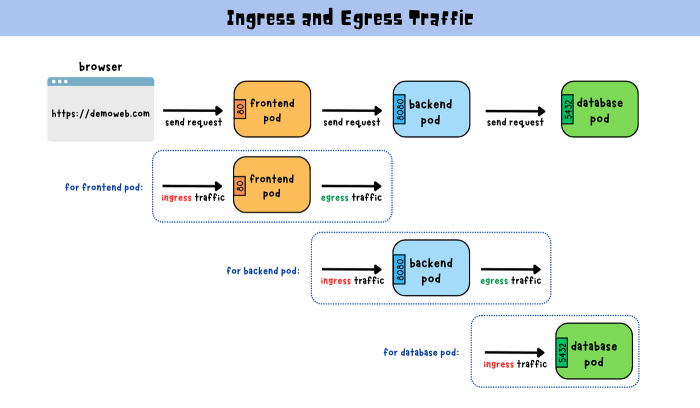
Understanding gated egress and ingress security patterns is crucial for modern network security. These patterns define how network traffic flows in and out of a system, enabling granular control and protection against unauthorized access. By strategically controlling network traffic, organizations can enhance the security posture of their infrastructure and safeguard sensitive data.
This exploration delves into the intricacies of gated security, examining various mechanisms, policy design principles, and implementation strategies. We will analyze the benefits and challenges of gated security, along with advanced techniques and future trends. Real-world case studies will illuminate the practical application of these concepts.
Introduction to Gated Egress and Ingress Security
Gated egress and ingress security are fundamental components of modern network security architectures. They represent a proactive approach to controlling the flow of network traffic, both into and out of an organization’s network, thereby mitigating potential threats. These mechanisms are crucial for protecting sensitive data, maintaining regulatory compliance, and preventing unauthorized access and malicious activity.Controlling network traffic flow is achieved by establishing security policies that define permitted and prohibited actions.
These policies are enforced by network gateways that act as checkpoints, evaluating traffic against predefined rules. This evaluation process is essential for preventing unwanted or malicious traffic from entering the network and for ensuring that sensitive data leaves the network only through authorized channels.
Key Differences Between Egress and Ingress Security
Egress security focuses on controlling outbound network traffic, ensuring that only authorized data leaves the network. Ingress security, conversely, focuses on controlling inbound traffic, preventing unauthorized access and malicious activity from entering the network. The key difference lies in the direction of traffic flow being monitored and regulated. This distinction is critical in establishing a robust security posture.
Common Use Cases for Gated Egress and Ingress Security
Gated egress and ingress security are vital in numerous scenarios. Protecting sensitive intellectual property, maintaining compliance with data privacy regulations (e.g., GDPR, HIPAA), and preventing data exfiltration are all crucial use cases. Further, they play a significant role in safeguarding against malware and phishing attacks, ensuring only legitimate users and applications have access to the network. They are essential for protecting financial institutions, healthcare organizations, and government agencies.
Comparison of Egress and Ingress Security Approaches
| Feature | Egress Security | Ingress Security |
|---|---|---|
| Direction of Control | Outbound traffic | Inbound traffic |
| Primary Goal | Preventing unauthorized data leakage and ensuring compliance | Preventing unauthorized access and malicious activity |
| Methods | Firewall rules, network segmentation, data loss prevention (DLP) tools, and content filtering. | Firewall rules, intrusion detection/prevention systems (IDS/IPS), and access control lists (ACLs). |
| Typical Concerns | Data exfiltration, insider threats, accidental data leakage. | Malware, denial-of-service (DoS) attacks, phishing attempts. |
| Examples | Restricting access to sensitive files from external users, preventing confidential documents from leaving the network. | Blocking malicious IP addresses, detecting and preventing intrusions. |
Types of Gated Security Mechanisms
Implementing robust security for network egress and ingress requires a multi-layered approach. Gated security mechanisms act as checkpoints, scrutinizing all traffic entering and leaving the network. These mechanisms are critical for enforcing security policies, preventing unauthorized access, and maintaining data integrity.
