In the ever-evolving landscape of software development, security is no longer an afterthought; it’s a fundamental requirement. “Shifting security left” represents a proactive approach, integrating security considerations early in the development lifecycle. This paradigm shift empowers developers to identify and address vulnerabilities before they become costly problems, leading to more robust and secure applications.
This guide explores the essential steps to effectively integrate security throughout your development process. We will cover everything from understanding the core principles of “shift left” to implementing secure coding practices, automating security testing, and establishing training programs for developers. By embracing this approach, you can significantly enhance your project’s security posture, reduce costs, and accelerate your release cycles.
Understanding the Concept of “Shift Left”
“Shift Left” in software development signifies a strategic move to incorporate security practices earlier in the software development lifecycle (SDLC). This approach fundamentally challenges the traditional, often waterfall-based, model where security was primarily addressed in the testing or deployment phases. By moving security considerations to the left, or earlier, in the SDLC, development teams can identify and remediate vulnerabilities more efficiently and cost-effectively.
Core Principles of “Shift Left”
The core principles of “Shift Left” revolve around proactive security, continuous integration, and early detection. This paradigm shift emphasizes the following:
- Early Integration of Security: Incorporating security checks and practices from the initial stages of planning and design. This includes threat modeling, secure coding guidelines, and security requirements definition.
- Automation: Automating security testing and analysis throughout the development process. This enables frequent, consistent, and rapid feedback on the security posture of the code. Tools such as Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Software Composition Analysis (SCA) are used to automate security checks.
- Continuous Feedback: Providing developers with immediate feedback on security vulnerabilities. This allows developers to fix issues as they arise, preventing them from accumulating and becoming more difficult to address later.
- Collaboration: Fostering collaboration between development, security, and operations teams. This ensures that security is a shared responsibility and that all stakeholders are aligned on security goals and practices.
Improvements to Security Posture through “Shift Left”
Adopting a “Shift Left” approach significantly enhances the security posture of a development project. This improvement is achieved through several key mechanisms:
- Reduced Vulnerability Exposure: Early detection and remediation of vulnerabilities minimize the window of opportunity for attackers. This proactive approach prevents vulnerabilities from reaching production, where they are more likely to be exploited.
- Enhanced Code Quality: Secure coding practices and automated security checks contribute to higher-quality code. Developers are more aware of security best practices, leading to fewer coding errors and security flaws.
- Improved Security Awareness: “Shift Left” promotes a security-conscious culture within the development team. Developers become more familiar with security threats and vulnerabilities, leading to a more proactive approach to security.
- Simplified Compliance: By integrating security into the SDLC, organizations can streamline compliance efforts. Automated security checks and reporting tools provide evidence of security controls, making it easier to meet regulatory requirements.
Benefits of Adopting a “Shift Left” Approach
Implementing a “Shift Left” strategy yields significant benefits, including cost savings and faster release cycles. These advantages are realized through:
- Cost Reduction: Fixing vulnerabilities early in the development process is significantly less expensive than fixing them later. According to IBM, the cost to fix a vulnerability can be up to 100 times more expensive if discovered in production compared to the design phase.
- Faster Release Cycles: By automating security checks and integrating them into the CI/CD pipeline, organizations can accelerate release cycles. Developers receive immediate feedback on security issues, allowing them to fix problems quickly and efficiently.
- Improved Developer Productivity: Automating security tasks frees up developers to focus on building features and functionality. By shifting security left, developers spend less time on reactive security tasks and more time on proactive development.
- Enhanced Customer Trust: A strong security posture builds customer trust. By demonstrating a commitment to security, organizations can enhance their reputation and improve customer loyalty.
Identifying Security Risks Early
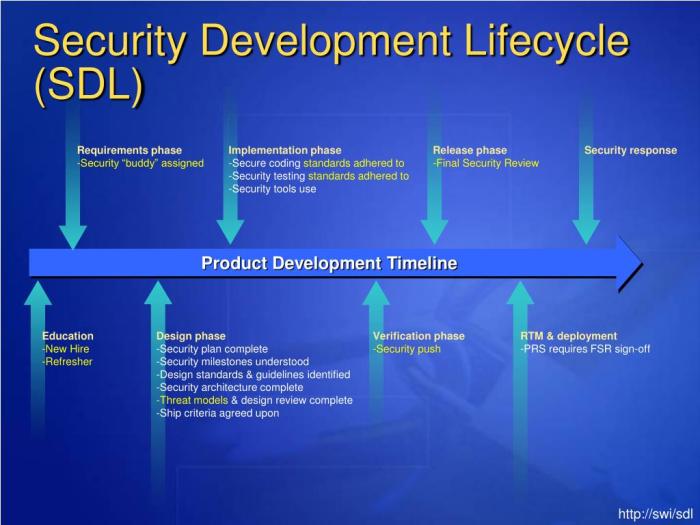
Proactive identification of security risks is crucial for shifting security left. This involves incorporating security considerations into the earliest stages of the software development lifecycle. By addressing vulnerabilities during design, developers can significantly reduce the cost and effort associated with remediation later in the process, leading to more secure and robust applications.
Proactive Vulnerability Identification During Design
Identifying vulnerabilities during the design phase involves a shift from reactive to proactive security practices. This includes activities like architectural analysis, threat modeling, and security requirement gathering. Early detection allows for the implementation of security controls at the foundation of the software, mitigating risks before code is even written.
Threat Modeling Techniques
Threat modeling is a systematic approach to identifying potential security threats and vulnerabilities. Various techniques are available, each with its strengths and weaknesses. The choice of technique depends on the project’s scope, complexity, and available resources.
- STRIDE: STRIDE is a mnemonic that stands for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. It helps categorize potential threats based on these six categories. The STRIDE model is particularly useful for identifying a broad range of threats and understanding their potential impact. It helps developers consider various attack vectors and security implications.
- PASTA (Process for Attack Simulation and Threat Analysis): PASTA is a risk-centric threat modeling methodology that focuses on business objectives. It provides a seven-step process: Definition of the Objectives, Definition of the Technical Scope, Application Decomposition, Threat Discovery, Vulnerability Analysis, Attack Modeling & Simulation, and Risk & Impact Analysis. PASTA emphasizes the attacker’s perspective, leading to more realistic threat assessments.
