Containerized applications are rapidly gaining traction, but debugging them presents unique challenges compared to traditional applications. This guide dives deep into the intricacies of debugging applications running within containers, offering a comprehensive roadmap for developers and administrators. From understanding the nuances of container runtimes to leveraging advanced debugging techniques, we explore a wide spectrum of strategies to effectively troubleshoot issues and optimize performance.
This comprehensive guide delves into various crucial aspects of debugging containerized applications. We’ll cover everything from fundamental logging strategies to advanced remote debugging techniques, providing a practical toolkit for anyone working with containers. This will ensure your debugging process is not only effective but also efficient, minimizing downtime and maximizing application performance.
Introduction to Container Debugging
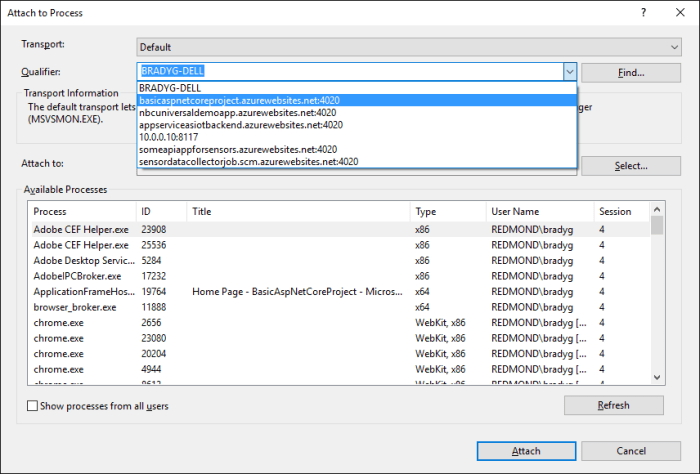
Debugging applications within containerized environments presents unique challenges compared to traditional debugging methods. Containers, by their nature of isolating applications and their dependencies, often obscure the underlying issues when something goes wrong. Understanding these intricacies is crucial for effective troubleshooting. This section delves into the specifics of container debugging, highlighting the differences, common pitfalls, and essential steps for successful debugging.
Challenges in Container Debugging
Traditional debugging methods often rely on direct access to the application’s process and environment. However, containers introduce a layer of abstraction. The application runs within a container, which in turn runs within a container runtime. This layered architecture makes it harder to directly inspect the application’s state and environment. Debugging often requires understanding the interplay between the container runtime and the application itself.
Misconceptions about Container Debugging
A common misconception is that debugging containerized applications is fundamentally different from debugging traditional applications. In reality, the core principles of debugging—understanding the code, tracing execution flow, and analyzing error messages—remain largely the same. The key difference lies in the additional layer of abstraction and the need to interact with the container runtime to gain access to the application’s state.
Another misconception is that debugging tools are not readily available or effective for containers. Modern debugging tools are increasingly adapted to the container environment, providing specialized capabilities to help with this task.
Understanding the Container Runtime
The container runtime, such as Docker, plays a critical role in the debugging process. It manages the container’s lifecycle, including its execution, resource allocation, and interaction with the host operating system. A deep understanding of how the runtime handles these aspects is essential to pinpoint problems that may not be immediately apparent. For instance, resource constraints imposed by the runtime can sometimes be the root cause of performance issues or crashes within the container.
Debugging Workflow for Containerized Applications
A typical debugging workflow for containerized applications involves several key steps:
- Initial Investigation: Gather relevant information, including logs, error messages, and any relevant configuration files. This is often the first step in identifying the potential cause of the issue.
- Inspecting Container Logs: Container logs are a crucial source of information. They provide insights into the application’s behavior, errors, and warnings during execution.
- Using Container Debugging Tools: Modern container runtimes and IDEs often include built-in tools or integrations to inspect the application’s state within the container. These tools allow developers to attach to the container process, set breakpoints, and inspect variables in real-time.
- Analyzing Application Code: Understanding the application’s codebase is essential. Tracing the execution path and identifying potential points of failure is often necessary to diagnose complex issues.
- Leveraging Containerized Development Environments: Replicating the development environment inside a container helps ensure that the issue is reproducible and can be fixed quickly.