Firewall Mechanisms
Firewalls are fundamental gated security mechanisms that control network traffic based on predefined rules. They act as a gatekeeper, examining packets and allowing or denying them based on source and destination IP addresses, ports, protocols, and other criteria. A properly configured firewall can prevent unauthorized access from external networks and block malicious traffic. Different firewall types exist, including packet filtering firewalls, stateful inspection firewalls, and application firewalls, each with varying capabilities and levels of security.
Stateful inspection firewalls maintain a record of active connections, providing more granular control than packet filtering. Application firewalls delve deeper into the application layer, identifying malicious code or activities that might evade detection by other firewall types.
Network Access Control (NAC) Systems
Network Access Control (NAC) systems extend the concept of gated security by verifying the security posture of devices connecting to the network. NAC goes beyond simple access control; it assesses the configuration and security status of a device before granting access. This proactive approach helps to prevent malware or vulnerabilities from entering the network by requiring devices to meet specific security criteria.
These criteria can include antivirus updates, operating system patches, and adherence to security policies. NAC is particularly valuable in preventing the proliferation of threats through compromised devices on the network.
Intrusion Detection and Prevention Systems (IDS/IPS)
Intrusion Detection and Prevention Systems (IDS/IPS) continuously monitor network traffic for malicious activity. IDS systems detect malicious activity, while IPS systems actively block it. These systems work by identifying known attack signatures, unusual patterns, or anomalies in network behavior. IDS/IPS systems are an integral part of a gated security architecture, providing a crucial layer of defense against both known and unknown threats.
IDS/IPS systems can be deployed at various points in the network to monitor different segments.
Interaction and Complementarity of Mechanisms
These gated security mechanisms work in concert, reinforcing each other’s strengths and mitigating weaknesses. For example, a firewall might block a known malicious IP address, while an IDS/IPS system can detect and block similar attacks originating from unknown sources. NAC systems can ensure that only devices meeting security standards are allowed onto the network, thus reducing the attack surface for firewalls and IDS/IPS.
A comprehensive gated security approach involves integrating these mechanisms effectively to create a robust defense.
Strengths and Weaknesses of Gated Security Mechanisms
| Mechanism | Strengths | Weaknesses |
|---|---|---|
| Firewall | Simple to implement, relatively inexpensive, and effective at blocking known threats. | Can be bypassed by sophisticated attackers, may not detect zero-day attacks, and can be vulnerable to misconfigurations. |
| NAC | Proactively enforces security policies, reducing the attack surface by controlling device security posture. | Can be complex to implement and manage, requires significant investment in infrastructure, and may disrupt legitimate access if not configured properly. |
| IDS/IPS | Detect and prevent known and unknown attacks, providing real-time threat response. | Can generate false positives, may miss new or sophisticated attacks, and require constant updates to stay effective. |
Policy Design for Gated Security
Designing effective security policies for gated egress and ingress traffic is crucial for protecting sensitive data and applications. These policies establish clear rules and controls, ensuring only authorized users and systems can access or leave information. A well-defined policy framework acts as a critical component in the overall gated security strategy, enabling consistent enforcement and minimizing security risks.
Creating Security Policies for Gated Egress and Ingress
Developing comprehensive security policies necessitates a structured approach. Begin by identifying the critical assets and applications requiring protection. This includes categorizing data based on sensitivity levels and defining specific access controls. The policy must also Artikel acceptable traffic patterns for both egress and ingress, clearly defining what is allowed and prohibited.
Defining Acceptable Network Traffic Patterns
Defining acceptable network traffic patterns is paramount. This involves specifying the types of data that can be transmitted, the destinations allowed, and the protocols permitted. Detailed logging and monitoring are crucial for detecting deviations from these patterns and responding promptly to anomalies. For example, a policy might restrict outbound connections to specific IP ranges or services. This is especially important when dealing with sensitive data or intellectual property.
Granular Control Over Network Access
Implementing granular control over network access ensures that only authorized users and systems have access to specific resources. This involves defining specific access permissions based on user roles, application types, and data sensitivity. Such granular controls can prevent unauthorized access to critical systems and data, minimizing the impact of security breaches.
Prioritizing Sensitive Data and Applications
Prioritizing sensitive data and applications for enhanced protection is vital. This necessitates implementing stricter access controls and monitoring for these assets. Data classification and labeling mechanisms help identify sensitive data, enabling targeted security measures. Regular security assessments of these applications and their access patterns are also recommended.