- Trike: Trike is an open-source threat modeling methodology that emphasizes risk-based security. It utilizes data flow diagrams and a structured approach to identify and prioritize risks based on their potential impact. Trike provides a comprehensive approach to threat modeling, covering various aspects of security.
- DREAD: DREAD is a system for rating threats based on Damage, Reproducibility, Exploitability, Affected users, and Discoverability. It provides a standardized way to assess and prioritize threats, allowing security teams to focus on the most critical vulnerabilities.
DREAD = (Damage + Reproducibility + Exploitability + Affected users + Discoverability) / 5
Integrating Security Requirements into the SDLC
Integrating security requirements into the Software Development Lifecycle (SDLC) ensures that security is not an afterthought but a fundamental aspect of the development process. This integration requires defining security requirements, incorporating them into design, implementation, testing, and deployment phases.
- Defining Security Requirements: Security requirements should be clearly defined and documented at the beginning of the project. These requirements should be based on industry best practices, regulatory compliance needs (e.g., GDPR, HIPAA), and the specific risks associated with the application. Requirements can be functional (e.g., authentication, authorization) or non-functional (e.g., performance, scalability).
- Security in Design: During the design phase, security requirements should inform the architectural decisions and the selection of technologies. This includes using secure design patterns, implementing input validation, and considering the principle of least privilege.
- Secure Coding Practices: Developers should adhere to secure coding standards and guidelines. This includes avoiding common vulnerabilities, such as SQL injection and cross-site scripting (XSS). Static and dynamic analysis tools can assist in identifying coding flaws.
- Security Testing: Comprehensive security testing, including penetration testing, vulnerability scanning, and fuzzing, should be performed throughout the SDLC. Testing should verify that security requirements are met and that vulnerabilities are identified and addressed.
- Deployment and Monitoring: Secure deployment practices, such as using secure configurations and monitoring for security events, are essential. Continuous monitoring allows for the detection of security incidents and facilitates timely responses.
Implementing Secure Coding Practices
Implementing secure coding practices is a critical step in shifting security left. This involves integrating security considerations directly into the software development lifecycle, starting from the initial coding phase. By proactively addressing vulnerabilities during development, organizations can significantly reduce the risk of security breaches and minimize the costs associated with remediation later in the process. This approach fosters a culture of security awareness among developers and results in more robust and resilient applications.
Importance of Secure Coding Standards and Best Practices
Establishing and adhering to secure coding standards and best practices is paramount for building secure software. These standards provide a consistent framework for developers to follow, reducing the likelihood of introducing vulnerabilities. They serve as a common language, ensuring that all team members understand and apply the same security principles. Regular updates to these standards are necessary to address emerging threats and evolving coding paradigms.
- Consistency and Standardization: Secure coding standards promote uniformity across the codebase, making it easier to identify and fix vulnerabilities. This also simplifies code reviews and reduces the learning curve for new developers.
- Reduced Vulnerabilities: Following best practices helps prevent common security flaws, such as SQL injection, cross-site scripting (XSS), and buffer overflows. This proactive approach significantly decreases the attack surface of the application.
- Improved Code Quality: Secure coding practices often align with general software engineering principles, leading to cleaner, more maintainable, and more reliable code.
- Enhanced Security Awareness: Regular training and adherence to standards increase developers’ understanding of security risks and how to mitigate them. This cultivates a security-conscious development culture.
- Compliance and Regulatory Requirements: Many industries have specific security regulations and compliance standards (e.g., PCI DSS, HIPAA). Secure coding practices help organizations meet these requirements.
Common Coding Vulnerabilities and Prevention
Understanding common coding vulnerabilities is crucial for preventing them. Developers must be aware of the potential risks associated with different coding practices and take appropriate measures to mitigate them. Regular security training and code reviews are essential for identifying and addressing these vulnerabilities.
- SQL Injection: Occurs when user-supplied data is not properly validated and used in SQL queries, allowing attackers to manipulate the query and gain unauthorized access to the database.
- Prevention: Use parameterized queries or prepared statements. These techniques separate the SQL code from the user-supplied data, preventing malicious code from being injected. Example: Instead of directly concatenating user input into a SQL query, use placeholders and bind the input to those placeholders.
- Cross-Site Scripting (XSS): Allows attackers to inject malicious scripts into web pages viewed by other users. This can lead to session hijacking, defacement, or redirection to malicious websites.
- Prevention: Sanitize and encode user input before displaying it on web pages. This involves removing or escaping special characters that could be interpreted as HTML or JavaScript. For example, use the appropriate encoding functions provided by your programming language or framework.
- Cross-Site Request Forgery (CSRF): Forces an authenticated user to submit a malicious request to a web application where they are currently authenticated.
- Prevention: Implement CSRF tokens. These are unique, secret tokens generated by the server and included in forms and requests. The server verifies the token upon submission to ensure the request originated from the user’s browser.
- Buffer Overflows: Occur when a program writes data beyond the allocated memory buffer, potentially overwriting adjacent memory locations. This can lead to crashes or arbitrary code execution.
- Prevention: Use safe string handling functions that perform bounds checking. Avoid using functions like `strcpy()` and `gets()`. Implement memory management techniques, such as using smart pointers in C++.
- Authentication and Authorization Flaws: Include weak password policies, lack of multi-factor authentication (MFA), and improper access control.
- Prevention: Implement strong password policies (e.g., requiring a minimum length, special characters, and numbers). Enforce MFA. Implement role-based access control (RBAC) to restrict access based on user roles.
- Insecure Direct Object References (IDOR): Occurs when an application provides direct access to objects based on user-supplied input without proper authorization checks.
- Prevention: Implement strict authorization checks for all object accesses. Avoid using predictable object identifiers.
Checklist for Developers for Writing Secure Code
A developer checklist provides a structured approach to ensure security considerations are incorporated throughout the coding process. This checklist serves as a guide, reminding developers of the essential steps to take to mitigate security risks. It should be integrated into the development workflow and regularly reviewed and updated.
- Input Validation: Validate all user input on both the client and server sides.
