Embarking on the journey of securing your digital landscape often leads to the pivotal strategy of network segmentation. This approach, at its core, divides your network into isolated segments, much like creating secure zones within a building. By understanding the fundamentals and meticulously planning, you can fortify your infrastructure against a multitude of threats.
This guide provides a structured approach to understanding, planning, and implementing network segmentation for security. We will explore the essential steps, from identifying critical assets and assessing risks to selecting the appropriate segmentation methods and configuring security measures. Whether you’re a seasoned IT professional or just beginning to explore network security, this guide will offer valuable insights and practical strategies.
Understanding Network Segmentation Basics
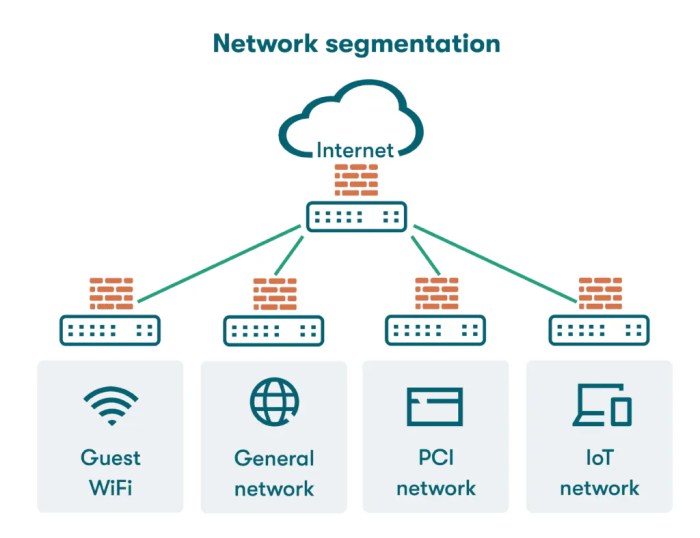
Network segmentation is a crucial security practice that involves dividing a computer network into smaller, isolated sections. This approach enhances security by limiting the impact of security breaches and improving overall network performance. By segmenting a network, organizations can control access to sensitive resources and prevent attackers from easily moving laterally within the network.
Core Concept of Network Segmentation
The core concept of network segmentation revolves around creating logical or physical boundaries within a network to isolate different segments. This isolation restricts the flow of traffic between segments, enforcing access controls and limiting the blast radius of potential security incidents. The primary goal is to contain threats, preventing them from spreading across the entire network.
Different Network Segmentation Models
Several models can be employed for network segmentation, each offering varying levels of security and complexity.
- VLANs (Virtual LANs): VLANs are a common method of network segmentation that uses the logical grouping of network devices. They operate at Layer 2 (Data Link Layer) of the OSI model. Devices within the same VLAN can communicate directly, while communication between different VLANs requires a router. This approach is relatively simple to implement and is often used to segment different departments or functional areas within an organization.
- Subnetting: Subnetting involves dividing a network into smaller subnets based on IP addresses. Each subnet represents a distinct segment, and traffic between subnets is typically routed. This method provides a more granular level of control than VLANs, allowing for more specific access control rules.
- Firewall-Based Segmentation: This approach uses firewalls to control traffic flow between network segments. Firewalls examine network traffic and apply rules to allow or deny communication based on source, destination, protocol, and other criteria. This provides a highly flexible and powerful segmentation model, enabling fine-grained control over network access.
- Micro-segmentation: Micro-segmentation is an advanced form of network segmentation that isolates individual workloads or applications. This creates highly granular security policies, allowing organizations to limit lateral movement within the data center or cloud environment. Micro-segmentation often uses software-defined networking (SDN) and is typically implemented at the hypervisor or operating system level.
Benefits of Implementing Network Segmentation for Security
Implementing network segmentation offers numerous security benefits, making it a critical component of a robust security posture.
- Reduced Attack Surface: Segmentation limits the scope of a potential security breach. If one segment is compromised, the attacker’s access is restricted to that segment, preventing them from easily accessing other parts of the network. This is analogous to having separate rooms in a house, where a fire in one room doesn’t automatically spread to the others.
- Improved Threat Containment: Segmentation helps contain security threats by preventing lateral movement. Even if an attacker gains access to a segment, they are unable to move to other segments without traversing through a firewall or other access control mechanisms.
- Enhanced Compliance: Many regulatory frameworks, such as PCI DSS (Payment Card Industry Data Security Standard), require network segmentation to protect sensitive data. Implementing segmentation helps organizations meet these compliance requirements.
- Simplified Security Management: Segmentation can simplify security management by allowing organizations to apply specific security policies to each segment. This makes it easier to monitor and control network traffic and identify potential security threats.
- Improved Performance: Segmentation can improve network performance by reducing broadcast traffic and congestion. This is especially beneficial in large networks where traffic can become overwhelming.
Identifying Assets and Risks
Identifying and assessing assets and risks is a crucial step in implementing network segmentation effectively. A thorough understanding of what needs protection and the potential threats is essential for designing a robust and secure segmented network. This process helps prioritize security efforts and allocate resources efficiently.
Identifying Critical Assets
Identifying critical assets is the first step in a risk assessment. These assets are the systems, data, and resources that are essential for the organization’s operations and whose compromise would have the most significant impact. This requires a systematic approach to discover and categorize the assets.To identify critical assets, consider these steps:
- Asset Discovery: Begin by creating an inventory of all network assets. This includes hardware (servers, workstations, routers, switches, firewalls, IoT devices), software (operating systems, applications, databases), and data (customer records, financial information, intellectual property). Network scanning tools, asset management systems, and manual documentation can be used to gather this information.
- Asset Classification: Categorize assets based on their function, sensitivity, and value to the organization. Examples of categories include:
- Confidential Data: Data that must be protected from unauthorized disclosure, such as financial records, personal health information (PHI), or trade secrets.
- Critical Systems: Systems essential for business operations, such as core business applications, database servers, and domain controllers.
