Zero trust networking is rapidly becoming a crucial security strategy for modern applications. This approach shifts from the traditional “trust but verify” model to a more granular and dynamic security paradigm. It requires meticulous consideration of every access point and resource, ensuring only authorized users and applications can interact. This guide delves into the key aspects of implementing zero trust networking patterns for various application types, from web and mobile apps to APIs, emphasizing the critical importance of micro-segmentation, access control, and continuous monitoring.
The guide systematically explores the practical implementation of zero trust, highlighting the specific security needs of different applications and providing actionable strategies for securing them. It emphasizes the need for a layered approach that encompasses secure coding practices, cloud security considerations, and the adaptation of existing infrastructure to the zero trust framework. This comprehensive approach ensures a robust security posture for applications in today’s complex digital landscape.
Introduction to Zero Trust Networking
Zero trust networking represents a paradigm shift in security strategy, moving away from traditional network access models that often assume trust within the network perimeter. Instead, it adopts a “never trust, always verify” approach, meticulously validating every user and device attempting to access resources, regardless of their location or network connection. This approach is crucial in today’s increasingly complex and dynamic threat landscape.Zero trust acknowledges the inherent risks of a traditional network model, where vulnerabilities and compromised devices can lead to widespread breaches.
This model fundamentally alters the traditional security strategy, making it more robust against modern threats. The core principles of zero trust are a significant departure from the assumptions of trust within the network perimeter.
Definition of Zero Trust Networking
Zero trust networking is a security model that assumes no implicit trust, either within or outside the organization’s network perimeter. Every access request, regardless of source, is meticulously validated and authorized. This approach significantly enhances security posture by treating every user and device as a potential threat and requiring continuous verification for access.
Core Principles of Zero Trust
Zero trust security contrasts sharply with traditional network security models, which often rely on perimeter defenses. The core principles underpinning zero trust include:
- Verification of every access request: Regardless of whether the user or device is internal or external, every access attempt is verified. This verification process includes authentication, authorization, and ongoing monitoring. This meticulous verification process is vital for maintaining security.
- Micro-segmentation of the network: The network is divided into smaller, isolated segments, limiting the impact of a breach. This approach minimizes the potential damage if an attacker gains access to one segment.
- Least privilege access: Users and devices are granted only the minimum access rights necessary to perform their tasks. This limits the potential damage from compromised accounts or devices.
- Continuous monitoring and analysis: The network is continuously monitored for suspicious activity, allowing for rapid detection and response to potential threats. This constant monitoring is crucial to identify and mitigate risks.
Importance of Zero Trust for Modern Applications
Modern applications often require access from a wider range of users and devices, including remote workers, contractors, and IoT devices. Zero trust ensures that these access requests are rigorously verified, mitigating the risks associated with these diverse access points. The importance of zero trust is highlighted by the increasing sophistication of cyberattacks.
Examples of Organizations Successfully Adopting Zero Trust
Numerous organizations have successfully implemented zero trust architectures, achieving significant improvements in security posture. For instance, companies in the financial sector have implemented zero trust to protect sensitive data. Furthermore, organizations in the healthcare sector have adopted zero trust to safeguard patient information. These examples demonstrate the practical application and benefits of zero trust.
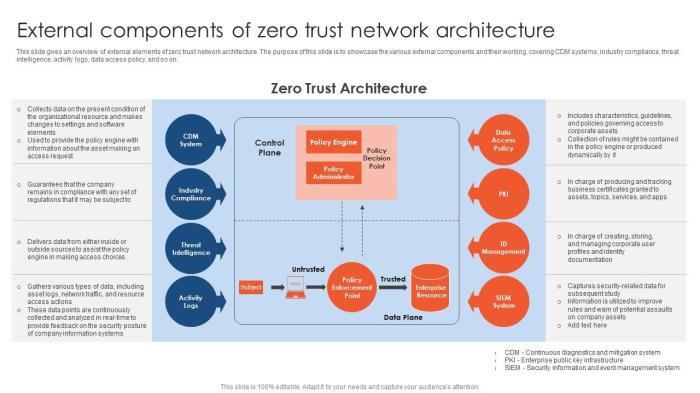
Key Components of a Zero Trust Architecture Relevant to Applications
A zero trust architecture relevant to applications incorporates several key components, ensuring robust security. These components are crucial for creating a secure environment.
