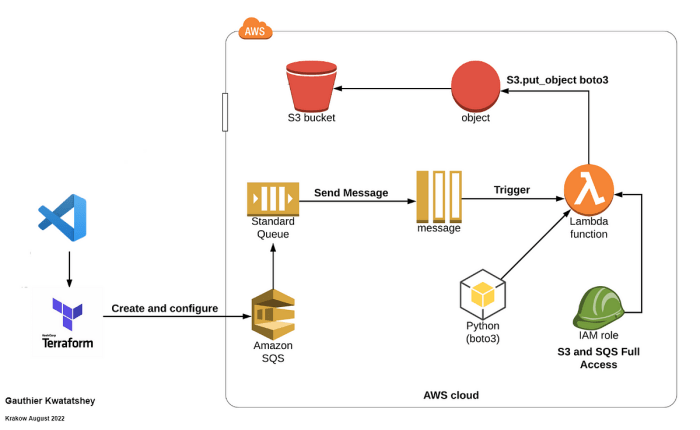
The integration of Amazon Simple Queue Service (SQS) with AWS Lambda functions provides a powerful mechanism for building scalable and event-driven applications. This architecture allows developers to decouple components, enabling asynchronous processing and improved fault tolerance. By leveraging SQS as a trigger, Lambda functions can react to messages in a queue, enabling a wide range of use cases, from processing large volumes of data to implementing complex workflows.
This document delves into the specifics of configuring and optimizing this integration. We will explore the fundamental concepts, delve into the practical steps of setting up queues and functions, and examine advanced configurations such as message filtering and error handling. Through detailed explanations and code examples, this guide aims to equip you with the knowledge to effectively utilize SQS triggers for Lambda functions in your cloud-based projects.
Introduction to SQS and Lambda Integration
The integration of Amazon Simple Queue Service (SQS) and AWS Lambda functions provides a powerful, event-driven architecture for building scalable and resilient applications. This combination allows for asynchronous processing of tasks, improving system responsiveness and handling bursts of workload efficiently. It’s a core component of many modern cloud-based solutions, offering a robust mechanism for decoupling components and enhancing overall system performance.
Core Concepts of SQS and Lambda Functions
SQS is a fully managed message queuing service. It allows applications to send, store, and receive messages between software components at any volume. Lambda, on the other hand, is a compute service that lets you run code without provisioning or managing servers. It executes code in response to events and automatically manages the underlying compute resources. The key lies in the asynchronous nature of SQS, allowing Lambda to process messages independently and concurrently.
Benefits of Using SQS as a Trigger for Lambda
Using SQS as a trigger for Lambda offers several significant advantages:
- Asynchronous Processing: SQS enables asynchronous task processing. Lambda functions are invoked when messages arrive in the queue, allowing the initiating application to continue without waiting for the processing to complete. This decoupling improves application responsiveness.
- Scalability: Lambda functions automatically scale to handle the number of messages in the queue. As the queue grows, Lambda automatically provisions and executes more function instances, ensuring that messages are processed efficiently.
- Reliability: SQS provides durable message storage. Messages are stored until a Lambda function successfully processes them and deletes them from the queue. This ensures that messages are not lost, even if a Lambda function fails.
- Decoupling: This architecture decouples the components of an application. The producer of messages (e.g., an application) doesn’t need to know about the consumer (the Lambda function). This decoupling simplifies development, deployment, and maintenance.
- Cost Efficiency: Lambda’s pay-per-use pricing model, combined with SQS’s low cost, makes this integration cost-effective, especially for intermittent workloads. You only pay for the compute time used by the Lambda functions and the number of SQS requests.
Scenario: Processing Order Events in an E-commerce Platform
Consider an e-commerce platform where customer orders are placed. When an order is placed, an event is generated. Integrating SQS and Lambda functions can handle order processing efficiently.
- Event Generation: When a customer places an order, the e-commerce application publishes an order event to an SQS queue. This event contains information about the order, such as the customer ID, order items, and total amount.
- Asynchronous Processing: A Lambda function is configured to trigger when new messages appear in the SQS queue. This function retrieves the order event from the queue.
- Order Processing Tasks: The Lambda function then performs various order processing tasks, such as:
- Validating the order data.
- Updating the inventory levels.
- Generating an invoice.
- Sending a confirmation email to the customer.
- Scalability and Resilience: If there’s a surge in orders (e.g., during a flash sale), SQS will queue the order events, and Lambda will automatically scale up to process them concurrently. If a Lambda function fails, the message remains in the queue until successfully processed, ensuring no orders are lost.
This architecture provides significant advantages. The main e-commerce application remains responsive, while the Lambda functions handle the order processing tasks in the background. The system can handle sudden spikes in order volume without performance degradation. This integration ensures the platform is scalable, reliable, and cost-effective.
Setting up an SQS Queue
Setting up an Amazon Simple Queue Service (SQS) queue is a fundamental step in building event-driven architectures that integrate with AWS Lambda functions. This process allows for the decoupling of application components, enhancing scalability, and improving the resilience of your systems. This section will guide you through the creation of an SQS queue in the AWS console, highlighting the different queue types and their respective use cases, along with the critical configuration options available.
