The transition to the cloud, while offering significant advantages, introduces inherent risks. Cloud migration projects, due to their complexity, are susceptible to unforeseen issues that can lead to service disruptions, data loss, and financial implications. Therefore, a robust rollback plan is not merely a recommendation but a critical component of a successful cloud migration strategy. This plan acts as a safety net, providing a structured approach to revert to a stable, pre-migration state in the event of a failure, thereby minimizing downtime and mitigating potential damage.
This comprehensive guide dissects the essential elements of crafting and implementing an effective rollback plan. We will explore the core principles, from understanding the need for a rollback to detailed procedures for data, infrastructure, and application rollback. The focus will be on practical strategies, testing methodologies, and automation techniques to ensure that your cloud migration is not only successful but also resilient against potential setbacks.
By meticulously planning and executing these steps, organizations can confidently navigate the complexities of cloud migration while safeguarding their critical assets.
Understanding the Need for a Rollback Plan
A rollback plan is a critical component of any cloud migration strategy, serving as a contingency mechanism to revert to a pre-migration state in the event of unforeseen issues. It provides a structured approach to minimize downtime, data loss, and reputational damage, safeguarding business continuity during the transition to the cloud. Without a well-defined rollback plan, organizations expose themselves to significant risks that can jeopardize the entire migration project.
Critical Role in Risk Mitigation
A rollback plan actively mitigates the inherent risks associated with cloud migration, which can involve complex technical challenges, data integrity issues, and unforeseen compatibility problems. It’s not merely a reactive measure; it’s a proactive strategy to manage potential failures.
Potential Failure Scenarios During Cloud Migration
Cloud migrations are complex undertakings, and several failure scenarios can necessitate a rollback. The following represent common areas where problems may arise, each potentially requiring a reversion to the original state:
- Data Migration Issues: Problems during data transfer, such as corruption, loss, or incompatibility with the target cloud environment, can render migrated data unusable. For example, a large financial institution migrating terabytes of customer transaction data might experience data corruption due to network interruptions during the transfer process, leading to inaccurate account balances and transaction histories.
- Application Compatibility Problems: Applications may not function correctly in the new cloud environment due to software version conflicts, missing dependencies, or differences in infrastructure configuration. Consider a scenario where a critical CRM application, migrated to the cloud, fails to integrate with existing on-premises systems due to incompatible APIs, resulting in disruptions to sales and customer service operations.
- Performance Degradation: The cloud environment might not deliver the expected performance levels, leading to slower application response times or insufficient resource allocation. This can occur due to incorrect sizing of virtual machines or network bottlenecks. An e-commerce website, experiencing a sudden surge in traffic after migration, might find its cloud infrastructure unable to handle the load, leading to slow page loading times and frustrated customers.
- Security Breaches: Security vulnerabilities can be inadvertently introduced during migration, leading to data breaches or unauthorized access. This might be due to misconfigured security settings or the failure to properly implement security controls in the cloud environment. A healthcare provider, migrating patient data to the cloud, could experience a data breach if access controls are not correctly configured, exposing sensitive patient information.
- Network Connectivity Problems: Network connectivity issues between on-premises systems and the cloud environment can prevent applications from functioning correctly. This can be caused by misconfigured network settings or insufficient bandwidth. A manufacturing company, relying on a cloud-based supply chain management system, might face disruptions if network connectivity to the cloud is unstable, leading to delays in production and deliveries.
- Cost Overruns: Unexpectedly high cloud costs can render the migration financially unsustainable. This might result from poor resource management or unforeseen charges. A small business, migrating its IT infrastructure to the cloud, might face significant cost overruns if it fails to properly monitor and optimize its cloud resource usage, leading to budget constraints.
Consequences of Not Having a Rollback Plan
The absence of a rollback plan exposes an organization to a range of severe consequences, potentially including:
- Prolonged Downtime: Without a rollback plan, resolving issues can take significantly longer, leading to extended periods of system downtime, impacting business operations. For instance, if a critical application fails during migration, the IT team may spend considerable time troubleshooting the issue without a plan to revert to the previous functional state, potentially causing several days of system unavailability.
- Data Loss or Corruption: Without a mechanism to restore data from backups or revert to a previous state, data loss or corruption is a significant risk. Imagine a scenario where a database migration fails and corrupts the primary database; without a rollback plan, the organization might face significant data loss and recovery efforts.
- Reputational Damage: System failures and data breaches can severely damage an organization’s reputation, leading to loss of customer trust and negative publicity. A major airline, experiencing a system outage due to a failed cloud migration, could face significant customer dissatisfaction and media scrutiny.
- Financial Losses: Downtime, data loss, and reputational damage can translate into significant financial losses, including lost revenue, remediation costs, and potential legal liabilities. A financial services company, experiencing a major system outage due to a failed cloud migration, could incur substantial financial losses due to disrupted transactions and customer service issues.
- Business Disruption: The inability to revert to a stable state can severely disrupt business operations, impacting productivity, customer service, and overall business continuity. A retail company, experiencing a point-of-sale system outage due to a failed cloud migration, might be unable to process customer transactions, leading to significant disruption to its operations.
Defining Scope and Objectives
The establishment of a robust rollback plan is predicated on a clear understanding of its boundaries and intended outcomes. This section meticulously Artikels the process of defining the scope of the rollback, identifying the systems and data encompassed, and subsequently elucidating the objectives, with a focus on minimizing disruption. Prioritization strategies, based on criticality, will also be explored to ensure the most critical components are addressed first.
Identifying Rollback Scope: Systems and Data
Defining the precise scope of the rollback plan is crucial for its efficacy. It necessitates a comprehensive inventory of all systems and data that are subject to migration. This involves a detailed assessment of interdependencies and potential points of failure.
- System Categorization: Categorize systems based on their functionality, such as core business applications, infrastructure services (e.g., databases, networking), and supporting services. This categorization aids in understanding the impact of a rollback on different areas of the business. For instance, a customer relationship management (CRM) system would be considered a core business application, while a monitoring system would be categorized as a supporting service.
- Data Mapping: Perform a thorough data mapping exercise. Identify all data sources, including databases, file systems, and cloud storage, along with their associated data flows and dependencies. This process ensures that all data required for a successful rollback is accounted for. For example, data might be stored in a relational database (e.g., PostgreSQL, MySQL), NoSQL database (e.g., MongoDB, Cassandra), or object storage (e.g., Amazon S3, Azure Blob Storage).
- Dependency Analysis: Analyze the dependencies between systems and data components. This helps in understanding the cascading effects of a rollback. For instance, a failure in the authentication system might impact multiple downstream applications.
- Impact Assessment: Evaluate the potential impact of a rollback on each system and data component. This includes considering the duration of the rollback, potential data loss, and the business impact. For example, a rollback of a financial transaction system would have a significantly higher business impact than a rollback of a reporting system.
- Define Rollback Boundaries: Clearly define the boundaries of the rollback plan, specifying which systems and data are included and excluded. This ensures that the plan is focused and manageable. For example, the rollback plan might only cover the migration of specific applications and data, while excluding the migration of the underlying infrastructure.
Defining Rollback Objectives: Minimizing Downtime and Data Loss
The primary objectives of a rollback plan are to minimize downtime and data loss. These objectives are achieved through careful planning, implementation, and testing. The design should also focus on the potential consequences of data loss, downtime, and the strategies employed to mitigate them.
- Minimize Downtime: Downtime directly translates to lost revenue and productivity. The rollback plan should be designed to minimize the duration of the rollback process.
