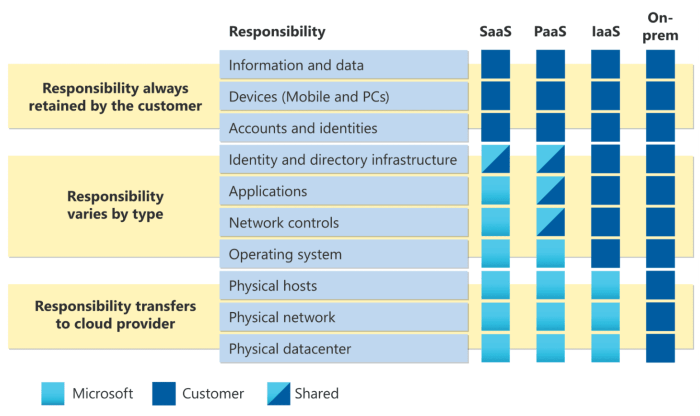
In the dynamic realm of cloud computing, understanding the shared responsibility model in cloud security is paramount. This framework delineates the security duties of both the cloud provider and the customer, creating a collaborative approach to safeguard data and applications. This guide delves into the intricacies of this model, providing a clear roadmap for navigating the complexities of cloud security and ensuring a robust security posture.
The shared responsibility model is not merely a concept; it’s a practical framework that defines how security tasks are divided. The cloud provider ensures the security of the cloud infrastructure itself, while the customer retains responsibility for securing their data and applications within that infrastructure. This collaborative effort is critical for maintaining data integrity, compliance, and overall security in the cloud environment.
Defining the Shared Responsibility Model
The Shared Responsibility Model is a fundamental concept in cloud computing security. It clarifies the security obligations of both the cloud provider and the customer. This model ensures a clear understanding of who is responsible for what, mitigating risks and promoting a robust security posture.
Core Concept of the Shared Responsibility Model
The Shared Responsibility Model dictates that security in the cloud is a joint effort. The cloud provider is responsible for securing the underlying infrastructure, including the physical hardware, networking, and virtualization layers. The customer is responsible for securing everything they put in the cloud, including their data, applications, and operating systems. This model acknowledges that the provider cannot fully secure a customer’s data and applications without the customer’s active participation.
Responsibilities of Each Party
The division of responsibilities varies depending on the cloud service model (IaaS, PaaS, SaaS). However, the core principle remains consistent: the provider secures the infrastructure “of the cloud,” while the customer secures the data and applications “in the cloud.”
- Cloud Provider Responsibilities: The cloud provider’s responsibilities generally include:
- Securing the physical infrastructure: This involves maintaining the data centers, including physical security, power, and cooling.
- Securing the virtualization layer: This encompasses the hypervisor and other virtualization components.
- Providing security of the underlying services: This includes network infrastructure, and compute services.
- Implementing security measures for the cloud infrastructure: This includes things like access control, data encryption, and threat detection.
- Ensuring compliance with relevant industry standards and regulations: This can include certifications like ISO 27001 or SOC 2.
- Customer Responsibilities: The customer’s responsibilities generally include:
- Securing their data: This includes data encryption, access control, and data backup and recovery.
- Securing their applications: This involves patching, vulnerability management, and application-level security controls.
- Securing their operating systems and virtual machines: This includes patching, configuration, and security monitoring.
- Managing user access and identities: This involves setting up access controls and managing user accounts.
- Configuring the security settings of cloud services: This includes setting up firewalls, network configurations, and other security features.
- Implementing security monitoring and logging: This involves monitoring security events and reviewing logs to identify and respond to threats.
- Compliance with internal policies and regulations.
Examples of Security Aspects
The following examples highlight the division of responsibilities:
- Provider-Managed: The provider handles the security of the physical data center. They control physical access, implement environmental controls (like temperature and humidity regulation), and manage the hardware infrastructure.
- Customer-Managed: The customer is responsible for securing the data stored in the cloud. This includes encrypting the data at rest and in transit, managing access control lists (ACLs), and implementing data loss prevention (DLP) strategies.
- Shared Responsibility: Security patching of the operating system on a virtual machine is a shared responsibility. The provider may provide the underlying infrastructure and tools for patching, but the customer is responsible for applying the patches to their virtual machines in a timely manner.
The Shared Responsibility Model is not a one-size-fits-all. The specific division of responsibilities varies based on the cloud service model (IaaS, PaaS, SaaS).
Cloud Provider Responsibilities
The cloud provider shoulders a significant portion of the security burden within the shared responsibility model. Their primary focus lies in securing the underlying infrastructure that supports cloud services. This includes everything from the physical data centers to the virtualized resources and networking components. Understanding these responsibilities is crucial for cloud consumers to effectively manage their own security posture.
Infrastructure Security Obligations
The cloud provider is responsible for the security of the infrastructure, which includes the hardware, software, networking, and facilities that support the cloud services. This commitment ensures a secure foundation for the services that customers build and deploy. This is a critical aspect because a breach at the infrastructure level can compromise all the services running on top of it.
- Physical Security: Cloud providers invest heavily in physical security measures to protect their data centers. These measures typically include:
- Multi-factor authentication for data center access, ensuring only authorized personnel can enter.
- 24/7 surveillance with security personnel, cameras, and intrusion detection systems to monitor for unauthorized activity.
- Controlled access points with biometric scanners and security checkpoints.
- Robust environmental controls, such as fire suppression systems and backup power generators, to protect against natural disasters and outages.
