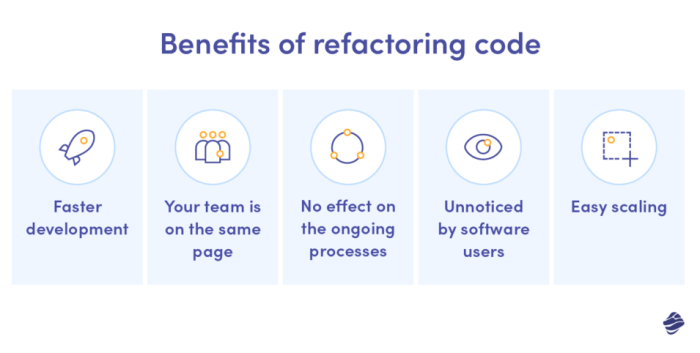
Refactoring code is crucial for long-term software health, allowing developers to improve code structure and maintainability without changing its core...

The Cloud Migration Architect is a crucial role in modern technology, guiding organizations through the complex process of shifting their infrastructu...

Cloud-based database schema transformation is a vital process for optimizing database structures, ensuring they align with evolving business needs and...

This article delves into "Factor III," a critical principle for modern software development that emphasizes separating application configuration from...
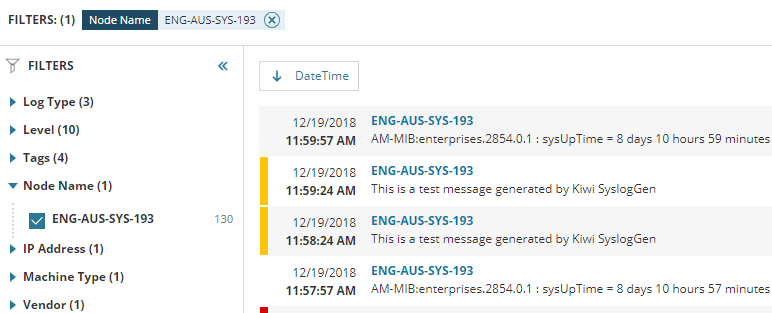
Modern businesses can leverage the power of real-time insights by treating raw log data as dynamic event streams. This approach, explored in detail, e...
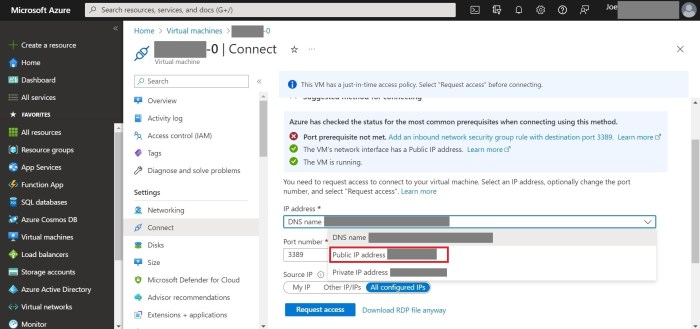
This article delves into the critical concept of Just-in-Time (JIT) access for cloud resources, exploring its core principles and the significant secu...
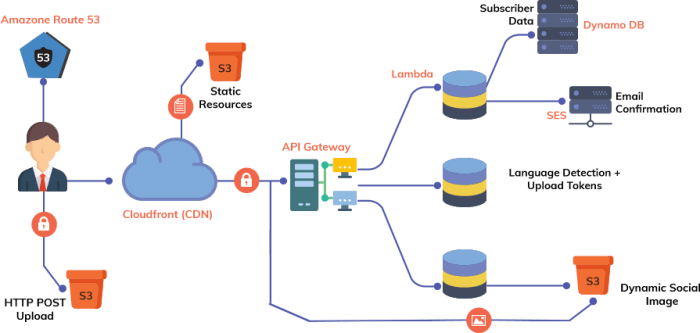
This article delves into the critical aspects of optimizing the inner loop development process for serverless applications, addressing common bottlene...

This comprehensive guide dives into the world of Jenkinsfiles, exploring their crucial role in automating Continuous Integration and Continuous Delive...
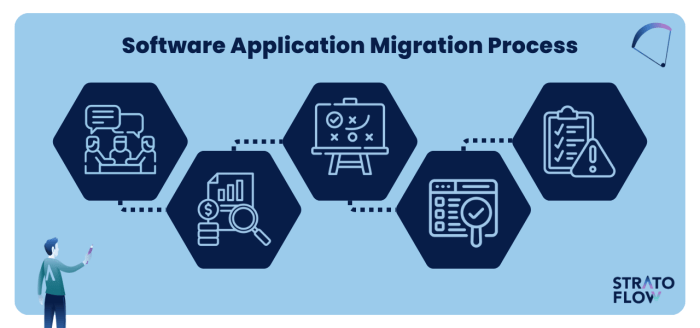
Migrating applications requires careful planning to ensure optimal performance post-migration. This comprehensive guide provides a detailed roadmap, c...