Creating an SQS Queue in the AWS Console
Creating an SQS queue within the AWS console is a straightforward process that can be completed in a few steps. The following Artikels the key actions required to establish a new queue:
- Navigate to the SQS Service: Access the AWS Management Console and search for “SQS” in the service search bar. Click on the SQS service to enter its dashboard.
- Initiate Queue Creation: On the SQS dashboard, click the “Create queue” button. This action will lead you to the queue creation form.
- Configure Queue Details: In the “Create Queue” form, you will be prompted to provide a name for your queue. Choose a descriptive and unique name. This is a crucial step for identifying and managing your queues effectively.
- Select Queue Type: Choose between “Standard” and “FIFO” queue types. The selection is based on the requirements of your application (further details are provided in the following ).
- Configure Queue Settings: Configure various settings such as message retention period, visibility timeout, and delay seconds. These settings will affect the behavior of your queue and its interaction with Lambda functions.
- Encryption Settings: Configure encryption settings using either AWS Key Management Service (KMS) or leave the queue unencrypted. The choice depends on security needs.
- Access Policy: Define an access policy that specifies which AWS accounts and services can interact with the queue. This is crucial for controlling access and maintaining security.
- Create Queue: After configuring all the settings, click the “Create queue” button. SQS will create the queue and make it available for use.
Queue Types: Standard vs. FIFO
SQS offers two primary queue types: Standard and FIFO (First-In-First-Out). Each type is designed to meet different application requirements. Understanding the differences is crucial for selecting the appropriate queue type for your use case.
Standard Queues:
Standard queues offer high throughput and can handle a virtually unlimited number of transactions. They provide at-least-once delivery, meaning a message might be delivered more than once. The order of messages is not guaranteed, which makes them suitable for scenarios where message order is not critical, such as:
- Asynchronous Task Processing: Handling background tasks, such as image processing or video transcoding, where the order of tasks is not essential.
- Event Notification: Distributing events to multiple subscribers, such as sending notifications or updating multiple services.
- Load Leveling: Smoothing out traffic spikes by buffering messages and allowing consumers to process them at their own pace.
FIFO Queues:
FIFO queues guarantee that messages are delivered in the exact order they are sent. They also ensure that a message is processed only once. FIFO queues are designed for applications that require strict message ordering and deduplication, for example:
- Financial Transactions: Processing financial transactions where the order of operations is crucial.
- Command Execution: Executing commands in a specific order, such as in a manufacturing process.
- Inventory Management: Managing inventory updates where the order of updates is critical to maintaining data integrity.
Configuration Options for SQS Queues
When creating an SQS queue, several configuration options are available to tailor the queue’s behavior to your application’s specific needs. These options significantly influence how messages are handled, delivered, and retained. Understanding these options is essential for optimizing the performance, reliability, and cost-effectiveness of your queue.
- Message Retention Period: Specifies the duration, in seconds, that messages are retained in the queue. The default is four days, but can be set from 60 seconds (1 minute) to 1,209,600 seconds (14 days). The message retention period should be set according to how long it takes for the Lambda function to process the message. If a message is not processed within the retention period, it is automatically deleted.
- Visibility Timeout: Determines the length of time, in seconds, that a message is invisible to other consumers after it is retrieved from the queue. The default is 30 seconds. If a consumer fails to process a message within the visibility timeout, the message becomes visible again and is available for another consumer to process. This mechanism is critical for handling processing failures and preventing messages from being lost.
- Delay Seconds: Specifies the amount of time, in seconds, that a message is delayed before it becomes available for processing. The delay can range from 0 to 900 seconds (15 minutes). This can be used to control the rate at which messages are processed, or to introduce a buffer before messages are processed. For example, if a message needs to be processed at a specific time, the delay seconds can be used to schedule the message for later processing.
- Maximum Message Size: Defines the maximum size of a message that can be sent to the queue. For standard queues, the maximum message size is 256 KB, while for FIFO queues, it is 256 KB. Setting the maximum message size appropriately can prevent large messages from overwhelming the queue and impacting performance.
- Receive Message Wait Time: Sets the amount of time, in seconds, that a ReceiveMessage call waits for a message to arrive in the queue before returning. The default is 0 seconds, but can be set from 0 to 20 seconds. This can reduce the number of empty responses and improve the efficiency of message retrieval.
- Delivery Delay: Applies to FIFO queues only, and it introduces a delay before messages are available for consumption. This feature is beneficial for coordinating message delivery across various parts of a distributed system.
- Content-Based Deduplication: Used in FIFO queues to prevent the processing of duplicate messages. SQS uses message content to identify duplicates.
Creating a Lambda Function
The integration of Amazon SQS with AWS Lambda functions facilitates asynchronous processing of messages, enabling scalable and event-driven architectures. This section details the process of creating a Lambda function, including selecting a runtime environment and designing a basic function to process messages from an SQS queue. This process allows developers to build responsive and resilient applications.
Creating a Lambda Function in the AWS Console
Creating a Lambda function within the AWS console involves several steps. The console provides a user-friendly interface for defining the function’s configuration and code.
- Navigate to the AWS Lambda console. This can be accessed through the AWS Management Console, by searching for “Lambda”.