- Identity and Access Management (IAM): This system is critical for verifying user and device identities. It employs robust authentication methods and authorization policies.
- Network Segmentation: The network is divided into smaller, isolated segments to limit the impact of a breach.
- Data Loss Prevention (DLP): This system protects sensitive data from unauthorized access or exfiltration.
- Security Information and Event Management (SIEM): This system monitors network activity for anomalies and suspicious behavior.
Identifying Application Security Requirements
Effective zero trust implementations hinge on a precise understanding of the security needs specific to each application type. This necessitates a thorough assessment of vulnerabilities, a prioritized approach to access control, and a robust evaluation of authentication and authorization mechanisms. A tailored strategy ensures each application operates securely within the zero trust perimeter.The diverse nature of modern applications—web, mobile, and APIs—demands a nuanced security approach.
The security requirements of each application type differ, reflecting varying attack surfaces and access patterns. Understanding these differences is critical for implementing effective zero trust policies.
Specific Security Needs of Application Types
Application types exhibit varying security needs, demanding tailored protection strategies. Web applications, for example, are often exposed to broader attack surfaces due to their public accessibility. Mobile applications, while offering convenient access, face unique risks associated with potentially compromised devices. APIs, serving as critical intermediaries, require stringent security measures to prevent unauthorized access and data breaches.
- Web Applications: Web applications frequently face cross-site scripting (XSS) and SQL injection attacks. These vulnerabilities exploit weaknesses in the application’s handling of user input, allowing malicious actors to inject harmful code. Robust input validation and parameterized queries are crucial defensive measures. Implementing secure session management and regularly updating frameworks are also vital. Consider the example of a vulnerable e-commerce website; an attacker could inject malicious scripts into product descriptions, potentially stealing customer data or manipulating transactions.
- Mobile Applications: Mobile applications are susceptible to malware infections, data breaches, and reverse engineering. Protecting sensitive data requires robust encryption, secure communication channels (like HTTPS), and strong authentication methods. The risk of compromised devices or side-channel attacks must be considered. Example: An app handling financial transactions must ensure that data is encrypted both in transit and at rest, utilizing strong encryption algorithms.
- APIs: APIs are frequently targeted due to their role as critical access points. Vulnerabilities like insecure authentication, lack of rate limiting, and inadequate authorization can compromise the entire system. Implementing robust authentication protocols, enforcing strict access controls, and incorporating rate limiting mechanisms are essential to mitigate these risks. A financial API, for example, must restrict access to authorized clients and implement rate limiting to prevent abuse or denial-of-service attacks.
Security Vulnerabilities Faced by Applications
Applications face a range of vulnerabilities, each demanding specific countermeasures. Understanding these vulnerabilities is essential to building a robust zero trust framework. Vulnerabilities can range from software flaws to misconfigurations and improper access controls.
- Injection Flaws: Injection flaws, like SQL injection and command injection, allow attackers to execute malicious code by manipulating application input. They frequently target vulnerabilities in data validation and input sanitization processes. A common example is a web application that fails to sanitize user input, allowing attackers to inject malicious SQL commands into queries.
- Cross-Site Scripting (XSS): XSS vulnerabilities enable attackers to inject malicious scripts into web pages viewed by other users. This can lead to data theft or account hijacking. A crucial countermeasure is to validate and sanitize user input.
- Broken Authentication and Session Management: Improper handling of authentication and session management allows attackers to compromise user accounts and gain unauthorized access. Secure session tokens, proper logout mechanisms, and strong password policies are essential.
Impact of Application Vulnerabilities on Zero Trust
Application vulnerabilities significantly impact the effectiveness of a zero trust strategy. A single compromised application can create a breach in the entire system, jeopardizing data and trust. A thorough understanding of application vulnerabilities is paramount to the overall zero trust strategy. The impact of a vulnerability depends on its severity and the application’s criticality within the system.