Common Debugging Tools
A variety of tools can aid in container debugging, including dedicated container debugging tools, and standard debugging tools adapted to container environments. These tools provide features such as attaching to container processes, inspecting container logs, and setting breakpoints within the containerized application. For example, Docker’s `docker exec` command can be used to run commands inside a running container, providing a means to interact with the application directly.
Additionally, some IDEs and debugging tools now directly support containerized environments, allowing for more seamless integration.
Logging Strategies for Containerized Applications
Effective logging is crucial for debugging containerized applications. Properly structured and configured logs provide valuable insights into application behavior, enabling swift identification and resolution of issues. The distributed nature of container environments necessitates robust logging strategies to ensure comprehensive visibility into the health and performance of applications across multiple containers and services.Logging in containerized applications necessitates a structured approach to ensure that logs are readily accessible and analyzable.
This involves choosing the right logging tools, configuring them effectively within the container orchestration platform, and establishing clear log formats for efficient debugging.
Logging Tools and Their Strengths/Weaknesses
Different logging tools offer varying levels of functionality and support. Selecting the appropriate tool depends on the specific needs of the application and the overall architecture.
| Tool | Strengths | Weaknesses |
|---|---|---|
| Fluentd | Flexible and powerful, capable of processing and forwarding logs to various destinations (Elasticsearch, Kafka, etc.). Supports complex log transformations. | Steeper learning curve compared to simpler options. Requires configuration for data routing and transformation. |
| Logstash | Excellent for log aggregation and analysis, with robust filtering and parsing capabilities. Well-suited for complex log processing pipelines. | Can be resource-intensive for high-volume log streams. Requires significant configuration to set up. |
| Splunk | Mature platform for log management and analysis, offering advanced search capabilities and visualization tools. Widely used in enterprise environments. | Can be expensive for large deployments. Requires dedicated infrastructure. |
| Journald | Lightweight and efficient logging system, particularly suitable for environments with limited resources. Good for simple applications. | Limited features compared to more comprehensive tools. Might not be suitable for complex log processing needs. |
Configuring Logging in Kubernetes
Kubernetes provides several mechanisms for configuring logging within containers. One common approach involves using the `log` field within a container’s configuration.
The Kubernetes `log` field can be configured to specify the logging driver, which directs how logs are handled. This field ensures the logs are accessible through the Kubernetes API. For instance, the `fluentd` driver facilitates log aggregation and analysis across containers and services. This configuration, integrated with the Kubernetes logging stack, helps maintain a centralized view of application logs.
Structuring Logs for Effective Debugging
Structured logs are vital for effective debugging. They enable developers to quickly filter and analyze logs based on specific criteria. A consistent log format allows for easier parsing and analysis using tools like grep, awk, or custom scripts.
A well-structured log format should include essential metadata such as timestamps, log levels (e.g., debug, info, error), component names, and relevant context. For example, including the container ID or pod name allows for precise identification of the source of a log message.
Filtering and Analyzing Container Logs
Filtering and analyzing logs effectively is crucial for isolating issues. Kubernetes provides tools to filter logs based on labels, namespaces, and other criteria. Tools like `kubectl logs` facilitate easy log retrieval. This allows developers to focus on relevant information without being overwhelmed by irrelevant entries.
Analyzing log output involves using tools and techniques to identify patterns, errors, and performance bottlenecks. Analyzing error messages, combined with relevant timestamps, can pinpoint the precise moment and location of failures within the application. Tools like grep, `jq`, or dedicated log analysis platforms are frequently used for this task.
Debugging Tools and Techniques
Containerized applications, while offering numerous benefits, can present unique debugging challenges. Effective debugging within this environment requires specialized tools and techniques that go beyond traditional methods. This section will Artikel various approaches for identifying and resolving issues within containerized applications.Debugging in containerized environments often involves understanding the container’s isolation and the interaction between the container and the host system.
Techniques for troubleshooting network connectivity, inspecting container processes, and using appropriate debugging tools are essential for efficient problem-solving.
Common Debugging Tools for Containers
Effective debugging of containerized applications relies on appropriate tools. Several tools excel at this task, offering various features to aid in diagnosing issues.