Sample Policy Document for Controlling Egress and Ingress Traffic
| Policy Component | Description |
|---|---|
| Policy Name | Gated Network Access Policy |
| Policy Scope | Covers all internal network users and systems. |
| Policy Objective | To control ingress and egress traffic for improved security. |
| Egress Traffic Rules |
|
| Ingress Traffic Rules |
|
| Monitoring and Logging | All network traffic is logged and monitored for suspicious activities. Regular reports are generated and reviewed for anomalies. |
Implementing Gated Egress and Ingress Security
Implementing gated egress and ingress security is crucial for controlling network access and maintaining data integrity. This involves establishing strict rules governing what data leaves and enters the network, effectively creating a controlled environment. This structured approach significantly reduces the risk of unauthorized access and data breaches.Implementing these controls requires a meticulous understanding of network traffic patterns and a proactive approach to security policy enforcement.
This approach involves configuring network devices, monitoring traffic, and consistently updating security policies. A comprehensive gated security framework safeguards sensitive data and maintains the confidentiality and integrity of network operations.
Firewall Configuration for Gated Security
Configuring a firewall for gated security involves several steps. A detailed and well-structured policy is paramount for effective enforcement. A consistent and updated policy is critical to prevent vulnerabilities. First, define the rules that dictate the permissible egress and ingress traffic. Next, configure the firewall to enforce these rules.
Comprehensive logging is vital to monitor the network’s activity.
- Defining Egress and Ingress Rules: Explicitly Artikel the permitted sources and destinations for data leaving and entering the network. This includes defining specific protocols, ports, and IP addresses allowed for communication. Rules should be granular, allowing for flexibility while maintaining a high level of security.
- Firewall Configuration: Configure the firewall to enforce the defined rules. This involves creating access control lists (ACLs) that match traffic against the established criteria. Proper configuration ensures only authorized traffic is permitted. The ACLs should be meticulously reviewed and tested to ensure accuracy.
- Traffic Monitoring and Logging: Implement mechanisms to monitor network traffic for compliance with the established rules. Real-time logging of traffic patterns helps in identifying anomalies and potential security breaches. This data is essential for security analysis and incident response.
- Security Best Practices: Regularly review and update security policies to reflect evolving threats and network needs. This proactive approach to security management ensures the system remains secure and effective. Implement regular security audits and penetration testing to identify potential vulnerabilities. Regular patching and updates for operating systems and applications are essential to address known vulnerabilities. Employ multi-factor authentication for increased security.
Network Device Configuration for Policy Enforcement
Configuring network devices for policy enforcement involves several crucial steps. Implementing robust security measures is critical for maintaining network integrity and preventing unauthorized access. This requires careful planning and execution to avoid disruptions.
- Implementing ACLs: Configure access control lists (ACLs) on routers and switches to enforce the gated security policies. These lists filter traffic based on defined criteria, including source and destination IP addresses, protocols, and ports.
- Configuring VPNs: Implement virtual private networks (VPNs) to secure remote access to the network. VPNs encrypt data transmitted over public networks, ensuring confidentiality and integrity. Configure VPN access policies and authenticate users appropriately.
- Using Network Segmentation: Segment the network into isolated zones to limit the impact of a security breach. This isolates sensitive data and applications, reducing the risk of lateral movement.
Monitoring Network Traffic for Compliance
Monitoring network traffic for compliance is essential to ensure the security policies are effectively enforced. This proactive approach to security helps detect and respond to potential threats.
- Using Network Monitoring Tools: Utilize network monitoring tools to track traffic patterns and identify anomalies that might indicate security violations. These tools provide insights into network activity, allowing for proactive identification of potential security threats.
- Implementing Intrusion Detection/Prevention Systems (IDS/IPS): Deploy IDS/IPS systems to actively monitor network traffic for malicious activity. These systems can detect and block malicious traffic, significantly enhancing network security.
- Analyzing Logs: Regularly review security logs to identify patterns and potential vulnerabilities. Thorough analysis of log data is essential for identifying trends and taking appropriate action.