Importance of Least Privilege Access for Applications
Granting applications only the necessary access rights—the principle of least privilege—is crucial in a zero trust environment. Overprivileged applications pose a higher risk. Restricting access limits the damage potential in case of compromise. By implementing least privilege, the impact of a breach is minimized, aligning with the core principles of zero trust.
Comparison of Authentication and Authorization Methods for Zero Trust
Various authentication and authorization methods are suitable for zero trust implementations. The choice depends on the specific application needs and security requirements. Factors such as ease of implementation, scalability, and security strength influence the selection process. Examples include OAuth 2.0, JWT, and SAML.
- OAuth 2.0: OAuth 2.0 is an authorization framework that allows applications to access protected resources on behalf of users. It provides a secure and standardized way to manage access, facilitating authorization delegation.
- JSON Web Tokens (JWT): JWTs are compact, self-contained security tokens that can be used for secure communication between parties. They are frequently used for authentication and authorization in APIs and web applications.
- SAML: Security Assertion Markup Language (SAML) is an XML-based protocol used for exchanging authentication and authorization information between security providers and service providers. It enables single sign-on and federated identity management.
Implementing Micro-segmentation for Applications
Micro-segmentation is a crucial component of zero trust architecture, enabling granular control over network access for applications. It isolates application resources, limiting the blast radius of a potential security breach. This approach significantly enhances security posture by preventing lateral movement within the network. By segmenting applications based on their functions and access requirements, organizations can minimize the impact of a compromised system.
Micro-segmentation and its Role in Zero Trust
Micro-segmentation fundamentally alters the traditional network security model. Instead of broad, untrusting access, it implements a highly granular approach. Each application component, or even individual function within an application, is assigned its own network segment. This isolates potential threats and significantly reduces the attack surface. In a zero trust environment, every access request, regardless of its source or destination, is meticulously scrutinized and authorized.
Micro-segmentation is a critical element in enforcing this principle by creating tightly controlled segments.
Application Resource Access Control
Micro-segmentation controls access to application resources by creating virtual network segments for specific application components. These segments are based on logical groupings of resources and their associated security requirements. Network traffic between segments is strictly controlled through defined access policies. This ensures that only authorized users and systems can interact with specific application components. This granular control prevents unauthorized access and data exfiltration.
Methods for Segmenting Applications Based on Functions
Application segmentation is achieved by identifying logical groupings of application components. These groupings can be based on various factors, such as business function, data sensitivity, and development lifecycle stages. For instance, a web application’s front-end, database server, and back-end processing components could be segmented into distinct logical units. Furthermore, different development stages, like staging and production, can be segmented to prevent unintended access.
Examples of Micro-segmentation Policies for Different Application Types
Different application types require different segmentation policies. A web application might be segmented into front-end, application logic, and database tiers. Each tier could have its own access policies, limiting access based on user roles and responsibilities. A cloud-based application might segment based on individual services, such as storage, compute, and database instances. These policies would be tailored to the specific access requirements of each service.
Segmentation of Application Components
| Application Component | Segment Name | Access Control Policy |
|---|---|---|
| Web Server | Web Tier | Allow access only from authorized load balancers and front-end proxies. |
| Application Logic | App Logic Tier | Allow access only from the Web Tier and authorized internal services. |
| Database Server | Database Tier | Allow access only from the App Logic Tier. |
| Staging Environment | Staging Tier | Allow access only from development teams and authorized testing tools. |
Access Control and Authorization for Applications
Implementing zero trust networking requires meticulous control over application access. This involves defining granular permissions and verifying user identities to ensure only authorized individuals can interact with specific applications. Effective access control minimizes potential security breaches and protects sensitive data.Application access control mechanisms are critical for enforcing security policies and preventing unauthorized access to sensitive data and resources.
These mechanisms should be comprehensive, covering all aspects of user interaction with the application, from initial login to data manipulation.