- `docker exec`: This command allows interaction with a running container. It’s a powerful tool for executing commands inside the container, enabling direct inspection of processes, logs, and files. For instance, running `docker exec -it
bash` provides a shell inside the container, facilitating direct interaction with the application. - `docker logs`: Provides access to container logs. This is a fundamental tool for understanding application behavior and identifying error messages. Filtering logs by time or specific s can pinpoint issues efficiently.
- `strace`: This system call tracer provides detailed information about system calls made by processes. By executing `strace -f
` within a container, you can track interactions with the operating system, revealing potential issues related to resource allocation or file access. - `tcpdump`: Captures network traffic. This is useful for troubleshooting network-related problems within a container. `tcpdump` can be used to capture network traffic on specific ports or from specific processes within the container, helping identify bottlenecks or communication failures.
Remote Debugging Techniques in Containers
Remote debugging allows you to debug an application running inside a container as if it were running on your local machine. This approach simplifies the process by eliminating the need to manually enter the container.
- Using a Debugger with SSH: Establishing a secure shell (SSH) connection to the container enables remote debugging. This method facilitates interacting with the application and setting breakpoints within the container’s code. Tools like `gdb` can then be employed to inspect variables and step through code execution.
- Specialized Container Debugging Tools: Some container platforms provide dedicated debugging tools. These tools often integrate seamlessly with the container environment, offering features like remote debugging and log analysis. They can make the debugging process considerably easier by providing a user-friendly interface.
Debugging with Debuggers in Containerized Applications
Debuggers are invaluable tools for examining the behavior of containerized applications. They provide detailed insights into the program’s execution, enabling developers to pinpoint errors precisely.
- Using gdb with Docker: `gdb` can be used to debug applications running within Docker containers. A common approach is to use `docker exec` to launch the application with debugging flags or a debug port, then connect to the process using `gdb`. This method allows setting breakpoints, inspecting variables, and stepping through the code to identify the source of errors.
Using `ps`, `top`, and `lsof` for Inspecting Processes and State
These command-line tools provide valuable insights into the processes and resource usage within a container. Their use enables detailed examination of the running processes and the system resources they consume.
- `ps`: This command displays a list of currently running processes. Using `ps aux | grep
` inside the container, you can identify and track the process of interest. - `top`: This command provides a dynamic view of system resource usage. Running `top` within a container helps monitor CPU, memory, and network usage by specific processes.
- `lsof`: This command displays the files opened by processes. Using `lsof` within a container helps to identify files or resources that the application is accessing, potentially revealing file system issues.
Troubleshooting Network Issues in Containerized Applications
Network issues are frequent causes of application problems within containers. Understanding the network configuration and interaction between the container and the host is crucial for resolution.
- Inspecting Container Network Configuration: Using `docker inspect
` provides details about the container’s network settings. Understanding the IP addresses, ports, and network interfaces assigned to the container is vital for diagnosing network-related problems. - Verifying Network Connectivity: Using tools like `ping` and `traceroute` within the container or on the host can identify network connectivity problems between the container and other systems.
Container Orchestration Platforms
Container orchestration platforms like Kubernetes and Docker Compose significantly simplify the deployment and management of containerized applications. They automate tasks such as scaling, load balancing, and resource allocation, which allows developers to focus on application logic rather than infrastructure management. Effective debugging within these platforms is crucial for identifying and resolving issues efficiently.
Debugging applications deployed on container orchestration platforms often requires a different approach compared to debugging standalone containers. These platforms provide tools and mechanisms for interacting with the containerized environment and managing the application’s lifecycle. This includes understanding the platform’s specific features and tools for debugging, and how they can be integrated with existing debugging strategies.
Debugging Applications on Kubernetes
Kubernetes provides a robust set of tools for debugging applications deployed within its cluster. `kubectl debug` is a powerful command-line tool that allows interactive debugging of running containers. This command creates a shell session inside the container, enabling direct interaction with the application’s code.
The `kubectl debug` command leverages the `port-forward` functionality of Kubernetes to establish a connection between the debugging tool and the container.
