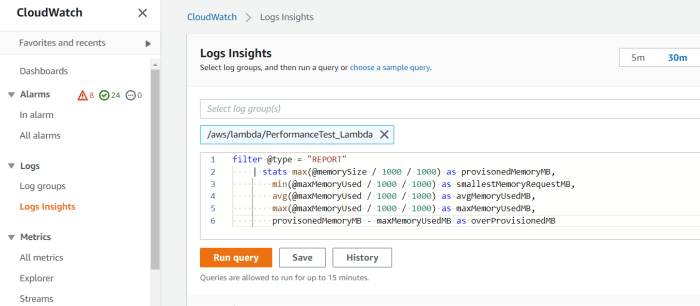
Choosing the Right Memory Size for Your AWS Lambda Function
Optimizing memory allocation is crucial for Lambda function performance, cost-effectiveness, and scalability. This article explores the direct impact...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Optimizing memory allocation is crucial for Lambda function performance, cost-effectiveness, and scalability. This article explores the direct impact...

This article explores the strategic use of Amazon DynamoDB for serverless applications, highlighting its suitability as a scalable and fully managed N...

This comprehensive guide dives deep into the financial landscape of serverless computing, exploring initial infrastructure costs, operational expendit...

This article explores vital strategies for significantly improving deployment frequency, a key metric in modern software development. It examines the...

This comprehensive guide delves into the critical world of log analysis, outlining its fundamental principles, diverse applications, and vital role in...

This comprehensive guide delves into the Cloud Cost and Usage Report (CUR), explaining its fundamental purpose, core components, and benefits for effe...

This article delves into the efficient and secure management of administrative tasks by introducing the concept of "Factor XII," a framework for execu...
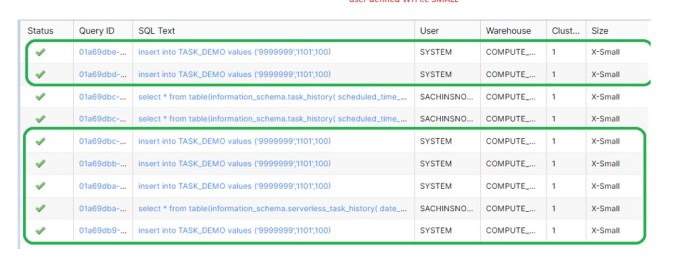
Serverless environments, while offering scalability and cost-efficiency, present challenges when executing tasks that exceed platform time limits. Thi...
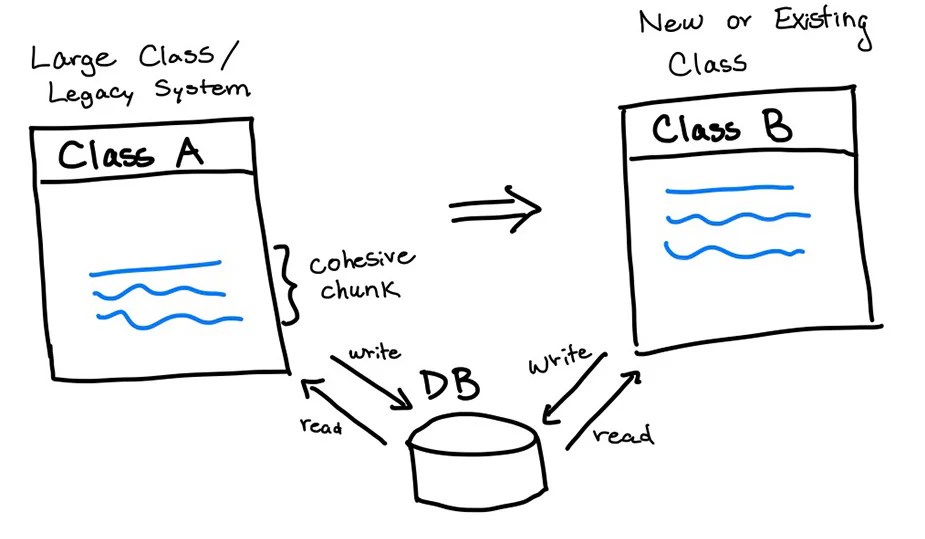
Facing the complexities of application modernization? The Strangler Fig pattern provides a strategic and controlled approach to incrementally update l...
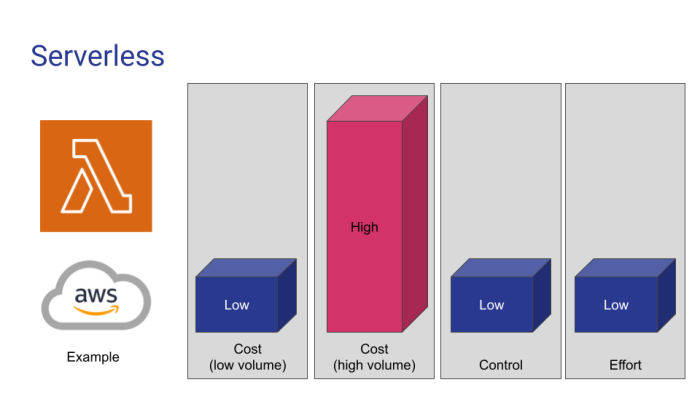
Serverless architecture presents unique debugging challenges due to its cloud-based nature, often requiring time-consuming deployments for issue ident...

Data migration, while crucial for business modernization, inherently carries risks that can disrupt operations. This article explores essential strate...
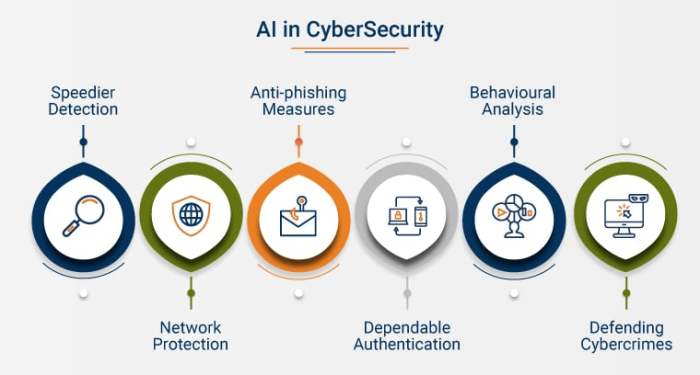
This article explores the vital integration of threat intelligence into cloud security operations, a crucial step in defending against modern cyber th...