- Minimize Data Loss: Data loss can have severe consequences, including regulatory penalties, reputational damage, and loss of customer trust. The rollback plan must incorporate measures to prevent data loss, such as regular backups, data replication, and version control.
- Recovery Time Objective (RTO): Define a Recovery Time Objective (RTO) for each system. RTO represents the maximum acceptable downtime for a system. The rollback plan should be designed to achieve the defined RTOs.
- Recovery Point Objective (RPO): Define a Recovery Point Objective (RPO) for each system. RPO represents the maximum acceptable data loss, measured in time. The rollback plan should be designed to meet the defined RPOs.
- Data Consistency: Ensure data consistency during the rollback process. This involves validating data integrity and ensuring that all data is restored to a consistent state.
- Testing and Validation: Thoroughly test and validate the rollback plan to ensure that it meets the defined objectives. This includes performing regular rollback drills to simulate real-world scenarios.
Prioritizing Rollback Procedures: Criticality-Based Approach
Prioritizing rollback procedures is essential to ensure that the most critical systems and data are restored first, minimizing the overall impact of the migration failure. A criticality-based approach ensures that resources are allocated efficiently and that the most important business functions are restored promptly.
- Criticality Assessment: Assess the criticality of each system and data component based on factors such as business impact, revenue generation, and regulatory requirements. This assessment should involve input from business stakeholders and technical experts. For example, a system that processes financial transactions would be considered more critical than a system that generates reports.
- Prioritization Matrix: Develop a prioritization matrix to rank systems and data components based on their criticality. This matrix should consider factors such as the potential impact of downtime, the sensitivity of the data, and the recovery time objective (RTO).
- Tiered Rollback Strategy: Implement a tiered rollback strategy, where systems and data components are rolled back in order of their criticality. This ensures that the most critical systems are restored first, minimizing the overall business impact.
- Dependencies and Sequencing: Account for dependencies between systems when prioritizing rollback procedures. Rollback procedures for dependent systems must be sequenced correctly to avoid cascading failures.
- Automated Rollback Procedures: Automate rollback procedures for critical systems to reduce the time required for the rollback and minimize the risk of human error. Automation can involve the use of scripts, tools, and orchestration platforms.
- Regular Review and Updates: Regularly review and update the prioritization matrix and rollback procedures to reflect changes in business requirements and system configurations. This ensures that the rollback plan remains effective over time.
Pre-Migration Planning and Preparation
Pre-migration planning and preparation are critical for a successful cloud migration and a smooth rollback process. This phase involves meticulous planning and execution of tasks designed to minimize risk and ensure a swift return to the pre-migration state if necessary. Proper preparation allows for rapid identification and resolution of issues during migration, enhancing overall resilience.
Data Backups and Snapshot Creation
Comprehensive data backups and snapshot creation are foundational elements of a robust rollback strategy. These measures safeguard against data loss and facilitate a quick restoration to the pre-migration environment. The frequency and scope of backups and snapshots must be determined based on the Recovery Point Objective (RPO) and Recovery Time Objective (RTO).Data backups involve creating copies of all critical data, including databases, application configurations, and user data.
These backups should be stored in a geographically diverse location to protect against regional outages. Snapshots, on the other hand, capture the state of a system at a specific point in time. They are generally faster to create and restore than full backups, making them suitable for frequent backups and quick rollbacks.
- Backup Strategies: Several backup strategies can be employed, each with its advantages and disadvantages.
- Full Backups: Involve backing up all data at once. They provide a complete recovery point but are time-consuming.
- Incremental Backups: Back up only the data that has changed since the last backup (full or incremental). They are faster than full backups but require a chain of backups for complete restoration.
- Differential Backups: Back up the data that has changed since the last full backup. They are faster than full backups but slower than incremental backups.
- Snapshot Strategies: Snapshot creation is a common feature in cloud environments, providing a point-in-time view of data.
- Volume Snapshots: Capture the state of a storage volume.
- Database Snapshots: Capture the state of a database at a specific point in time.
- Application-Aware Snapshots: Snapshots that are designed to take into account the specific needs of the application.
- Example: Consider a retail company migrating its e-commerce platform to the cloud. Before migration, they would create full backups of their databases, file systems, and application configurations. They would also take volume snapshots of their production servers. These backups and snapshots would be stored in a separate region to ensure data availability in case of a regional outage.
- Formula: The optimal backup frequency can be calculated using the following formula:
Backup Frequency = (RPO) / (Average Time to Perform Backup)
Pre-Migration Checklist
A comprehensive checklist ensures that all necessary steps are completed before initiating the cloud migration. This checklist should be meticulously followed to minimize risks and streamline the rollback process. Each item on the checklist should be verified and documented to ensure accountability and facilitate troubleshooting.
- Environment Assessment:
- Verify that all existing on-premises systems are inventoried, documented, and understood.
- Assess the dependencies between applications and systems.
- Identify any compatibility issues between on-premises systems and the cloud environment.
- Cloud Environment Setup:
- Configure the cloud environment, including virtual networks, security groups, and storage.
- Ensure that the cloud environment is properly sized to accommodate the migrated workloads.
- Implement security measures, such as identity and access management (IAM) and network security.
- Data Preparation:
- Migrate data to the cloud, including databases, files, and applications.
- Validate data integrity after migration.
- Implement data synchronization mechanisms to keep data consistent between on-premises and cloud environments during migration.
- Testing and Validation:
- Conduct thorough testing of the migrated applications and systems in the cloud environment.
- Verify that all applications and systems function as expected.
- Test the rollback plan to ensure its effectiveness.
- Documentation:
- Document all migration steps, including configurations, dependencies, and troubleshooting procedures.
- Document the rollback plan, including the steps to be taken and the roles and responsibilities.
- Communication Plan:
- Establish clear communication channels and escalation paths.
- Inform all stakeholders about the migration plan and the rollback plan.
Communication Channels and Escalation Paths
Establishing clear communication channels and well-defined escalation paths is crucial for effective rollback execution. These communication structures facilitate rapid information flow, enabling swift decision-making and issue resolution.
- Communication Channels:
- Primary Channel: A dedicated communication channel, such as a chat room or a shared document, should be established for real-time updates and discussions.
- Secondary Channels: Email and phone calls should be used for less urgent communications and formal documentation.
- Escalation Paths:
- Tier 1: Initial point of contact for issues, responsible for basic troubleshooting and initial assessment.
- Tier 2: Experts who can provide in-depth analysis and implement solutions.
- Tier 3: Senior management or stakeholders who can authorize decisions and allocate resources.
- Communication Plan Elements:
- Contact List: A comprehensive list of contacts, including names, roles, and contact information, should be readily available.
- Issue Reporting Template: A standardized template for reporting issues, including details about the issue, impact, and steps taken to resolve it.
- Regular Status Updates: Scheduled updates to keep stakeholders informed of progress, issues, and risks.
- Example: Consider a scenario where an application is experiencing performance issues after migration. The monitoring system detects the issue and alerts the Tier 1 support team. If the Tier 1 team cannot resolve the issue, they escalate it to the Tier 2 team, which includes application and infrastructure specialists. If the Tier 2 team cannot resolve the issue within a specified timeframe, the issue is escalated to the Tier 3 team, which may involve the project manager and senior IT management.
This escalation process ensures that critical issues are addressed promptly and effectively.
Data Backup and Recovery Strategies
Effective data backup and recovery strategies are critical for a successful cloud migration rollback. These strategies ensure that in the event of issues during or after migration, data can be restored to a previous, known-good state, minimizing downtime and data loss. The selection of appropriate backup methods, thorough testing, and data integrity verification are all essential components of a robust rollback plan.