Using `kubectl debug` requires specifying the pod name and the port number to debug. This allows developers to attach to a specific process within the container and step through the code, examine variables, and inspect the application’s state in real-time.
Debugging Containers within Docker Compose
Docker Compose, while not offering the same comprehensive debugging features as Kubernetes, still allows for debugging. The approach often involves using `docker exec` to enter the container and use tools like `gdb` or `strace`.
Debugging with Docker Compose involves executing a command within the container to access the application and use tools like `gdb` or `strace` to debug the code.
This method can be effective for smaller applications or for situations where a simple shell session is sufficient. For more complex scenarios, leveraging tools provided by the Docker daemon can be helpful.
Comparison of Debugging Tools and Strategies
| Orchestration Platform | Debugging Tools | Strategies |
|---|---|---|
| Kubernetes | `kubectl debug`, `kubectl port-forward`, `kubectl exec` | Interactive debugging within the container using `kubectl debug`, inspecting logs, tracing the application’s lifecycle. |
| Docker Compose | `docker exec`, `docker logs`, container-specific utilities | Using `docker exec` to enter the container, utilizing debugging tools like `gdb`, or analyzing logs. |
This table provides a simplified comparison. The specific tools and strategies may vary based on the application’s architecture and the nature of the debugging issue.
Leveraging Platform Monitoring for Debugging
Container orchestration platforms provide comprehensive monitoring capabilities. Monitoring tools often provide insights into resource usage, network traffic, and application performance, which can be invaluable in identifying potential debugging points. Observability features such as metrics, logs, and tracing can help pinpoint bottlenecks and performance issues.
Leveraging platform monitoring tools allows developers to correlate application behavior with resource utilization and identify potential problems before they escalate.
By examining metrics and logs, developers can understand the application’s performance and resource consumption, helping in diagnosing problems that might not be immediately obvious through direct debugging. This proactive approach can significantly reduce debugging time.
Troubleshooting Common Issues
Containerized applications, while offering numerous benefits, can present unique debugging challenges. Understanding common issues and their effective troubleshooting strategies is crucial for maintaining application stability and performance within a containerized environment. This section delves into typical problems encountered during container debugging, outlining troubleshooting steps and performance analysis techniques.
Troubleshooting in a containerized environment often requires a multifaceted approach. A thorough understanding of the container’s internal workings, coupled with knowledge of the host system and the application itself, is essential for effective resolution. The steps Artikeld below will help you navigate common problems and restore optimal application functionality.
Network Connectivity Problems
Network issues are a frequent source of frustration in containerized applications. These issues can stem from misconfigurations in the container network, conflicts with other containers, or problems with the host machine’s networking infrastructure.
To diagnose network problems, first verify that the container can reach essential services. Use `ping` or `curl` commands from within the container to test connectivity to external resources. If connectivity is lost, inspect the container’s network configuration. Ensure the container has the necessary network access and that ports are exposed correctly. Examine logs for error messages related to network issues.
Check for firewall rules that might be blocking communication. Review the container orchestration platform’s network configuration settings, especially if using services like Docker Compose or Kubernetes. If the issue persists, check the host machine’s network configuration and logs for any conflicts or outages.
Resource Constraints
Containers, like any other application, are susceptible to resource limitations. Insufficient CPU, memory, or disk space can lead to performance degradation or application crashes. Understanding how to identify and address resource constraints is critical.
Analyzing container metrics, such as CPU usage, memory consumption, and disk I/O, is essential for identifying resource bottlenecks. Tools like `docker stats` and container-specific monitoring tools can provide valuable insights. Adjust container resource limits (CPU shares, memory limits) in the container definition file or orchestration platform to prevent resource exhaustion. If possible, optimize the application code to reduce resource consumption.
Consider scaling the containerized application vertically or horizontally to handle increased load.
Application Crashes
Application crashes within a container can be caused by various factors, including runtime errors, unexpected input, or conflicts with other components. Efficiently handling these crashes is critical for maintaining application stability.
Examine container logs for error messages or stack traces. These clues often pinpoint the root cause of the crash. Isolate the faulty code section by stepping through the application logic using debugging tools within the container. Check for potential dependencies or external service issues that could trigger the crash. If the crash occurs during specific operations, analyze the input data or sequence of events leading to the crash.
