
5 Key Functions of the NIST Cybersecurity Framework
The NIST Cybersecurity Framework is a widely adopted, voluntary standard designed to help organizations proactively manage and reduce cybersecurity ri...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

The NIST Cybersecurity Framework is a widely adopted, voluntary standard designed to help organizations proactively manage and reduce cybersecurity ri...

This article explores the critical role of automation in modern migration factories, detailing how it streamlines complex processes. From automated da...
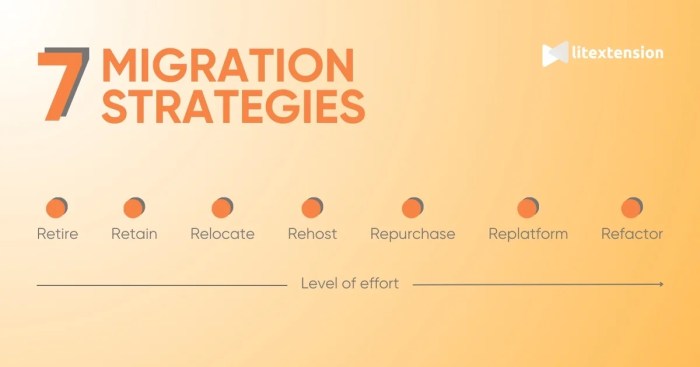
Application migration strategies can significantly impact application latency, a crucial performance indicator reflecting the speed of user request pr...
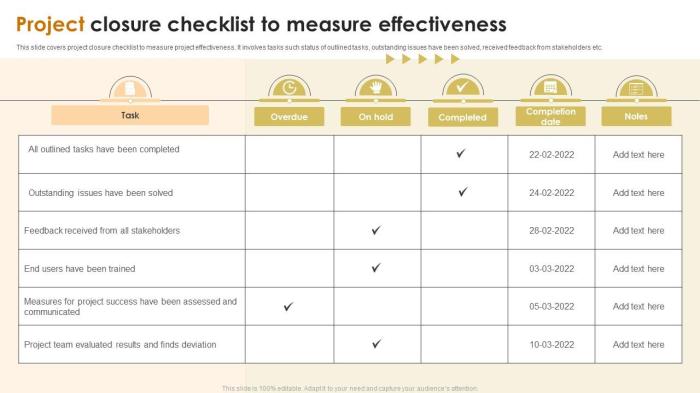
In today's evolving threat landscape, measuring the effectiveness of your security program is paramount. This guide provides a structured approach to...

Minimize disruptions and maximize success by understanding and reducing your change failure rate. This comprehensive guide delves into identifying roo...

Migrating data requires meticulous planning to ensure data integrity throughout the process. This article provides a comprehensive guide to proactivel...

Successfully navigating a cloud migration hinges on establishing well-defined objectives. This comprehensive guide provides a step-by-step approach, c...
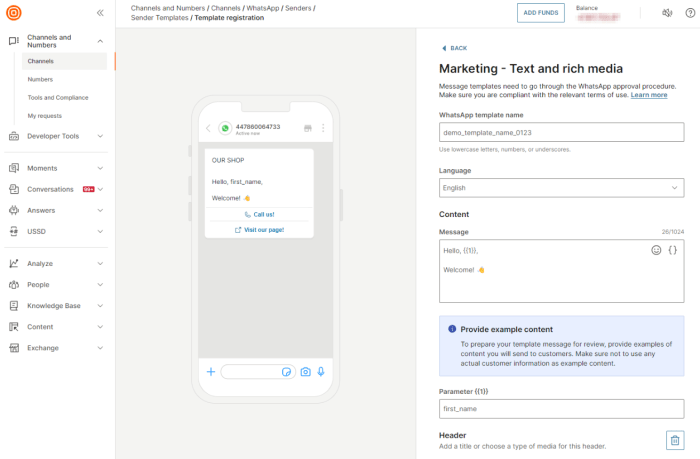
Safeguarding your organization's critical data requires a proactive approach to backup and recovery. This guide provides a step-by-step framework for...
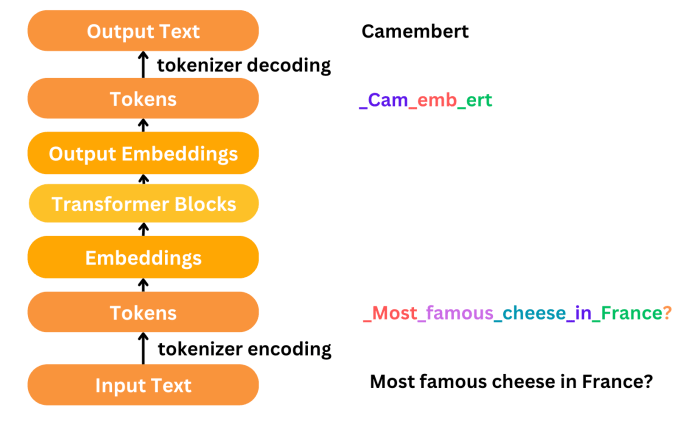
This comprehensive article delves into the critical role of tokenization in modern data security, exploring its core concepts, operational mechanisms,...
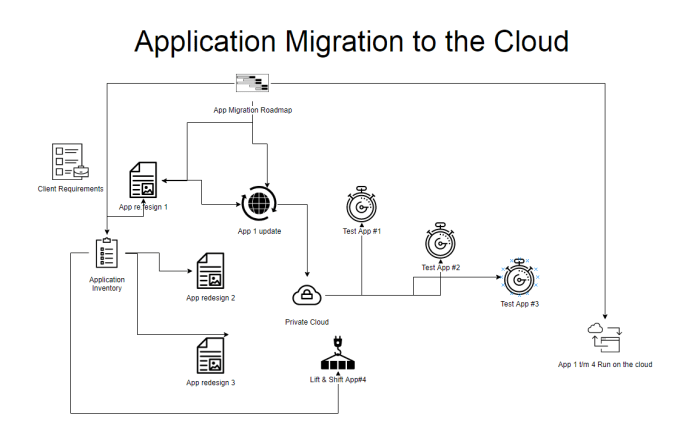
This comprehensive guide provides a step-by-step approach to migrating your web application to the cloud, covering crucial aspects from understanding...

This article provides a comprehensive overview of the roles and responsibilities within a Security Operations Center (SOC), crucial for modern cyberse...
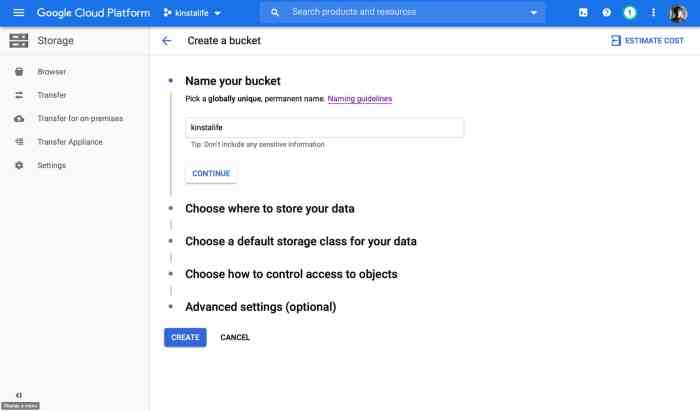
With the increasing reliance on cloud storage, securing your buckets from misconfiguration is crucial. This article delves into the unique security ch...