Data Backup Methods for Cloud Environments
Various data backup methods are suitable for cloud environments, each with its own advantages and disadvantages regarding cost, recovery time objective (RTO), and recovery point objective (RPO). Selecting the right method or combination of methods depends on the specific requirements of the application and the criticality of the data.
- Snapshot-Based Backups: This method captures a point-in-time copy of the data, typically stored within the cloud provider’s infrastructure. Snapshots are often quick to create and recover, making them suitable for frequently changing data. They provide a low RTO and RPO. However, snapshots may not be suitable for long-term archiving.
- Object Storage Backups: Data is backed up to object storage, often utilizing cloud-native services like Amazon S3, Azure Blob Storage, or Google Cloud Storage. Object storage offers high durability, scalability, and cost-effectiveness, making it suitable for both short-term and long-term backups. The RTO and RPO can vary depending on the retrieval method used.
- Database-Specific Backups: Database systems often provide their own backup and recovery mechanisms, such as logical backups, physical backups, and transaction log backups. These methods allow for granular control over the backup process and enable point-in-time recovery. The choice depends on the database type and the specific requirements.
- Application-Aware Backups: These backups understand the application’s data structure and dependencies. They can perform consistent backups of complex applications, ensuring that data is recovered in a consistent state. This can involve pausing application writes during the backup process.
- Hybrid Backups: This approach combines on-premises backups with cloud-based backups. This can offer redundancy and flexibility, allowing for faster local recovery while also providing offsite protection against disasters. Hybrid backups are especially relevant during cloud migration as they allow data to be backed up both in the source and target environments.
Testing Data Recovery Procedures
Rigorous testing of data recovery procedures is essential to validate the effectiveness of the rollback plan. Regular testing ensures that the recovery process functions as expected and that recovery time objectives (RTOs) and recovery point objectives (RPOs) can be met. Testing should be performed at regular intervals and after any significant changes to the infrastructure or backup configuration.
- Recovery Simulations: These simulations involve restoring data from backups to a test environment. The restored data is then validated to ensure its integrity and consistency. Simulations should mimic real-world failure scenarios to assess the recovery process.
- Full System Recovery Tests: These tests involve restoring an entire system from backups, including operating systems, applications, and data. These tests provide a comprehensive evaluation of the recovery process and identify any potential issues. They are typically performed less frequently due to the time and resources required.
- Failover Testing: Failover testing involves simulating a failure in the production environment and verifying that the system automatically fails over to the backup environment. This test validates the failover mechanism and ensures that the system remains available during a failure.
- Documentation Review: Reviewing and updating the recovery documentation is critical. This ensures that the documentation accurately reflects the current environment and recovery procedures. Documentation should be clear, concise, and easily accessible.
- Performance Evaluation: Performance should be measured during the recovery process, focusing on how quickly the data is restored and the performance of the restored system. Metrics such as recovery time and data transfer rates should be tracked and compared to established benchmarks.
Verifying the Integrity of Backed-Up Data
Verifying the integrity of backed-up data is a crucial step to ensure that the data is recoverable and consistent. This process involves checking the data for corruption, verifying its consistency with the source data, and validating that the data is in a usable state. Several methods can be used to verify data integrity.
- Checksum Verification: Checksums are used to detect data corruption. After the backup, a checksum is calculated for the backed-up data and compared to the checksum of the original data. If the checksums do not match, it indicates data corruption. Popular checksum algorithms include MD5, SHA-1, and SHA-256.
- Data Validation: Data validation involves checking the data for consistency and completeness. This can involve verifying that the data conforms to specific data types, formats, and constraints. Data validation can be performed using database queries, data analysis tools, or custom scripts.
- Restoration and Verification: Restoring a sample of the backed-up data to a test environment and verifying its usability is a key component of data integrity verification. This process allows for testing of the recovery process and ensures that the data can be successfully recovered.
- Metadata Verification: Metadata associated with the data, such as file names, timestamps, and permissions, should be verified to ensure its integrity. This verification ensures that the data is correctly associated with its metadata and that the metadata has not been corrupted.
- Regular Auditing: Implement regular auditing of the backup and recovery processes. Auditing includes reviewing logs, monitoring performance metrics, and verifying the integrity of the backups. This ensures that the backup and recovery processes are functioning correctly and that any issues are identified and addressed promptly.
Infrastructure Rollback Procedures
Implementing a comprehensive infrastructure rollback plan is crucial for mitigating risks associated with cloud migration. This plan provides a systematic approach to revert changes and restore the pre-migration state, ensuring business continuity and minimizing downtime. It involves detailed procedures, automation strategies, and validation steps to guarantee a smooth and efficient rollback process.
Reverting Infrastructure Changes
The ability to revert infrastructure changes is paramount in a cloud migration rollback. This involves a methodical approach to undoing deployments, configurations, and modifications made during the migration process.
- Virtual Machine (VM) Rollback: This involves restoring VMs to their pre-migration state. This can be achieved by:
- Restoring from Backups: Utilize the data backups created during the pre-migration phase to restore VMs. The specific method depends on the cloud provider and the backup strategy employed. For example, Amazon Web Services (AWS) offers Amazon Machine Images (AMIs) that can be used to quickly restore EC2 instances.
Azure uses Azure Virtual Machine backups, and Google Cloud offers snapshots.
- Re-deploying from Configuration Management: If configuration management tools like Ansible, Chef, or Puppet were used to provision the VMs in the cloud, the same tools can be used to redeploy the VMs in the original on-premises environment or a designated rollback environment. This involves applying the pre-migration configuration scripts.
- Data Synchronization: Ensure that data changes that occurred in the cloud environment after the migration are synchronized back to the original on-premises environment or a rollback environment. This may involve using database replication tools or data synchronization services.
- Restoring from Backups: Utilize the data backups created during the pre-migration phase to restore VMs. The specific method depends on the cloud provider and the backup strategy employed. For example, Amazon Web Services (AWS) offers Amazon Machine Images (AMIs) that can be used to quickly restore EC2 instances.
- Network Configuration Rollback: Network configurations, such as virtual private networks (VPNs), firewalls, and load balancers, must be reverted. This includes:
- Reverting VPN Connections: Re-establish VPN connections to the on-premises environment by reconfiguring the cloud-based VPN gateways and reverting any changes made to on-premises firewalls.
- Reconfiguring Firewalls: Revert firewall rules to their pre-migration state, ensuring that traffic flows correctly between the on-premises environment and the cloud environment. This involves disabling any new rules created during the migration and re-enabling the original rules.
- Restoring Load Balancers: Reconfigure load balancers to direct traffic back to the on-premises servers or a designated rollback environment. This may involve updating DNS records to point to the on-premises IP addresses.
- Storage Rollback: Revert storage changes, including data migration and storage configuration. This involves:
- Data Synchronization: If data was migrated to cloud storage, synchronize any changes back to the on-premises storage. Tools such as rsync or cloud-specific synchronization services can be used.
- Reverting Storage Configurations: Reconfigure storage services to point to the original on-premises storage locations.
Restoring Cloud Resources to Pre-Migration State
A step-by-step guide is essential for restoring cloud resources to their pre-migration state, ensuring a controlled and efficient rollback process. This guide should be documented, tested, and readily available to the migration team.
- Initiate Rollback: Declare the rollback and assemble the rollback team. This team should consist of personnel with expertise in infrastructure, networking, databases, and applications.