Common Container Errors and Probable Causes
| Error | Probable Cause |
|---|---|
| “Container exited with code 1” | Application crashes, runtime errors, or incorrect configurations. |
| “Resource limit exceeded” | Insufficient allocated resources (CPU, memory, or disk). |
| “Network connection failed” | Issues with container networking, host machine network, or firewall rules. |
| “Image pull failed” | Issues with the Docker registry, network connectivity, or incorrect image specification. |
Recovery Methods
Identifying and addressing the root cause of an error is the first step towards recovery. Redeploying the container with corrected configurations, increasing allocated resources, or fixing application bugs are common recovery strategies. If the issue stems from external dependencies, resolving the dependency problems or adjusting the application logic to handle potential failures is important. In complex scenarios, rolling back to a previous deployment version can be a viable option to restore application functionality.
Security Considerations in Container Debugging
Debugging containerized applications presents unique security challenges. Care must be taken to prevent exposing sensitive data or compromising the security posture of the entire system. A secure debugging environment is crucial to mitigate these risks and maintain the integrity of the containerized application and the host infrastructure.
Understanding the potential security implications of debugging is paramount. Incorrectly configured debugging tools or processes can lead to data breaches, unauthorized access, and potential exploitation of vulnerabilities. This necessitates a proactive approach to secure debugging practices within containerized environments.
Security Implications of Container Debugging
Container debugging can introduce vulnerabilities if not implemented securely. Improper access controls and insecure debugging environments can expose sensitive data and configurations, potentially leading to unauthorized access and data breaches. This is exacerbated by the shared nature of container environments where multiple applications may run concurrently, potentially increasing the risk of compromise. Debugging tools themselves can become vectors for attacks if not carefully vetted and configured.
Secure Debugging Environments
Creating a dedicated and isolated debugging environment is vital. This environment should be segregated from the production environment to prevent unintended exposure of sensitive data or configurations. Virtual machines (VMs) or dedicated network segments can be used to isolate the debugging environment and limit the impact of potential breaches. Furthermore, stringent access controls should be implemented to restrict access to the debugging environment to authorized personnel only.
Preventing Security Vulnerabilities During Debugging
Employing secure debugging techniques is crucial to prevent security vulnerabilities. Using tools with strong security features, like those with robust access controls, is paramount. Implementing least privilege access for debugging tools and personnel is critical to limit the potential damage from any security breaches or misconfigurations. Regular security audits and penetration testing of the debugging environment should be conducted to identify and mitigate potential vulnerabilities.
Secure Logging Practices within a Container
Secure logging is essential for containerized applications. Logs should be encrypted in transit and at rest, protecting sensitive information from unauthorized access. Logs should be properly formatted and structured to facilitate analysis without compromising sensitive data. Log rotation policies should be implemented to manage the volume of logs and prevent potential storage issues. Logging should be designed to comply with data privacy regulations and industry best practices.
Recommendations for Secure Debugging Procedures in Containerized Environments
Secure debugging procedures should be a fundamental part of the containerization lifecycle. Explicitly defined security protocols should be established and followed during the debugging process. Regular security assessments and penetration testing of the debugging environment should be performed to proactively identify and address potential vulnerabilities. Strict access control policies and authentication mechanisms should be enforced for all debugging tools and processes.
Furthermore, container images used for debugging should be carefully audited for known vulnerabilities and patched accordingly.
Performance Analysis and Optimization
Optimizing the performance of containerized applications is crucial for ensuring responsiveness, scalability, and resource efficiency. Effective performance analysis and optimization techniques are essential for identifying and mitigating bottlenecks within containerized environments, leading to improved application performance and user experience. This involves understanding the interplay between the application, container runtime, and underlying infrastructure.
Methods for Analyzing Containerized Application Performance
Performance analysis of containerized applications requires a multi-faceted approach. Monitoring tools provide real-time insights into resource utilization, such as CPU, memory, network bandwidth, and disk I/O. Detailed logging mechanisms offer valuable insights into application behavior, allowing for identification of potential performance issues. Furthermore, tracing tools are essential for understanding the flow of requests through the application, highlighting areas with prolonged processing times.
