
Kubernetes Pod Security Policies: Understanding and Implementing Best Practices
Kubernetes Pod Security Policies (PSPs) are crucial for bolstering the security of your containerized applications within a Kubernetes cluster. These...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Kubernetes Pod Security Policies (PSPs) are crucial for bolstering the security of your containerized applications within a Kubernetes cluster. These...
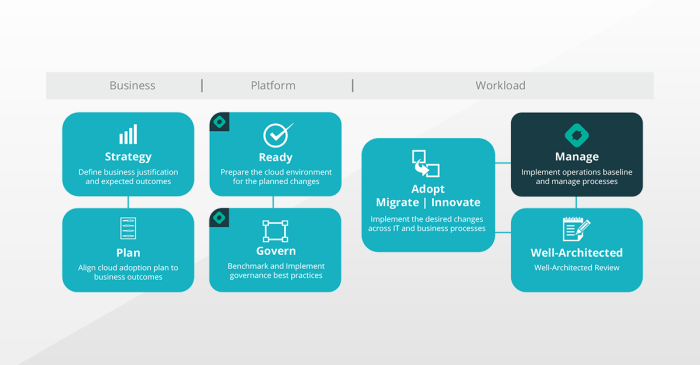
The Azure Cloud Adoption Framework (CAF) provides a comprehensive, phased methodology for organizations transitioning to the Azure cloud environment....
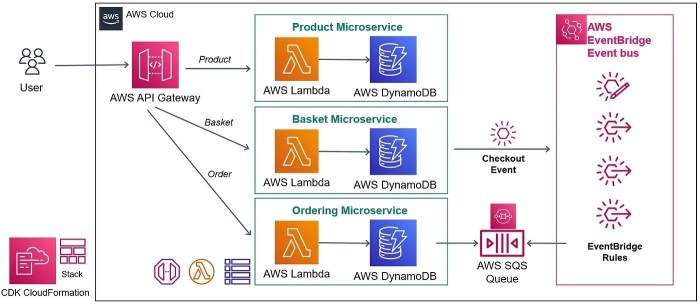
This comprehensive guide delves into the critical aspects of scheduling Lambda functions to automate tasks, covering essential AWS services like Cloud...

This comprehensive guide explores how to build robust and scalable machine learning pipelines within cloud environments. The article covers essential...

This article delves into the critical security challenges inherent in serverless computing, covering everything from authentication and authorization...
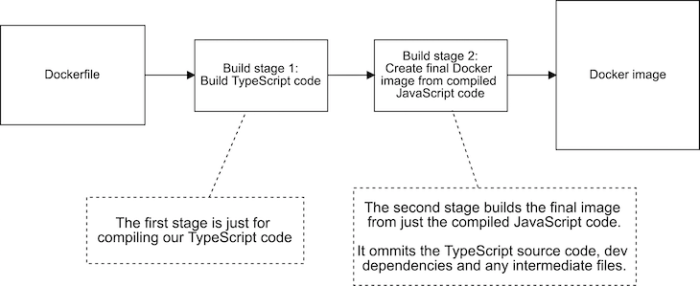
This article provides a comprehensive guide to multi-stage Docker builds, exploring their advantages over single-stage builds in optimizing image size...

Migration projects often face resistance to change, stemming from psychological factors and concerns about the unknown. To ensure a successful transit...
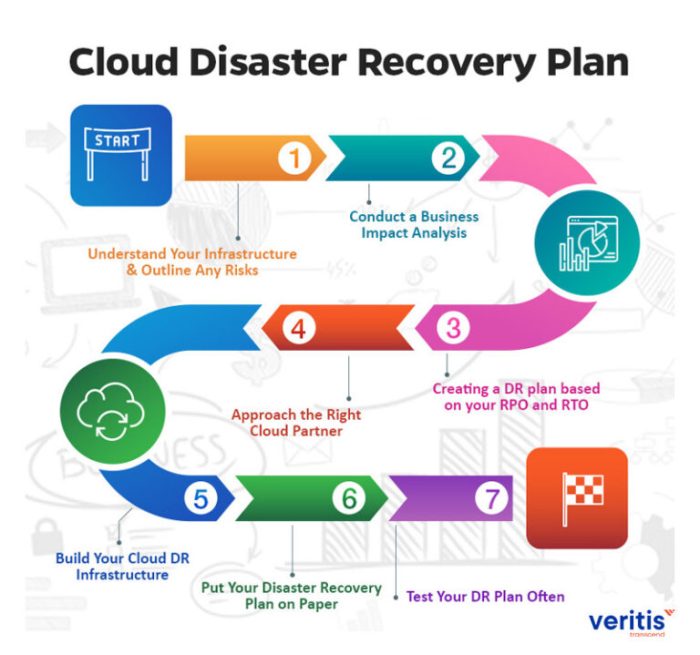
This comprehensive guide explores the critical elements of a cloud disaster recovery plan, covering everything from understanding core objectives and...
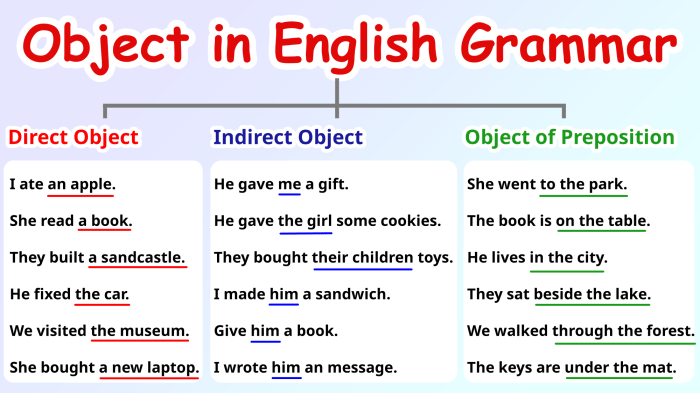
This comprehensive guide delves into the world of object storage, exploring its core concepts, architecture, and diverse applications across various i...
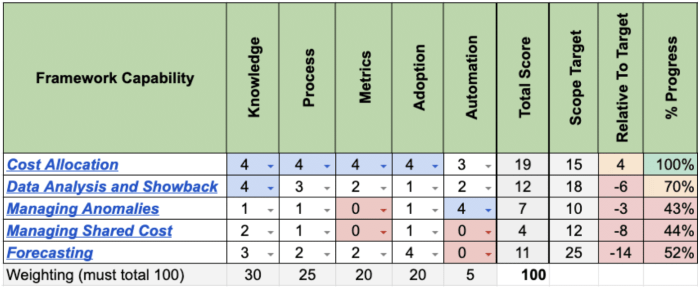
Understand the critical role of a FinOps Review Assessment in optimizing cloud spending and resource utilization. This comprehensive guide delves into...
This comprehensive article delves into the transformative technology of homomorphic encryption, exploring its core functionality, diverse types, and u...
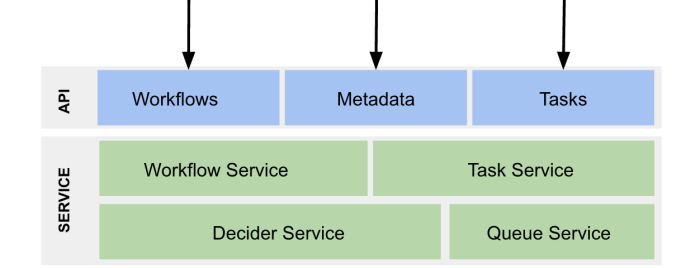
Navigating the complexities of microservices is crucial for building robust and scalable applications. This article provides a comprehensive guide, co...