- Ensure that all user-supplied data is checked for type, length, format, and range.
- Use whitelisting instead of blacklisting.
- Output Encoding: Encode output to prevent XSS and other injection attacks.
- Use the appropriate encoding functions for the output context (e.g., HTML, JavaScript, URL).
- Authentication and Authorization: Implement secure authentication and authorization mechanisms.
- Use strong password policies and multi-factor authentication.
- Implement role-based access control (RBAC).
- Session Management: Secure session management to prevent session hijacking.
- Use secure cookies (e.g., `HttpOnly`, `Secure`).
- Regenerate session IDs after authentication.
- Cryptography: Use cryptography correctly to protect sensitive data.
- Use strong encryption algorithms and key management practices.
- Never store passwords in plain text. Use password hashing algorithms (e.g., bcrypt, Argon2).
- Error Handling: Handle errors securely.
- Avoid displaying sensitive information in error messages.
- Log errors securely for debugging purposes.
- Code Reviews: Conduct regular code reviews.
- Have peers review code for security vulnerabilities.
- Use static analysis tools to identify potential issues.
- Dependency Management: Manage dependencies securely.
- Regularly update dependencies to the latest versions to patch security vulnerabilities.
- Use dependency scanning tools to identify known vulnerabilities in dependencies.
- Testing: Perform security testing.
- Conduct unit tests, integration tests, and penetration testing.
- Use automated security testing tools.
- Documentation: Document security-related aspects of the code.
- Document security requirements, design decisions, and implementation details.
Integrating Security Testing into the Development Pipeline
Integrating security testing into the development pipeline is crucial for a successful shift-left strategy. By automating and embedding security checks throughout the software development lifecycle (SDLC), organizations can identify and remediate vulnerabilities early, reducing the cost and effort associated with fixing them later. This proactive approach enhances software quality, reduces risk, and improves overall security posture.
Types of Security Tests and Their Roles
Different types of security tests serve distinct purposes within the SDLC. Understanding their roles is essential for building a comprehensive security testing strategy.
- Static Application Security Testing (SAST): SAST, often referred to as “white-box testing,” analyzes source code, bytecode, or binaries to identify security vulnerabilities. It examines the code without executing it.
- Role: SAST tools help developers find flaws early in the development process, such as coding errors, insecure configurations, and violations of coding standards.
- Example: Tools like SonarQube, Coverity, and Veracode Static Analysis scan the codebase for potential vulnerabilities like SQL injection, cross-site scripting (XSS), and buffer overflows.
- Dynamic Application Security Testing (DAST): DAST, also known as “black-box testing,” assesses a running application from the outside, simulating attacks to identify vulnerabilities. It does not require access to the source code.
- Role: DAST tools identify vulnerabilities that are detectable when the application is running, such as those related to authentication, authorization, and input validation.
- Example: Tools like OWASP ZAP, Burp Suite, and Acunetix are used to simulate attacks and identify vulnerabilities such as cross-site scripting (XSS), SQL injection, and broken authentication.
- Software Composition Analysis (SCA): SCA identifies and analyzes open-source and third-party components used in an application.
- Role: SCA helps organizations manage the security risks associated with using open-source components, including known vulnerabilities and license compliance issues.
- Example: Tools like Snyk, Black Duck, and WhiteSource scan the project dependencies to identify known vulnerabilities and provide recommendations for remediation.
- Interactive Application Security Testing (IAST): IAST combines elements of both SAST and DAST, providing real-time feedback during application testing. It instruments the application to monitor its behavior during runtime.
- Role: IAST offers more accurate and efficient vulnerability detection by combining the benefits of static and dynamic analysis.
- Example: Tools like Contrast Security and HCL AppScan on Cloud offer IAST capabilities.
- Penetration Testing: Penetration testing involves simulating real-world attacks by ethical hackers to identify vulnerabilities and assess the effectiveness of security controls.
- Role: Penetration tests provide a comprehensive assessment of an application’s security posture by identifying vulnerabilities that automated tools may miss.
- Example: Penetration testers use a variety of tools and techniques to exploit vulnerabilities, such as social engineering, web application attacks, and network reconnaissance.
Automating Security Testing in a CI/CD Pipeline
Automating security testing within a CI/CD pipeline streamlines the development process and ensures that security checks are performed regularly. This proactive approach enables developers to identify and fix vulnerabilities early, reducing the risk of security breaches. The following steps Artikel a procedure for automating security testing.
- Choose Security Testing Tools: Select appropriate security testing tools based on the application’s technology stack and security requirements.
- Consider SAST tools for code analysis, DAST tools for dynamic testing, SCA tools for component analysis, and IAST for integrated testing.
- For example, SAST tools can be integrated into the build process to analyze code after each commit, while DAST tools can be triggered after the application is deployed to a testing environment.
- Define scan configurations, including the scope of the scan, the types of vulnerabilities to be checked, and the desired level of detail in the reports.
- The reports should include details about the vulnerabilities, such as the location in the code, the severity level, and recommended remediation steps.
- Define clear roles and responsibilities for addressing vulnerabilities, and establish timelines for fixing them based on their severity.
- After a vulnerability is fixed, re-run the security tests to verify that the fix is effective and that no new vulnerabilities have been introduced.
Interpreting Security Testing Results and Prioritizing Remediation Efforts
Understanding and effectively managing security testing results is essential for prioritizing remediation efforts and improving overall security posture. This involves analyzing the reports, assessing the risks, and taking appropriate actions to address identified vulnerabilities.
- Review Security Testing Reports: Carefully review the reports generated by security testing tools to identify vulnerabilities, their severity levels, and their potential impact.
- Pay attention to the details provided in the reports, such as the location of the vulnerabilities, the recommended remediation steps, and any relevant context information.
- Assess the Risks: Assess the risks associated with each vulnerability based on its severity, exploitability, and potential impact on the application and its users.
- Consider factors such as the sensitivity of the data handled by the application, the potential for financial or reputational damage, and the likelihood of an attack.
- Prioritize Remediation Efforts: Prioritize remediation efforts based on the risk assessment, focusing on the most critical vulnerabilities first.
