Embarking on the journey of what are the steps for migrating a virtual machine to the cloud signifies a pivotal shift in IT infrastructure management, moving from on-premises environments to the dynamic scalability and cost efficiencies of cloud platforms. This transition involves a multifaceted process, encompassing strategic planning, meticulous execution, and ongoing optimization. Understanding the nuances of this migration is crucial for organizations seeking to enhance their agility, reduce operational costs, and unlock the full potential of cloud computing.
This comprehensive guide delves into the essential steps required to successfully migrate your virtual machines to the cloud. From initial assessment and strategic planning to post-migration optimization and security considerations, we’ll explore each phase with a focus on practical implementation and best practices. This exploration will cover key aspects like choosing the right cloud provider, selecting the appropriate migration strategy, configuring migration tools, ensuring data integrity, and optimizing costs.
The ultimate goal is to provide a clear roadmap for a smooth and successful cloud migration journey.
Understanding the Cloud Migration Process
The migration of virtual machines (VMs) to the cloud represents a significant shift in IT infrastructure management, offering organizations the potential for increased agility, scalability, and cost efficiency. This process, however, is not a simple “lift and shift.” It requires careful planning, execution, and ongoing management to realize its full benefits and mitigate potential risks. Understanding the underlying motivations, architectural considerations, and associated trade-offs is crucial for a successful cloud migration strategy.
Reasons for Cloud Migration
Organizations choose to migrate VMs to the cloud for a variety of compelling reasons, primarily centered around operational efficiency, cost optimization, and enhanced business agility. These drivers often work in concert, creating a powerful incentive for cloud adoption.
- Cost Reduction: Cloud providers typically offer a pay-as-you-go pricing model, which can significantly reduce capital expenditure (CAPEX) associated with on-premises infrastructure. Organizations can avoid the costs of hardware purchase, maintenance, and upgrades. Furthermore, they can optimize resource utilization by scaling up or down based on demand, minimizing wasted resources. For example, a company that experiences peak demand during specific periods can scale up its VMs only when needed, avoiding the cost of maintaining idle resources.
- Scalability and Elasticity: Cloud platforms provide unparalleled scalability, allowing organizations to rapidly provision and de-provision resources as needed. This elasticity is particularly beneficial for applications with fluctuating workloads. For instance, an e-commerce website can easily handle a surge in traffic during a holiday sale by scaling up its VMs to accommodate the increased demand, and then scale down when the peak demand subsides.
- Improved Reliability and Availability: Cloud providers invest heavily in infrastructure redundancy and disaster recovery capabilities. VMs hosted in the cloud benefit from these features, resulting in higher availability and improved business continuity. This can be illustrated by comparing the recovery time objective (RTO) and recovery point objective (RPO) of a cloud-based VM versus an on-premises VM. Cloud-based VMs typically offer significantly shorter RTOs and RPOs due to automated failover and data replication mechanisms.
- Enhanced Agility and Innovation: Cloud platforms offer a wide range of services, including compute, storage, databases, and development tools, that can accelerate the development and deployment of new applications and services. This agility enables organizations to respond quickly to market changes and innovate more rapidly. For instance, a software development company can use cloud-based development environments to quickly prototype and test new features without the overhead of managing on-premises infrastructure.
Cloud Deployment Models and VM Migration
Different cloud deployment models offer varying levels of control, management responsibility, and abstraction, directly impacting how VMs are migrated and managed. The choice of model significantly influences the migration strategy and the ongoing operational model.
- Infrastructure as a Service (IaaS): In the IaaS model, the cloud provider provides the underlying infrastructure, including servers, storage, and networking. The organization retains control over the operating systems, middleware, and applications running on the VMs. This model is often used for “lift and shift” migrations, where existing VMs are moved to the cloud with minimal changes. Examples include Amazon Web Services (AWS) EC2, Microsoft Azure Virtual Machines, and Google Compute Engine.
The organization is responsible for the operational aspects of the VM, including patching, security, and performance optimization.