- Hardware Security: Providers are responsible for the security of the underlying hardware. This includes:
- Secure hardware configurations, including regular patching and updates to firmware and operating systems.
- Hardening of servers and network devices to minimize attack surfaces.
- Secure disposal of hardware to prevent data breaches when equipment is decommissioned.
- Implementing hardware-based security features, such as Trusted Platform Modules (TPMs), to protect cryptographic keys and other sensitive data.
- Network Security: Network security is another crucial area of responsibility. Providers implement various measures to secure the network infrastructure:
- Network segmentation to isolate customer environments and prevent lateral movement in case of a breach.
- Firewalls and intrusion detection/prevention systems to monitor and filter network traffic.
- DDoS protection to mitigate denial-of-service attacks.
- Secure network configurations, including regular patching and vulnerability scanning.
- Encryption of data in transit to protect data as it moves between data centers and users.
- Software Security: Cloud providers have a significant role in securing the software used to manage the cloud environment:
- Regular patching and updates to address vulnerabilities in operating systems, hypervisors, and other software components.
- Vulnerability scanning and penetration testing to identify and remediate security weaknesses.
- Secure software development practices, including code reviews and security testing, to prevent vulnerabilities from being introduced.
- Compliance with industry standards and regulations, such as ISO 27001 and SOC 2, to demonstrate a commitment to security best practices.
Customer Responsibilities
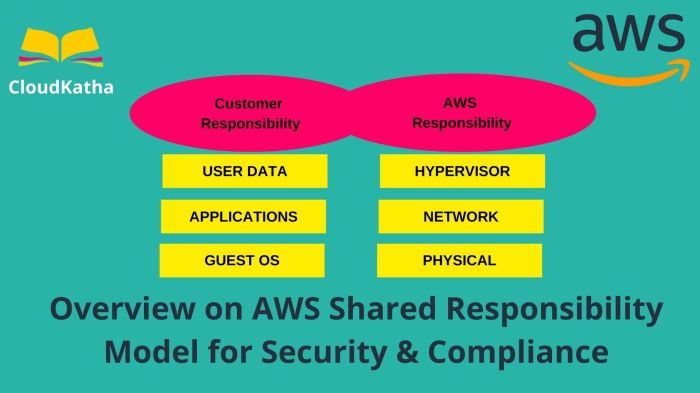
The Shared Responsibility Model clearly defines that while cloud providers secure the underlying infrastructure, customers retain significant control and, consequently, responsibility for securing their data and applications within the cloud environment. Understanding and fulfilling these responsibilities is crucial for maintaining a strong security posture and mitigating risks. This section details the key customer duties.
Securing Data and Applications
Customers are primarily responsible for the security of their data and applications hosted in the cloud. This includes a variety of tasks, all aimed at protecting information from unauthorized access, use, disclosure, disruption, modification, or destruction. The cloud provider offers tools and services to aid in these efforts, but the ultimate responsibility rests with the customer.
- Data Security: This encompasses protecting data at rest (stored data), data in transit (data moving between locations), and data in use (data actively being processed). This includes implementing appropriate encryption, access controls, and data loss prevention (DLP) measures.
- Application Security: Securing applications involves protecting against vulnerabilities, implementing secure coding practices, and regularly patching and updating software. This also includes conducting penetration testing and vulnerability assessments to identify and address potential weaknesses.
- Configuration Management: Customers must ensure that all cloud resources are configured securely. This includes setting up appropriate network configurations, firewall rules, and security groups to control network traffic and limit access.
- Monitoring and Logging: Continuous monitoring of security events and logging activities is essential for detecting and responding to security incidents. Customers should establish robust monitoring systems and regularly review logs for suspicious activity.
Identity and Access Management (IAM)
Identity and Access Management (IAM) is a critical component of cloud security. It governs who has access to what resources and under what conditions. Customers are responsible for configuring and managing IAM within their cloud environment. Properly implemented IAM significantly reduces the risk of unauthorized access and data breaches.
- User Authentication: This involves verifying the identity of users attempting to access cloud resources. Customers should utilize strong authentication methods, such as multi-factor authentication (MFA), to enhance security.
- Authorization: This involves granting users specific permissions to access resources based on their roles and responsibilities. The principle of least privilege should be applied, granting users only the necessary access they need to perform their jobs.
- Role-Based Access Control (RBAC): RBAC enables administrators to define roles with specific permissions and assign users to those roles. This simplifies access management and reduces the risk of misconfiguration.
- Regular Auditing: Regularly auditing IAM configurations and user access is essential for identifying and remediating security vulnerabilities. This involves reviewing user permissions, access logs, and configuration settings.
Data Encryption and Compliance
Data encryption and adherence to compliance requirements are essential aspects of customer responsibilities. Encryption protects data from unauthorized access, even if the underlying infrastructure is compromised. Compliance involves adhering to industry regulations and standards.
- Data Encryption: Customers must implement encryption to protect data at rest and in transit. This includes choosing appropriate encryption algorithms and key management strategies.
Encryption is often implemented using Advanced Encryption Standard (AES) algorithms. A practical example is using AES-256 encryption for sensitive data stored in a cloud-based database.
- Key Management: Securely managing encryption keys is critical. Customers can use cloud provider key management services or implement their own key management solutions. Secure key storage and rotation are essential.