- Use a risk-based approach to prioritize vulnerabilities, addressing those with the highest severity and greatest potential impact.
- Create a table to help visualize the prioritization:
- Remediate Vulnerabilities: Take appropriate actions to remediate the identified vulnerabilities, such as fixing the code, updating dependencies, or implementing security controls.
- Follow the recommended remediation steps provided in the security testing reports and consult with security experts if needed.
- Retest the Application: After remediating vulnerabilities, retest the application to verify that the fixes are effective and that no new vulnerabilities have been introduced.
- Rerun the security tests and review the results to ensure that the vulnerabilities have been resolved.
- Track Remediation Progress: Track the progress of remediation efforts, including the number of vulnerabilities identified, the number of vulnerabilities fixed, and the time taken to remediate them.
- Use a vulnerability management system or spreadsheet to track the progress and provide visibility into the security posture.
| Vulnerability | Severity | Impact | Priority | Remediation Steps |
|---|---|---|---|---|
| SQL Injection | Critical | Data Breach, System Takeover | High | Input Validation, Parameterized Queries |
| Cross-Site Scripting (XSS) | High | Account Takeover, Data Theft | High | Output Encoding, Input Validation |
| Broken Authentication | Medium | Unauthorized Access | Medium | Secure Password Storage, Multi-Factor Authentication |
Utilizing Static Application Security Testing (SAST)
Static Application Security Testing (SAST) is a crucial component of the “shift left” strategy, enabling developers to identify and address security vulnerabilities early in the software development lifecycle. By analyzing source code, byte code, or binaries, SAST tools can pinpoint potential weaknesses before the code is even executed. This proactive approach significantly reduces the cost and effort required to fix security flaws, leading to more secure and reliable applications.
Benefits and Functionality of SAST Tools
SAST tools offer several key benefits in the realm of application security. They provide a comprehensive and automated way to scan code for a wide range of vulnerabilities.
- Early Vulnerability Detection: SAST tools analyze code during the development phase, allowing developers to identify and fix vulnerabilities before the code is integrated or deployed. This reduces the risk of security breaches and minimizes the cost of remediation.
- Automated Code Analysis: SAST tools automate the process of security code review, saving time and effort compared to manual code reviews. They can quickly scan large codebases and identify potential security flaws based on predefined rules and patterns.
- Compliance and Standards Adherence: SAST tools can help organizations comply with security standards and regulations, such as OWASP Top 10, PCI DSS, and HIPAA. They can be configured to enforce coding standards and identify violations.
- Improved Code Quality: By identifying coding errors and security vulnerabilities, SAST tools contribute to improved code quality and reduce the likelihood of bugs and crashes.
- Cost Savings: Addressing security vulnerabilities early in the development lifecycle is significantly less expensive than fixing them later. SAST tools help organizations avoid costly security incidents and remediation efforts.
SAST tools function by analyzing the source code or compiled code without executing it. They employ various techniques, including:
- Lexical Analysis: Breaking down the code into tokens (s, identifiers, operators).
- Syntax Analysis: Parsing the code to ensure it adheres to the programming language’s grammar rules.
- Semantic Analysis: Analyzing the code’s meaning and identifying potential vulnerabilities based on predefined rules and patterns.
- Data Flow Analysis: Tracking how data moves through the code to identify potential vulnerabilities like SQL injection and cross-site scripting (XSS).
- Control Flow Analysis: Examining the execution paths within the code to identify vulnerabilities related to control flow, such as buffer overflows.
Examples of SAST Tools and Their Features
A variety of SAST tools are available, each offering a range of features and capabilities. Here are a few examples:
- SonarQube: An open-source platform that provides continuous inspection of code quality and security. It supports multiple programming languages and integrates with various build systems and IDEs. SonarQube detects bugs, vulnerabilities, and code smells, and provides detailed reports and metrics.
- Veracode: A cloud-based SAST solution that analyzes code for security vulnerabilities and compliance issues. Veracode supports a wide range of programming languages and provides detailed reports and remediation guidance. It also integrates with various IDEs and build systems.
- Checkmarx: A SAST tool that identifies and remediates security vulnerabilities in source code. It supports a wide range of programming languages and provides real-time feedback to developers. Checkmarx integrates with various IDEs and build systems, and offers features such as vulnerability prioritization and remediation guidance.
- Coverity: A SAST tool that provides static analysis for software security and quality. It supports multiple programming languages and integrates with various IDEs and build systems. Coverity detects a wide range of defects and vulnerabilities, including security flaws, coding errors, and performance issues.
- Fortify Static Code Analyzer (SCA): A SAST tool from Micro Focus that analyzes source code for security vulnerabilities. It supports numerous programming languages and provides detailed reports, remediation guidance, and integration with various development tools.
These tools share common features, including:
- Vulnerability Detection: Identifying a wide range of security vulnerabilities, such as SQL injection, cross-site scripting (XSS), buffer overflows, and insecure coding practices.
- Code Analysis: Analyzing code for compliance with coding standards and security best practices.
- Reporting and Visualization: Generating detailed reports and visualizations of identified vulnerabilities, including severity levels, code locations, and remediation guidance.
- Integration: Integrating with various IDEs, build systems, and CI/CD pipelines to automate the security testing process.
- Customization: Allowing users to customize the tool’s rules and settings to fit their specific needs and coding standards.
Workflow for Integrating SAST into the Development Process
Integrating SAST into the development process requires a well-defined workflow to maximize its effectiveness. The following table Artikels a sample workflow:
| Phase | Action | Tool | Output |
|---|---|---|---|
| Requirement Gathering | Define security requirements and coding standards. | N/A | Security requirements document, coding standards guidelines. |
| Development | Developers write code and commit it to the version control system. | IDE with SAST plugin, e.g., SonarLint | Real-time feedback on code quality and security vulnerabilities within the IDE. |
| Code Review | Code is reviewed by other developers. | SAST tool, e.g., SonarQube, Veracode | Detailed reports on identified vulnerabilities, code quality metrics, and security recommendations. |
| Build & Integration | The code is built and integrated with other components. | SAST tool integrated into the build pipeline, e.g., Jenkins with SonarQube plugin | Automated security scans during the build process, with reports and alerts. |
| Testing | Perform unit tests, integration tests, and system tests. | SAST tool, e.g., Coverity | Vulnerability reports, code quality metrics, and remediation guidance. |
| Deployment | Code is deployed to the production environment. | N/A | Secure deployment with minimized vulnerabilities. |
| Maintenance | Continuous monitoring and re-scanning of code with SAST tools. | SAST tool, e.g., Checkmarx | Regular security assessments and updates. |
Implementing Dynamic Application Security Testing (DAST)
Dynamic Application Security Testing (DAST) plays a crucial role in shifting security left by identifying vulnerabilities in running applications. Unlike SAST, which analyzes source code, DAST examines the application from the outside, simulating attacks to uncover weaknesses in its runtime behavior. This approach complements SAST, providing a more comprehensive security posture.