Access Control Mechanisms
Various access control mechanisms can be implemented to secure applications. These include role-based access control (RBAC), attribute-based access control (ABAC), and policy-based access control. Each method has its strengths and weaknesses, and the optimal choice depends on the specific application and its security requirements.
- Role-Based Access Control (RBAC): This method assigns users to roles, and each role is granted specific permissions. For example, a “Sales Representative” role might be allowed to view customer data but not modify it. This approach simplifies management and ensures consistency in access permissions across different users.
- Attribute-Based Access Control (ABAC): This method grants access based on attributes of the user, resource, and environment. For instance, a user with “high-security clearance” might be allowed access to classified documents, while others may not. ABAC provides more granular control compared to RBAC.
- Policy-Based Access Control: This mechanism defines rules and policies for access control. The policies specify conditions under which a user can access a resource, making it flexible and adaptable to changing security requirements. This is particularly useful in complex environments.
Least Privilege Access
Enforcing least privilege access is crucial for minimizing the impact of a security breach. This principle limits user access to only the necessary resources and functionalities. For example, a database administrator should only have access to database modification functions, and not general file access on the system. This approach drastically reduces the potential damage if an account is compromised.
- Implementing least privilege requires a thorough understanding of the application’s functionality and the roles of each user. This understanding enables a granular control of the actions a user can perform.
- Security policies should be carefully designed to define the minimal permissions required for each user role. This approach helps prevent accidental or malicious data breaches.
- Regular audits and reviews of user permissions are essential to maintain the effectiveness of least privilege access control.
User Identity and Attribute Verification
Verifying user identity and attributes is paramount to securing application access. This involves validating the user’s credentials, such as usernames and passwords, and ensuring that the user is who they claim to be. Additional attributes like location, device, or time of access can further enhance security.
- Strong password policies and multi-factor authentication (MFA) are vital for verifying user identity.
- Using identity providers (IdPs) can simplify user authentication and provide a central repository for user data and attributes.
- Regularly reviewing and updating security policies for identity verification is necessary to stay abreast of evolving security threats.
Multi-Factor Authentication
Multi-factor authentication (MFA) adds an extra layer of security by requiring multiple forms of verification to authenticate a user. For example, a user might be required to enter a password and then confirm their identity through a one-time code sent to their mobile phone. This approach makes it significantly harder for attackers to gain access, even if they have compromised one form of authentication.
- Implementing MFA enhances the security posture of applications and protects against unauthorized access attempts.
- The choice of MFA methods should align with the sensitivity of the application and the risk tolerance of the organization.
- Continuous monitoring and evaluation of MFA effectiveness are necessary to ensure its continued effectiveness.
Access Control Models
The table below illustrates different access control models for applications.
| Access Control Model | Description | Strengths | Weaknesses |
|---|---|---|---|
| Role-Based Access Control (RBAC) | Grants access based on predefined roles | Simple to implement, manageable | Less granular control |
| Attribute-Based Access Control (ABAC) | Grants access based on user, resource, and environmental attributes | Highly granular, adaptable | Complex to implement and manage |
| Policy-Based Access Control | Defines rules and policies for access | Flexible, adaptable to changes | Requires expertise in policy definition |
Monitoring and Auditing Application Access
Effective implementation of zero trust necessitates continuous monitoring and auditing of application access. This proactive approach allows organizations to identify and address potential security vulnerabilities before they lead to breaches. By tracking access attempts and scrutinizing security events, organizations can better understand application usage patterns, detect anomalies, and respond swiftly to threats.Application access monitoring is crucial for maintaining the security posture of an organization.
Regular monitoring provides insights into user activity, potential malicious behavior, and system vulnerabilities, which is essential for maintaining a secure environment. This vigilance enables organizations to quickly identify and remediate any security gaps, thereby reducing the risk of unauthorized access and data breaches.