- Compliance Requirements: Customers are responsible for ensuring their cloud deployments comply with relevant industry regulations and standards, such as HIPAA, PCI DSS, and GDPR. This includes implementing appropriate security controls and demonstrating compliance through audits and assessments.
- Compliance Tools: Cloud providers often offer tools and services to assist customers in achieving compliance. These tools can automate compliance checks, generate reports, and provide guidance on implementing security controls.
Differences Across Cloud Service Models (IaaS, PaaS, SaaS)
The Shared Responsibility Model isn’t a one-size-fits-all concept. Its application and the division of duties between the cloud provider and the customer change significantly depending on the cloud service model being utilized. Understanding these nuances is crucial for effectively securing your cloud environment and mitigating potential risks. The level of control and management a customer has directly impacts their security responsibilities.
Shared Responsibility Shifts
The responsibilities within the Shared Responsibility Model shift dramatically as you move up the cloud service stack, from Infrastructure as a Service (IaaS) to Platform as a Service (PaaS) and finally to Software as a Service (SaaS). In IaaS, the customer retains more control and, consequently, more responsibility for securing the operating system, applications, and data. PaaS offers a more managed environment, shifting some of those responsibilities to the provider.
SaaS, being the most managed model, places the greatest burden of security on the provider, leaving the customer with primarily data and access management responsibilities.
Responsibilities Across IaaS, PaaS, and SaaS
The following table illustrates the division of responsibilities across IaaS, PaaS, and SaaS. This comparison clarifies the specific security domains each party is accountable for in each service model. The table focuses on the key areas of responsibility to provide a clear and concise overview.
| Responsibility Area | IaaS | PaaS | SaaS |
|---|---|---|---|
| Data | Customer | Customer | Customer |
| Applications | Customer | Customer | Provider |
| Operating System | Customer | Customer | Provider |
| Middleware | Customer | Provider | Provider |
| Runtime | Customer | Provider | Provider |
| Virtualization | Provider | Provider | Provider |
| Servers | Provider | Provider | Provider |
| Networking | Provider | Provider | Provider |
| Physical Security | Provider | Provider | Provider |
The table clearly illustrates the shift in responsibilities. For example, in IaaS, the customer is responsible for securing their data, applications, and operating system. In PaaS, the provider takes on responsibility for the middleware and runtime environments, easing the customer’s burden. Finally, in SaaS, the provider handles nearly all aspects of security, with the customer primarily responsible for their data and access management.
A real-world example would be using AWS (IaaS), where a customer must manage their EC2 instance security, while with Salesforce (SaaS), the provider is responsible for most of the security.
Data Security in the Shared Responsibility Model
Data security is a crucial aspect of cloud computing, and the shared responsibility model defines how this security is managed between the cloud provider and the customer. Understanding this division of labor is essential for effectively securing your data in the cloud. It ensures that both parties take the necessary steps to protect data from unauthorized access, breaches, and loss.
Data Security Handling
The shared responsibility model for data security dictates a clear division of duties. The cloud provider is responsible for the security
- of* the cloud, while the customer is responsible for the security
- in* the cloud. This means the cloud provider secures the underlying infrastructure, including physical security, network security, and the security of the services they offer. The customer, on the other hand, is responsible for securing the data itself, along with the applications, operating systems, and access controls related to that data.
Customer Data Protection Methods
Customers must implement several data protection methods to fulfill their responsibilities within the shared responsibility model. These methods ensure the confidentiality, integrity, and availability of data stored in the cloud.
- Data Encryption: Encryption is a fundamental data protection method. Customers should encrypt data both at rest (when stored) and in transit (when being transferred). This makes the data unreadable to unauthorized parties, even if they gain access to the storage or network. For example, a financial institution storing customer payment information in the cloud would encrypt the data using robust encryption algorithms like AES-256.
This would protect the sensitive information from potential breaches.
- Access Control: Implementing robust access controls is essential. This involves defining who has access to the data, what level of access they have (read, write, execute), and regularly reviewing and updating these permissions. This includes employing multi-factor authentication (MFA) to verify user identities, thereby reducing the risk of unauthorized access. For example, a healthcare provider would use access controls to ensure that only authorized medical professionals can access patient records stored in the cloud, using MFA to enhance security.
- Data Backup and Recovery: Regularly backing up data and having a well-defined disaster recovery plan is critical. Customers must ensure that data is backed up securely and that they can restore it quickly in case of data loss or corruption. The backup strategy should include offsite backups and regular testing of the recovery process. For instance, an e-commerce company would maintain frequent backups of its customer database and order information to ensure business continuity in case of a data center outage.
- Data Loss Prevention (DLP): DLP involves implementing policies and technologies to prevent sensitive data from leaving the organization’s control. This might include monitoring network traffic, scanning for sensitive data in files, and blocking unauthorized data transfers. An example of DLP is a company that monitors employee emails for sensitive information, such as social security numbers or credit card details, and blocks any attempts to send this information outside the company.
- Data Governance: Data governance encompasses the policies, processes, and standards for managing data throughout its lifecycle. This includes defining data classification, data retention policies, and data quality standards. An example is a marketing company that establishes data governance policies to ensure the accuracy and privacy of customer data used in marketing campaigns, complying with regulations like GDPR.
Cloud Provider Role in Data Protection
Cloud providers also play a significant role in data protection, focusing on securing the underlying infrastructure and providing tools to assist customers in securing their data.