- Communication: Communicate the rollback initiation to all stakeholders, including business users, application owners, and IT support teams. Provide regular updates on the rollback progress.
- Decommission Cloud Resources: Stop all running cloud resources and deprovision any new resources created during the migration. This may include stopping VMs, disabling network services, and terminating cloud services.
- Restore Data: Restore data to the pre-migration environment.
- Database Restoration: Restore databases from backups to the on-premises environment or a designated rollback environment. This may involve using database-specific tools to restore from backup files.
- File System Restoration: Restore file systems from backups using the appropriate tools and procedures.
- Reconfigure Network: Reconfigure the network to direct traffic back to the pre-migration environment.
- DNS Updates: Update DNS records to point to the original on-premises IP addresses or the rollback environment.
- Firewall Rules: Revert firewall rules to their pre-migration state.
- VPN Re-establishment: Re-establish VPN connections to the on-premises environment.
- Re-establish Applications: Start and test applications in the pre-migration environment or the rollback environment.
- Application Testing: Thoroughly test applications to ensure functionality and data integrity.
- User Validation: Verify that users can access applications and data.
- Verification: Verify the success of the rollback.
- System Monitoring: Monitor systems and applications to ensure they are functioning correctly.
- Performance Testing: Perform performance testing to validate that performance meets pre-migration standards.
- Finalize Rollback: Once the rollback is complete and validated, finalize the process by decommissioning cloud resources and documenting the rollback procedure.
Automating Infrastructure Rollback
Automating the infrastructure rollback process significantly reduces the time and effort required to revert to the pre-migration state. This automation also minimizes the potential for human error and improves the reliability of the rollback.
- Scripting: Utilize scripting languages like Python, Bash, or PowerShell to automate rollback tasks.
- VM Restoration Scripts: Develop scripts to automate the restoration of VMs from backups or the re-deployment of VMs using configuration management tools.
- Network Configuration Scripts: Create scripts to automate network configuration changes, such as updating firewall rules, configuring VPN connections, and modifying DNS records.
- Data Synchronization Scripts: Develop scripts to synchronize data between the cloud environment and the on-premises environment or the rollback environment.
- Infrastructure as Code (IaC) Tools: Employ IaC tools such as Terraform, AWS CloudFormation, Azure Resource Manager, or Google Cloud Deployment Manager to automate the rollback process. IaC tools enable the definition and management of infrastructure in code, making it easier to revert infrastructure changes.
- Version Control: Utilize version control systems like Git to manage IaC code, enabling the ability to revert to previous versions of infrastructure configurations.
- Automated Deployment: Automate the deployment of infrastructure configurations to the on-premises environment or a rollback environment.
- Orchestration Tools: Integrate orchestration tools, such as Jenkins, GitLab CI/CD, or Azure DevOps, to automate the entire rollback workflow.
- Rollback Pipelines: Create rollback pipelines that automate the execution of scripts and IaC templates.
- Automated Testing: Integrate automated testing into the rollback pipeline to validate the rollback process.
- Examples:
- Terraform Example: A Terraform script can be used to destroy all cloud resources created during the migration. Then, a separate Terraform script can be used to redeploy the resources in the on-premises environment, using the original configuration files.
- Ansible Example: Ansible playbooks can be used to restore the VMs to their original state by re-running the configuration management playbooks, which were used to configure the VMs during the initial migration.
Application Rollback Strategies
Application rollback strategies are critical for ensuring business continuity during cloud migrations. A well-defined plan minimizes downtime and data loss by enabling a swift return to a stable application state when issues arise. This section focuses on methods for rolling back application deployments, providing guidance on deploying previous versions and testing rollback procedures.
Methods for Rolling Back Application Deployments, Including Version Control
Effective application rollback relies heavily on robust version control systems and well-defined deployment strategies. These systems and strategies allow for the management of application code, configurations, and dependencies, ensuring a reliable mechanism to revert to a known-good state.
- Version Control Systems: Utilizing a version control system (e.g., Git, Subversion) is paramount. These systems track changes to code, enabling easy identification of specific versions. Every deployment should be tagged or associated with a specific commit to facilitate rollback.
- Immutable Infrastructure: Implementing immutable infrastructure, where servers are replaced rather than modified, streamlines rollback. This approach minimizes configuration drift and ensures consistency between different application versions. For example, using tools like Docker or Kubernetes, the entire application stack (code, dependencies, and configuration) is packaged as a container or pod, making it easier to deploy and rollback.
- Blue/Green Deployments: This deployment strategy involves maintaining two identical environments: blue (live) and green (staging). New application versions are deployed to the green environment, tested, and then traffic is switched from blue to green. If issues arise, traffic can be quickly switched back to the blue environment. This strategy offers zero-downtime rollback.
- Canary Deployments: Canary deployments involve deploying a new application version to a small subset of users (the “canary”) to test its performance in a production environment. If the canary deployment is successful, the new version is gradually rolled out to all users. If failures occur, the traffic to the canary deployment can be reverted.
- Configuration Management: Employing configuration management tools (e.g., Ansible, Chef, Puppet) allows for versioning and management of application configurations. This ensures that the application’s environment can be consistently recreated, facilitating rollback.
Guide for Deploying Previous Application Versions in Case of Failures
A step-by-step guide is crucial for a successful application rollback. This guide provides clear instructions to minimize errors and ensure a quick return to a functional state. The specific steps will vary depending on the chosen deployment strategy and infrastructure.
- Identify the Issue: Determine the root cause of the failure. This might involve monitoring logs, error messages, and performance metrics.
- Identify the Last Known Good Version: Determine the version of the application that was functioning correctly before the failure. This information is typically available within the version control system.
- Rollback Procedure (Based on Deployment Strategy):
- Blue/Green: Switch the traffic back to the blue environment.
- Canary: Disable the canary deployment and redirect traffic to the previous stable version.
- Immutable Infrastructure: Redeploy the previous application version from the version control system using the existing infrastructure provisioning tools.
- Traditional Deployments: Rollback the application code and configuration to the previous version. This often involves redeploying the application binaries and reverting database schema changes.
- Revert Database Schema Changes (If Applicable): If the application deployment included database schema changes, it may be necessary to revert those changes to maintain compatibility with the previous application version. This might involve running rollback scripts or restoring a database backup.
- Monitor the Rolled-Back Application: After the rollback, closely monitor the application’s performance, error rates, and user experience to ensure that it is functioning correctly.
- Investigate the Failure: Once the application is stable, investigate the root cause of the failure to prevent similar issues in the future. This investigation should include reviewing logs, monitoring data, and application code.
Demonstrate How to Test Application Rollback Procedures
Thorough testing of rollback procedures is essential to ensure their effectiveness. This testing should occur regularly and should simulate various failure scenarios to validate the rollback process.
- Simulate Failure Scenarios: Create realistic failure scenarios to test the rollback process. Examples include:
- Deployment errors.
- Performance degradation.
- Data corruption.
- Security vulnerabilities.
- Automated Testing: Automate the rollback testing process as much as possible. This ensures that the rollback procedures are consistently tested and validated.
- Testing Tools: Utilize testing tools to automate various aspects of the rollback process, such as verifying the correct application version, testing data integrity, and validating the system’s functionality.
- Regular Drills: Conduct regular rollback drills to familiarize the operations team with the rollback procedures. This allows for practice and refinement of the process.
- Document Test Results: Document the results of each test, including the steps taken, the outcome, and any lessons learned. This documentation helps in identifying areas for improvement.