Importance of Monitoring Application Access Attempts
Monitoring application access attempts is vital for identifying anomalies and suspicious activity. By tracking access requests, organizations can gain valuable insights into application usage patterns, detect unusual access behaviors, and potentially identify potential security threats. Regular analysis of these attempts allows for early detection of malicious actors attempting to exploit vulnerabilities.
Methods for Detecting and Responding to Security Threats
Implementing robust security monitoring tools and techniques is paramount to detecting and responding to threats targeting applications. Employing intrusion detection systems (IDS) and intrusion prevention systems (IPS) is critical for identifying and blocking malicious activity in real-time. Security information and event management (SIEM) systems are also crucial for aggregating and analyzing security logs from various sources, enabling proactive threat detection and response.
Use of Security Information and Event Management (SIEM) Systems
Security Information and Event Management (SIEM) systems play a crucial role in consolidating security logs from various sources. They correlate events to identify potential threats and anomalies, providing a centralized view of security activity. SIEM systems automate the analysis of logs, enabling rapid identification of suspicious patterns and activities, allowing for swift response and remediation. By correlating events from different systems, SIEM systems can reveal patterns that might not be apparent in isolated logs.
Need for Regular Security Audits of Application Access
Regular security audits of application access are essential to ensure the ongoing effectiveness of security controls. These audits assess the configuration of access controls, the effectiveness of monitoring systems, and the overall security posture of applications. They help in identifying and addressing potential vulnerabilities and gaps in the security architecture. Audits provide a systematic approach to assessing the current security state and ensuring alignment with established security policies and standards.
Common Security Events and Their Potential Implications
Regular audits and monitoring of application access require understanding potential security events and their implications. This table Artikels common security events and their potential consequences:
| Security Event | Potential Implications |
|---|---|
| Unauthorized Login Attempt | Potential compromise of application, data breaches, and unauthorized access. |
| Suspicious Network Traffic | Potential denial-of-service attack, data exfiltration, or malicious activity. |
| High Volume of Failed Login Attempts | Possible brute-force attack targeting user credentials or application vulnerabilities. |
| Unusual Application Usage Patterns | Possible insider threat, data exfiltration, or malware activity. |
| Changes to Application Configuration | Unauthorized modification of application settings, potential for exploitation. |
Zero Trust and Cloud Applications
Cloud-based applications have become ubiquitous, offering scalability, flexibility, and cost-effectiveness. However, securing these applications within a zero trust framework presents unique challenges. Traditional perimeter-based security models are insufficient in the cloud environment. This section explores the specific considerations for securing cloud applications, leveraging cloud security features, and implementing zero trust principles.
Securing Cloud-Based Applications
Cloud environments, by their nature, lack a physical perimeter. Therefore, a fundamental shift in security thinking is required. Instead of relying on a single point of entry, zero trust mandates verifying and authorizing every user, device, and application request, regardless of its location within the cloud infrastructure. This granular control is crucial for preventing unauthorized access and data breaches.
Furthermore, cloud-specific security features and tools must be integrated into the zero trust strategy.
Leveraging Cloud Security Features for Zero Trust
Cloud providers offer a wealth of security features that can be leveraged to enhance zero trust implementation. These features include identity and access management (IAM) solutions, data encryption at rest and in transit, and robust network segmentation capabilities. Proper configuration and integration of these features are critical to a successful zero trust strategy. For example, implementing role-based access control (RBAC) within the cloud’s IAM system allows for fine-grained control over access to specific cloud resources.
Cloud Access Security Brokers (CASBs)
Cloud Access Security Brokers (CASBs) play a critical role in securing cloud applications within a zero trust framework. CASBs act as a central point of control for all cloud application access, providing visibility into application usage and enforcing security policies. They monitor and control access to cloud services, enabling granular control and visibility. By integrating with existing security tools, CASBs enhance overall security posture and enable real-time threat detection.
Securing Cloud-Native Applications
Cloud-native applications are designed for deployment and scaling in cloud environments. Securing these applications requires a nuanced approach that considers their distributed nature and dynamic characteristics. Zero trust principles should be implemented from the ground up, encompassing container security, microservices security, and API security. A key aspect is securing the APIs that these applications use to communicate with each other.