The Role of DAST in Identifying Runtime Vulnerabilities
DAST tools simulate attacks against a running application, mirroring how a real-world attacker might interact with it. This “black box” testing approach doesn’t require access to the source code, making it suitable for testing third-party applications or applications where source code access is restricted. By actively probing the application, DAST identifies vulnerabilities that may only manifest during runtime, such as those related to configuration, authentication, and authorization.
It helps to uncover flaws that could be missed by static analysis, ensuring that the application behaves as expected under various conditions and attack scenarios.
Comparing and Contrasting SAST and DAST
SAST and DAST are complementary security testing methods, each with its own strengths and weaknesses. Understanding these differences allows for a more effective and comprehensive security strategy.
| Feature | SAST (Static Application Security Testing) | DAST (Dynamic Application Security Testing) |
|---|---|---|
| Testing Approach | Analyzes source code | Tests running application |
| Access Required | Source code access required | No source code access required |
| Vulnerability Detection | Identifies vulnerabilities in the code itself (e.g., coding errors, insecure libraries) | Identifies vulnerabilities in the running application (e.g., runtime errors, misconfigurations, authentication flaws) |
| Timing | Performed early in the development lifecycle (during coding) | Performed later in the development lifecycle (during testing or staging) |
| Strengths | Early detection of vulnerabilities; identifies vulnerabilities that may not be apparent during runtime; can be integrated into the development process (e.g., IDE integration). | Identifies vulnerabilities that manifest during runtime; tests the application from an attacker’s perspective; doesn’t require source code access; detects misconfigurations. |
| Weaknesses | Can produce false positives; may not identify runtime vulnerabilities; requires source code access. | Can be slower than SAST; may not identify the exact location of the vulnerability in the code; can be affected by environment and configuration. |
SAST is best used early in the development cycle to catch vulnerabilities during coding, while DAST is employed later to assess the application’s behavior in a running environment. Combining both approaches offers a more robust security posture, covering both the code and the application’s runtime behavior.
Common DAST Vulnerabilities
DAST tools are designed to detect a wide range of vulnerabilities. Here are some of the most common issues they identify:
- SQL Injection: Exploiting vulnerabilities in database queries to access, modify, or delete sensitive data. This occurs when user-supplied data is not properly sanitized before being used in a SQL query. For example, an attacker might inject malicious code into a login form to bypass authentication.
- Cross-Site Scripting (XSS): Injecting malicious scripts into web pages viewed by other users. Attackers use XSS to steal user cookies, redirect users to malicious sites, or deface websites.
- Cross-Site Request Forgery (CSRF): Forcing an authenticated user to submit a request to a web application without their consent. An attacker can use CSRF to change a user’s password, make purchases, or perform other actions on the user’s behalf.
- Authentication and Authorization Issues: Flaws in the way a system verifies user identities and controls access to resources. This can include weak password policies, insufficient session management, or vulnerabilities in access control mechanisms.
- Server Misconfiguration: Incorrectly configured servers that expose sensitive information or provide unintended access. Examples include default credentials, outdated software, or improperly configured security headers.
- Unvalidated Redirects and Forwards: Allowing attackers to redirect users to malicious websites. This happens when a web application does not properly validate the destination URL provided in a redirect or forward operation.
- Information Disclosure: Exposing sensitive information, such as error messages, stack traces, or database credentials, to attackers. This information can be used to understand the system’s vulnerabilities and plan further attacks.
Incorporating Security into Infrastructure as Code (IaC)
Integrating security into Infrastructure as Code (IaC) is crucial for establishing a secure and consistent infrastructure. This approach allows security measures to be automated and applied across all infrastructure deployments, minimizing manual errors and ensuring that security is not an afterthought. It helps to proactively address vulnerabilities and reduce the attack surface.
Securing Infrastructure Configurations Using IaC
IaC allows for the definition and management of infrastructure through code, making it possible to embed security controls directly into infrastructure definitions. This means that security configurations, such as network settings, access controls, and encryption protocols, are defined alongside the infrastructure components.
- Policy as Code: IaC enables the implementation of “policy as code,” where security policies are defined and enforced through code. Tools like Open Policy Agent (OPA) can be integrated with IaC pipelines to evaluate infrastructure configurations against predefined policies.
- Configuration Hardening: IaC allows for the automated hardening of infrastructure components. For instance, security best practices, such as disabling unnecessary services, enabling firewalls, and applying security patches, can be incorporated into the IaC templates.
- Version Control: IaC code is typically stored in version control systems, such as Git. This allows for tracking changes, rolling back to previous versions, and collaborating on infrastructure configurations. Version control also provides an audit trail for security-related changes.
- Immutable Infrastructure: IaC facilitates the creation of immutable infrastructure. Instead of modifying existing infrastructure, new infrastructure is built from scratch with the desired configurations. This reduces the risk of configuration drift and ensures consistency.
Security Checks and Validation within IaC Pipelines
Integrating security checks and validation into IaC pipelines is a critical step in ensuring the security of deployed infrastructure. This involves performing security assessments at various stages of the IaC lifecycle.
- Static Analysis: Tools like tfsec (for Terraform) or cfn-lint (for AWS CloudFormation) can be used to perform static analysis of IaC code. These tools scan the code for common security vulnerabilities, such as misconfigured access controls, insecure network settings, and outdated software versions.