- Example Scenario: Consider a scenario where a new application deployment introduces a critical bug that causes a significant increase in error rates. The rollback procedure would involve:
- Detecting the increased error rate through monitoring.
- Identifying the problematic application version.
- Initiating the rollback process, which might involve reverting to the previous application version using a blue/green deployment strategy.
- Monitoring the application after the rollback to ensure that the error rate returns to normal.
Data Rollback Procedures
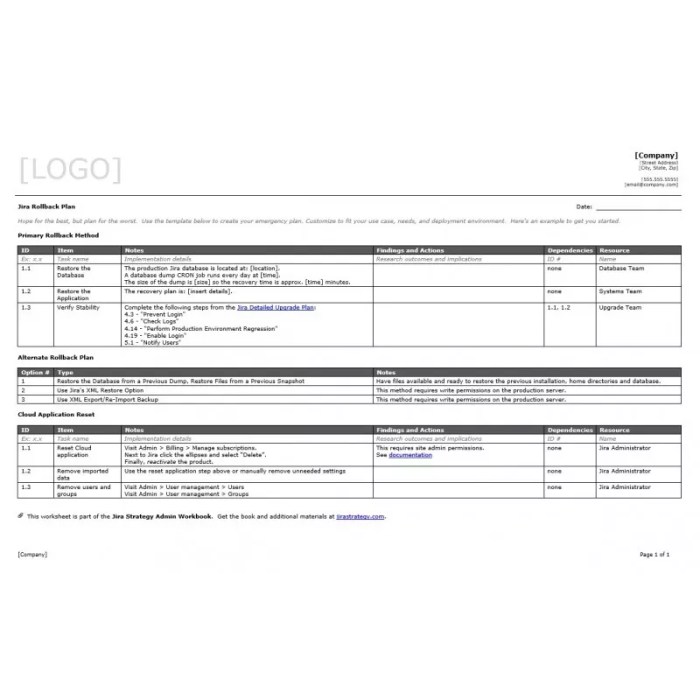
Data rollback is a critical component of any cloud migration rollback plan. The ability to restore data to its pre-migration state quickly and accurately minimizes downtime and data loss, ensuring business continuity. This section Artikels the procedures, considerations, and validation steps required for a successful data rollback.
Restoring Data to Pre-Migration State
The process of restoring data to its pre-migration state depends on the chosen data backup and recovery strategies. The method selected should align with the Recovery Time Objective (RTO) and Recovery Point Objective (RPO) defined during the planning phase.
- Identifying the Source of Truth: Determine the definitive source of the pre-migration data. This is typically the original on-premises or previous cloud environment. Verify the integrity of this source before initiating the rollback.
- Data Restoration from Backups: This is the most common method.
- Select the appropriate backup: Choose the backup snapshot or archive created before the migration or at a defined checkpoint. Consider the timestamp of the backup and the RPO to ensure data consistency.
- Restore to the target environment: Restore the data to the original on-premises or previous cloud environment. This may involve restoring databases, file systems, and other data repositories. The restoration process should follow a well-defined procedure documented during the pre-migration phase.
- Data Synchronization: In scenarios where data has been actively changing during the migration or immediately after the migration, consider the data synchronization strategies to reconcile changes.
- Identify data changes: Track any data modifications that occurred in both the source and the target environments after the initial backup.
- Apply delta changes: Apply these changes to the restored data to ensure the pre-migration state reflects the most recent data.
- Database-Specific Procedures: Database rollback often requires specific steps depending on the database system (e.g., MySQL, PostgreSQL, Oracle).
- Utilize database backup tools: Employ database-specific backup and restore utilities.
- Restore transaction logs: Apply transaction logs (e.g., redo logs, transaction logs) to the restored database to recover to a specific point in time, minimizing data loss.
- Test the database: Verify the database integrity and functionality after restoration.
- File System Restoration: File systems require a specific approach to restoring data.
- Restore from backups: Restore file system data from the chosen backup source.
- Maintain file permissions and attributes: Ensure file permissions, ownership, and other attributes are preserved during the restoration process.
- Test the file system: Verify the restored file system contains the expected data and that all files are accessible.
Handling Data Inconsistencies During Rollback
Data inconsistencies can arise during rollback due to several factors, including data changes that occurred in both the source and target environments during the migration process, network latency, or application-level issues. Implementing strategies to manage these inconsistencies is crucial.
- Conflict Detection and Resolution: Implement conflict detection mechanisms to identify data discrepancies between the source and target environments.
- Use conflict detection tools: Employ tools that compare data across different environments to identify inconsistencies.
- Define conflict resolution policies: Establish clear policies for resolving data conflicts, such as prioritizing data from the source environment or using a merge strategy.
- Data Reconciliation: Data reconciliation involves bringing inconsistent data into a consistent state.
- Manual reconciliation: Involve manual data review and reconciliation, especially for complex data conflicts.
- Automated reconciliation: Utilize scripts or tools to automate data reconciliation based on predefined rules.
- Data Transformation: Data transformation might be needed to reconcile data format, data types, or data structures between the source and target environments.
- Implement data mapping: Create data mapping rules to transform data from the target environment to align with the source environment’s data format.
- Apply transformation scripts: Use transformation scripts or ETL (Extract, Transform, Load) processes to apply data transformations.
- Database Transactions: Implement database transactions to ensure data consistency during the rollback process.
- Use ACID properties: Ensure the rollback process adheres to the ACID (Atomicity, Consistency, Isolation, Durability) properties to guarantee data integrity.
- Implement rollback transactions: Use database transaction rollback features to revert data changes that have not been committed.
- Auditing and Logging: Implement auditing and logging to track data changes and reconciliation activities.
- Maintain audit trails: Create audit trails to track all data modifications and reconciliation steps.
- Analyze logs: Analyze logs to identify the root causes of data inconsistencies and to improve the rollback process.
Validating Data Restoration
Data validation is essential to ensure that the rollback was successful and that the restored data is accurate and complete. This involves performing several checks and tests to verify the data’s integrity.
- Data Comparison: Perform data comparison between the restored data and the pre-migration data.
- Use data comparison tools: Employ data comparison tools to compare data across different environments.
- Compare data sets: Compare data sets at the table, record, or field level.
- Verify data integrity: Verify data integrity by comparing checksums, hash values, or other data integrity checks.
- Functional Testing: Conduct functional tests to ensure the restored data supports the application’s functionality.
- Execute test cases: Run test cases to verify application functionality, data retrieval, and data modification.
- Validate data access: Verify data access permissions and access control mechanisms.
- Performance Testing: Performance testing should be performed to ensure that the restored data supports the application’s performance requirements.
- Measure performance metrics: Measure response times, transaction throughput, and resource utilization.
- Compare performance metrics: Compare the performance metrics of the restored data with the pre-migration performance metrics.
- Data Sampling: Perform data sampling to verify the integrity of large datasets.
- Select sample data: Select a representative sample of data from the restored data.
- Verify sample data: Verify the sample data for accuracy and completeness.
- User Acceptance Testing (UAT): Involve users in testing the restored data.
- Conduct UAT: Conduct UAT to ensure the restored data meets user requirements.
- Gather user feedback: Gather user feedback to identify any data-related issues or inconsistencies.
Testing and Validation
Rigorous testing and validation are crucial to ensure the cloud migration rollback plan functions as designed and meets its objectives. This phase involves systematically evaluating the plan’s efficacy under various simulated failure conditions. It allows for identifying weaknesses, refining procedures, and building confidence in the organization’s ability to revert to the pre-migration state quickly and efficiently. This section details the design, execution, and documentation of these critical tests.