Implementing security at the API level helps to control access to specific functionalities and data within the application.
Example of Securing Cloud-Native Applications
A company using Kubernetes for its cloud-native application deployment can implement network policies to restrict communication between containers. These policies, enforced by the Kubernetes cluster, ensure that only authorized containers can communicate with each other. Similarly, using a CASB can provide visibility into API calls, enabling the detection of suspicious activity and enforcing access controls.
Diagram of a Cloud-Based Application in a Zero Trust Environment
[Diagram description: A cloud-based application (e.g., a web application) is depicted with a series of interconnected boxes. The boxes represent various components of the application, such as the web server, database, and API gateway. These components are connected via a secure network, with each component having its own security controls. A cloud access security broker (CASB) is depicted in the diagram as a central control point, monitoring and enforcing security policies across the cloud-based application.
External users, devices, and other applications are connected to the cloud-based application through a zero trust network access (ZTNA) gateway. Each component and connection point are secured with identity and access management (IAM) mechanisms. A robust network segmentation is visible. This diagram illustrates the key components of a zero trust cloud application security architecture. ]
Zero Trust and Containerized Applications
Containerized applications, leveraging technologies like Docker and Kubernetes, have become integral components of modern software development and deployment. However, securing these dynamic environments within a zero trust framework requires specific strategies. This section Artikels essential considerations for implementing zero trust principles in containerized application environments.
Securing Containerized Applications
Containerized applications present unique security challenges due to their dynamic nature and the potential for rapid deployment and scaling. Implementing a zero trust model necessitates a shift from traditional network access controls to granular, context-aware policies that govern access to resources based on the principle of least privilege. This approach ensures that only authorized containers and processes can access necessary resources.
Role of Container Orchestration Platforms
Container orchestration platforms like Kubernetes play a critical role in securing containerized applications. These platforms provide the infrastructure for managing and scaling container deployments. Kubernetes, in particular, offers extensive capabilities for defining and enforcing network policies, allowing administrators to control communication between containers and other resources in the network. This centralized control enables a more consistent and manageable approach to enforcing zero trust principles across the containerized environment.
Implementing Network Policies for Containers
Effective network policies are crucial for restricting access within a containerized environment. Kubernetes’ network policies provide a mechanism for defining rules that control traffic between pods (container instances) and other resources within the cluster. These policies can be configured to allow only specific communication paths, thereby limiting exposure to potential vulnerabilities. Examples include restricting access to specific services or preventing communication between pods that do not need to interact.
For instance, a policy might allow only a specific database pod to communicate with a web application pod.
Securing Container Images and Deployments
Ensuring the security of container images and deployments is paramount. Vulnerabilities in the container images themselves can compromise the entire application. Zero trust dictates that images should be scanned for vulnerabilities before deployment and that only verified, secure images are allowed into the environment. Regular updates and patches for container images are critical to maintain a robust security posture.
A pipeline approach can ensure that containers are scanned, validated, and updated on a consistent schedule.
Using Container Security Scanning Tools
Container security scanning tools are essential for proactively identifying vulnerabilities within container images and deployments. These tools analyze the container images for known vulnerabilities and provide remediation recommendations. Tools like Anchore, Clair, and Trivy can be integrated into CI/CD pipelines to automate the scanning process. These tools are instrumental in ensuring that only secure container images are used, thereby preventing malicious code from entering the system.
Zero Trust and Mobile Applications
Mobile applications are increasingly critical for businesses and individuals, providing access to sensitive data and services. However, this reliance introduces unique security challenges, especially when considering the diverse and often less-controlled environments where mobile devices operate. Securing mobile application access requires a robust and adaptable approach that goes beyond traditional security measures.Mobile applications, by their very nature, operate in a diverse and often less-controlled environment, ranging from corporate networks to public Wi-Fi hotspots.
This inherent variability necessitates a more granular and dynamic approach to security than traditional network models. The risk of data breaches and unauthorized access is amplified when these applications interact with sensitive data or systems. Zero trust principles provide a suitable framework to address these vulnerabilities.