- Public-Facing Assets: Systems that are accessible from the internet, such as web servers and email servers.
- Asset Prioritization: Prioritize assets based on their criticality. Assets with a higher impact on business operations or a greater potential for damage should be given the highest priority. This prioritization helps in determining the level of protection required for each asset.
- Documentation: Maintain detailed documentation of all assets, including their location, function, owner, and security requirements. This documentation should be regularly updated to reflect changes in the network environment.
Comparing Risk Assessment Methods
Several methods can be used to assess the risks associated with network security. The choice of method depends on the organization’s size, resources, and the complexity of its network. Each method has its strengths and weaknesses.Here’s a comparison of common risk assessment methods:
- Qualitative Risk Assessment: This method relies on expert judgment and subjective assessments to evaluate risks. It uses descriptive terms (e.g., high, medium, low) to rate the likelihood and impact of threats. This method is relatively quick and inexpensive to implement but can be less precise. It is suitable for smaller organizations or when a rapid assessment is needed.
- Quantitative Risk Assessment: This method uses numerical data and statistical analysis to calculate the financial impact of risks. It involves estimating the Annualized Rate of Occurrence (ARO) and the Single Loss Expectancy (SLE). The Annualized Loss Expectancy (ALE) is then calculated using the formula:
ALE = ARO
– SLEThis method provides a more objective and precise assessment of risks but requires more data and expertise. It is suitable for organizations with mature security programs and sufficient data. For example, an organization might estimate the SLE of a data breach to be $1 million and the ARO to be 0.1 (once every ten years). The ALE would be $100,000.
- Hybrid Risk Assessment: This method combines qualitative and quantitative approaches. It uses qualitative methods to identify and prioritize risks and then uses quantitative methods to assess the most critical risks. This approach offers a balance between speed, accuracy, and resource requirements. It is a practical choice for most organizations.
- Vulnerability Scanning and Penetration Testing: These methods proactively identify vulnerabilities in the network. Vulnerability scanning uses automated tools to identify known weaknesses, while penetration testing simulates real-world attacks to exploit vulnerabilities. These methods provide valuable insights into the effectiveness of existing security controls. They are often used in conjunction with other risk assessment methods.
Detailing Potential Threats Mitigated by Network Segmentation
Network segmentation is a powerful security measure that can mitigate a wide range of potential threats by limiting the impact of security breaches. By dividing a network into isolated segments, organizations can contain the damage caused by a successful attack and prevent attackers from moving laterally across the network.Network segmentation can help mitigate the following threats:
- Malware Infections: Segmentation limits the spread of malware by preventing it from easily infecting other segments. If a workstation in one segment is infected, it cannot automatically access resources in other segments. This containment reduces the scope of the infection.
- Ransomware Attacks: Segmentation restricts ransomware’s ability to encrypt critical data across the entire network. If ransomware encrypts files in one segment, the attacker’s access is limited, and the impact is reduced. The ability to quickly isolate the affected segment is also crucial.
- Insider Threats: Segmentation can restrict access based on the principle of least privilege, limiting the damage a malicious insider can cause. Employees only have access to the resources they need to perform their job functions.
- Lateral Movement: Segmentation hinders attackers’ ability to move laterally across the network after gaining initial access. Attackers cannot easily pivot from one segment to another to reach their target assets. This significantly increases the difficulty of escalating privileges and accessing sensitive data.
- Denial-of-Service (DoS) Attacks: Segmentation can help isolate the impact of DoS attacks. By segmenting critical services, an attack on one segment is less likely to affect other parts of the network. This can help maintain business continuity.
- Data Breaches: Segmentation limits the scope of data breaches by restricting access to sensitive data. Even if an attacker gains access to a segment containing sensitive data, they cannot easily access data in other segments. This reduces the amount of data exposed in a breach.
Planning the Segmentation Strategy
Designing a robust network segmentation strategy is a crucial step in fortifying your organization’s security posture. It moves beyond simply understanding your assets and risks, focusing on proactively shaping your network architecture to minimize the impact of potential breaches and control access effectively. This stage involves a strategic approach, carefully considering business requirements and operational needs.
Designing a Network Segmentation Strategy Based on Business Needs
A successful segmentation strategy is inextricably linked to the specific needs and operational goals of your business. A one-size-fits-all approach is ineffective; instead, tailor the segmentation to align with your organization’s structure, data sensitivity, and regulatory compliance requirements. This ensures the security measures enhance, rather than hinder, business operations.To design an effective segmentation strategy, consider the following:
- Business Function: Segment your network based on the core functions performed within your organization. This might include separating departments like finance, human resources, and research and development. Each segment should be isolated to prevent unauthorized access to sensitive data and resources.
- Data Sensitivity: Classify your data based on its sensitivity level (e.g., public, internal, confidential, highly confidential). Create network segments to isolate data based on its classification. This ensures that the most sensitive data is protected behind the most robust security controls. For example, financial records should be placed in a highly secure segment, isolated from less sensitive data.
- Regulatory Compliance: Consider industry-specific regulations and compliance requirements (e.g., HIPAA, PCI DSS, GDPR). Segment your network to meet these compliance needs. For instance, if you handle credit card information, you’ll need to create a Payment Card Industry Data Security Standard (PCI DSS) compliant segment.
- User Roles and Access Control: Implement role-based access control (RBAC) to determine who can access what within each segment. This minimizes the attack surface by limiting access to only the necessary resources. For example, an HR representative should only have access to HR-related data within the HR segment.
- Threat Modeling: Identify potential threats and vulnerabilities within each segment. This helps to determine the appropriate security controls, such as firewalls, intrusion detection systems, and access control lists (ACLs), needed to mitigate risks.
- Network Topology: Analyze your existing network topology to determine the best segmentation approach. Consider using VLANs, subnets, and firewalls to create isolated segments.