Identifying Bottlenecks in Containerized Applications
Bottlenecks in containerized applications can stem from various sources. These include issues within the application code itself, limitations of the container runtime, or inefficiencies in the underlying infrastructure. Resource contention between containers within a shared host can also lead to performance degradation. Analyzing resource utilization patterns and request response times can pinpoint these areas of concern.
Optimizing the Performance of Containerized Applications
Optimizing containerized applications involves addressing the identified bottlenecks. This can range from code optimization to improved resource allocation. Techniques like caching frequently accessed data, implementing efficient algorithms, and reducing database queries can improve application performance. Furthermore, strategic deployment on suitable hardware and network configurations can yield significant improvements.
Profiling Tools for Containerized Applications
Several profiling tools cater to the needs of containerized applications. These tools allow developers to examine the execution flow of the application code, identifying sections with high CPU or memory consumption. They provide insights into function calls, method durations, and memory allocations. This granular level of detail aids in pinpoint identification of performance issues. Tools like `perf` and `flame graphs` are commonly used for deep analysis.
`perf` provides detailed performance statistics and `flame graphs` visualize call stacks, highlighting the most time-consuming functions.
Using Profiling Tools to Pinpoint Performance Issues
Profiling tools offer a systematic approach to pinpoint performance issues within containerized applications. For instance, if a `perf` analysis reveals high CPU usage in a specific function, developers can then investigate the underlying logic, identify areas of improvement, and implement optimizations to reduce the function’s resource consumption. The output from the profiling tools can guide developers to understand the time spent in various parts of the application, allowing for targeted optimizations and enhancing the application’s efficiency.
A thorough analysis of profiling data can pinpoint and address performance bottlenecks effectively.
Remote Debugging Strategies
Remote debugging allows developers to inspect and modify the behavior of containerized applications running in isolated environments without needing to directly access the container host. This capability is crucial for troubleshooting issues, performing performance analysis, and identifying security vulnerabilities within the containerized application. This approach provides a secure and efficient means to interact with the application in its contained environment.
Secure Remote Connections
Establishing secure remote connections is paramount for debugging containerized applications. This typically involves using secure protocols like SSH or a dedicated debugging port forwarding mechanism. SSH tunnels create encrypted connections between the developer’s machine and the container, ensuring the confidentiality and integrity of the debugging process. Using SSH keys rather than passwords enhances security further. Dedicated debugging ports are also an effective solution to facilitate remote debugging without exposing the entire container network.
Using SSH keys and port forwarding methods is often a standard practice in security-sensitive environments.
Setting Up a Remote Debugging Environment
A well-configured remote debugging environment is essential for smooth operation. This often involves the following steps:
- Identifying the container’s IP address or hostname and the port number where the debugging session will be initiated.
- Establishing a secure shell (SSH) connection to the host machine where the container is running.
- Using a remote debugging tool to connect to the container through the SSH connection, usually via a port forwarding mechanism. This establishes the debugging channel. Specific tools and their configuration methods will vary.
Troubleshooting Connection Problems
Troubleshooting remote debugging connections involves diagnosing issues with the network, the SSH connection, or the container’s configuration. Potential problems include firewall restrictions, incorrect port mappings, and issues with the debugging tool itself. Verify the SSH connection’s functionality by testing it independently. Check the firewall rules on both the developer’s machine and the host machine to ensure that the debugging port is open.
Ensure that the container’s configuration correctly maps the debugging port to the host machine’s port. Confirm the debugging tool is configured correctly.
Using Tools for Remote Debugging
Several tools facilitate remote debugging of containerized applications. These tools often leverage SSH tunnels or dedicated debugging ports to connect to the container’s processes. Popular choices include `gdb` (GNU Debugger) and `lldb` (LLDB).