Designing a Testing Strategy for Rollback Plan Effectiveness
A well-defined testing strategy is essential for validating the rollback plan. It should encompass a variety of test types, each targeting specific aspects of the rollback process. The strategy must also consider the scope, objectives, and potential risks associated with the migration.
- Test Levels: A tiered approach should be implemented, starting with unit tests to validate individual components, progressing to integration tests to verify the interaction between components, and culminating in system tests that simulate the entire rollback process.
- Test Types: Various testing methodologies should be utilized.
- Functional Testing: Verifies that the rollback process correctly restores the pre-migration functionality of the applications and infrastructure.
- Performance Testing: Assesses the speed and efficiency of the rollback process, including the time required to restore data and services. Performance metrics should be compared against predefined Service Level Agreements (SLAs).
- Security Testing: Ensures that the rollback process does not introduce any new security vulnerabilities and that sensitive data is protected during the rollback.
- Disaster Recovery Testing: Simulates various failure scenarios, such as data corruption, network outages, or hardware failures, to validate the effectiveness of the rollback plan in different adverse conditions.
- Test Data: Realistic test data that mirrors the production environment should be used to accurately simulate real-world scenarios. This data should be representative of the volume, complexity, and characteristics of the production data. Data masking techniques should be employed to protect sensitive information.
- Test Environment: A dedicated, isolated test environment that closely resembles the production environment is crucial for performing testing without impacting live systems. This environment should include copies of the applications, databases, and infrastructure components.
- Test Cases: Detailed test cases should be developed, outlining the steps required to execute each test, the expected results, and the pass/fail criteria. Test cases should be documented comprehensively and regularly reviewed and updated to reflect changes in the migration plan or environment.
- Automation: Automation should be leveraged wherever possible to streamline the testing process, reduce manual effort, and improve the accuracy and consistency of testing. Automated testing tools can be used to execute tests, collect data, and generate reports.
- Frequency: Testing should be conducted regularly, including before the migration, after any significant changes to the migration plan, and at least annually to ensure the rollback plan remains effective.
Creating a Framework for Simulating Failure Scenarios
Simulating failure scenarios is vital to validate the rollback process under various adverse conditions. A robust framework should be established to replicate potential failures, ensuring the plan’s resilience. This framework should incorporate various techniques to mimic real-world issues.
- Failure Scenarios: A comprehensive set of failure scenarios should be defined, covering a wide range of potential issues.
- Data Corruption: Simulate data corruption in databases or storage systems using tools that introduce errors into the data.
- Network Outages: Simulate network failures by disconnecting network connections or simulating network latency and packet loss.
- Hardware Failures: Simulate hardware failures by shutting down virtual machines, storage devices, or network components.
- Application Errors: Simulate application crashes, errors, or performance degradation by introducing code errors or resource exhaustion.
- Security Breaches: Simulate security breaches by attempting unauthorized access to systems or data.
- Human Error: Simulate human errors, such as accidental data deletion or configuration mistakes.
- Simulation Tools: Appropriate tools should be selected to simulate each failure scenario.
- Chaos Engineering Tools: These tools are designed to intentionally introduce failures into systems to test their resilience. Examples include Chaos Monkey, Gremlin, and Chaos Mesh.
- Network Emulators: Tools like NetEm can simulate network latency, packet loss, and other network conditions.
- Data Corruption Tools: Tools that corrupt data can be used to simulate data corruption in databases or storage systems.
- Virtualization Tools: Virtualization platforms can be used to simulate hardware failures by shutting down virtual machines or simulating resource exhaustion.
- Scenario Execution: The execution of each failure scenario should follow a structured approach.
- Preparation: The test environment should be prepared by creating a copy of the production environment, installing the necessary tools, and configuring the test data.
- Injection: The failure scenario should be injected into the test environment using the appropriate tools.
- Observation: The system’s behavior should be observed during the failure scenario, including monitoring logs, metrics, and performance data.
- Rollback Execution: The rollback process should be initiated and executed to restore the system to its pre-migration state.
- Verification: The system’s functionality and data integrity should be verified after the rollback process is complete.
- Monitoring and Logging: Comprehensive monitoring and logging should be implemented to capture detailed information about the failure scenarios and the rollback process. This data is essential for analyzing the results of testing and identifying areas for improvement.
Demonstrating Documentation of Testing and Validation Results
Documenting the results of testing and validation is critical for demonstrating the effectiveness of the rollback plan, identifying areas for improvement, and providing a historical record of testing activities. This documentation should be comprehensive, accurate, and easily accessible.
- Test Plan: A detailed test plan should be created, outlining the scope, objectives, and methodology of the testing and validation activities. The test plan should include the following information:
- Test objectives
- Test scope
- Test environment
- Test cases
- Test data
- Test execution schedule
- Roles and responsibilities
- Success criteria
- Test Execution Reports: For each test execution, a detailed test execution report should be generated, documenting the following:
- Test case ID
- Test execution date and time
- Test environment configuration
- Test steps
- Test results (pass/fail)
- Observed behavior
- Error messages
- Screenshots or other evidence
- Test execution duration
- Testers involved
- Any deviations from the test plan
- Defect Tracking: Any defects or issues identified during testing should be documented in a defect tracking system. Each defect should be assigned a priority and tracked through its lifecycle, from discovery to resolution.
- Analysis and Reporting: The results of testing and validation should be analyzed to identify trends, patterns, and areas for improvement. A summary report should be created, including the following information:
- Overall test results (e.g., percentage of tests passed, percentage of tests failed)
- Key findings
- Defect summary
- Recommendations for improvement
- Action items
- Version Control: All testing and validation documentation should be stored in a version control system to track changes, maintain a history of revisions, and ensure the integrity of the documentation.
- Review and Approval: The testing and validation documentation should be reviewed and approved by the appropriate stakeholders, including the project manager, system administrators, and application owners.
Automation and Tools
Implementing a robust rollback plan is significantly enhanced by leveraging automation tools. Automating rollback procedures minimizes human error, accelerates recovery timelines, and ensures consistency across the migrated environment. This section focuses on the integration of automation into the rollback process, providing a practical guide and a comparative analysis of various tools.
Streamlining the Rollback Process with Automation
Automation is critical for a successful cloud migration rollback. It allows for the rapid and reliable restoration of the pre-migration state, minimizing downtime and mitigating potential business impacts. This involves automating various stages of the rollback, from data restoration to infrastructure reconfiguration.The integration of automation within the rollback workflow involves several key steps:
- Automated Data Backup and Restore: Utilize tools that automate the creation and management of backups. This includes scheduling regular backups, verifying their integrity, and providing automated restoration capabilities. For instance, consider a scenario where a company uses a database like PostgreSQL. Automation can be implemented to automatically back up the database to a separate storage location. In case of a rollback, the automation script restores the database from the backup, minimizing data loss and downtime.
- Infrastructure as Code (IaC) for Rollback: Employ IaC tools like Terraform or AWS CloudFormation to define and manage the infrastructure. This allows for the recreation of the pre-migration infrastructure state with a single command. For example, if a company migrates its web servers to AWS using Terraform, the Terraform configuration files can be used to redeploy the original web server infrastructure in case of a rollback.
This ensures that the infrastructure is restored to its exact pre-migration configuration.
- Automated Application Deployment and Configuration: Use tools like Ansible, Chef, or Puppet to automate the deployment and configuration of applications. These tools can be used to revert application deployments to their previous versions or to reconfigure application settings to match the pre-migration environment.