Organizing Network Segments Based on Function, Sensitivity, and Access Requirements
The organization of your network segments directly impacts the effectiveness of your security strategy. This involves carefully grouping resources based on their function, the sensitivity of the data they handle, and the access privileges required. This structured approach minimizes the impact of a security breach by limiting the lateral movement of attackers within the network.Here’s how to organize your network segments:
- Functional Segmentation: Group resources based on their primary function. This approach isolates departments or business units, preventing unauthorized access to resources outside their scope. Examples include:
- Finance: Contains financial applications, databases, and related resources.
- Human Resources: Houses employee data, payroll systems, and HR applications.
- Research and Development: Contains intellectual property, research data, and development environments.
- Data Sensitivity Segmentation: Create segments based on the sensitivity of the data stored and processed. This ensures that sensitive data is protected by the most stringent security controls. Examples include:
- Public Segment: Contains publicly accessible web servers and services.
- Internal Segment: Contains internal applications and data accessible to employees.
- Confidential Segment: Contains sensitive data requiring restricted access.
- Highly Confidential Segment: Contains the most sensitive data, requiring the highest level of protection.
- Access Control Segmentation: Implement access control mechanisms, such as role-based access control (RBAC) and network access control (NAC), to restrict access to resources based on user roles and privileges.
- Example Scenario: Consider a healthcare organization. They might segment their network as follows:
- Patient Data Segment: Contains electronic health records (EHRs), patient portals, and related systems. This segment is highly protected, with strict access controls and audit trails to comply with HIPAA regulations.
- Administrative Segment: Houses administrative applications, billing systems, and internal communications.
- Guest Network: Provides internet access for visitors, isolated from internal resources.
Creating a Plan for Implementing Segmentation in a Phased Approach
Implementing network segmentation is a significant undertaking that requires careful planning and execution. A phased approach allows you to gradually introduce segmentation, minimizing disruption to business operations and allowing for iterative improvements based on lessons learned. This methodical approach ensures a smoother transition and reduces the risk of unforeseen issues.Here’s a phased approach to implementing network segmentation:
- Phase 1: Assessment and Planning:
- Network Assessment: Conduct a thorough assessment of your current network infrastructure, including its topology, existing security controls, and data flows.
- Define Segmentation Goals: Clearly define your segmentation objectives, such as reducing the attack surface, improving data security, and meeting compliance requirements.
- Develop a Detailed Plan: Create a comprehensive implementation plan, including timelines, resource allocation, and specific tasks.
- Phase 2: Pilot Implementation:
- Select a Pilot Segment: Choose a non-critical segment to pilot your segmentation strategy. This allows you to test your implementation without affecting critical business operations.
- Implement Segmentation Controls: Deploy the necessary segmentation controls, such as VLANs, firewalls, and access control lists (ACLs), in the pilot segment.
- Testing and Validation: Thoroughly test the pilot segment to ensure that it functions as expected and that the segmentation controls are effective.
- Phase 3: Gradual Rollout:
- Expand Segmentation: Gradually expand segmentation to other segments, following the implementation plan.
- Monitor and Optimize: Continuously monitor the performance of the segmented network and optimize the security controls as needed.
- Documentation and Training: Document the segmentation architecture and provide training to IT staff and users.
- Phase 4: Continuous Monitoring and Improvement:
- Regular Audits: Conduct regular audits to assess the effectiveness of the segmentation strategy and identify areas for improvement.
- Security Updates: Regularly update security controls, such as firewalls and intrusion detection systems, to address emerging threats.
- Review and Adapt: Periodically review and adapt the segmentation strategy to address changing business needs and evolving threat landscapes.
Example: A financial institution may implement a phased approach, starting with segmenting its cardholder data environment (CDE) to comply with PCI DSS. They might then expand segmentation to isolate their online banking systems and internal financial applications.
Choosing Segmentation Methods
Selecting the right network segmentation methods is crucial for effectively isolating critical assets and minimizing the impact of security breaches. The optimal approach depends on factors such as network size, complexity, budget, and the organization’s specific security requirements. Several methods can be employed, often in combination, to achieve robust segmentation.
VLANs (Virtual LANs)
VLANs are a common and relatively simple method for segmenting a network at the data link layer (Layer 2 of the OSI model). They logically group devices together, regardless of their physical location, creating separate broadcast domains.
- Advantages of VLANs:
- Ease of implementation: VLANs are typically configured on network switches, making them relatively easy to deploy.
- Cost-effectiveness: VLANs utilize existing network infrastructure, minimizing the need for additional hardware.
- Improved performance: By reducing broadcast traffic, VLANs can improve network performance.
- Enhanced security: VLANs isolate traffic, preventing unauthorized access to sensitive data.
- Disadvantages of VLANs:
- Limited scalability: Managing a large number of VLANs can become complex.
- Layer 2 limitations: VLANs operate at Layer 2, which means they are susceptible to certain Layer 2 attacks, such as MAC address spoofing.
- Security risks: Misconfigured VLANs can create security vulnerabilities. For example, if a device is incorrectly assigned to a VLAN, it could potentially access resources it shouldn’t.
For example, consider a company with a network segmented into VLANs for different departments: Sales, Marketing, and Engineering. Each VLAN would isolate the traffic of each department. A user in the Sales VLAN would not be able to directly communicate with a device in the Engineering VLAN without going through a router or firewall. This prevents a potential security breach in one department from affecting the others.
Subnets
Subnets are a method of segmenting a network at the network layer (Layer 3 of the OSI model). Subnetting involves dividing a larger IP network into smaller, more manageable networks.
- Advantages of Subnets:
- Improved network organization: Subnets provide a logical structure for managing IP addresses and network traffic.
- Enhanced security: Subnets allow for the implementation of access control lists (ACLs) and routing rules to control traffic flow between subnets.
- Better scalability: Subnets make it easier to expand a network as an organization grows.
- Disadvantages of Subnets:
- Increased complexity: Subnetting requires a solid understanding of IP addressing and network routing.
- Configuration overhead: Configuring and managing subnets can be time-consuming, especially for large networks.
- Potential for routing issues: Incorrectly configured routing can disrupt network connectivity.