- Data at Rest Protection: Cloud providers implement various measures to protect data at rest. This includes:
- Physical Security: Ensuring the physical security of data centers through measures like access controls, surveillance, and environmental controls. This prevents unauthorized physical access to servers and storage devices.
- Storage Encryption: Offering encryption options for data stored on their infrastructure. This ensures that even if a storage device is compromised, the data remains unreadable without the proper decryption keys.
- Key Management: Providing key management services to securely store and manage encryption keys, which are crucial for decrypting the data.
- Data in Transit Protection: Cloud providers use several mechanisms to secure data in transit.
- Network Encryption: Implementing encryption protocols like TLS/SSL to encrypt data transmitted between the customer and the cloud provider’s services, as well as between services within the cloud. This prevents eavesdropping and tampering with data during transit.
- Secure Protocols: Supporting secure protocols such as HTTPS, SFTP, and SSH for data transfer, ensuring that data is transmitted securely over the network.
- Compliance Certifications: Cloud providers obtain and maintain various compliance certifications (e.g., ISO 27001, SOC 2, HIPAA) to demonstrate their commitment to data security and provide assurance to customers. These certifications help customers meet their own compliance requirements.
Identity and Access Management (IAM)
IAM is a cornerstone of cloud security, playing a critical role in the shared responsibility model. Effectively managing identities and controlling access to cloud resources is paramount for protecting data and ensuring the confidentiality, integrity, and availability of cloud services. Customers bear significant responsibility for IAM, as they are ultimately accountable for who can access their data and how.
Significance of IAM in the Shared Responsibility Model
In the shared responsibility model, IAM serves as the primary mechanism for customers to control access to their cloud resources. While cloud providers offer IAM services and infrastructure, the customer is responsible for configuring and managing these services to meet their specific security requirements. This includes defining user roles, assigning permissions, and implementing access controls that align with the principle of least privilege.
Failure to properly implement IAM can lead to unauthorized access, data breaches, and non-compliance with regulatory requirements. The provider ensures the underlying IAM infrastructure is secure and available, but the customer determines how it’s used.
Customer Management of User Access and Permissions
Customers must actively manage user access and permissions within their cloud environment. This involves creating user accounts, assigning roles, and defining policies that govern what users can do. Robust IAM practices require a deep understanding of the principle of least privilege, which dictates that users should only be granted the minimum level of access necessary to perform their job functions.
This minimizes the potential damage from compromised credentials or insider threats. Customers should also regularly review and audit user access, revoking permissions when no longer needed and ensuring that access controls are up-to-date.
Best Practices for IAM in the Cloud
Implementing strong IAM practices is crucial for securing cloud environments. The following bullet points detail essential best practices:
- Implement the Principle of Least Privilege: Grant users only the minimum necessary access to perform their tasks. This limits the potential impact of a security breach. For example, instead of giving a user “administrator” access to all resources, assign them specific permissions for the tasks they need to perform, such as read-only access to a database or the ability to create and manage virtual machines.
- Use Multi-Factor Authentication (MFA): Enable MFA for all user accounts to add an extra layer of security. This requires users to provide a second form of verification, such as a code from a mobile app or a security key, in addition to their password. MFA significantly reduces the risk of unauthorized access, even if an attacker obtains a user’s password.
- Manage and Rotate Access Keys: Regularly rotate access keys (e.g., API keys) to minimize the risk of compromise. Access keys provide programmatic access to cloud resources, so it’s essential to treat them with the same level of security as passwords. Implement automated key rotation policies to streamline this process.
- Automate User Provisioning and Deprovisioning: Use automated tools and processes to manage user accounts and permissions. This reduces the risk of human error and ensures that access is granted and revoked promptly when needed. This also improves efficiency and helps maintain consistent access control across the organization.
- Implement Role-Based Access Control (RBAC): Define roles that map to job functions and assign users to these roles. RBAC simplifies access management and ensures that users have the appropriate permissions for their responsibilities. For instance, create roles such as “Database Administrator,” “Application Developer,” and “Security Analyst,” each with pre-defined permissions.
- Monitor and Audit Access: Regularly monitor user activity and audit access logs to detect and respond to potential security incidents. Review logs for unusual activity, such as access from unexpected locations or attempts to access sensitive data. Implement security information and event management (SIEM) systems to streamline this process.
- Regularly Review and Update IAM Policies: Review and update IAM policies on a regular basis to ensure they remain effective and aligned with business needs. This includes reviewing user roles, permissions, and access controls to identify and address any vulnerabilities. This is an ongoing process that should be part of a comprehensive security program.
- Use Strong Password Policies: Enforce strong password policies, including minimum length, complexity requirements, and regular password changes. This is a fundamental security practice that helps protect user accounts from brute-force attacks and other password-based threats. Consider using password managers to assist with creating and storing strong passwords.
- Educate Users on Security Best Practices: Provide security awareness training to all users to educate them on IAM best practices and the importance of protecting their credentials. This training should cover topics such as phishing, social engineering, and password security. A well-informed user base is a critical line of defense against security threats.
Compliance and Regulatory Considerations
The shared responsibility model significantly impacts how organizations approach compliance with various regulations. Understanding this impact is crucial for cloud adoption, as it defines the division of duties between the cloud provider and the customer in ensuring regulatory adherence. This collaborative approach is essential for successfully navigating the complexities of data protection and security regulations.