- Monitoring and Alerting for Rollback Triggers: Implement robust monitoring and alerting systems to detect issues that might trigger a rollback. These systems should automatically notify the operations team and initiate rollback procedures based on pre-defined thresholds. For example, if a monitoring system detects a significant increase in error rates after the migration, it can automatically trigger a rollback to the previous environment.
- Orchestration and Workflow Automation: Use orchestration tools to coordinate the various automation steps in the rollback process. These tools can define the sequence of actions to be taken during a rollback, ensuring that each step is executed in the correct order.
Integrating Rollback Procedures into the Migration Workflow
Integrating rollback procedures into the migration workflow involves a systematic approach, ensuring that rollback capabilities are incorporated at each stage of the migration. This integration ensures that the rollback process is streamlined, efficient, and well-documented.The integration process comprises the following steps:
- Planning and Design: Integrate rollback planning from the initial design phase of the migration. Define rollback triggers, procedures, and timelines. This includes documenting all necessary steps and resources required for a successful rollback.
- Automation Implementation: Implement the automation tools and scripts necessary for data backup, infrastructure provisioning, application deployment, and monitoring. Ensure these tools are integrated into the overall migration process.
- Testing and Validation: Thoroughly test the rollback procedures before and after the migration. Conduct regular rollback drills to validate the effectiveness of the procedures and identify any potential issues.
- Documentation: Document all rollback procedures, including the steps involved, the tools used, and the expected outcomes. This documentation should be readily available to the operations team and updated regularly.
- Training: Train the operations team on the rollback procedures and the use of the automation tools. This ensures that the team is prepared to execute the rollback process efficiently.
- Continuous Improvement: Regularly review and update the rollback procedures based on feedback from testing and actual rollback events. Continuously improve the automation tools and processes to optimize the rollback process.
Comparative Analysis of Automation Tools
Various automation tools are available to facilitate cloud migration rollbacks. The choice of tools depends on the specific requirements of the migration and the existing infrastructure. The following table provides a comparative analysis of some popular tools, highlighting their functionality, benefits, and limitations:
| Tool Name | Functionality | Benefits | Limitations |
|---|---|---|---|
| Terraform | Infrastructure as Code (IaC), provisioning and managing infrastructure. | Automates infrastructure provisioning and de-provisioning; supports multiple cloud providers; version control and collaboration. | Steeper learning curve; can be complex for large-scale deployments; state management can be challenging. |
| Ansible | Configuration management, application deployment, and orchestration. | Agentless architecture; simple syntax; supports parallel execution; idempotent operations. | Can be less effective for complex workflows; limited GUI support; scalability can be an issue for very large environments. |
| AWS CloudFormation | IaC, provisioning and managing AWS resources. | Native integration with AWS services; supports infrastructure-as-code; provides templates for common architectures. | Vendor-specific; limited support for non-AWS resources; can be challenging to manage complex templates. |
| Jenkins | Continuous integration and continuous delivery (CI/CD), automation workflows. | Highly extensible with plugins; supports a wide range of tools; customizable pipelines. | Steeper learning curve; requires careful configuration; can become complex with many plugins. |
Monitoring and Alerting
Effective monitoring and alerting are crucial components of a robust rollback plan for cloud migration. Continuous observation of system performance, application behavior, and data integrity provides early warning signs of potential issues, enabling timely intervention and, if necessary, a swift rollback to the pre-migration state. This proactive approach minimizes downtime, reduces the impact of migration failures, and safeguards the business continuity.
Importance of Monitoring During and After Migration
Monitoring plays a pivotal role throughout the cloud migration process, extending beyond the initial cutover. It’s an ongoing activity that provides visibility into the health and performance of the migrated environment.
- Performance Tracking: Monitors key performance indicators (KPIs) such as CPU utilization, memory usage, network latency, and disk I/O. Tracking these metrics allows for identification of performance bottlenecks or degradation that might indicate problems arising from the migration process or incompatibility with the new cloud environment. For instance, a sudden increase in network latency after migration could suggest issues with network configuration or geographic distribution of resources.
- Application Behavior Monitoring: Focuses on application-specific metrics, including response times, error rates, transaction volumes, and resource consumption. This is essential to ensure that applications function correctly in the cloud environment and meet performance expectations. A surge in application error rates post-migration, for example, might indicate code compatibility issues or incorrect configuration settings.
- Data Integrity Verification: Ensures the accuracy and consistency of data during and after migration. This involves monitoring data replication processes, verifying data synchronization between the on-premises and cloud environments, and checking for data corruption or loss. Monitoring the number of records and comparing the values between source and destination databases can uncover data discrepancies.
- User Experience Monitoring: Gauges the end-user experience by tracking metrics such as website load times, application responsiveness, and the frequency of user-reported issues. This offers valuable insights into the usability and performance of the migrated applications from the user’s perspective. Monitoring tools can simulate user actions to proactively detect potential problems.
- Security Monitoring: Detects and responds to security threats and vulnerabilities in the cloud environment. This includes monitoring for unauthorized access attempts, unusual network activity, and potential data breaches. Security monitoring tools can alert on suspicious behavior and provide insights into security incidents.
System for Setting Up Alerts for Potential Rollback Triggers
A well-defined alerting system is essential for identifying potential rollback triggers promptly. Alerts should be configured based on predefined thresholds and conditions that indicate a deviation from the expected behavior of the migrated environment.
- Define Critical Metrics and Thresholds: Identify the key performance indicators (KPIs) that are critical for the successful operation of the migrated applications and infrastructure. These KPIs might include response times, error rates, CPU utilization, and network latency. Set specific thresholds for each KPI, defining acceptable ranges for normal operation. Thresholds should be based on historical data, performance benchmarks, and the specific requirements of the applications.
For example, a response time exceeding 2 seconds for a critical transaction could trigger an alert.
- Implement Alerting Rules: Configure alerting rules within monitoring tools to automatically trigger notifications when KPIs exceed predefined thresholds. These rules should be specific and actionable, clearly defining the conditions that trigger an alert. For instance, an alert might be triggered if CPU utilization exceeds 90% for more than 5 minutes.
- Configure Alerting Channels: Define the channels through which alerts will be delivered, such as email, SMS, or integration with incident management systems. Ensure that the appropriate teams or individuals are notified based on the severity and type of the alert. Implement escalation procedures to ensure that alerts are addressed promptly, even if the primary contact is unavailable.
- Integrate with Automation Tools: Integrate the alerting system with automation tools to enable automated responses to certain alerts. For example, if an alert indicates a resource shortage, the automation tool could automatically scale up the resources to alleviate the problem.
- Regularly Review and Refine Alerts: Periodically review and refine the alerting rules and thresholds to ensure they remain relevant and effective. Adjust thresholds based on changing performance characteristics and application requirements. Analyze historical alert data to identify patterns and improve the accuracy of the alerting system.
Analyzing Monitoring Data to Identify Issues That Require Rollback
Analyzing monitoring data is crucial to identifying issues that might necessitate a rollback. The goal is to quickly determine the root cause of problems and evaluate the severity of the impact on the business.
- Correlation of Metrics: Analyze the relationships between different metrics to identify potential root causes. For example, if high CPU utilization correlates with slow response times, it might indicate a performance bottleneck related to CPU processing. Similarly, high error rates could correlate with a specific application component, pointing to a code issue.