Consider a scenario where a company has a single /24 (255.255.255.0) network and wants to segment its network. They can create multiple subnets, such as a /26 (255.255.255.192) subnet for servers, a /27 (255.255.255.224) subnet for workstations, and a /28 (255.255.255.240) subnet for printers. This allows for granular control over network traffic and enhances security. Each subnet can be configured with specific access controls, preventing unauthorized access to sensitive resources.
Firewalls in Network Segmentation
Firewalls are essential components in network segmentation, acting as gatekeepers that control network traffic based on predefined rules. They can be deployed at various points in the network to enforce segmentation policies.
- Firewall Placement and Functionality:
- Perimeter Firewall: A perimeter firewall sits at the edge of the network, protecting it from external threats. It filters traffic entering and leaving the network.
- Internal Firewalls (Segmentation Firewalls): These firewalls are placed within the network to segment different areas, such as VLANs or subnets. They enforce security policies between internal segments.
- Application-Layer Firewalls: These firewalls inspect traffic at the application layer, providing more granular control over specific applications and protocols.
- How Firewalls Enforce Segmentation:
- Access Control Lists (ACLs): Firewalls use ACLs to define rules that permit or deny traffic based on source and destination IP addresses, ports, and protocols.
- Stateful Inspection: Firewalls track the state of network connections, allowing them to make more informed decisions about traffic flow.
- Deep Packet Inspection (DPI): Some firewalls perform DPI to analyze the content of network packets, allowing for the detection and blocking of malicious traffic.
For instance, a company might deploy a firewall between its public-facing web server (in a DMZ) and its internal network. This firewall would allow inbound traffic on port 80 and 443 (for HTTP and HTTPS) to the web server but would block all other inbound traffic, preventing unauthorized access to the internal network. The firewall can also be configured to inspect the traffic, ensuring it adheres to the security policies of the organization.
Implementing VLANs for Segmentation
Implementing VLANs (Virtual LANs) is a fundamental step in network segmentation, providing a logical separation of network traffic. This separation enhances security by isolating sensitive data and limiting the impact of security breaches. VLANs also improve network performance by reducing broadcast domains. Properly configured VLANs are a cornerstone of a robust network security posture.
Configuring VLANs on Network Switches
Configuring VLANs involves defining the VLANs themselves and assigning switch ports to those VLANs. The specific commands and interface may vary slightly depending on the switch vendor (e.g., Cisco, Juniper, HP), but the underlying principles remain the same. This process creates isolated broadcast domains, improving security and network efficiency.The configuration typically involves these steps:
- Accessing the Switch Configuration Interface: This can be done via the command-line interface (CLI) through a console connection (serial or SSH) or a web-based graphical user interface (GUI).
- Entering Configuration Mode: You’ll need to enter a privileged mode and then the configuration mode, often using commands like “enable” and “configure terminal” (Cisco-like).
- Creating the VLANs: Define the VLANs by assigning them unique IDs and names. For example, to create VLAN 10 named “Sales”, you might use the command “vlan 10” followed by “name Sales”.
- Assigning Ports to VLANs: For each port, specify the VLAN to which it belongs. This usually involves selecting the interface (port) and using commands like “switchport mode access” (for a single VLAN) or “switchport mode trunk” (for carrying multiple VLANs). Then, use the command “switchport access vlan [VLAN ID]”.
- Verifying the Configuration: After configuration, verify the setup using commands such as “show vlan” (Cisco-like) to confirm that VLANs are created and ports are assigned correctly.
Creating and Assigning Ports to VLANs: Step-by-Step Guide
The process of creating VLANs and assigning ports involves precise configuration steps. The following table provides a structured overview of the process, which can be adapted to different switch platforms, although the core concepts remain the same. Each step is crucial for ensuring correct segmentation and network functionality.
| Step | Description | Example (Cisco-like) |
|---|---|---|
| 1. Access Switch CLI | Connect to the switch via console, SSH, or Telnet. Authentication may be required. | ssh [email protected] |
| 2. Enter Enable Mode | Enter privileged EXEC mode to access configuration commands. | enable |
| 3. Enter Global Configuration Mode | Enter configuration mode to modify switch settings. | configure terminal |
| 4. Create VLAN | Create a VLAN and assign it a unique ID and a descriptive name. | vlan 10 |
| 5. Configure Interface(s) | Select the interface (port) to be assigned to a VLAN. | interface GigabitEthernet0/1 |
| 6. Set Port Mode | Configure the port mode (access or trunk). Access mode assigns a port to a single VLAN, while trunk mode carries traffic for multiple VLANs. | switchport mode access |
| 7. Assign VLAN to Port | Assign the port to the desired VLAN. | switchport access vlan 10 |
| 8. Exit Configuration Mode | Exit the interface configuration and global configuration modes. | exit |
| 9. Save Configuration | Save the configuration to the startup configuration file. | copy running-config startup-config |
| 10. Verify Configuration | Verify VLAN configuration. | show vlan brief |
Subnetting for Network Isolation
Subnetting is a fundamental technique in network segmentation, providing a crucial layer of isolation and control. By dividing a larger network into smaller, manageable subnetworks, subnetting enhances security, improves performance, and simplifies network administration. This section delves into the specifics of subnetting, detailing its role, implementation steps, and practical examples.
Role of Subnetting in Network Segmentation
Subnetting plays a vital role in network segmentation by logically dividing a network into smaller, independent segments. This isolation prevents unauthorized access between different parts of the network. It also restricts the blast radius of security incidents, limiting the impact of a breach to a specific subnet. This targeted approach is crucial for maintaining overall network security.
Steps Involved in Planning and Implementing a Subnetting Scheme
Planning and implementing a subnetting scheme involves several key steps to ensure effectiveness and efficiency. These steps must be carefully considered for optimal network performance and security.
- Assess Network Requirements: Determine the number of hosts and devices required in each segment. This involves analyzing existing network infrastructure and anticipating future growth.