Impact of the Shared Responsibility Model on Compliance
The shared responsibility model fundamentally reshapes how organizations approach compliance with regulations like GDPR, HIPAA, and PCI DSS. It does not eliminate compliance requirements; instead, it reallocates the responsibility for specific aspects of compliance between the cloud provider and the customer. The cloud provider is responsible for the security
- of* the cloud (e.g., the underlying infrastructure, data centers, and physical security), while the customer is responsible for the security
- in* the cloud (e.g., data security, access control, and application security).
Collaboration for Achieving Compliance
Achieving compliance often requires close collaboration between the cloud provider and the customer. This collaboration ensures that both parties fulfill their respective responsibilities to meet regulatory requirements.
- Cloud Provider’s Role: The cloud provider typically offers services and features designed to assist customers in achieving compliance. This includes providing compliant infrastructure, security tools, and documentation that describes how their services can be used in a compliant manner.
- Customer’s Role: Customers must configure and manage their cloud environments in a way that aligns with the specific compliance requirements. This involves implementing appropriate security controls, managing user access, and regularly monitoring their cloud resources.
- Example: GDPR Compliance: Under GDPR, both the cloud provider (acting as a data processor) and the customer (acting as a data controller) have responsibilities. The cloud provider ensures the infrastructure meets GDPR requirements, while the customer is responsible for ensuring data privacy, data subject rights, and obtaining proper consent.
- Example: HIPAA Compliance: In the context of HIPAA, the cloud provider often provides a Business Associate Agreement (BAA), outlining their commitment to protecting protected health information (PHI). The customer, however, must ensure that they use the cloud services in a way that complies with HIPAA’s security and privacy rules, including implementing appropriate safeguards for PHI.
- Example: PCI DSS Compliance: For PCI DSS compliance, the cloud provider is responsible for securing the underlying infrastructure and providing a secure environment. The customer is responsible for the security of their applications and data within that environment, including payment card data. They may need to undergo a PCI DSS assessment to demonstrate compliance.
Resources and Tools for Understanding Compliance Requirements
Numerous resources and tools are available to help customers understand and meet their compliance obligations in the cloud. These resources offer guidance, best practices, and support for navigating complex regulatory landscapes.
- Cloud Provider Documentation: Cloud providers offer extensive documentation, including compliance guides, white papers, and security best practices specific to their services. These resources detail how to configure and use services in a compliant manner.
- Compliance Checklists: Many organizations provide compliance checklists tailored to specific regulations. These checklists help customers assess their compliance posture and identify areas that need attention.
- Security Information and Event Management (SIEM) Tools: SIEM tools can help customers monitor their cloud environments, detect security threats, and generate compliance reports.
- Compliance Audits and Assessments: Customers may conduct compliance audits and assessments to validate their compliance posture. These assessments can be performed by internal teams or external auditors.
- Third-Party Compliance Solutions: Various third-party vendors offer specialized compliance solutions, including tools for automating compliance tasks, generating reports, and providing expert guidance.
- Industry Standards and Frameworks: Organizations can leverage industry standards and frameworks, such as ISO 27001, NIST, and CIS benchmarks, to enhance their compliance efforts. These frameworks provide a structured approach to security and compliance.
Incident Response and Security Operations
The Shared Responsibility Model extends to security incidents, dictating how both the cloud provider and the customer respond to and manage security breaches. Effective incident response relies on a clear understanding of each party’s obligations and coordinated efforts. This collaborative approach is crucial for minimizing damage, containing threats, and restoring services efficiently.
Shared Responsibilities During a Security Incident
The responsibilities during a security incident are split between the cloud provider and the customer. Both parties must act swiftly and effectively, following pre-defined procedures and communicating transparently. The specific distribution of responsibilities depends on the cloud service model (IaaS, PaaS, SaaS).
- Cloud Provider Responsibilities: The cloud provider is primarily responsible for the security
-of* the cloud. This includes securing the underlying infrastructure, providing security tools and services, and responding to incidents that affect the provider’s infrastructure or shared services. The provider’s responsibilities include:- Monitoring the infrastructure for suspicious activity and anomalies.
- Providing incident response capabilities, such as forensic analysis tools and support.
- Notifying customers of security incidents affecting shared services, in a timely manner.
- Implementing and maintaining security controls at the infrastructure level.
- Offering tools and resources to assist customers with their incident response efforts.
- Customer Responsibilities: The customer is responsible for the security
in* the cloud. This encompasses securing their data, applications, and workloads. The customer’s responsibilities include
- Monitoring their applications and data for suspicious activity.
- Implementing their own incident response plan.
- Investigating security incidents within their environment.
- Notifying the cloud provider of any incidents that may affect the provider’s infrastructure or shared services.
- Configuring and managing security controls for their workloads.
- Shared Responsibilities: Certain aspects of incident response are shared, requiring close collaboration. This includes:
- Coordination: Both parties must coordinate their efforts to investigate and resolve incidents.
- Communication: Transparent and timely communication is crucial to ensure everyone is informed.
- Data Sharing: Sharing relevant data, such as logs and threat intelligence, is essential for effective response.
- Containment: Both parties may need to collaborate to contain the incident and prevent further damage.
Coordination During a Security Breach
Effective coordination is the cornerstone of a successful response to a security breach. This coordination ensures that actions are aligned, communication is clear, and the incident is resolved efficiently.
- Notification and Escalation: The first step involves rapid notification.
- Customer’s Perspective: Upon detecting a security incident, the customer must immediately notify the cloud provider. The notification should include details such as the nature of the incident, the affected systems, and any initial findings. The customer also needs to follow their internal escalation procedures.