- Platform as a Service (PaaS): PaaS provides a platform for developing, running, and managing applications without the need to manage the underlying infrastructure. The cloud provider handles the operating systems, middleware, and runtime environments. This model is less common for direct VM migration but is suitable for re-architecting applications to take advantage of PaaS services. For example, a VM running a web application could be migrated to a PaaS environment such as AWS Elastic Beanstalk or Google App Engine.
The organization focuses on the application code and data, while the cloud provider manages the platform.
- Software as a Service (SaaS): SaaS delivers software applications over the internet, with the cloud provider managing the entire infrastructure and application stack. This model is not directly applicable to VM migration, as the organization does not manage its own VMs. However, organizations might migrate from on-premises software to SaaS alternatives, effectively replacing their VMs with cloud-based services. Examples include Salesforce for CRM and Microsoft 365 for productivity applications.
The selection of the appropriate cloud deployment model for VM migration hinges on factors such as existing infrastructure, application requirements, and the organization’s technical expertise and resource constraints. A hybrid approach, combining elements of different models, may be the optimal solution for certain organizations.
Benefits and Drawbacks of Cloud Migration for VMs
Migrating VMs to the cloud presents a balance of significant benefits and potential drawbacks that must be carefully considered during the planning phase. A thorough assessment of these factors is critical to determining the feasibility and overall success of the migration project.
- Benefits:
- Reduced Capital Expenditure (CAPEX): Shifting from CAPEX to operational expenditure (OPEX) can free up capital for other strategic initiatives.
- Improved Scalability and Elasticity: Cloud environments enable rapid scaling up or down of resources to meet changing demands.
- Enhanced Reliability and Availability: Cloud providers offer robust infrastructure and disaster recovery capabilities.
- Increased Agility and Innovation: Access to a wide range of cloud services can accelerate development and deployment cycles.
- Improved Operational Efficiency: Automation and managed services can reduce the burden of infrastructure management.
- Drawbacks:
- Vendor Lock-in: Migrating to a specific cloud provider can create dependencies that make it difficult to switch providers in the future.
- Security Concerns: Data security and compliance are paramount. Organizations must ensure their data is secure in the cloud.
- Complexity: Migrating VMs to the cloud can be a complex process, requiring specialized skills and careful planning.
- Cost Management: Cloud costs can be difficult to predict and control, requiring effective monitoring and optimization strategies.
- Performance Considerations: Network latency and application performance can be impacted by cloud infrastructure, requiring careful performance testing and optimization.
Successfully navigating the cloud migration process involves carefully weighing these benefits and drawbacks. Organizations must develop a comprehensive migration strategy that addresses the specific challenges and opportunities presented by their unique IT environment and business objectives.
Assessing Your Current Environment
Evaluating your existing on-premises virtual machine (VM) infrastructure is a crucial first step in a successful cloud migration. This assessment phase involves a detailed examination of your current IT environment to understand its characteristics, dependencies, and resource utilization. This comprehensive understanding is fundamental for making informed decisions about the migration strategy, cloud provider selection, and the overall cost and effort involved.
Identifying Key Aspects of On-Premises VM Infrastructure
A thorough assessment of your on-premises VM infrastructure involves examining several key aspects to understand its capabilities and limitations. This information is vital for creating a realistic migration plan and minimizing potential issues during and after the transition.
- Hardware: The physical hardware on which your VMs are running directly impacts performance, compatibility, and migration options. Analyzing hardware specifications, including CPU, memory, storage (type, capacity, and performance), and network interfaces, is essential. For example, identifying the age of the hardware helps predict potential end-of-life issues and their impact on the migration timeline. A comprehensive analysis includes:
- Server models and manufacturers.
- CPU specifications (cores, clock speed, architecture).
- RAM capacity and utilization.
- Storage configuration (RAID levels, disk types – SSD, HDD).
- Network interface cards (NICs) and their bandwidth.
- Software: Understanding the software landscape is crucial. This includes the operating systems, applications, and middleware running on your VMs. Compatibility with cloud providers is a primary concern. Specific software versions, dependencies, and licensing models need careful consideration.