- Choose a Network Addressing Scheme: Select a private IP address range (e.g., 192.168.0.0/16, 10.0.0.0/8) or a public IP range if the network is directly connected to the internet.
- Define Subnet Masks: Calculate subnet masks based on the number of required hosts per subnet. The subnet mask determines the network and host portions of the IP address.
- Assign IP Addresses: Assign IP addresses to devices within each subnet, ensuring each device has a unique IP address, subnet mask, and default gateway.
- Configure Network Devices: Configure routers, switches, and firewalls to forward traffic between subnets based on defined rules and access control lists (ACLs).
- Test and Validate: Test network connectivity and security policies to ensure that the subnetting scheme functions as intended. Verify that traffic is routed correctly and that access controls are enforced.
Examples of Subnetting Calculations and Their Application
Subnetting calculations are essential for determining the appropriate network and host address space for each subnet. The following examples illustrate how to calculate subnet masks and determine the number of usable hosts per subnet.
Example 1: Class C Network Subnetting
Consider a network with the IP address range 192.168.1.0/24. We want to create two subnets, one for servers and one for client workstations.
- Original Network: 192.168.1.0/24 (Subnet mask: 255.255.255.0)
- Subnetting: To create two subnets, we borrow one bit from the host portion of the IP address. This changes the subnet mask.
- New Subnet Mask: 255.255.255.128 (/25)
- Subnet 1 (Servers): 192.168.1.0/25 (Usable IP range: 192.168.1.1 – 192.168.1.126)
- Subnet 2 (Workstations): 192.168.1.128/25 (Usable IP range: 192.168.1.129 – 192.168.1.254)
In this example, the /25 subnet mask allows for 126 usable host addresses per subnet, providing sufficient address space for the servers and workstations.
Example 2: Class B Network Subnetting
Suppose a company has a network using the 172.16.0.0/16 address space and wants to create subnets for different departments.
- Original Network: 172.16.0.0/16 (Subnet mask: 255.255.0.0)
- Subnetting: To create subnets, borrow bits from the host portion. For example, to create 4 subnets, two bits are borrowed.
- New Subnet Mask: 255.255.192.0 (/18)
- Subnet 1 (Marketing): 172.16.0.0/18 (Usable IP range: 172.16.0.1 – 172.16.63.254)
- Subnet 2 (Finance): 172.16.64.0/18 (Usable IP range: 172.16.64.1 – 172.16.127.254)
- Subnet 3 (IT): 172.16.128.0/18 (Usable IP range: 172.16.128.1 – 172.16.191.254)
- Subnet 4 (Sales): 172.16.192.0/18 (Usable IP range: 172.16.192.1 – 172.16.255.254)
The /18 subnet mask provides a larger number of usable host addresses per subnet compared to the /25 in the previous example, suitable for larger departments.
These examples demonstrate how subnetting provides the flexibility to organize and isolate network resources based on organizational needs, improving both security and network manageability.
Firewall Configuration and Rules
Firewalls are a critical component in a segmented network, acting as the gatekeepers that control the flow of traffic between different segments. They enforce the segmentation policies you’ve established, preventing unauthorized access and limiting the impact of security breaches. Proper firewall configuration is essential to realizing the full security benefits of network segmentation.
Importance of Firewalls in Segmented Networks
Firewalls play a pivotal role in maintaining the integrity and security of segmented networks. They operate by inspecting network traffic and comparing it against a set of predefined rules. These rules dictate which traffic is allowed to pass and which is blocked. Without firewalls, the segmentation you’ve implemented would be significantly weakened, as traffic could freely traverse between segments, negating the isolation intended by your design.
- Traffic Control: Firewalls provide granular control over network traffic, enabling administrators to define specific rules for each segment.
- Access Control: They enforce access control policies, ensuring that only authorized users and devices can access specific resources within each segment.
- Threat Mitigation: Firewalls act as a first line of defense against various threats, such as malware and unauthorized access attempts, by blocking malicious traffic.
- Compliance: Firewalls help organizations meet regulatory compliance requirements by enforcing security policies and providing audit trails.
Examples of Firewall Rules for Controlling Network Traffic
Firewall rules are the cornerstone of network segmentation, defining the allowed and denied traffic flows. These rules are typically based on various criteria, including source and destination IP addresses, ports, protocols, and more.Here are some examples:
- Allowing HTTP traffic: Allow traffic from any source to the web server (e.g., IP address 192.168.1.10) on port 80 (HTTP). This rule permits users from any network segment to access the web server.
- Denying SSH access: Deny traffic from the internet (any source IP) to the internal server (e.g., 192.168.1.20) on port 22 (SSH). This rule prevents external access to the server via SSH, enhancing security.
- Restricting database access: Allow traffic from the application server (e.g., 192.168.1.15) to the database server (e.g., 192.168.1.30) on port 3306 (MySQL). This rule limits database access to only the application server, reducing the attack surface.
- Allowing DNS traffic: Allow traffic from any internal network segment to the DNS server (e.g., 192.168.1.5) on port 53 (DNS). This rule enables name resolution for internal devices.
Configuring Firewall Rules to Enforce Segmentation Policies
Configuring firewall rules is a crucial step in implementing network segmentation. The process involves defining the specific rules that align with your segmentation strategy and enforcing access control policies. The rules should be designed to permit necessary traffic while blocking all other traffic by default.Here’s a general approach to configuring firewall rules:
- Identify Traffic Flows: Determine the required communication paths between different network segments. Document which services, protocols, and ports are needed for each application and service.
- Define Rules: Create firewall rules based on the identified traffic flows. These rules should specify the source and destination IP addresses, ports, and protocols. For example: “Allow traffic from the application server (192.168.1.10) to the database server (192.168.1.20) on port 3306 (MySQL).”
- Implement “Deny All” Rule: Implement a “deny all” rule at the end of your rule set. This ensures that any traffic not explicitly allowed is blocked. This “deny all” rule is a critical element in implementing a zero-trust approach.