- Provider’s Perspective: The provider notifies the customer if an incident affecting shared services is detected. This notification is usually accompanied by information about the incident, the impact on the customer, and the steps the provider is taking to mitigate the issue.
- Investigation and Analysis: Both parties collaborate on investigating the breach.
- Customer’s Role: The customer investigates the incident within their environment, gathering logs, analyzing data, and identifying the root cause.
- Provider’s Role: The provider may provide support, such as forensic tools, or investigate the incident on its infrastructure. The provider analyzes the incident’s impact on shared services.
- Containment, Eradication, and Recovery: The goal is to limit damage, remove the threat, and restore normal operations.
- Containment: Both parties work to contain the incident. This may involve isolating affected systems, blocking malicious traffic, or taking other actions to prevent further damage.
- Eradication: Once the incident is contained, the focus shifts to eradicating the threat. This involves removing malware, patching vulnerabilities, and taking other steps to eliminate the root cause.
- Recovery: After eradication, the focus is on recovering affected systems and data. This may involve restoring backups, rebuilding systems, and ensuring that all systems are functioning correctly.
- Post-Incident Activities: Following the resolution, a review is conducted.
- Lessons Learned: Both parties conduct a post-incident review to identify lessons learned and improve their incident response processes.
- Documentation: All activities, findings, and actions taken during the incident are documented to create a comprehensive record.
- Improvement: The review results are used to improve security controls, incident response procedures, and communication protocols.
Procedure for Incident Response and Communication
A well-defined procedure is essential for effective incident response. This procedure Artikels the steps to be taken during an incident and ensures consistent and coordinated actions. Communication protocols are also crucial to keep all stakeholders informed.
- Preparation: Before an incident occurs, both the provider and customer should establish their incident response plans.
- Cloud Provider: The provider develops a comprehensive incident response plan, including procedures for detecting, analyzing, containing, eradicating, and recovering from security incidents. The provider establishes communication channels and protocols for notifying customers and coordinating responses.
- Customer: The customer creates an incident response plan tailored to their environment and applications. The customer identifies key personnel, defines roles and responsibilities, and establishes communication channels.
- Detection and Analysis: The first step is to detect and analyze the incident.
- Cloud Provider: The provider monitors its infrastructure and services for suspicious activity, using security tools and monitoring systems. When an incident is detected, the provider analyzes the event to determine its nature, scope, and impact.
- Customer: The customer monitors its applications and data for suspicious activity. When an incident is detected, the customer analyzes the event to understand its nature, scope, and impact.
- Containment and Eradication: Once the incident is understood, steps are taken to contain and eradicate the threat.
- Cloud Provider: The provider works to contain the incident, which may involve isolating affected systems or blocking malicious traffic. The provider takes steps to eradicate the threat, such as patching vulnerabilities or removing malware.
- Customer: The customer works to contain the incident within their environment, which may involve isolating affected systems, changing passwords, or blocking malicious traffic. The customer takes steps to eradicate the threat, such as removing malware, patching vulnerabilities, or rebuilding compromised systems.
- Recovery and Post-Incident Activities: After the threat is eradicated, the focus shifts to recovery and post-incident activities.
- Cloud Provider: The provider works to restore services and systems. The provider conducts a post-incident review to identify lessons learned and improve its incident response procedures.
- Customer: The customer works to restore their applications and data. The customer conducts a post-incident review to identify lessons learned and improve their incident response procedures.
- Communication Protocols: Effective communication is crucial throughout the incident response process.
- Notification: The cloud provider and customer must establish clear communication channels for notifying each other of security incidents.
- Updates: Regular updates should be provided to keep all stakeholders informed of the incident’s progress, including the nature of the incident, the impact, the actions being taken, and the expected resolution time.
- Escalation: Escalation procedures should be in place to ensure that critical information is escalated to the appropriate personnel.
- Documentation: All communications and actions taken during the incident should be documented to create a comprehensive record.
Security Best Practices and Recommendations
Implementing robust security practices is paramount for customers leveraging cloud services. While the cloud provider shoulders significant security responsibilities, customers retain crucial control over their data, applications, and access management. Proactive implementation of security best practices ensures a strong security posture and mitigates potential risks.
General Security Best Practices for Cloud Customers
Customers should adopt a comprehensive approach to security, encompassing various aspects of their cloud environment. This involves continuous monitoring, regular audits, and a commitment to staying informed about the latest threats and vulnerabilities.
- Implement Strong Access Controls: Employ the principle of least privilege. Grant users only the necessary permissions to perform their tasks. Regularly review and update access rights.
- Enable Multi-Factor Authentication (MFA): MFA adds an extra layer of security, requiring users to verify their identity through multiple factors (e.g., password and a code from a mobile device). This significantly reduces the risk of unauthorized access.
- Regularly Patch and Update Systems: Keep operating systems, applications, and security software up to date. Patching vulnerabilities promptly is critical to prevent exploitation by attackers.
- Encrypt Data at Rest and in Transit: Encrypting data protects it from unauthorized access, whether stored in databases or transmitted over networks. Use strong encryption algorithms.
- Monitor and Log Activity: Implement comprehensive logging and monitoring to detect suspicious activity. Regularly review logs for anomalies and potential security incidents. Establish alerts for critical events.
- Implement a Robust Backup and Disaster Recovery Plan: Back up data regularly and test the recovery process. This ensures business continuity in case of data loss or system failures.