- Click “Create function.” This initiates the function creation wizard.
- Choose a function configuration method. Options include “Author from scratch,” “Use a blueprint,” or “Browse serverless app repository.” Selecting “Author from scratch” allows for a custom function definition.
- Configure basic function details. This includes:
- Function name: A unique identifier for the Lambda function.
- Runtime: The programming language and version for the function (e.g., Python 3.9, Node.js 18.x, Java 11).
- Architecture: Specifies the instruction set architecture for the function’s underlying compute environment (e.g., x86_64 or arm64).
- Configure permissions. This involves creating or selecting an execution role. The execution role grants the Lambda function permissions to access other AWS services, such as SQS. The role must include permissions for logging (e.g., writing to CloudWatch) and, in the case of SQS integration, for reading messages from the queue.
- Configure the function’s code. This is where the function logic is implemented. The code processes the messages received from the SQS queue. The console provides an in-line code editor.
- Configure the function’s trigger. The trigger specifies the event source that invokes the Lambda function. For SQS integration, the SQS queue is configured as the trigger. This configuration defines the SQS queue that the Lambda function will monitor.
- Configure additional settings. This involves adjusting memory allocation, timeout settings, and environment variables. These settings influence the function’s performance and resource consumption.
- Review and create the function. After reviewing the configuration, the function can be created.
Selecting a Runtime Environment
Choosing the appropriate runtime environment for a Lambda function is a critical design decision. The runtime environment determines the programming language and supporting libraries available to the function.
Considerations for runtime selection include:
- Programming language proficiency: The developer’s familiarity with a particular language (e.g., Python, Node.js, Java) influences development efficiency and code maintainability.
- Performance characteristics: The performance characteristics of the language and its runtime environment. Some runtimes may have faster cold start times or better performance for specific workloads.
- Available libraries and frameworks: The availability of libraries and frameworks for specific tasks. Some languages have more mature ecosystems for tasks like data processing or machine learning.
- Existing code base: Compatibility with existing code. Integrating a new function into an existing system might require using the same language as other components.
- Supported features: Lambda supports various runtimes, each with specific features and updates. The availability of the latest language features and security patches is an important consideration.
The choice of runtime environment influences several aspects of function behavior, including:
- Cold start time: The time it takes for a function to start executing when invoked for the first time or after a period of inactivity.
- Memory usage: The amount of memory the function requires to execute.
- Performance: The overall speed and efficiency of the function.
- Development and deployment complexity: The ease of developing, testing, and deploying the function.
Basic Lambda Function Code Example (Python)
A simple Lambda function, written in Python, can be designed to process messages received from an SQS queue. This example logs the message content to CloudWatch Logs.
The following Python code snippet demonstrates a basic Lambda function that logs the incoming SQS message. This function receives events from SQS and processes each message within the event. The function parses the message body and logs it.
import jsonimport logginglogger = logging.getLogger()logger.setLevel(logging.INFO)def lambda_handler(event, context): for record in event['Records']: try: message_body = json.loads(record['body']) logger.info(f"Received message: message_body") except json.JSONDecodeError: logger.error(f"Unable to decode message body: record['body']") except Exception as e: logger.error(f"An error occurred: e") return 'statusCode': 200, 'body': json.dumps('Messages processed successfully!') Explanation of the code:
- The code imports the necessary modules:
jsonfor parsing JSON messages andloggingfor logging information to CloudWatch. - The code defines a logger to log messages.
- The
lambda_handlerfunction is the entry point for the Lambda function. It receives aneventobject containing information about the triggered event (in this case, messages from the SQS queue) and acontextobject providing runtime information. - The code iterates through each record in the
Recordslist within theeventobject. Each record represents a message from the SQS queue. - The code attempts to parse the message body, which is expected to be in JSON format.
- If the parsing is successful, the code logs the message body using the
logger.info()method. - If the parsing fails (e.g., the message body is not valid JSON), the code logs an error message using the
logger.error()method. - If any other exception occurs during message processing, the code logs an error message.
- The function returns a status code and a success message.
Configuring the SQS Trigger for Lambda
Integrating Amazon SQS with AWS Lambda is a powerful pattern for building event-driven, scalable applications. This section Artikels the crucial steps for configuring an SQS queue to trigger a Lambda function, along with critical settings for managing message processing and ensuring resilience. Proper configuration is essential for optimizing performance, handling failures gracefully, and controlling costs.
Configuring the SQS Queue as a Trigger for Lambda
Configuring the SQS queue as a trigger involves associating the queue with a Lambda function, enabling the function to be invoked automatically when messages are added to the queue. This process involves several key steps, usually performed through the AWS Management Console, AWS CLI, or infrastructure-as-code tools like AWS CloudFormation or Terraform.The steps to configure the SQS trigger are as follows:
- Navigate to the AWS Lambda console and select the desired Lambda function.
- Choose the “Configuration” tab and then “Triggers”.
- Click “Add trigger”.
- Select “SQS” from the trigger options.
- Choose the SQS queue from the dropdown list. The queue must reside in the same AWS region as the Lambda function.
- Configure the trigger settings, including the batch size and any dead-letter queue settings.