- Test and Monitor: Thoroughly test the firewall rules to ensure they function as intended. Monitor firewall logs to identify any unauthorized access attempts or unexpected traffic patterns. Regularly review and update firewall rules as your network and security requirements evolve.
The “deny all” rule, often placed as the last rule in the configuration, is a fundamental security principle.
The “deny all” rule ensures that all traffic that is not explicitly permitted is blocked, reducing the attack surface and preventing unauthorized access.
Access Control Lists (ACLs)
Access Control Lists (ACLs) are a fundamental component of network security, providing granular control over network traffic. They function as filters, examining packets based on predefined criteria and deciding whether to permit or deny them. Effectively implemented ACLs are critical for enforcing security policies and limiting the attack surface of a network.
Function of ACLs in Controlling Network Access
ACLs are primarily used to control network access by examining packet headers and making decisions based on configured rules. They operate by matching specific criteria, such as source and destination IP addresses, port numbers, and protocols, against a set of defined rules. This allows network administrators to precisely dictate which traffic is allowed to traverse the network and which traffic is blocked.ACLs typically work by comparing the attributes of a network packet against a list of rules.
The first rule that matches the packet’s attributes determines the action taken: either permitting or denying the packet. The process continues until a match is found or the end of the ACL is reached. If no match is found, a default action is often applied, such as implicitly denying the packet. This mechanism is critical for network security, allowing for the enforcement of the principle of least privilege, where users and systems are granted only the necessary access.
Best Practices for Creating and Managing ACLs
Creating and managing ACLs effectively is crucial for maintaining network security and performance. Following best practices ensures that ACLs are both effective and maintainable.
- Planning and Documentation: Before creating an ACL, thoroughly plan its purpose and scope. Document the reasons for each rule, the devices it applies to, and the expected outcome. This documentation is essential for troubleshooting, auditing, and future modifications.
- Specificity and Granularity: ACLs should be as specific as possible. Instead of permitting or denying entire subnets, use specific IP addresses or address ranges when possible. This reduces the attack surface and provides finer control over network traffic.
- Ordering of Rules: The order of rules in an ACL is critical because the rules are processed sequentially. Place the most specific rules at the beginning to ensure they are evaluated first. This can significantly improve efficiency and security.
- Default Deny Principle: Adopt a default deny approach, where all traffic is denied by default unless explicitly permitted. This approach minimizes the risk of unauthorized access and strengthens network security.
- Regular Review and Auditing: Regularly review and audit ACLs to ensure they are still relevant, effective, and aligned with current security policies. Remove unnecessary or outdated rules to simplify the ACL and improve performance.
- Testing and Validation: Test ACLs in a non-production environment before deploying them to production. This allows you to verify that the rules function as intended without disrupting critical network services.
- Centralized Management: Use centralized management tools whenever possible to simplify the creation, deployment, and management of ACLs across multiple network devices. This improves consistency and reduces the risk of errors.
Implementing ACLs to Restrict Access Between Network Segments
ACLs are a powerful tool for restricting access between network segments, effectively isolating them and preventing unauthorized communication. This can be achieved by creating ACLs on routers or firewalls that control traffic flow between different VLANs or subnets.For example, consider a network with two segments: a user segment (VLAN 10) and a server segment (VLAN 20). The goal is to allow users in VLAN 10 to access specific services on servers in VLAN 20 (e.g., HTTP on port 80) while preventing unauthorized access to other services or communication between the two segments.Here’s a simplified example of how this might be implemented using a firewall or router:
1. Create an ACL
Define an ACL named “User-to-Server-Access” on the firewall/router.
2. Define Rules
Within the ACL, create the following rules:
Rule 1
Permit TCP traffic from the user segment (VLAN 10, source IP range) to the server segment (VLAN 20, destination IP range) on port 80 (HTTP).
Rule 2
Deny all other traffic from the user segment (VLAN 10) to the server segment (VLAN 20).
Rule 3
Permit established connections (traffic initiated from the server to the user segment in response to the request). This is crucial to allow the server to send responses back to the user.
3. Apply the ACL
Apply the “User-to-Server-Access” ACL to the interface that connects VLAN 10 and VLAN 20.The result is that only HTTP traffic from the user segment to the server segment is permitted. All other traffic, including attempts to access other ports or services, is denied. This effectively isolates the server segment from unauthorized access while allowing the necessary communication for users to access web services.This configuration enhances network security by minimizing the attack surface and controlling the flow of traffic between segments.
This principle of least privilege, implemented through ACLs, is a cornerstone of robust network segmentation strategies.
Monitoring and Maintaining Segmentation
Effective network segmentation is not a one-time implementation; it requires continuous monitoring and maintenance to ensure its ongoing effectiveness. Regular reviews, updates, and audits are essential to adapt to evolving threats, changes in the network environment, and new business requirements. This section Artikels crucial aspects of monitoring, maintaining, and auditing network segmentation.
Monitoring Network Traffic
Monitoring network traffic is paramount to understanding how segmented networks function and to identify potential security breaches or policy violations. Several methods and tools can be employed to achieve comprehensive monitoring.
- Network Intrusion Detection Systems (NIDS): NIDS analyze network traffic for malicious activity. They examine packets, looking for patterns that match known attack signatures or anomalous behavior. Examples include Snort and Suricata, which can be deployed on specific network segments to monitor traffic flow. They can alert administrators to suspicious activity, such as unauthorized access attempts or data exfiltration.
- Security Information and Event Management (SIEM) Systems: SIEM systems collect and analyze security data from various sources, including firewalls, intrusion detection systems, and network devices. They correlate events to provide a comprehensive view of the network’s security posture. They can also generate alerts based on predefined rules and anomalies. Popular SIEM solutions include Splunk, QRadar, and ArcSight. A SIEM can provide a centralized dashboard for monitoring network traffic across all segments, offering a holistic view of the network’s security.