- Policy Enforcement: Integration with policy engines, such as OPA, allows for the enforcement of security policies during the IaC deployment process. These policies can define rules for resource configurations, such as the required encryption levels or the allowed instance types.
- Secret Scanning: IaC code should be scanned for hardcoded secrets, such as passwords, API keys, and database connection strings. Tools like git-secrets can be used to prevent the accidental commit of sensitive information to version control.
- Compliance Checks: IaC can be used to automate compliance checks against industry standards, such as PCI DSS, HIPAA, and CIS benchmarks. This ensures that the infrastructure meets the required security standards.
- Example of a simple tfsec rule (Terraform):
The example below illustrates how tfsec detects the use of an insecure protocol.
Rule: `aws_s3_bucket_public_read_access`
Description: Ensures S3 buckets do not have public read access.
Severity: HIGH
Resolution: Set `public_read` to false in the S3 bucket configuration.
Automating the Deployment of Secure Infrastructure
Automating the deployment of secure infrastructure through IaC is a key element in ensuring consistent and repeatable security configurations. This involves integrating security checks into the deployment pipeline and automating the deployment process.
- CI/CD Integration: IaC pipelines can be integrated with CI/CD (Continuous Integration/Continuous Deployment) systems, such as Jenkins, GitLab CI, or AWS CodePipeline. This allows for automated testing, validation, and deployment of infrastructure changes.
- Automated Testing: Security testing can be integrated into the CI/CD pipeline. This includes static analysis, dynamic analysis, and penetration testing of the infrastructure.
- Deployment Automation: The deployment process should be automated, using tools like Terraform, AWS CloudFormation, or Ansible. This ensures that infrastructure is deployed consistently and securely.
- Rollback Mechanisms: Implement rollback mechanisms to revert to a previous, known-good state if a deployment fails or a security issue is detected.
- Example of a simplified CI/CD pipeline (Terraform with GitHub Actions):
- Developer commits IaC code to a Git repository (e.g., GitHub).
- GitHub Actions triggers a workflow.
- Workflow performs static analysis using tfsec.
- Workflow runs a plan using Terraform.
- Workflow validates the plan against security policies (e.g., using OPA).
- If all checks pass, the workflow applies the Terraform configuration.
- Infrastructure is deployed or updated.
Training and Awareness Programs for Developers
Security training for developers is a critical component of a successful shift-left strategy. Equipping developers with the knowledge and skills to identify and address security vulnerabilities early in the development lifecycle significantly reduces the risk of costly remediation efforts later on. Investing in comprehensive training programs fosters a security-conscious culture within the development team, leading to more secure code and a more robust overall security posture.
Importance of Security Training for Developers
Providing developers with adequate security training is not merely a best practice; it’s a necessity in today’s threat landscape. Developers, as the primary creators of software, are the first line of defense against security vulnerabilities. Without proper training, they may inadvertently introduce flaws that attackers can exploit.Effective security training programs:
- Reduce the likelihood of vulnerabilities being introduced in the code.
- Empower developers to proactively identify and mitigate security risks.
- Promote a security-conscious mindset throughout the development lifecycle.
- Minimize the cost and time associated with fixing security bugs.
- Improve overall software quality and resilience.
Examples of Effective Security Training Modules and Content
Effective security training modules should be engaging, practical, and relevant to the developers’ daily work. The training should not be a one-time event, but rather an ongoing process of education and reinforcement.Examples of effective training modules and content include:
- Interactive Code Challenges: Offer hands-on exercises where developers practice identifying and fixing vulnerabilities in real-world code snippets. These challenges could be presented through platforms like OWASP Juice Shop or similar intentionally vulnerable applications.
- Security Awareness Videos: Create short, engaging videos that explain common security threats, attack vectors, and best practices. These videos should be easily accessible and regularly updated to reflect the evolving threat landscape.
- Live Coding Workshops: Conduct live coding sessions where security experts demonstrate secure coding techniques and best practices. These workshops can provide developers with opportunities to ask questions and receive personalized feedback.
- Gamified Training: Use gamification techniques, such as points, badges, and leaderboards, to make security training more engaging and motivating. This can help to increase participation and knowledge retention.
- Case Studies: Present real-world case studies of security breaches and vulnerabilities to illustrate the consequences of poor security practices. These case studies should highlight the impact of vulnerabilities on businesses and users. For example, a case study could analyze the Equifax data breach, emphasizing the role of known vulnerabilities in the exploitation.
Essential Security Topics for Developer Training
A comprehensive developer training program should cover a range of essential security topics. The specific topics should be tailored to the technologies and frameworks used by the development team.Essential security topics to include in a developer training program are:
- Secure Coding Principles: Teach developers the fundamental principles of secure coding, such as input validation, output encoding, and secure authentication and authorization. This should cover principles like the “Principle of Least Privilege,” where each component of the application is granted only the minimum necessary permissions to function.
- Common Web Application Vulnerabilities: Provide in-depth training on common web application vulnerabilities, such as SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and authentication and authorization flaws. Explain how these vulnerabilities work and how to prevent them.
- Secure API Development: Cover the security aspects of API development, including authentication, authorization, input validation, and rate limiting. Explain best practices for designing and implementing secure APIs, including the use of industry standards like OAuth 2.0 and OpenID Connect.
- Security Testing Methodologies: Introduce developers to various security testing methodologies, such as static analysis, dynamic analysis, and penetration testing. Explain how to use these techniques to identify and fix vulnerabilities.
- Cryptography Fundamentals: Provide a basic understanding of cryptography, including encryption, hashing, and digital signatures. Explain how to use cryptographic techniques to protect sensitive data. For example, understanding the difference between symmetric and asymmetric encryption, and when to use each, is critical.
- OWASP Top Ten: Educate developers on the OWASP Top Ten vulnerabilities, which represent the most critical web application security risks. Provide practical guidance on how to prevent these vulnerabilities.
- Security in DevOps: Integrate security into the DevOps pipeline, including automated security testing, infrastructure as code (IaC) security, and container security. This includes topics such as scanning container images for vulnerabilities.
- Security Awareness: Promote general security awareness, including topics such as phishing, social engineering, and password security. This should include recognizing and avoiding common phishing attacks, and the importance of strong, unique passwords.