Comparison of Remote Debugging Methods
| Method | Description | Pros | Cons |
|---|---|---|---|
| SSH Tunneling | Uses SSH to establish a secure tunnel for debugging. | Secure, widely supported | Can be complex to configure, might impact container performance |
| Dedicated Debugging Ports | Using dedicated ports for debugging within the container. | Can be more efficient than SSH tunneling, less complex for basic debugging. | Requires configuration changes within the container, might require extra setup. |
Debugging State Management
Containerized applications often rely on intricate state management mechanisms. Understanding and effectively troubleshooting these mechanisms is crucial for maintaining application stability and integrity. Problems with state management can manifest in unpredictable behavior, data inconsistencies, and application crashes. This section explores common issues, troubleshooting methods, and tools for debugging state management within containerized environments.
State management in containerized applications encompasses various aspects, from persistent data storage to in-memory data structures. Ensuring data integrity and consistency across container restarts, deployments, and scaling is a critical challenge. Effective debugging requires a systematic approach to identify the root cause of state management problems.
Common State Management Issues in Containerized Applications
Various issues can arise in containerized applications regarding state management. These include data corruption, race conditions during concurrent access to shared state, and inconsistencies between different components of the application. Understanding these issues is the first step in effectively troubleshooting them.
- Data corruption can result from various factors, such as disk failures, network issues, or application bugs. This can lead to loss or modification of critical data, impacting the application’s functionality and potentially causing system-wide issues.
- Race conditions often occur when multiple processes or threads attempt to access and modify shared state simultaneously. Without proper synchronization mechanisms, these concurrent operations can lead to unpredictable and inconsistent application behavior.
- Inconsistencies between different components can arise from mismatched state representations or differences in the way different parts of the application interact with the shared state. This can lead to incorrect calculations, data loss, or other unexpected behavior.
Troubleshooting State Management Problems
Effective troubleshooting involves a methodical approach. This begins with analyzing logs and monitoring metrics to identify potential issues. Then, examining the application’s code and its interaction with the state management mechanisms is necessary.
- Analyze application logs to identify error messages, warnings, or unusual patterns related to state management operations. Reviewing log messages can pinpoint the exact time and context of the problem, which is crucial for tracing the root cause.
- Monitor application metrics, such as CPU usage, memory consumption, and network activity. Identifying performance bottlenecks or resource constraints can indicate potential problems with state management. For example, excessive CPU usage during a specific state transition could suggest a problem with the synchronization or locking mechanisms.
- Inspect the application’s code to understand how the state is managed. This includes identifying all points where the state is accessed, modified, or persisted. Careful review of the code, including the algorithms used to update and retrieve state, is essential to identify potential bugs.
Tracking Changes in Application State
Tracking changes in the application’s state within a container is critical for debugging. Tools and techniques can pinpoint the exact sequence of events leading to a state issue.
- Implement logging strategies to record state changes at key points in the application’s execution. This allows for detailed analysis of how the state evolves over time. By strategically placing log entries, you can track the state transitions and identify the exact point where a problem arises.
- Utilize debugging tools that provide real-time visibility into the application’s state. These tools allow you to inspect the values of variables, the state of objects, and the relationships between different parts of the application. This direct observation is critical in identifying inconsistencies or corruption.
Tools for Debugging State Management Within Containers
Several tools aid in debugging state management issues within containers. These tools offer diverse functionalities, allowing for comprehensive analysis of the application’s state.
- Container-specific debugging tools, often provided by container platforms, provide access to the container’s internal state. These tools allow examination of process memory and file system changes, providing a detailed view of the container’s behavior.
- Debugging tools for the programming languages used in the application, such as debuggers for Java, Python, or Go, can be used to step through code and inspect the state at different points during execution. These debuggers can pinpoint the exact location and nature of state management issues.
Diagnosing Data Corruption Issues
Data corruption within containers necessitates careful analysis to pinpoint the source and implement corrective measures. Comparing the expected and actual state values is crucial for identifying the issue.
- Compare the expected state values with the actual state values to identify discrepancies. Using version control or a state snapshot mechanism can help determine the point at which corruption occurred.
- Analyze the code for potential errors that could lead to data corruption. Focus on areas where data is loaded, stored, or modified. Review these parts of the code for potential flaws that could lead to unintended changes or data loss.
Advanced Debugging Techniques
Containerized applications, while offering numerous benefits, introduce unique challenges for debugging. Advanced techniques are crucial for effectively identifying and resolving issues within complex containerized environments. These techniques delve beyond basic troubleshooting, focusing on analyzing interactions between containers, intricate dependencies, and optimized logging strategies.