- Click “Add” to create the trigger. The Lambda function will now be invoked whenever a message is added to the queue.
Specifying Batch Size and Maximum Concurrent Executions
Batch size and maximum concurrent executions are critical settings for controlling how the Lambda function processes messages from the SQS queue. These settings directly impact the function’s performance, cost, and ability to handle message volume.* Batch Size: The batch size determines the number of messages the Lambda function receives in a single invocation. Larger batch sizes can improve efficiency by reducing the number of invocations and associated overhead.
However, a larger batch size can also increase the latency if a single message in the batch causes the entire batch to fail. For example, if the batch size is set to 10, and the Lambda function processes each message individually, it will receive up to 10 messages from the queue in a single invocation. The Lambda function’s code will then process all 10 messages within that single invocation.
If one message in the batch fails, the entire batch will be retried, based on the retry policy.
Maximum Concurrent Executions
This setting controls the maximum number of concurrent instances of the Lambda function that can be running at any given time. This helps prevent the Lambda function from being overwhelmed by a large influx of messages and controls the function’s overall resource consumption. It is directly related to Lambda function concurrency. Setting a limit on concurrency helps to prevent uncontrolled scaling and potential costs associated with a large number of concurrent function invocations.
For instance, setting a maximum concurrency of 100 means that the Lambda function will not be invoked more than 100 times concurrently. If more messages arrive in the queue, they will be processed only after one or more of the current function instances complete.
Configuration Settings Comparison
Several configuration settings are available for the SQS trigger. Understanding these settings and their impact is critical for optimizing performance and ensuring application reliability.The following table compares the configuration settings for the SQS trigger, including batch size, maximum concurrency, and dead-letter queue settings.
| Setting | Description | Impact | Considerations |
|---|---|---|---|
| Batch Size | The maximum number of messages the Lambda function receives in a single invocation (1-10). | Higher batch sizes can increase throughput and reduce invocation overhead. Larger batch sizes can increase the time to process messages and increase the likelihood of the entire batch failing due to a single error. | Consider the processing time per message and the desired latency. Test different batch sizes to optimize performance. The default is 10 messages. |
| Maximum Concurrency | The maximum number of concurrent function invocations. | Controls the maximum number of function instances running concurrently, helping to manage resources and prevent over-provisioning. It impacts the scalability and cost of the function. | Set based on the expected message volume, function processing time, and desired cost. The default is the account concurrency limit. |
| Dead-Letter Queue (DLQ) | An SQS queue to which messages are sent if they cannot be processed successfully after a specified number of retries. | Provides a mechanism for handling messages that fail to be processed, allowing for debugging and reprocessing. DLQs improve application resilience and data integrity. | Configure a DLQ to capture failed messages and implement a strategy for handling them, such as manual inspection, reprocessing, or error reporting. DLQ setting can be configured for the queue itself, and in some cases, for the trigger. |
| Visibility Timeout | The duration (in seconds) that a message is invisible to other consumers after it is retrieved from the queue. | Prevents other consumers from processing a message that is already being processed by a Lambda function. Impacts how quickly messages are reprocessed if a function invocation fails. | Set based on the expected processing time of a single message. If the function fails to process a message within the visibility timeout, the message becomes visible again in the queue. |
| Filter Criteria | Specifies filter patterns for messages that the Lambda function should process. | Allows the function to process only a subset of messages in the queue based on the message attributes or content. Improves efficiency by filtering unnecessary messages. | Use to selectively trigger the function based on message content or attributes. |
Message Processing within the Lambda Function

The core functionality of integrating SQS with Lambda revolves around how the Lambda function interacts with and processes the messages retrieved from the SQS queue. This interaction involves parsing the message data, executing business logic, and implementing robust error handling to ensure data integrity and system resilience. The following sections detail the mechanics of message reception, attribute extraction, body processing, and the crucial aspects of error management within the Lambda function’s execution environment.
Receiving Messages from SQS
The Lambda function, when triggered by an SQS queue, receives an event object. This event object is a JSON structure containing an array of records, each representing a message from the queue. Each record includes detailed information about the message, such as the message body, message attributes, receipt handle, and other metadata. The function’s runtime environment automatically handles the retrieval of messages from the queue based on the configured trigger settings, such as batch size.
Extracting Message Attributes and Body
The event object passed to the Lambda function contains the message body and attributes, allowing for data processing. Extracting these components is crucial for the function’s operational logic.The message body typically contains the primary data payload. Message attributes, on the other hand, provide metadata about the message, such as timestamps, sender information, or custom application-specific data.Here is an example illustrating how to extract the message body and attributes using Python:“`pythonimport jsondef lambda_handler(event, context): for record in event[‘Records’]: message_body = json.loads(record[‘body’]) message_attributes = record[‘messageAttributes’] # Process the message body and attributes print(f”Message Body: message_body”) print(f”Message Attributes: message_attributes”) # Example of accessing a specific attribute if ‘operation’ in message_attributes: operation = message_attributes[‘operation’][‘stringValue’] print(f”Operation: operation”)“`In this example:
- The `event` object contains the SQS event data.
- The code iterates through each `record` in the `Records` array.
- `record[‘body’]` holds the message body, which is parsed using `json.loads()`.