- Vulnerability Management: Teach developers how to identify, assess, and prioritize vulnerabilities. This includes using vulnerability scanners and understanding vulnerability scoring systems like CVSS.
- Secure Development Lifecycle (SDLC): Introduce the SDLC and how to integrate security at each stage. This involves incorporating security considerations into the planning, design, implementation, testing, and deployment phases of software development.
Leveraging Security Tools and Technologies
To effectively “shift left” and integrate security throughout the development lifecycle, organizations need to leverage a variety of security tools and technologies. These tools automate and streamline security processes, enabling developers to identify and address vulnerabilities early in the development process. Selecting the right tools and technologies is crucial for creating a secure and efficient development environment.
Identifying a Range of Security Tools that Support the “Shift Left” Approach
The “shift left” approach relies heavily on various security tools designed to detect vulnerabilities and enforce security best practices throughout the development lifecycle. These tools can be broadly categorized based on their function and the stage of the development process they support.
- Static Application Security Testing (SAST) Tools: These tools analyze source code, bytecode, or binaries to identify security vulnerabilities, coding errors, and compliance issues. SAST tools are typically used early in the development process, during the coding phase.
- Dynamic Application Security Testing (DAST) Tools: DAST tools simulate attacks against a running application to identify vulnerabilities such as cross-site scripting (XSS), SQL injection, and other common web application security flaws. DAST tools are typically used later in the development lifecycle, during the testing and deployment phases.
- Software Composition Analysis (SCA) Tools: SCA tools identify and analyze open-source components used in an application. They scan for known vulnerabilities in these components and help manage license compliance.
- Interactive Application Security Testing (IAST) Tools: IAST tools combine elements of both SAST and DAST. They instrument the application during runtime to provide real-time vulnerability detection and contextual information about the vulnerabilities.
- Infrastructure as Code (IaC) Security Tools: These tools scan infrastructure-as-code templates (e.g., Terraform, CloudFormation) to identify misconfigurations, security vulnerabilities, and compliance issues before infrastructure is provisioned.
- Container Security Tools: These tools scan container images for vulnerabilities, malware, and misconfigurations. They also monitor running containers for suspicious activity.
- Secrets Management Tools: These tools help securely store and manage sensitive information, such as API keys, passwords, and certificates, preventing them from being hardcoded into the application.
- Security Orchestration, Automation, and Response (SOAR) Tools: SOAR tools automate security tasks, such as vulnerability scanning, incident response, and threat intelligence gathering.
Discussing How to Choose the Right Security Tools for a Specific Development Environment
Selecting the appropriate security tools requires a thorough understanding of the development environment, application architecture, and the organization’s security goals. Several factors should be considered when choosing security tools.
- Application Type and Architecture: Different application types (e.g., web applications, mobile apps, microservices) and architectures require different security tools. For instance, a web application might benefit from DAST and SAST tools, while a microservices architecture might require container security and API security tools.
- Development Language and Frameworks: Ensure that the chosen tools support the programming languages, frameworks, and libraries used in the development environment.
- Integration Capabilities: The tools should seamlessly integrate with the existing development pipeline, including the IDE, build systems, and CI/CD pipelines. This integration enables automated security testing and feedback loops.
- Accuracy and False Positive Rate: Evaluate the accuracy of the tools and the rate of false positives. High false positive rates can lead to developer frustration and wasted time.
- Scalability and Performance: The tools should be able to handle the scale of the development environment and the volume of code being analyzed. Performance should not significantly impact the development process.
- Ease of Use: The tools should be user-friendly and easy to integrate into the development workflow. Developers should be able to understand and address the findings without requiring extensive security expertise.
- Cost and Licensing: Consider the cost of the tools, including licensing fees, maintenance costs, and training requirements.
- Vendor Support and Community: Evaluate the vendor’s support, documentation, and the size of the community. A strong community can provide valuable resources and support.
- Compliance Requirements: Consider any relevant compliance requirements (e.g., PCI DSS, HIPAA) and choose tools that support those requirements.
Creating a Table with Security Tools Information
The following table provides an overview of various security tools, their functionalities, benefits, and integration points.
| Tool | Functionality | Benefits | Integration Points |
|---|---|---|---|
| SAST (e.g., SonarQube, Veracode Static Analysis) | Analyzes source code for vulnerabilities, coding errors, and compliance issues. | Early vulnerability detection, improved code quality, and adherence to coding standards. | IDE plugins, build systems (e.g., Maven, Gradle), CI/CD pipelines. |
| DAST (e.g., OWASP ZAP, Burp Suite) | Simulates attacks against a running application to identify vulnerabilities. | Identifies vulnerabilities in the deployed application, validates the effectiveness of security controls. | CI/CD pipelines, test environments. |
| SCA (e.g., Snyk, Black Duck Software) | Identifies and analyzes open-source components for vulnerabilities and license compliance. | Reduces the risk of using vulnerable open-source components, manages software licenses. | Build systems, package managers, CI/CD pipelines. |
| IaC Security (e.g., Terraform Cloud, AWS CloudFormation Guard) | Scans infrastructure-as-code templates for misconfigurations and security vulnerabilities. | Ensures secure infrastructure deployments, prevents configuration drift. | CI/CD pipelines, version control systems. |
| Container Security (e.g., Docker Security Scanning, Aqua Security) | Scans container images for vulnerabilities, malware, and misconfigurations. | Secures containerized applications, improves container image security posture. | Container registries, CI/CD pipelines, container orchestration platforms (e.g., Kubernetes). |
| Secrets Management (e.g., HashiCorp Vault, AWS Secrets Manager) | Securely stores and manages sensitive information like API keys, passwords, and certificates. | Prevents hardcoding of secrets, improves security posture, simplifies key rotation. | Application code, CI/CD pipelines, infrastructure-as-code. |
Measuring and Monitoring Security Efforts
Measuring and monitoring the effectiveness of “shift left” initiatives is crucial for demonstrating their value, identifying areas for improvement, and ensuring that security investments are yielding the desired results. Without a robust measurement framework, it’s difficult to understand the impact of these efforts and to justify continued investment in security practices. This allows organizations to continuously improve their security posture.