Security Considerations and Challenges
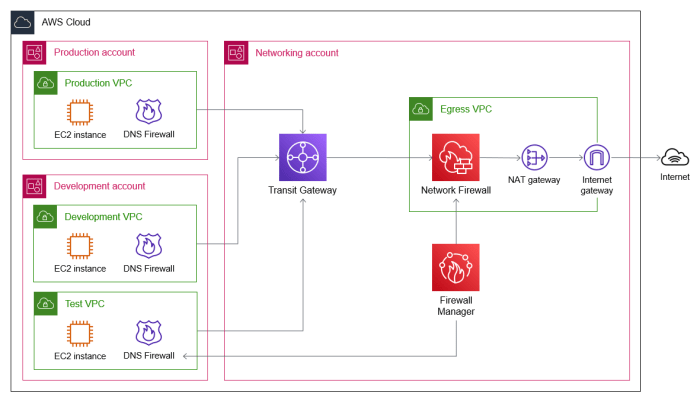
Implementing gated egress and ingress security mechanisms introduces a range of security considerations. While these mechanisms enhance overall system security, they also present challenges related to policy management, exception handling, performance, and continuous monitoring. Careful consideration of these aspects is crucial for successful deployment and maintenance.The complexity of modern network architectures, combined with the ever-evolving threat landscape, demands a robust and adaptable security posture.
Gated security, with its granular control over network traffic, requires a comprehensive understanding of potential risks and challenges.
Potential Security Risks and Vulnerabilities
Gated egress and ingress security, while providing strong controls, can introduce vulnerabilities if not properly implemented. Insufficient access control, poorly defined policies, and inadequate monitoring can create openings for malicious actors. For example, a poorly configured egress filter might inadvertently allow sensitive data to be exfiltrated, while an overly restrictive ingress policy could block legitimate access attempts. Thorough risk assessments and penetration testing are vital to identify and mitigate these potential weaknesses.
Challenges of Managing and Maintaining Complex Security Policies
Managing and maintaining a comprehensive set of security policies for gated egress and ingress can be challenging, particularly in dynamic environments. Policies must be regularly updated to reflect changes in the organization’s security posture, applications, and user needs. A lack of automation in policy management can lead to errors, inconsistencies, and increased administrative overhead. The scale and complexity of policies also necessitate well-defined processes for review, approval, and deployment to avoid introducing unintended vulnerabilities.
Handling Exceptions and Bypasses to Policies
Security policies must be flexible enough to accommodate legitimate exceptions and bypasses. Creating a clear process for requesting and approving exceptions is crucial. These processes should be documented and audited to ensure transparency and accountability. Examples include allowing access to specific servers for maintenance or specific types of traffic for testing. Automated tools can streamline the exception request process, while rigorous documentation of all exceptions is essential for future reference and audit trails.
Importance of Continuous Monitoring and Auditing
Continuous monitoring and auditing of gated egress and ingress security policies are essential for detecting and responding to security incidents. Regular audits help identify policy drift and ensure that the system remains aligned with security objectives. Monitoring tools can provide real-time visibility into network traffic, helping to detect anomalies and potential attacks. These tools should be configured to alert on unusual patterns, suspicious activity, and policy violations.
Detailed logs and audit trails should be preserved and reviewed periodically to identify potential weaknesses and vulnerabilities.
Addressing Potential Performance Bottlenecks
Implementing gated security mechanisms can potentially introduce performance bottlenecks if not carefully designed and optimized. Overly complex or poorly configured policies can lead to significant delays in network traffic processing. To mitigate these issues, network engineers should carefully evaluate the performance impact of each policy and make necessary adjustments. Using optimized network infrastructure, load balancing, and caching techniques can minimize the impact of gated security on performance.
Regular performance testing and tuning are essential to ensure optimal system performance under normal and stressed conditions.
Advanced Gated Security Techniques
Advanced gated security techniques represent a crucial evolution in securing network access, moving beyond basic ingress and egress controls to encompass a more comprehensive and adaptable approach. These methods are designed to mitigate sophisticated threats and enhance the overall security posture of an organization by employing more granular and dynamic controls. This proactive approach reduces attack surface and strengthens the defense against advanced persistent threats (APTs) and zero-day exploits.These techniques often integrate with existing security infrastructure, leveraging identity and access management (IAM) and threat intelligence to proactively identify and respond to potential threats.
The use of zero-trust architectures and microsegmentation is pivotal in achieving a more secure environment, enabling organizations to better control network access and limit the impact of a breach.