- `record[‘messageAttributes’]` provides a dictionary of message attributes.
Error Handling Strategies
Implementing effective error handling is essential for building resilient and reliable Lambda functions. Errors can occur for various reasons, including invalid message formats, issues with downstream services, or temporary network outages. Strategies for handling these errors include retries and the use of dead-letter queues (DLQs).
- Retries: When an error occurs, Lambda functions can automatically retry processing the message. The retry behavior is configurable through the Lambda function’s configuration, allowing you to specify the number of retries and the interval between them. The default behavior varies depending on the language runtime and configuration settings. Excessive retries without addressing the root cause can lead to resource exhaustion.
- Dead-Letter Queues (DLQs): DLQs provide a mechanism for isolating messages that cannot be processed successfully after a specified number of retries. When a message fails to be processed after the configured number of retries, SQS sends the message to the DLQ. This allows for the investigation of failed messages and prevents them from blocking the processing of other messages. The DLQ is typically another SQS queue.
The DLQ’s configuration is done when the Lambda function is set up.
An example of how to configure a DLQ using the AWS Management Console:
- Navigate to the Lambda function’s configuration.
- Select “Configuration”.
- Choose “Asynchronous invocation”.
- Edit the DLQ settings to specify an SQS queue.
Error handling and DLQs are essential components in ensuring the durability and reliability of the data processing pipeline.
Handling Errors and Retries
The integration of Amazon SQS and AWS Lambda functions provides a robust framework for asynchronous processing. However, it’s crucial to account for potential failures in message processing. These failures can stem from various sources, including transient network issues, errors within the Lambda function’s code, or problems accessing external resources. Implementing effective error handling and retry mechanisms is paramount for ensuring data integrity, system resilience, and overall application reliability.
This section will delve into the built-in retry mechanisms, dead-letter queues, and the importance of monitoring and logging within this integration.
Built-in Retry Mechanisms
Lambda, when triggered by SQS, incorporates built-in retry mechanisms to handle transient errors. Understanding these mechanisms is key to designing resilient systems.The retry behavior is determined by the configuration of the Lambda function’s SQS trigger. By default, Lambda retries processing a message a certain number of times before sending it to a dead-letter queue (DLQ).
- Retry Attempts: The default retry count is typically determined by the `MaximumReceiveCount` setting on the SQS queue itself. This setting defines how many times a message can be received before being considered a failure.
- Exponential Backoff: Lambda uses an exponential backoff strategy between retries. This means the delay between retries increases with each attempt. This approach helps to avoid overwhelming downstream services during periods of instability. For instance, if a service is temporarily unavailable, the exponential backoff provides it with more time to recover.
- Visibility Timeout: When a Lambda function successfully receives a message from SQS, the message becomes invisible to other consumers for a period known as the visibility timeout. If the function fails to process the message within this timeout, the message becomes visible again and is available for another attempt. This timeout is crucial for preventing duplicate processing.
- Configurable Settings: While the default retry behavior is a good starting point, it’s often necessary to adjust these settings based on the specific requirements of the application. For example, if the application is processing critical messages, the `MaximumReceiveCount` might need to be increased.
Configuring Dead-Letter Queues (DLQs)
Dead-letter queues (DLQs) are essential for managing messages that cannot be successfully processed after multiple retries. They serve as a holding area for these messages, allowing for investigation and potential manual intervention.
Setting up a DLQ involves configuring the SQS queue to which failed messages are sent. The Lambda function’s SQS trigger must be configured to use the DLQ. When a message exceeds the maximum receive count, it is moved to the DLQ.
- DLQ Configuration: The DLQ is simply another SQS queue, typically with a different name to distinguish it from the main queue.
- Message Attributes: When a message is sent to the DLQ, it usually retains information about the number of times it was retried and the reason for the failure. This information is critical for debugging.
- Inspecting DLQ Messages: Regularly monitoring the DLQ is essential. Tools like the AWS Management Console or the AWS CLI can be used to view and analyze messages in the DLQ.
- Re-processing Messages: Messages in the DLQ can be reprocessed after the underlying issue is resolved. This might involve fixing a bug in the Lambda function or addressing an issue with an external dependency.
Monitoring Error Rates and Implementing Proper Logging
Effective monitoring and logging are critical for identifying and resolving issues related to message processing failures. These practices provide insights into the health and performance of the SQS-Lambda integration.
- Monitoring Metrics: CloudWatch metrics provide valuable insights into the performance of the SQS-Lambda integration. Key metrics to monitor include:
- ApproximateNumberOfMessagesVisible: Indicates the number of messages available for processing in the queue.
- ApproximateNumberOfMessagesNotVisible: Shows the number of messages currently being processed (or in flight).
- NumberOfMessagesSent: Represents the total number of messages sent to the queue.
- NumberOfMessagesDeleted: Shows the number of messages successfully processed and removed from the queue.
- NumberOfMessagesReceived: Indicates the total number of messages received by Lambda functions.
- ConcurrentExecutions: Monitors the number of Lambda function invocations running concurrently.
- Errors: Tracks the number of Lambda function invocations that result in errors.