Understanding the intricate workings of containerized applications, including their interactions with shared resources and the complexities of orchestrators like Kubernetes, is essential for effectively debugging issues. Advanced logging, enhanced debugging tools, and a structured approach to multi-container troubleshooting are vital for successful resolution.
Advanced Logging Techniques for Complex Scenarios
Effective logging is paramount for diagnosing issues in containerized applications. Advanced techniques involve tailoring logging to specific needs, utilizing structured logging formats, and leveraging log aggregation tools. These methods allow for more precise analysis of application behavior and identify potential issues quickly.
For instance, using structured logging formats like JSON allows for more effective filtering and querying of logs. This structured approach allows debugging tools to easily parse and analyze log entries, making it simpler to isolate and reproduce issues. Advanced log aggregation tools provide centralized storage and analysis capabilities, allowing for comprehensive insights into application behavior across multiple containers.
Real-time log streaming and alerts provide immediate notifications of critical events.
Debugging Multi-Container Applications
Multi-container applications present unique debugging challenges. Strategies for troubleshooting include understanding the dependencies between containers, analyzing inter-container communication, and monitoring resource usage across the entire application.
A comprehensive understanding of how containers interact with each other is essential. This often involves understanding the network configurations and the mechanisms through which containers communicate, such as inter-container communication mechanisms or shared volumes. Monitoring resource consumption across all containers can highlight bottlenecks and resource conflicts that might not be apparent in a single container.
Advanced Debugging Tools and Techniques for Analyzing Application Interactions
Debugging tools need to be tailored to the containerized environment. This requires specialized tools capable of tracing and analyzing interactions between containers. Advanced debugging techniques include utilizing container-specific tools, leveraging orchestration platform features, and employing network analysis tools.
Container-specific tools offer detailed insights into container internals. These often provide insights into resource utilization, network traffic, and execution context. Orchestration platforms like Kubernetes provide built-in debugging capabilities, allowing for monitoring and tracing of application behavior across the entire cluster. Network analysis tools are crucial for understanding communication patterns between containers, identifying network bottlenecks, and verifying data flow.
Troubleshooting Complex Dependencies in a Containerized Environment
Complex dependencies in containerized applications require a methodical approach to troubleshooting. This involves identifying dependencies, analyzing dependency conflicts, and utilizing dependency management tools. Furthermore, understanding the impact of dependencies on resource allocation is essential for effective troubleshooting.
Dependencies need to be identified and documented. This documentation aids in understanding how components interact and pinpoint potential points of failure. Understanding how dependencies conflict is crucial for debugging. Tools for dependency management can assist in tracking and resolving these conflicts. Analyzing the impact of dependencies on resource allocation helps identify and prevent bottlenecks.
Identifying bottlenecks helps to optimize the application.
Closing Summary
In conclusion, debugging containerized applications requires a multifaceted approach that considers logging, tools, orchestration platforms, troubleshooting, security, performance analysis, and remote strategies. This guide has equipped you with the necessary knowledge to tackle common and complex issues effectively. By understanding the unique characteristics of containerized environments and applying the techniques discussed, you can significantly enhance your debugging capabilities and optimize your containerized application deployments.
Clarifying Questions
What are the common pitfalls when debugging containerized applications?
Common pitfalls include network connectivity issues within the container, misconfigurations in logging setups, and difficulties in tracing the application’s flow within the containerized environment.
How can I effectively analyze container logs for debugging?
Utilize log aggregation tools to centralize logs from multiple containers. Employ filters to isolate relevant logs and analyze them for patterns, errors, or unusual events. Tools like fluentd or Elasticsearch can be helpful.
What are some specific debugging tools for Kubernetes?
Kubernetes offers tools like `kubectl debug` for remote debugging. Understanding the Kubernetes debugging context and utilizing relevant commands are key.
How do I handle security considerations during container debugging?
Prioritize secure debugging environments. Ensure all debugging tools and techniques used are secure, limiting access to only authorized personnel. Carefully review logging practices and apply appropriate security measures to avoid exposing sensitive data during the debugging process.