Zero-Trust Architectures
Zero-trust architectures fundamentally shift the security paradigm from a traditional “trust but verify” approach to a “never trust, always verify” model. Every user, device, and application is treated as potentially untrusted, requiring continuous authentication and authorization, regardless of their location or network affiliation. This approach dramatically reduces the attack surface by limiting access to only the necessary resources, even within the corporate network.
The implementation of microsegmentation complements this approach, providing an additional layer of control and isolation. By segmenting networks into smaller, isolated units, the impact of a compromise is contained.
Microsegmentation
Microsegmentation, a crucial component of zero-trust, isolates network resources into smaller, more manageable segments. This granular control restricts lateral movement within the network, preventing attackers from spreading their influence once a breach occurs. By isolating sensitive data and applications, microsegmentation limits the scope of a potential compromise. This isolation, in combination with strong access controls, minimizes the potential impact of a successful attack.
Identity and Access Management (IAM)
IAM plays a critical role in gated security by managing user and device identities and controlling access to resources. Robust IAM systems authenticate users and devices, assign roles, and enforce policies, ensuring that only authorized entities can access sensitive information. This is achieved through multi-factor authentication (MFA), role-based access control (RBAC), and other advanced IAM features. By integrating IAM with gated security, organizations can provide more granular access control, ensuring that only necessary access is granted, and that users are authenticated in every step of their access to sensitive information and resources.
Threat Intelligence
Threat intelligence is essential for informing gated security policies. By analyzing data on emerging threats, attack vectors, and malicious actors, organizations can proactively adjust their security policies to counter potential attacks. Integrating threat intelligence into gated security systems enables organizations to respond to threats in real-time, adjusting policies and access controls to minimize risks. Threat intelligence feeds provide real-time information, enabling rapid response to emerging threats, enhancing the security posture and reducing potential damage.
Comparison of Advanced Security Techniques
| Technique | Egress Security Enhancement | Ingress Security Enhancement |
|---|---|---|
| Zero-Trust Architecture | Stricter controls on outbound data flow, limiting unauthorized data exfiltration. | Only authorized entities are permitted to access the network. |
| Microsegmentation | Limits the impact of an egress compromise to a specific segment, preventing lateral movement. | Containment of potential ingress attacks by isolating vulnerable systems. |
| IAM | Controls user access to sensitive data leaving the network. | Ensures only authenticated users can access the network. |
| Threat Intelligence | Proactive adjustments to egress policies based on observed threats. | Proactive adjustments to ingress policies based on observed threats. |
Case Studies and Examples
Real-world implementations of gated egress and ingress security demonstrate significant improvements in data protection and network security posture. Organizations across various sectors have successfully integrated these mechanisms, achieving notable outcomes. This section explores illustrative examples and highlights the positive impacts of gated security.Implementing gated security is not a one-size-fits-all solution. Different industries and network types require tailored approaches.
This section also explores how various industries leverage gated security in specific scenarios, showcasing the adaptability of these mechanisms.
Illustrative Examples of Successful Implementations
Various organizations have successfully implemented gated egress and ingress security measures, leading to demonstrable improvements in their security posture. These implementations showcase the practicality and effectiveness of these security strategies.
- A financial institution, facing frequent attempts at unauthorized data exfiltration, implemented gated egress controls. These controls restricted access to sensitive financial data, limiting its exposure and significantly reducing the risk of data breaches. This resulted in a substantial decrease in attempted data breaches and a marked improvement in overall security.
- A healthcare provider, prioritizing patient data privacy, deployed gated ingress controls. These controls ensured only authorized devices and applications could access patient records, mitigating the risk of unauthorized access and data breaches. This approach reduced the risk of malware infections and ensured compliance with HIPAA regulations.
Positive Outcomes of Implementations
The positive outcomes of gated egress and ingress security implementations often include a reduction in data breaches, improved compliance with regulations, and enhanced network security. These benefits are quantifiable and directly impact the organization’s security posture.
- Reduced Data Breaches: Gated security mechanisms effectively restrict unauthorized access, significantly decreasing the likelihood of data breaches. This is a crucial benefit, especially in industries dealing with sensitive data.