- Error Rate Calculation: Calculating the error rate is crucial for assessing the system’s health. This can be done by dividing the number of errors by the total number of invocations. A consistently high error rate indicates a need for investigation and resolution.
- Logging: Comprehensive logging is essential for debugging and troubleshooting. Lambda functions should log relevant information, including:
- Message IDs: To trace the processing of specific messages.
- Timestamps: For tracking the timing of events.
- Error Messages: Detailed information about any errors that occur.
- Context Information: Information about the Lambda function’s environment, such as the function name and request ID.
- Centralized Logging: Centralizing logs using services like CloudWatch Logs allows for easier analysis and aggregation of logs from multiple Lambda functions. Log aggregation helps to identify patterns and correlations across different events.
- Alerting: Setting up alerts based on CloudWatch metrics and log patterns is crucial for proactively identifying and responding to issues. For example, an alert can be triggered if the error rate exceeds a certain threshold.
Monitoring and Logging
Effective monitoring and logging are critical for maintaining the health, performance, and reliability of an SQS-Lambda integration. By actively tracking relevant metrics and meticulously logging events, developers gain valuable insights into the system’s behavior, enabling proactive identification and resolution of potential issues. This section details the AWS tools available for monitoring and logging, along with best practices for implementing a robust monitoring and logging strategy.
Monitoring Tools in AWS
AWS provides a suite of monitoring tools designed to track the performance of various services, including SQS and Lambda. These tools allow developers to gain visibility into the system’s operation and identify potential bottlenecks or errors.
- Amazon CloudWatch: CloudWatch is the primary monitoring service in AWS. It collects, stores, and provides access to metrics and logs. It allows the creation of dashboards to visualize key performance indicators (KPIs), set alarms to trigger notifications based on predefined thresholds, and analyze logs to diagnose issues. CloudWatch integrates seamlessly with both SQS and Lambda, providing a centralized platform for monitoring the integration.
- AWS X-Ray: AWS X-Ray is a distributed tracing system that helps developers analyze and debug microservices applications. While not directly a monitoring tool in the same way as CloudWatch, X-Ray provides valuable insights into the flow of requests through the system, helping to identify performance bottlenecks and pinpoint the source of errors, particularly in complex applications involving multiple services.
Useful CloudWatch Metrics
CloudWatch provides a range of metrics that can be used to monitor the performance of an SQS-Lambda integration. Monitoring these metrics allows developers to proactively identify and address issues, ensuring the system’s reliability and performance.
- Lambda Invocations: This metric tracks the number of times the Lambda function is invoked. It provides a general overview of the function’s activity. A sudden increase in invocations might indicate a backlog in the SQS queue or an increase in the number of messages being processed. Conversely, a decrease could signal that the queue is emptying or that the function is experiencing errors.
- Lambda Errors: This metric tracks the number of errors that occur during Lambda function executions. Monitoring this metric is crucial for identifying and addressing issues within the function code or the integration itself. An increasing number of errors could indicate a problem with the message processing logic, dependencies, or the resources the function is accessing.
- Lambda Throttles: This metric indicates the number of times the Lambda function was throttled due to reaching its concurrency limits. If the function is throttled frequently, it indicates that the function’s concurrency limits need to be increased to handle the volume of messages.
- SQS ApproximateAgeOfOldestMessage: This metric tracks the age of the oldest message in the SQS queue, measured in seconds. Monitoring this metric helps to identify delays in message processing. A consistently increasing age indicates that messages are not being processed as quickly as they are being added to the queue, potentially leading to message buildup and delays.
- SQS NumberOfMessagesSent: This metric shows the total number of messages sent to the queue. It provides a general view of the load the queue is handling.
- SQS NumberOfMessagesDeleted: This metric tracks the number of messages successfully deleted from the queue.
- SQS NumberOfMessagesAvailable: This metric represents the number of messages currently available in the queue for processing. It is important to monitor this to ensure the queue does not have an ever-growing number of messages.
For example, consider a scenario where an e-commerce platform uses an SQS-Lambda integration to process order confirmations. If the `ApproximateAgeOfOldestMessage` metric consistently exceeds a certain threshold (e.g., 60 seconds), it indicates that order confirmations are not being processed in a timely manner. This could lead to a poor customer experience and potential business impacts. Investigating the cause (e.g., slow Lambda function execution, errors in the processing logic, or insufficient Lambda function concurrency) is crucial.
Logging Strategy for Lambda Function
A well-defined logging strategy is essential for debugging, troubleshooting, and monitoring the behavior of a Lambda function. This strategy should include detailed logging of messages, errors, and custom metrics.
- Logging Messages: Log messages at different severity levels (e.g., DEBUG, INFO, WARN, ERROR) to provide context about the function’s execution. Log input parameters, intermediate results, and any relevant information to facilitate debugging. Using structured logging (e.g., JSON format) makes it easier to query and analyze logs.
- Logging Errors: Capture and log all errors, including the error message, stack trace, and any relevant context. This information is critical for diagnosing and resolving issues. Consider using exception handling to gracefully catch and log errors.
- Logging Custom Metrics: Log custom metrics to track application-specific information that is not provided by default CloudWatch metrics. For example, you could log the number of successful order confirmations, the processing time for each order, or the number of retries. Custom metrics provide valuable insights into the function’s performance and behavior.