- Conduct Regular Security Assessments: Perform vulnerability scans, penetration tests, and security audits to identify and address weaknesses in the cloud environment.
- Educate and Train Employees: Provide security awareness training to all employees. This helps them understand security risks and best practices, and prevents social engineering attacks.
- Choose Strong Passwords and Manage Them Securely: Enforce strong password policies and use a password manager to generate and store complex passwords securely. Avoid reusing passwords across different accounts.
- Stay Informed about Security Threats: Keep up-to-date with the latest security threats and vulnerabilities. Subscribe to security newsletters and follow industry best practices.
Specific Recommendations for Securing Applications and Data
Securing applications and data requires a tailored approach, considering the specific technologies and data sensitivity involved. The following recommendations provide more granular guidance.
- Secure Application Development: Integrate security into the software development lifecycle (SDLC). Use secure coding practices, conduct regular code reviews, and perform security testing throughout the development process. Consider using tools like static and dynamic analysis to identify vulnerabilities.
- Protect APIs: Secure APIs with authentication, authorization, and rate limiting. Regularly monitor API usage for suspicious activity. Document APIs thoroughly to facilitate secure integration with other systems.
- Implement Web Application Firewalls (WAFs): WAFs protect web applications from common attacks, such as cross-site scripting (XSS) and SQL injection. Configure WAFs to filter malicious traffic and block known attack patterns.
- Secure Databases: Implement strong database security measures, including access controls, encryption, and regular backups. Regularly audit database configurations for vulnerabilities. Consider using database activity monitoring to detect and respond to suspicious database activity.
- Data Loss Prevention (DLP): Implement DLP solutions to prevent sensitive data from leaving the cloud environment. Configure DLP policies to identify and block unauthorized data transfers.
- Use Container Security: For containerized applications, use container security tools to scan images for vulnerabilities, monitor container activity, and enforce security policies. Isolate containers to limit the impact of potential security breaches.
- Network Segmentation: Segment the cloud network to isolate different workloads and restrict lateral movement by attackers. Implement firewalls and network access control lists (ACLs) to control network traffic.
- Choose the Right Cloud Services: Select cloud services that align with your security requirements. Consider the security features offered by each service and how they integrate with your overall security strategy. For example, consider the use of services with built-in security features such as identity and access management (IAM), data encryption, and network security.
- Implement Intrusion Detection and Prevention Systems (IDS/IPS): Deploy IDS/IPS to monitor network traffic for malicious activity and automatically block or mitigate threats. Regularly update IDS/IPS signatures to detect the latest threats.
- Regularly Review Security Configurations: Periodically review all security configurations to ensure they are up-to-date and aligned with best practices. This includes firewall rules, access control lists, and security policies. Automated tools can assist in this process.
Resources for Further Reading and Security Training
Continuous learning is essential for staying ahead of evolving security threats. The following resources provide valuable information and training opportunities.
- Cloud Provider Documentation: Consult the official documentation of your cloud provider (e.g., AWS, Azure, Google Cloud). This documentation provides detailed information about security features, best practices, and configuration options.
- Security Standards and Frameworks: Familiarize yourself with industry-recognized security standards and frameworks, such as ISO 27001, NIST Cybersecurity Framework, and PCI DSS. These frameworks provide guidance on implementing comprehensive security programs.
- Online Security Training Platforms: Utilize online security training platforms, such as SANS Institute, Coursera, Udemy, and Cloud Academy. These platforms offer a wide range of courses and certifications on cloud security topics.
- Industry Blogs and Publications: Follow reputable security blogs and publications, such as Krebs on Security, The Hacker News, and Dark Reading. These resources provide up-to-date information on security threats, vulnerabilities, and best practices.
- Cloud Security Alliance (CSA): Join the Cloud Security Alliance (CSA) and access its resources, including the Cloud Controls Matrix (CCM) and other publications. The CSA is a non-profit organization that promotes best practices for cloud security.
- National Institute of Standards and Technology (NIST): Explore the NIST website for cybersecurity publications, including frameworks, guidelines, and standards. NIST provides valuable resources for organizations of all sizes.
- Vendor Security Bulletins and Advisories: Regularly review security bulletins and advisories from vendors of cloud services, software, and hardware. These advisories provide information about vulnerabilities and recommended mitigation steps.
- Security Conferences and Events: Attend security conferences and events, such as Black Hat, DEF CON, and RSA Conference. These events offer opportunities to learn from industry experts, network with peers, and stay up-to-date on the latest security trends.
- Security Certifications: Consider obtaining relevant security certifications, such as Certified Information Systems Security Professional (CISSP), Certified Cloud Security Professional (CCSP), and AWS Certified Security – Specialty. These certifications demonstrate expertise in cloud security.
Visualizing the Model
Understanding the shared responsibility model is significantly enhanced through visual aids. Illustrations and diagrams provide a clear and concise representation of the division of responsibilities between the cloud provider and the customer. These visuals facilitate a better grasp of complex concepts and aid in the identification of potential security gaps. They also offer a readily accessible reference point for teams, ensuring consistent understanding and adherence to security protocols.
Descriptive Illustration of the Shared Responsibility Model
The shared responsibility model can be visualized as a layered approach. Imagine a building, where the foundation and structural integrity (physical infrastructure) are entirely the responsibility of the cloud provider. This includes data centers, power, and network connectivity. The cloud provider is also responsible for securing the underlying virtualization layer, the hypervisor, and the physical security of the data centers.