- Improved Regulatory Compliance: Many industries are subject to strict regulations regarding data protection. Gated security helps organizations meet these compliance requirements by restricting access to sensitive information and ensuring that only authorized users can access it.
- Enhanced Network Security: By controlling both ingress and egress traffic, gated security strengthens the overall network security posture. This approach proactively safeguards against threats from external sources and internal malicious actors.
Case Study: Preventing a Data Breach
A large e-commerce company experienced a surge in suspicious outbound traffic from a specific department. Investigating the issue, security personnel discovered that a rogue employee was attempting to exfiltrate customer data. Implementing gated egress controls, specifically targeting the department’s network segment, immediately blocked the unauthorized data transfer. This proactive measure prevented a potential data breach, saving the company millions of dollars in potential fines and reputational damage.
Different Industries and Scenarios
The application of gated security varies based on the industry and the specific security needs.
| Industry | Scenario | Security Benefit |
|---|---|---|
| Healthcare | Restricting access to patient records | Ensures compliance with HIPAA regulations and protects sensitive patient data. |
| Finance | Controlling access to financial transactions | Reduces the risk of fraud and unauthorized access to sensitive financial data. |
| Government | Protecting classified information | Safeguards national security and compliance with government regulations. |
Security Benefits for Different Network Types
The benefits of gated security are applicable across various network types, including LANs, WANs, and cloud environments.
- LANs: Gated security on LANs helps contain threats within a specific network segment, preventing lateral movement and minimizing the impact of compromised systems.
- WANs: Gated security on WANs ensures that sensitive data is only transmitted to authorized destinations, mitigating the risk of data breaches over extended networks.
- Cloud Environments: Gated security in cloud environments restricts access to cloud resources, preventing unauthorized access and data exfiltration.
Monitoring and Auditing
Effective gated security relies heavily on robust monitoring and auditing mechanisms. These processes provide critical insights into policy adherence, identify potential vulnerabilities, and enable swift responses to security incidents. Thorough monitoring ensures that security policies remain effective and compliant with regulations.
Methods for Monitoring Gated Security Policies
Various methods are employed to monitor the implementation and effectiveness of gated security policies. These include continuous log collection, automated security scanning, and regular security assessments. A comprehensive approach often involves combining these techniques to gain a holistic view of security posture.
Log Analysis and SIEM
Log analysis is fundamental to understanding and responding to security events within a gated security architecture. Security Information and Event Management (SIEM) systems consolidate logs from various sources, enabling correlation and analysis of events. This allows for the identification of anomalies and potential threats that might otherwise go unnoticed. By analyzing patterns in log data, security teams can gain valuable insights into the behavior of authorized users and systems, and detect suspicious activity.
This analysis can also be used to refine security policies over time, improving their effectiveness.
Dashboards and Reports for Compliance Tracking
Dashboards and reports are crucial for visualizing compliance with gated security policies. These tools provide a summary of key metrics, such as the number of successful and failed access attempts, and the proportion of policy violations. Regular reports allow for trend analysis and proactive identification of potential issues. Visualizations can highlight discrepancies and areas requiring attention, helping to streamline the compliance process.
Identifying and Addressing Security Incidents
Monitoring systems can proactively identify and escalate security incidents, enabling rapid response and mitigation. This proactive approach minimizes the impact of breaches and maintains system integrity. Early detection and swift action are essential in managing incidents and restoring normal operations as quickly as possible. The use of predefined incident response procedures and playbooks facilitates the coordination of resources and personnel during incidents.
Ensuring Policy Effectiveness and Compliance
Regularly assessing the effectiveness of gated security policies and ensuring adherence to relevant regulations is critical. This involves conducting periodic audits to verify policy implementation and identify areas for improvement. Regular reviews should also examine the effectiveness of security controls and make adjustments as necessary to keep pace with evolving threats. Policies should be consistently reviewed and updated to reflect changes in business needs, regulatory requirements, and emerging threats.
Compliance with relevant industry standards, such as NIST Cybersecurity Framework, is crucial to demonstrate the organization’s commitment to a robust security posture.