A practical approach to implementing a logging strategy involves:
- Choosing a Logging Library: Utilize a logging library (e.g., `logging` in Python, `winston` in Node.js) to structure and format log messages consistently.
- Setting Log Levels: Configure appropriate log levels to control the verbosity of the logs. Use DEBUG for detailed information during development, INFO for general operational information, WARN for potential issues, and ERROR for critical errors.
- Adding Context: Include relevant context in log messages, such as the message ID, request ID, or any other identifiers that help trace the execution flow.
- Structured Logging: Use structured logging formats like JSON to make it easier to parse and query logs. This allows for more efficient analysis using tools like CloudWatch Logs Insights.
For example, a Lambda function processing order confirmations could log the following information:“`json “level”: “INFO”, “message”: “Received order confirmation message”, “order_id”: “12345”, “timestamp”: “2024-02-29T10:00:00Z”“`This structured log entry provides information about the received message, the order ID, and the timestamp, making it easier to track and analyze the order processing flow. If an error occurs, a similar entry with an “ERROR” level and the error details would be logged, facilitating the debugging process.
Advanced Configuration Options
Event-driven architectures benefit significantly from the ability to precisely control how messages are processed. SQS, in conjunction with Lambda, offers advanced configuration options to refine message handling, enhancing efficiency and reducing unnecessary invocations. These options allow developers to optimize resource utilization and build more robust applications.
Message Filtering with SQS and Lambda Triggers
Message filtering enables Lambda functions to process only a subset of messages from an SQS queue, based on predefined criteria. This significantly improves efficiency by preventing unnecessary Lambda invocations for messages that are irrelevant to the function’s purpose.To implement message filtering, developers utilize the event source mapping configuration within the Lambda service. This configuration defines the criteria that messages must meet to trigger the Lambda function.
The criteria are specified using JSON filter patterns. When a message arrives in the SQS queue, the Lambda service evaluates the message attributes against these filter patterns. Only messages that match the filter criteria will trigger the Lambda function. This approach minimizes the number of Lambda function executions, conserving resources and reducing operational costs.
Configuring Event Source Mapping for Message Filtering
Configuring event source mapping involves setting up filter patterns within the Lambda console or through infrastructure-as-code tools. These filter patterns specify the conditions that messages must satisfy to trigger the Lambda function.
- Filter Pattern Structure: The filter pattern is a JSON document that defines the attributes to be matched and their expected values. The attributes are based on the message attributes defined when the message is sent to the SQS queue.
- Matching Logic: The Lambda service uses a matching algorithm to evaluate the filter pattern against the message attributes. Messages must satisfy all filter criteria to trigger the function.
- Attribute Definitions: The filter patterns can specify exact matches, prefix matches, or range matches, providing flexibility in defining the filter criteria.
- Resource Optimization: Filtering can dramatically reduce Lambda invocation costs, particularly when the queue receives a high volume of messages, but only a small percentage require processing.
Example: Configuring Event Source Mapping with JSON Filter
The following blockquote provides an example of a JSON filter pattern used in event source mapping. This configuration triggers the Lambda function only for messages with a specific ‘MessageType’ attribute value.
"MessageType": ["OrderCreated"]
This filter pattern triggers the Lambda function only when a message contains a message attribute named “MessageType” with a value equal to “OrderCreated”.
Security Considerations
Securing the integration between Amazon Simple Queue Service (SQS) and AWS Lambda functions is paramount to protect sensitive data and maintain the integrity of your applications. This involves implementing robust security measures at every stage, from access control to data encryption, to mitigate potential threats. A multi-layered security approach, incorporating best practices for both SQS and Lambda, is crucial for a resilient and secure system.
Securing the SQS-Lambda Integration: Best Practices
Implementing the following security best practices is essential to protect your SQS-Lambda integration from unauthorized access and data breaches.
- Least Privilege Principle: Grant only the necessary permissions to IAM roles associated with SQS and Lambda. This limits the blast radius of potential security breaches. For example, the Lambda function should only have permissions to read from the specific SQS queue and not broader access to other AWS services or resources unless absolutely required.
- Regularly Review and Update IAM Policies: Continuously assess and update IAM policies to reflect the principle of least privilege and to adapt to evolving security threats. This includes regularly reviewing access logs to identify any suspicious activity or unauthorized access attempts.
- Enable Encryption at Rest and in Transit: Encrypt messages within the SQS queue using AWS Key Management Service (KMS) and enforce HTTPS for all communication between SQS and Lambda. This ensures data confidentiality.
- Monitor for Security Events: Implement comprehensive monitoring and logging to detect and respond to security incidents. This includes monitoring CloudTrail logs for unauthorized API calls and CloudWatch metrics for unusual activity patterns.
- Use VPC Endpoints (for private access): If the Lambda function and SQS queue are in the same VPC, use VPC endpoints to ensure that all traffic remains within the AWS network, thereby enhancing security. This avoids the use of public internet.
- Implement Input Validation and Sanitization: Within the Lambda function, validate and sanitize all incoming messages to prevent injection attacks or other malicious inputs. This is a critical step to safeguard against vulnerabilities.