Importance of Measuring “Shift Left” Effectiveness
It is essential to measure the effectiveness of “shift left” initiatives for several key reasons. This measurement allows for data-driven decision-making, helping organizations optimize their security investments.
- Quantifying Return on Investment (ROI): Measuring the impact of “shift left” allows organizations to demonstrate the ROI of their security investments. By tracking metrics like reduced vulnerability remediation costs, fewer security incidents, and faster development cycles, organizations can justify continued investment in security tools and training.
- Identifying Areas for Improvement: Monitoring key metrics helps identify areas where “shift left” initiatives are not as effective as desired. This information allows for targeted improvements to processes, tools, and training programs, leading to a more robust security posture.
- Ensuring Compliance: Many regulatory frameworks and industry standards require organizations to demonstrate the effectiveness of their security controls. Measuring and monitoring “shift left” initiatives helps organizations meet these compliance requirements.
- Improving Developer Efficiency: By tracking metrics related to developer productivity and the time spent on security-related tasks, organizations can identify opportunities to streamline processes and reduce friction for developers. This leads to faster development cycles and improved developer satisfaction.
Key Performance Indicators (KPIs) for Security
Establishing relevant KPIs is essential for accurately measuring the success of “shift left” initiatives. These KPIs should be aligned with the organization’s overall security goals and should be regularly reviewed and adjusted as needed.
- Number of vulnerabilities identified during early-stage testing: This metric measures the effectiveness of SAST and other early-stage security testing methods. A decrease in the number of vulnerabilities found in later stages, such as during penetration testing, indicates that “shift left” is working.
- Time to remediate vulnerabilities: This KPI tracks the time it takes to fix identified vulnerabilities. “Shift left” initiatives should lead to a reduction in remediation time, as vulnerabilities are identified and addressed earlier in the development lifecycle.
- Cost of vulnerability remediation: Remediation costs are significantly lower when vulnerabilities are found and fixed early. Tracking this metric demonstrates the financial benefits of “shift left.”
- Number of security incidents: This is a critical measure of overall security effectiveness. A decrease in the number of security incidents indicates a stronger security posture.
- Developer satisfaction with security tools and processes: Surveys and feedback mechanisms can be used to gauge developer satisfaction. Positive feedback suggests that security practices are being integrated effectively into the development workflow.
- Percentage of code coverage by security tests: This metric measures the extent to which security tests are being applied to the codebase. Higher coverage indicates a more comprehensive security assessment.
- Mean Time to Detect (MTTD): MTTD measures the time it takes to detect a security vulnerability or incident. A lower MTTD indicates that security monitoring and detection capabilities are effective.
- Mean Time to Resolve (MTTR): MTTR measures the time it takes to resolve a security vulnerability or incident. A lower MTTR indicates that remediation processes are efficient.
Procedure for Monitoring Security Metrics and Reporting on Progress
A well-defined procedure is essential for consistently monitoring security metrics and effectively reporting on progress. This procedure should include the following steps.
- Define Metrics: Clearly define the KPIs to be tracked, ensuring they align with the organization’s security goals.
- Establish Data Collection Methods: Determine how data will be collected for each KPI. This may involve using security tools, logging systems, and survey platforms.
- Set Baseline and Targets: Establish a baseline for each KPI and set realistic targets for improvement.
- Automate Data Collection and Reporting: Automate the process of collecting and reporting on security metrics. This can be done through dashboards, automated reports, and integrated security tools.
- Regularly Review and Analyze Data: Regularly review and analyze the collected data to identify trends, anomalies, and areas for improvement.
- Generate Reports and Communicate Findings: Generate regular reports summarizing the findings and communicate them to relevant stakeholders, including developers, security teams, and management.
- Iterate and Improve: Continuously iterate on the monitoring and reporting process based on feedback and changing security needs.
For example, consider the following scenario: An organization implements SAST and DAST tools as part of its “shift left” strategy. To monitor the effectiveness, they establish the following KPIs: number of vulnerabilities identified during SAST, time to remediate vulnerabilities, and the number of security incidents. They collect data from their SAST/DAST tools and issue tracking system. They set a baseline for each KPI and establish targets for improvement (e.g., a 20% reduction in the number of vulnerabilities found in production within six months).
Monthly reports are generated, analyzing the trends and highlighting the progress toward meeting the targets. The reports are shared with the development and security teams. The data analysis allows the organization to identify specific types of vulnerabilities that are prevalent, and they then adjust their training programs and coding guidelines to address these issues, thus continuously improving their security posture.
Final Summary
In conclusion, shifting security left is not merely a trend but a crucial evolution in software development. By proactively embedding security into every phase of the development lifecycle, from design to deployment, organizations can build more secure, resilient, and reliable applications. Embracing this approach requires a commitment to continuous learning, the implementation of appropriate tools and technologies, and a culture that prioritizes security at every level.
Ultimately, shifting security left fosters a more secure and efficient development process, leading to better software and a more secure digital world.
Answers to Common Questions
What exactly does “shift left” mean in the context of software development?
Shifting security left means moving security-related activities earlier in the software development lifecycle. Instead of addressing security concerns at the end (e.g., during testing or deployment), “shift left” encourages developers to consider security from the design and coding phases.
What are the primary benefits of shifting security left?
The main benefits include early vulnerability detection, reduced remediation costs, faster release cycles, improved code quality, and a stronger overall security posture. It also fosters a security-conscious culture among developers.
How can I convince my team to adopt a “shift left” approach?
Highlight the benefits, such as cost savings and reduced risks. Provide training and support, integrate security tools into the existing workflow, and demonstrate how it improves efficiency. Start with small steps and gradually expand the approach.
What types of tools are essential for a “shift left” strategy?
Essential tools include Static Application Security Testing (SAST) tools, Dynamic Application Security Testing (DAST) tools, security linters, and tools for Infrastructure as Code (IaC) security validation. CI/CD pipeline integration is also crucial.
How do I measure the success of my “shift left” efforts?
Track metrics such as the number of vulnerabilities found early, the time to fix vulnerabilities, the cost of remediation, and the overall reduction in security incidents. Regular security audits and penetration tests can also provide valuable insights.