- Trend Analysis: Track the trends of key metrics over time to identify patterns and anomalies. Sudden changes in trends might indicate a problem. For instance, a steady increase in error rates could signal a gradual degradation in application performance, potentially requiring rollback.
- Root Cause Analysis: Employ root cause analysis techniques to pinpoint the underlying cause of issues. This involves examining logs, events, and other data sources to understand why problems are occurring. For example, if data replication fails, investigate the network connectivity, database configurations, and replication settings to identify the cause of the failure.
- Impact Assessment: Evaluate the impact of identified issues on business operations. Consider factors such as the number of affected users, the criticality of the affected applications, and the financial implications of the outage. This assessment will help determine the severity of the issue and the need for rollback.
- Rollback Decision: Based on the analysis of monitoring data and the impact assessment, make an informed decision about whether to initiate a rollback. If the issues are severe, widespread, or pose a significant risk to business operations, initiate the rollback process. The decision should be made based on predefined criteria and documented procedures.
Communication and Coordination
Effective communication and robust coordination are critical components of a successful cloud migration rollback plan. A breakdown in either can lead to confusion, delays, and potentially catastrophic consequences, jeopardizing the integrity of the data and the availability of critical services. A well-defined communication strategy ensures all stakeholders are informed, understand their responsibilities, and can respond effectively during the rollback process.
Importance of Clear Communication During a Rollback
Clear and concise communication minimizes the risk of errors and misunderstandings, enabling a swift and efficient rollback. Ambiguity and lack of information can result in incorrect actions, prolonging the downtime and increasing the potential for data loss or corruption.
- Reduced Confusion: A clear communication strategy minimizes the likelihood of confusion among team members, stakeholders, and end-users. Each party understands their role and responsibilities.
- Faster Issue Resolution: Prompt and accurate communication facilitates rapid identification and resolution of any issues encountered during the rollback. This includes immediate reporting of anomalies and rapid dissemination of solutions.
- Minimization of Downtime: By providing timely updates and instructions, clear communication helps minimize the duration of downtime during the rollback process.
- Enhanced Coordination: Effective communication ensures seamless coordination among various teams involved in the rollback, such as infrastructure, application, and database teams.
- Stakeholder Alignment: Regular communication keeps stakeholders informed about the progress of the rollback, managing expectations and preventing unnecessary anxiety.
Communication Plan for Rollback
A well-structured communication plan defines the roles, responsibilities, and communication channels required for a successful rollback. This plan should be established before the migration begins and updated as necessary.
- Roles and Responsibilities: Clearly define the roles and responsibilities of each individual or team involved in the rollback. This includes:
- Rollback Manager: Oversees the entire rollback process, making critical decisions and ensuring adherence to the plan.
- Technical Lead(s): Responsible for executing the technical aspects of the rollback, including infrastructure, application, and database recovery.
- Communication Lead: Manages all communications, ensuring timely updates and disseminating information to relevant stakeholders.
- Subject Matter Experts (SMEs): Provide specialized knowledge and support for specific areas of the migration or rollback.
- Stakeholders: Include executive leadership, business owners, and end-users who need to be kept informed about the progress.
- Communication Channels: Establish clear communication channels for different types of information.
- Primary Communication Channel: A centralized platform (e.g., a dedicated Slack channel, Microsoft Teams group, or email distribution list) for general announcements, status updates, and urgent communications.
- Incident Management System: Use an incident management system (e.g., ServiceNow, Jira Service Management) to track and manage issues encountered during the rollback. This system should provide a clear audit trail of all actions taken.
- Regular Status Updates: Schedule regular status updates (e.g., hourly or bi-hourly) to keep stakeholders informed of the rollback progress. These updates should include key metrics, issues encountered, and actions taken.
- Escalation Paths: Define clear escalation paths for critical issues that require immediate attention. This should include contact information for key personnel and escalation procedures.
- Communication Frequency: Determine the frequency of communication based on the severity and complexity of the rollback.
- Critical Rollbacks: Provide frequent updates (e.g., every 15-30 minutes) via the primary communication channel and incident management system.
- Non-Critical Rollbacks: Provide updates less frequently (e.g., hourly or bi-hourly).
- Communication Content: Define the content of communication messages.
- Status Updates: Include the current status of the rollback, any issues encountered, actions taken, and next steps.
- Incident Reports: Provide detailed information about any incidents, including the root cause, impact, and resolution steps.
- Decision Logs: Document all key decisions made during the rollback process, including the rationale behind the decisions.
Structure for Documenting Rollback Activities and Decisions
Maintaining a comprehensive record of all rollback activities and decisions is crucial for post-mortem analysis, identifying areas for improvement, and ensuring accountability. This documentation should be centralized, easily accessible, and consistently updated throughout the rollback process.
- Centralized Repository: Establish a centralized repository (e.g., a shared document management system, a dedicated wiki, or a project management tool) to store all rollback-related documentation.
- Documentation Structure: Define a standardized structure for documenting rollback activities and decisions. This structure should include:
- Rollback Plan Reference: A link to the original rollback plan.
- Timeline: A detailed timeline of events, including start and end times for each task.
- Tasks and Actions: A record of all tasks performed during the rollback, including the responsible parties and the outcomes.
- Decisions Log: A log of all key decisions made during the rollback, including the date, time, decision makers, rationale, and the impact of the decision.
- Issues and Resolutions: A detailed record of all issues encountered, including the root cause, impact, and resolution steps.
- Metrics and Performance Data: Relevant metrics and performance data, such as downtime duration, data loss, and application performance after the rollback.
- Communication Logs: Records of all communication, including the date, time, sender, recipient, and content of each message.
- Version Control: Implement version control for all documents to track changes and maintain a historical record.
- Accessibility and Security: Ensure that the documentation repository is accessible to authorized personnel only and that appropriate security measures are in place to protect the confidentiality and integrity of the data.
- Post-Rollback Review: After the rollback is complete, conduct a post-mortem review to analyze the documentation, identify areas for improvement, and update the rollback plan accordingly. This review should involve all key stakeholders.
Conclusion
In conclusion, the creation and rigorous implementation of a rollback plan are paramount to the success and stability of any cloud migration initiative. This involves comprehensive planning, proactive preparation, and the integration of automation and monitoring tools. By adhering to the guidelines Artikeld in this guide, organizations can effectively minimize risks, reduce downtime, and ensure the continuity of their operations.
Ultimately, a well-executed rollback plan is not just a contingency measure; it is an investment in the resilience and future-proofing of your cloud environment.
Essential Questionnaire
What triggers a rollback?
A rollback is triggered by critical failures during or after migration, including application errors, data corruption, performance degradation, or security breaches that compromise service availability or data integrity.
How long should a rollback take?
The rollback duration should be predetermined and optimized to minimize downtime, ideally measured in hours, based on the complexity of the environment and the scope of the rollback plan. Regular testing is crucial for optimizing this timeframe.
What is the difference between a rollback and disaster recovery?
A rollback reverts to a previous, stable state, while disaster recovery focuses on restoring operations after a major disruption, often involving a different infrastructure or location. Rollback is a subset of disaster recovery, specific to the migration process.
How often should the rollback plan be tested?
The rollback plan should be tested regularly, ideally at least quarterly, and after any significant changes to the infrastructure, applications, or migration procedures. Testing frequency should be adjusted based on the criticality of the systems and the frequency of changes.
What happens to data changes made after the migration but before the rollback?
Data changes made post-migration but before the rollback are typically addressed using incremental backups or data synchronization strategies. The rollback plan should include procedures for reconciling or discarding these changes, depending on their impact and criticality.