IAM Roles and Permissions for SQS and Lambda
IAM roles and permissions are the cornerstone of secure access control in AWS. Properly configuring these elements is critical to restrict access to SQS and Lambda resources.
- Lambda Execution Role: This role grants the Lambda function the permissions it needs to execute. The execution role should include permissions to read messages from the SQS queue (
sqs:ReceiveMessage,sqs:DeleteMessage, andsqs:GetQueueAttributes), log events to CloudWatch (logs:CreateLogGroup,logs:CreateLogStream, andlogs:PutLogEvents), and, if needed, interact with other AWS services. - SQS Queue Policy: The SQS queue policy defines which entities (e.g., Lambda functions, IAM users) have permission to access the queue. The policy should explicitly grant the Lambda function’s execution role permission to read messages from the queue. It is best practice to restrict access to the queue based on the Lambda function’s role ARN, not a wildcard or public access.
- Resource-Based Policies: In some cases, you might use resource-based policies (e.g., on the SQS queue) to control access. However, IAM roles are generally preferred for Lambda functions because they provide a more manageable and auditable way to manage permissions.
- Example IAM Policy for Lambda:
"Version": "2012-10-17", "Statement": [ "Effect": "Allow", "Action": [ "sqs:ReceiveMessage", "sqs:DeleteMessage", "sqs:GetQueueAttributes" ], "Resource": "arn:aws:sqs:REGION:ACCOUNT_ID:YOUR_QUEUE_NAME" , "Effect": "Allow", "Action": [ "logs:CreateLogGroup", "logs:CreateLogStream", "logs:PutLogEvents" ], "Resource": "arn:aws:logs:REGION:ACCOUNT_ID:log-group:/aws/lambda/YOUR_FUNCTION_NAME:*" ]
This policy grants the Lambda function the necessary permissions to interact with the specified SQS queue and CloudWatch logs.
Replace `REGION`, `ACCOUNT_ID`, `YOUR_QUEUE_NAME`, and `YOUR_FUNCTION_NAME` with your actual values.
Encrypting Messages: In Transit and At Rest
Data encryption is a fundamental security practice to protect the confidentiality of messages. Encryption ensures that even if unauthorized access occurs, the data remains unreadable without the appropriate decryption keys.
- Encryption in Transit (HTTPS): Ensure that all communication between SQS and Lambda occurs over HTTPS. AWS automatically handles the encryption in transit for SQS API calls over HTTPS. This prevents eavesdropping on the network. The configuration is handled by default.
- Encryption at Rest (KMS): Enable server-side encryption (SSE) with KMS for the SQS queue. This encrypts the messages stored in the queue. You can choose to use an AWS-managed KMS key or create a customer-managed KMS key.
- AWS-Managed KMS Key: AWS provides a default KMS key that you can use. This simplifies setup but offers less control over key management.
- Customer-Managed KMS Key: Create a customer-managed KMS key for greater control over key rotation, access control, and audit logging. This is often the preferred option for security-sensitive applications.
- Key Rotation: Regularly rotate the KMS keys to enhance security. KMS key rotation automatically updates the encryption keys used to protect your data, minimizing the impact of a compromised key. AWS KMS supports automatic key rotation for customer-managed keys.
- Example: Enabling Encryption at Rest for an SQS Queue:
- In the AWS Management Console, navigate to the SQS service.
- Select the queue you want to configure.
- Go to the “Encryption” section.
- Choose either “AWS Managed KMS Key” or “Customer Managed KMS Key”.
- If you choose “Customer Managed KMS Key”, select the KMS key you want to use.
- Save the changes.
Conclusive Thoughts
In conclusion, utilizing SQS as a trigger for Lambda functions is a crucial strategy for developing robust, scalable, and responsive applications within the AWS ecosystem. By mastering the concepts of queue creation, function configuration, and error handling, developers can unlock the full potential of this integration. Implementing appropriate monitoring and security measures ensures the reliability and protection of the system.
This combination provides a foundation for constructing resilient, event-driven architectures capable of handling diverse workloads and optimizing resource utilization.
FAQ Explained
What happens if a Lambda function fails to process a message from SQS?
By default, the message is retried. The number of retries is configurable within the SQS trigger configuration. If the function continues to fail after the configured retries, the message can be sent to a Dead Letter Queue (DLQ) for further investigation.
Can I process messages in a specific order using SQS and Lambda?
Yes, by using FIFO (First-In, First-Out) queues in SQS. FIFO queues guarantee message ordering, which is crucial for scenarios where message sequence matters. However, FIFO queues have certain limitations compared to standard queues, such as lower throughput.
How does batching work with SQS and Lambda?
When configuring the SQS trigger for a Lambda function, you can specify a batch size. The Lambda function will receive a batch of messages from the queue at once, increasing efficiency. The batch size impacts the number of messages the Lambda function processes with each invocation.
How do I monitor the performance of the SQS-Lambda integration?
AWS CloudWatch provides comprehensive monitoring capabilities. You can track metrics such as invocation counts, errors, approximate age of the oldest message, and queue depth. These metrics help you identify bottlenecks, troubleshoot issues, and optimize the performance of your application.