The customer, on the other hand, is responsible for securing everything above this foundation.The layers above the foundation are as follows:* Infrastructure as a Service (IaaS): The cloud provider manages the underlying infrastructure. The customer is responsible for the operating system, middleware, applications, and data. The customer is also responsible for the security configurations within their virtual machines, including firewalls, intrusion detection systems, and access control.* Platform as a Service (PaaS): The cloud provider manages the underlying infrastructure, operating system, and runtime environment.
The customer is responsible for the applications and data. This means the customer needs to secure their application code, configure application-level security settings, and manage data security within the platform.* Software as a Service (SaaS): The cloud provider manages the entire stack, including the application and data. The customer is primarily responsible for data security, identity and access management (IAM), and the security configurations within the SaaS application (e.g., user permissions, data access controls).In this building analogy, the customer is responsible for the contents of their ‘apartments’ (applications and data) in each service model.
The provider ensures the building is structurally sound and secure, but the customer dictates what goes inside and how it is secured.
Diagram of Provider and Customer Responsibilities Across Service Models
A diagram can effectively illustrate the shifting responsibilities across IaaS, PaaS, and SaaS. This diagram typically takes the form of a table, clearly delineating the cloud provider’s and the customer’s roles in each service model. The table should have three main columns: Service Model (IaaS, PaaS, SaaS), Cloud Provider Responsibilities, and Customer Responsibilities.Here’s a simplified representation:
| Service Model | Cloud Provider Responsibilities | Customer Responsibilities |
|---|---|---|
| IaaS | Physical infrastructure, virtualization, networking, and underlying compute resources. | Operating systems, middleware, applications, data, identity and access management, and network security configurations within the virtual environment. |
| PaaS | Physical infrastructure, virtualization, operating systems, runtime environments, and underlying platform services. | Applications, data, application-level security configurations, and identity and access management within the platform. |
| SaaS | Physical infrastructure, virtualization, operating systems, runtime environments, applications, and data storage. | Data security, identity and access management, user access controls, and the configuration of the SaaS application security settings. |
This table-based diagram provides a quick reference for understanding the division of labor in cloud security. It helps to avoid misunderstandings and ensures that both parties are aware of their obligations. For example, in an IaaS model, if a customer fails to patch their operating system and a vulnerability is exploited, the customer is responsible for the breach, not the cloud provider.
Infographic: Flow of Security Responsibilities
An infographic is a visually appealing way to demonstrate the flow of security responsibilities. This infographic can use a flowchart-like design to show how security responsibilities shift based on the cloud service model. The infographic should begin with the underlying infrastructure, which is entirely the responsibility of the cloud provider. From there, the diagram branches out to illustrate the specific responsibilities for each service model.The infographic could include the following elements:* Start: Cloud Provider: Physical security, Data Center Operations, Hardware Security.
IaaS
Customer: Operating System Security, Application Security, Data Security, Network Security, Access Control. Cloud Provider: Underlying Infrastructure Security, Virtualization Security, Network Security.
PaaS
Customer: Application Security, Data Security, Application Access Control. Cloud Provider: Underlying Infrastructure Security, Operating System Security, Platform Security.
SaaS
Customer: Data Security, User Access Control, Application Configuration. Cloud Provider: Application Security, Data Security, Infrastructure Security.Each section could include icons representing different security aspects, such as firewalls, intrusion detection systems, data encryption, and identity management. The infographic can also use color-coding to differentiate between provider and customer responsibilities. For example, the provider’s responsibilities could be represented in blue, while the customer’s responsibilities are in orange.
This visual clarity helps to highlight the areas where responsibilities overlap and where the customer has more control and accountability.This infographic format allows for a quick understanding of the security responsibilities in a cloud environment. It can be shared across teams, departments, and with stakeholders to ensure everyone understands their roles in maintaining a secure cloud environment.
End of Discussion
In conclusion, mastering the shared responsibility model is essential for anyone venturing into the cloud. By understanding the roles and responsibilities of both the provider and the customer, organizations can build a strong security foundation. This comprehensive guide has provided a solid understanding of the model, from its core principles to practical application, and empowers readers to make informed decisions about cloud security.
Embracing this model ensures a secure and compliant cloud environment, enabling businesses to leverage the full potential of cloud computing with confidence.
Popular Questions
What happens if there’s a security breach?
The response depends on the area of responsibility. The cloud provider handles infrastructure breaches, while the customer addresses issues within their applications and data. Both parties collaborate to investigate and remediate the incident.
How do I know which security measures are my responsibility?
The cloud service model (IaaS, PaaS, or SaaS) dictates your responsibilities. The provider manages more in SaaS, while you have more control in IaaS. Review the provider’s documentation and service level agreements to clarify your duties.
Is the shared responsibility model the same for all cloud providers?
While the core concept remains the same, the specifics can vary. Each provider has its own security practices and service offerings. Always consult the provider’s documentation to understand their specific implementation of the model.
How can I ensure compliance with regulations like GDPR in the cloud?
You are responsible for ensuring your data and applications comply with regulations. The provider offers tools and services to assist, but you must configure your environment to meet compliance requirements, including data encryption, access controls, and regular audits.
What are the benefits of understanding the shared responsibility model?
Understanding the model allows you to build a robust security posture, allocate resources effectively, meet compliance requirements, and reduce the risk of data breaches. It fosters a collaborative relationship with your cloud provider for enhanced security.