Future Trends in Gated Security
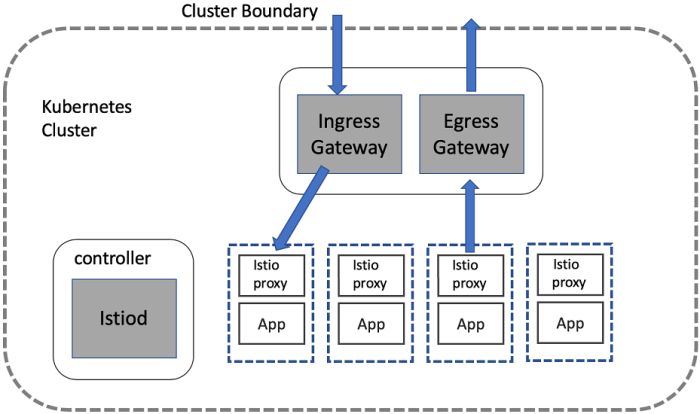
Gated egress and ingress security, while currently crucial, are poised for significant evolution. The rapid pace of technological advancements, particularly in cloud computing, containerization, and artificial intelligence, demands a proactive approach to anticipate and adapt to emerging threats. This necessitates a deep understanding of future trends to ensure ongoing effectiveness and resilience.
Emerging Trends in Gated Security
The landscape of gated security is continuously evolving, driven by innovative technologies and ever-changing threat vectors. Future trends will prioritize enhanced automation, integration with cloud environments, and leveraging advanced analytics for proactive threat detection.
Impact of Cloud Computing and Containerization
Cloud-native architectures and containerization are fundamentally altering the way applications are deployed and managed. This shift necessitates adapting gated security mechanisms to function seamlessly within these environments. Security policies must be dynamic and adaptable to the ephemeral nature of containers and the distributed nature of cloud deployments. For instance, microservices in cloud deployments require granular access control and dynamic policy adjustments based on service context and runtime characteristics.
Role of AI and Machine Learning in Enhancing Security
Artificial intelligence (AI) and machine learning (ML) are poised to play a critical role in bolstering gated security. AI-powered threat detection systems can analyze vast quantities of data in real-time to identify and respond to suspicious activities with unparalleled speed. ML algorithms can learn from historical data to predict and proactively mitigate emerging threats. Examples of this include using anomaly detection to flag unusual network traffic patterns or automatically adjusting security policies based on detected malicious activity.
Evolving Threats and Challenges
The threat landscape is constantly evolving, with new and sophisticated attacks emerging regularly. Future threats may leverage vulnerabilities in cloud-native architectures, exploit the inherent complexity of containerized environments, or manipulate AI systems for malicious purposes. A critical challenge lies in keeping pace with the ever-increasing sophistication of attacks, requiring proactive and adaptable security measures.
Adaptation of Gated Security to Future Trends
Gated egress and ingress security solutions must evolve to address the emerging challenges and trends. This necessitates adopting a more dynamic and automated approach to security policy enforcement. For example, incorporating AI-driven threat intelligence into security gateways can enable faster and more accurate threat detection and response. Furthermore, integrating security tools and platforms with cloud-native environments will streamline security management and enhance efficiency.
The key to success lies in proactively adapting security measures to maintain resilience against evolving threats.
Conclusion
In conclusion, gated egress and ingress security patterns are vital for protecting sensitive data and maintaining a secure network environment. By understanding the principles, mechanisms, and implementation steps Artikeld in this discussion, organizations can implement effective security measures to safeguard their assets. Continuous monitoring and adaptation to evolving threats are paramount for long-term security.
FAQ Insights
What is the difference between egress and ingress security?
Egress security controls outbound traffic, while ingress security controls inbound traffic. Egress security focuses on preventing sensitive data from leaving the network, while ingress security prevents unauthorized access from entering the network.
What are some common use cases for gated security?
Gated security is essential for protecting sensitive data, preventing data breaches, and complying with regulatory requirements. It’s also crucial for controlling access to applications and services, and for maintaining network integrity.
How do firewalls, NAC, and IDS/IPS contribute to gated security?
Firewalls control network traffic based on predefined rules, NAC enforces policies on devices connecting to the network, and IDS/IPS detect and prevent malicious activities. Together, they create a multi-layered security approach.
What are the challenges of managing complex gated security policies?
Managing complex policies can be challenging due to the need for granular control and potential performance bottlenecks. Careful planning, thorough testing, and continuous monitoring are essential to address these challenges.