- Network Performance Monitoring (NPM) Tools: NPM tools focus on network performance metrics such as latency, bandwidth utilization, and packet loss. While not specifically designed for security, they can help identify performance bottlenecks that could indicate a security issue or misconfiguration. They provide insights into traffic patterns and volumes, helping to understand normal network behavior and detect deviations. Examples of NPM tools include SolarWinds Network Performance Monitor and PRTG Network Monitor.
- NetFlow/sFlow Analysis: These technologies provide detailed information about network traffic flows, including source and destination IP addresses, ports, protocols, and traffic volume. This data is invaluable for identifying unusual traffic patterns, such as excessive traffic between segments or unexpected communication with external hosts. Tools like Cisco’s NetFlow Analyzer or ManageEngine NetFlow Analyzer can be used to visualize and analyze this data.
- Packet Capture and Analysis: Capturing and analyzing network packets provides the most detailed view of network traffic. Tools like Wireshark allow for in-depth examination of individual packets, enabling the identification of malicious payloads, unauthorized communication, and policy violations. Packet capture is particularly useful for forensic investigations and troubleshooting security incidents.
Regular Review and Update of Segmentation Policies
Network segmentation policies should not be static; they must be regularly reviewed and updated to remain effective. This process involves assessing the current segmentation design, identifying changes in the network environment, and adjusting policies accordingly.
- Scheduled Policy Reviews: Establish a schedule for regular reviews of segmentation policies. This could be quarterly, semi-annually, or annually, depending on the size and complexity of the network and the organization’s risk profile.
- Change Management Process: Implement a robust change management process to ensure that any changes to the network, such as new applications, services, or infrastructure, are properly assessed for their impact on segmentation. This includes documenting the changes, evaluating the security implications, and updating segmentation policies as needed.
- Business Requirement Alignment: Ensure that segmentation policies align with current business requirements. As business needs evolve, so too may the segmentation strategy. For example, the deployment of a new cloud-based application might necessitate adjustments to network access rules to allow for secure communication.
- Threat Landscape Assessment: Regularly assess the current threat landscape to identify new and emerging threats that could impact the network. This information should inform updates to segmentation policies, such as the addition of new rules to block known attack vectors or restrict access to sensitive resources.
- Vulnerability Scanning and Penetration Testing: Conduct regular vulnerability scanning and penetration testing to identify vulnerabilities in the network and assess the effectiveness of segmentation controls. The results of these assessments should be used to prioritize updates to segmentation policies and address any identified weaknesses.
Tools for Auditing Network Segmentation Effectiveness
Auditing network segmentation is critical to verify that implemented policies are functioning as intended and that the network is secure. Several tools can be used to audit network segmentation.
- Network Scanners: Tools like Nessus and OpenVAS can be used to scan the network for vulnerabilities and misconfigurations that could compromise segmentation. They can identify open ports, services, and vulnerabilities that could be exploited to bypass segmentation controls.
- Firewall Rule Analyzers: These tools analyze firewall rules to identify potential security gaps, such as overly permissive rules or conflicting rules. They can also help to ensure that firewall rules are aligned with segmentation policies. Examples include SolarWinds Firewall Security Manager and FireMon.
- Compliance Reporting Tools: These tools help to generate reports that demonstrate compliance with relevant security standards and regulations, such as PCI DSS or HIPAA. They can verify that segmentation policies are in place and that the network meets the required security controls.
- Network Mapping Tools: Tools like NetBrain or network diagrams created manually can be used to visualize the network and identify the connections between different segments. This helps to verify that segmentation is implemented correctly and that unauthorized access paths are not present.
- Penetration Testing: Penetration testing simulates real-world attacks to assess the effectiveness of segmentation controls. Penetration testers attempt to bypass segmentation to gain unauthorized access to sensitive resources. The results of the penetration test provide valuable insights into the effectiveness of segmentation and identify areas for improvement.
Common Challenges and Solutions
Implementing network segmentation, while crucial for security, often presents various hurdles. Understanding these challenges and having effective solutions in place is vital for a successful and secure network architecture. This section delves into common obstacles and strategies to overcome them.
Complexity in Implementation
Network segmentation can introduce significant complexity, especially in large and dynamic environments. This complexity arises from the need to configure and manage multiple network devices, security policies, and access controls across different segments.To address this challenge:
- Phased Implementation: Break down the segmentation project into manageable phases. This allows for testing and refinement at each stage, minimizing disruption and allowing for iterative improvements. For instance, start by segmenting a less critical area and then expand.
- Automation: Utilize automation tools for configuration, policy enforcement, and monitoring. Tools like Ansible, Chef, or Puppet can streamline the process and reduce manual errors.
- Centralized Management: Implement a centralized management platform for all security devices and policies. This simplifies the administration, monitoring, and troubleshooting of the segmented network.
Performance Impact
Segmentation can potentially impact network performance, especially if not implemented correctly. Increased traffic routing, firewall processing, and the introduction of new devices can introduce latency and bottlenecks.To mitigate performance issues:
- Careful Planning: Thoroughly plan the segmentation strategy, considering network traffic patterns and bandwidth requirements. Identify critical paths and optimize routing configurations.
- Hardware Considerations: Ensure that network devices, such as firewalls and routers, have sufficient processing power and bandwidth capacity to handle the segmented traffic load.
- Traffic Optimization: Implement Quality of Service (QoS) mechanisms to prioritize critical traffic and prevent congestion. Optimize firewall rules to minimize processing overhead.
Compatibility Issues
Ensuring compatibility between different network devices and security tools can be a significant challenge. Incompatible devices or configurations can lead to connectivity problems and security vulnerabilities.To overcome compatibility issues:
- Vendor Selection: Choose network devices and security tools that are compatible with each other. Consider using a single vendor or a vendor ecosystem that offers interoperability.
- Testing: Thoroughly test the compatibility of all devices and configurations before deploying them in a production environment.
- Standardization: Adhere to industry standards and best practices to ensure compatibility and interoperability. For example, using standard protocols and configurations.
Cost Considerations
Implementing network segmentation can involve significant costs, including the purchase of new hardware, software, and professional services.To manage costs effectively:
- Budgeting: Develop a detailed budget that includes all costs associated with the project, such as hardware, software, labor, and ongoing maintenance.