Security Challenges of Mobile Applications
Mobile devices often lack the same level of security controls and management as traditional desktop computers. They can be easily lost, stolen, or compromised. Furthermore, the proliferation of diverse operating systems and applications further complicates security management. The use of public Wi-Fi networks adds an extra layer of risk, as these networks are often unsecured and susceptible to eavesdropping and malicious attacks.
The potential for malware and phishing attacks on mobile devices is a critical concern.
Securing Mobile Application Access
A multi-layered approach is essential for securing mobile application access. This includes strong authentication methods, such as multi-factor authentication (MFA), to verify the identity of the user. Furthermore, encryption of data both in transit and at rest is crucial. Network segmentation and access control policies can restrict access to specific resources based on user identity and device characteristics.
Regular security audits and updates to the applications themselves are essential.
Mobile Device Management (MDM) Solutions
Mobile Device Management (MDM) solutions play a vital role in securing mobile applications. These solutions provide administrators with granular control over mobile devices, including the ability to enforce security policies, deploy software updates, and remotely wipe data in case of loss or compromise. By utilizing MDM, organizations can maintain a consistent security posture across all mobile devices. Effective MDM implementation allows for the consistent enforcement of security policies across all devices.
These policies might include encryption requirements, access restrictions, and application approval processes.
Implementing Zero Trust for Mobile Applications
Implementing zero trust for mobile applications requires extending the zero trust principles to encompass mobile devices. This includes verifying the identity of the device itself, along with the user. Organizations should implement policies that mandate multi-factor authentication for mobile access. These policies must encompass all access points, regardless of whether they are on-premises or in the cloud.
The use of advanced threat detection and response tools can provide additional protection against evolving threats. Real-time monitoring of mobile application activity helps detect and respond to anomalies. Examples of zero trust principles include verifying the user and device identity, and limiting access to only the resources required.
Diagram: Security Flow for a Mobile Application
+-----------------+ +-----------------+ +-----------------+| Mobile Device | --> | Authentication | --> | Application |+-----------------+ +-----------------+ +-----------------+| (e.g., iPhone) | | Service (e.g., MFA)| | (e.g., Banking App) |+-----------------+ +-----------------+ +-----------------+ | | | | | | v v+-----------------+ +-----------------+ +-----------------+| Network Gateway | --> | Network Access | --> | Resource Server |+-----------------+ +-----------------+ +-----------------+| (e.g., Firewall) | | Control (e.g., ZT) | | (e.g., Database) |+-----------------+ +-----------------+ +-----------------+
The diagram illustrates the security flow of a mobile application accessing resources.
The mobile device initiates the request, which is verified by the authentication service. The access is granted only after successful verification of the user and device, limiting access to the required resources. The network gateway enforces zero trust principles, controlling access based on verified identities.
Summary

In conclusion, implementing zero trust networking for applications requires a holistic strategy encompassing various aspects, from application design and development to integration with existing infrastructure. This approach ensures granular control over access, minimizes vulnerabilities, and empowers organizations to effectively secure their applications in an evolving threat landscape. By adopting the principles Artikeld in this guide, organizations can confidently deploy applications while prioritizing security and minimizing risk.
General Inquiries
What are the typical challenges in integrating zero trust with legacy systems?
Integrating zero trust with legacy systems can present challenges related to compatibility, performance, and the potential disruption to existing workflows. Careful planning and phased migration strategies are crucial to mitigate these issues. Furthermore, understanding the specific vulnerabilities and access points within legacy systems is essential for developing effective security policies.
How does zero trust affect mobile application security?
Mobile applications introduce unique security challenges due to their diverse deployment environments and user access points. Zero trust principles necessitate strong authentication methods, device management, and granular control over data access to secure mobile application interactions.
What role do API gateways play in zero trust security?
API gateways act as a critical security layer in a zero trust architecture. They enforce access policies, validate user identities, and provide a central point for managing and monitoring application access, thus enhancing overall security posture.