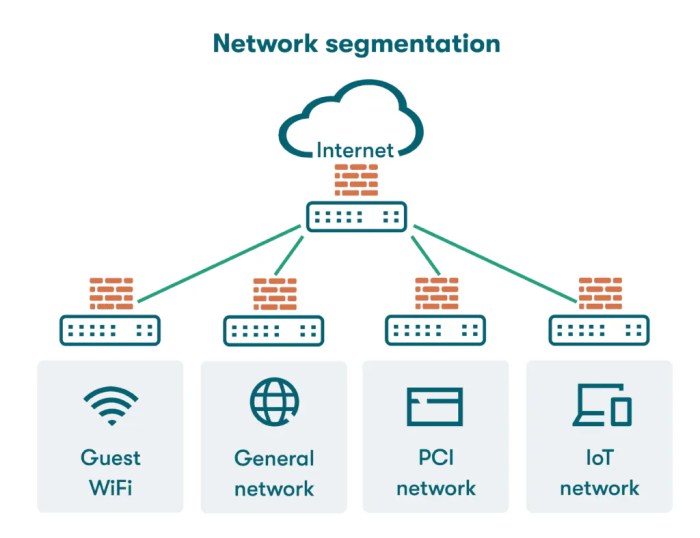
Network Segmentation: A Practical Guide to Enhanced Security
This comprehensive guide provides a deep dive into network segmentation, a crucial strategy for bolstering your organization's security posture. From...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This comprehensive guide provides a deep dive into network segmentation, a crucial strategy for bolstering your organization's security posture. From...
This article delves into the world of serverless databases, exploring their core concepts, evolution, and advantages over traditional systems. You'll...

The CAP Theorem is a fundamental concept in distributed systems, compelling developers to choose between consistency, availability, and partition tole...

Migrating databases to the cloud offers significant advantages in scalability, cost, and accessibility, but requires a strategic approach. This artic...

Pair programming, a collaborative software development technique, offers significant advantages for teams seeking to improve code quality, knowledge s...
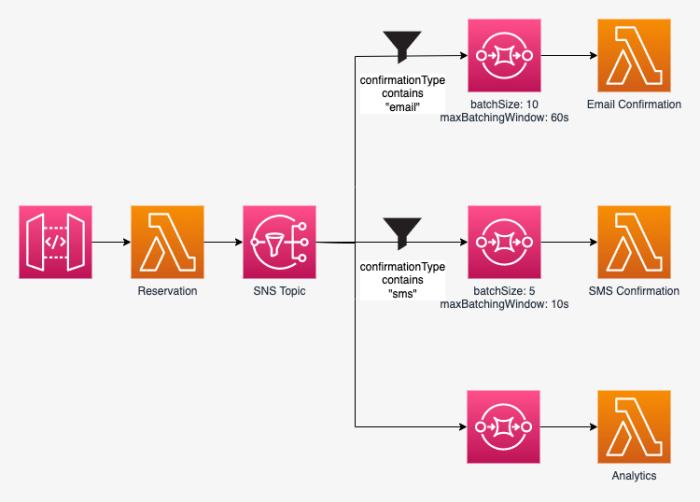
This article provides a comprehensive guide to leveraging Amazon SNS for efficient message fan-out to AWS Lambda functions. Readers will learn how to...

Edge computing is transforming data processing by minimizing latency and improving response times for real-time applications. By shifting computation...

This article explores the crucial role of Product Owners in FinOps, outlining their responsibilities in managing and optimizing cloud costs throughout...

This article delves into the concept of NoOps, exploring its core principles and how serverless computing can facilitate its achievement. By examining...
Facing an increasingly complex cyber threat landscape, security operations teams need efficient solutions. This article explores how Security Orchestr...
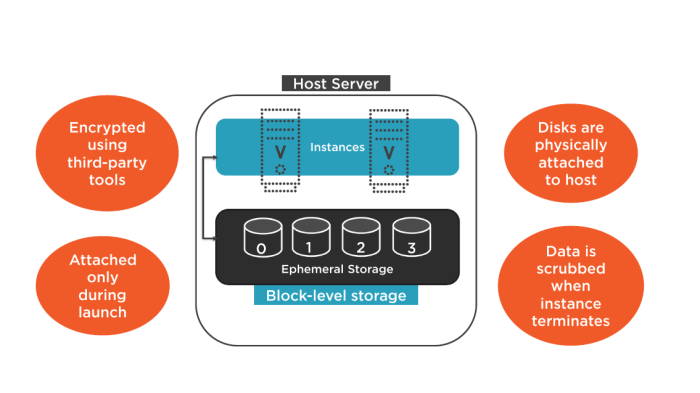
This article delves into the world of ephemeral storage within serverless functions, exploring its characteristics, advantages, and limitations. Reade...

This article provides a comprehensive overview of the Common Vulnerabilities and Exposures (CVE) database, detailing its purpose, structure, and the r...