- Phased Approach: Implement the segmentation in phases to spread the costs over time. Prioritize the most critical segments first.
- Open-Source Solutions: Consider using open-source solutions for some aspects of the implementation to reduce costs. However, carefully evaluate the security implications and support options.
Security Policy Management
Managing and enforcing security policies across multiple network segments can be complex and time-consuming. Inconsistent or poorly defined policies can create vulnerabilities.To improve security policy management:
- Centralized Policy Management: Implement a centralized platform for managing and enforcing security policies across all network segments.
- Automation: Automate the policy enforcement process to ensure consistency and reduce manual errors.
- Regular Audits: Conduct regular audits of security policies to ensure they are up-to-date and effective. Review and update policies based on changing threats and business needs.
Here’s some advice for a smooth implementation:
- Start with a Clear Plan: Define your goals, assess your risks, and develop a detailed implementation plan before starting.
- Prioritize Security: Make security the primary driver of your segmentation strategy. Focus on isolating critical assets and protecting sensitive data.
- Test and Validate: Thoroughly test all configurations and policies before deploying them in a production environment. Regularly validate your segmentation effectiveness.
Security Best Practices in a Segmented Network
Implementing network segmentation is a significant step towards enhancing security, but it’s only the first part of the journey. Maintaining a robust security posture in a segmented environment requires adhering to a set of best practices that focus on proactive measures, continuous monitoring, and rapid incident response. This ensures that the benefits of segmentation are fully realized and that the network remains resilient against evolving threats.
Securing Communication Between Network Segments
Effective communication between network segments is crucial for business operations, but it must be secured to prevent unauthorized access and data breaches. This involves careful planning and implementation of security controls to manage traffic flow between different parts of the network.
- Least Privilege Principle: Grant only the necessary access rights. For example, if a user in the sales segment needs to access a database in the finance segment, grant them only the specific permissions required to access the necessary data, and nothing more. This limits the potential damage if a segment is compromised.
- Firewall Rules: Implement strict firewall rules that allow only essential traffic between segments. These rules should be regularly reviewed and updated to reflect changes in business needs and threat landscapes. For instance, only allow specific ports and protocols (e.g., HTTPS for web traffic, SSH for secure remote access) through the firewall.
- Intrusion Detection and Prevention Systems (IDPS): Deploy IDPS solutions within and between segments to monitor network traffic for malicious activity. These systems can detect and block suspicious traffic, providing an additional layer of security. They can identify anomalous behavior, such as a sudden increase in traffic from an unusual source.
- Encryption: Encrypt all sensitive data in transit between segments. Use protocols like TLS/SSL for web traffic and VPNs for secure remote access. This ensures that even if traffic is intercepted, it remains unreadable to unauthorized parties.
- Regular Auditing: Conduct regular audits of firewall rules, access controls, and network configurations to identify and remediate any security vulnerabilities. Audits should include penetration testing to simulate attacks and assess the effectiveness of security controls.
Incident Response Strategies Within a Segmented Environment
A well-defined incident response strategy is essential for minimizing the impact of security breaches in a segmented network. Segmentation, while enhancing security, also necessitates a more granular and targeted approach to incident response. This strategy needs to be proactive, adaptable, and tested regularly.
- Incident Response Plan: Develop a comprehensive incident response plan that Artikels the steps to be taken in the event of a security incident. This plan should include roles and responsibilities, communication protocols, and escalation procedures. The plan should clearly define who is responsible for each task during an incident.
- Containment Strategies: Define containment strategies to isolate compromised segments and prevent the spread of malware or unauthorized access. This might involve disabling network interfaces, changing firewall rules, or quarantining infected systems.
- Forensic Analysis: Conduct thorough forensic analysis to determine the root cause of the incident, identify affected systems, and collect evidence for legal or compliance purposes. This involves preserving logs, capturing network traffic, and analyzing malware samples.
- Eradication and Recovery: Implement procedures for eradicating the threat and recovering affected systems. This might involve patching vulnerabilities, removing malware, restoring systems from backups, and rebuilding compromised segments.
- Post-Incident Activities: Conduct a post-incident review to analyze the incident, identify lessons learned, and improve security controls and incident response procedures. This review should include a timeline of events, a summary of the impact, and recommendations for preventing future incidents.
- Regular Testing and Drills: Regularly test the incident response plan through tabletop exercises and simulated attacks. These exercises help to identify weaknesses in the plan and ensure that the incident response team is prepared to respond effectively to real-world incidents. For example, a simulated ransomware attack on a specific segment could test the effectiveness of containment and recovery procedures.
Ending Remarks
In conclusion, implementing network segmentation is a proactive and powerful defense strategy. By understanding the principles, carefully planning your approach, and consistently monitoring your network, you can significantly reduce your attack surface and enhance your overall security posture. Remember that continuous review and adaptation are key to maintaining a robust and secure network environment, ensuring your digital assets are protected against evolving threats.
FAQ Insights
What is the primary benefit of network segmentation?
The primary benefit is to limit the impact of a security breach. If one segment is compromised, the attacker’s access is contained, preventing them from easily accessing other critical parts of your network.
How does network segmentation help with compliance?
Segmentation helps meet compliance requirements by isolating sensitive data and systems, such as those containing financial or personal information, ensuring they are protected according to industry standards like PCI DSS or HIPAA.
What are the key considerations when choosing a segmentation method?
Consider your network size, budget, existing infrastructure, and the sensitivity of the data within each segment. Also, think about the expertise of your team and the level of ongoing management required.
How often should I review my network segmentation policies?
It’s recommended to review your segmentation policies at least annually, or more frequently if there are significant changes to your network, business needs, or security threats.
What tools are helpful for monitoring a segmented network?
Network monitoring tools, intrusion detection systems (IDS), and security information and event management (SIEM) systems are essential for monitoring traffic, detecting anomalies, and ensuring the effectiveness of your segmentation strategy.