- Operating system versions (Windows Server, Linux distributions).
- Application versions and compatibility with cloud environments (e.g., legacy applications).
- Middleware components (databases, web servers, application servers).
- Software licensing models (perpetual, subscription, bring-your-own-license).
- Network: Network configuration significantly influences migration strategies and performance. This includes network topology, bandwidth, latency, and security configurations. Mapping the network infrastructure allows for a seamless transition of network services to the cloud. Key network considerations include:
- Network topology (VLANs, subnets, firewalls).
- Bandwidth utilization and latency.
- Network security configurations (firewall rules, intrusion detection systems).
- VPN connections and their performance.
- DNS and DHCP configurations.
Designing a Process for Documenting VM State
Documenting the current state of your VMs is a critical step. It provides a baseline for comparison, facilitates troubleshooting, and supports informed decision-making throughout the migration process. A well-defined documentation process should capture configurations, dependencies, and resource utilization.
- Configuration Documentation: Comprehensive documentation of each VM’s configuration provides a snapshot of its current state. This documentation forms the basis for recreating or migrating the VM to the cloud. This includes:
- Operating system version and patch levels.
- Hardware configuration (CPU, memory, storage).
- Network settings (IP address, DNS settings, gateway).
- Installed software and their versions.
- User accounts and access permissions.
- Dependency Mapping: Identifying dependencies between VMs and other resources is essential for ensuring application functionality after migration. Understanding these dependencies helps prevent downtime and ensures that all necessary components are migrated together. Dependency mapping includes:
- Application dependencies on other VMs.
- Database connections and their configurations.
- Shared storage dependencies.
- Network dependencies (e.g., firewall rules, load balancers).
- Resource Utilization Monitoring: Monitoring resource utilization provides insights into the performance characteristics of each VM. This data helps determine the appropriate cloud instance size and optimize resource allocation. Monitoring involves tracking:
- CPU utilization.
- Memory utilization.
- Disk I/O.
- Network traffic.
- Documentation Tools and Methods: Utilize a combination of tools and methods to ensure comprehensive documentation.
- Automated Discovery Tools: Tools that automatically scan your environment and collect configuration data. Examples include:
- VMware vCenter (for VMware environments).
- Microsoft System Center Configuration Manager (for Windows environments).
- Manual Documentation: Using spreadsheets, wikis, or dedicated documentation platforms to record information not automatically captured.
- Data Visualization: Utilizing dashboards and reports to visualize resource utilization and dependencies.
- Automated Discovery Tools: Tools that automatically scan your environment and collect configuration data. Examples include:
Creating a Checklist for Assessing VM Compatibility
A compatibility checklist ensures that each VM can successfully migrate to the chosen cloud provider. This checklist focuses on identifying potential roadblocks and ensuring a smooth transition. Compatibility assessments should consider operating systems, software dependencies, and hardware requirements.
- Operating System Compatibility: Ensure that the operating system running on the VM is supported by the cloud provider. Cloud providers typically offer support for a range of operating systems, but older or less common versions might not be fully supported.
- Verify that the operating system version is on the cloud provider’s supported list.
- Check for any specific OS configurations required by the cloud provider.
- Assess the availability of cloud-specific OS images or templates.
- Software Dependency Compatibility: Determine whether the software running on the VM is compatible with the cloud environment. This includes applications, databases, and middleware. Some applications may require modifications or updates to function correctly in the cloud.
- Check for software compatibility with the cloud provider’s infrastructure.
- Identify any required software updates or patches.
- Assess the availability of cloud-native alternatives.
- Hardware Requirement Compliance: Ensure that the VM’s hardware requirements (CPU, memory, storage, network) are met by the cloud provider’s instance types. This assessment involves matching the VM’s current resource allocation with the cloud provider’s available options.
- Compare the VM’s CPU, memory, and storage requirements with the available instance types.
- Assess the network bandwidth and latency requirements.
- Evaluate the need for specialized hardware, such as GPUs.
- Licensing Compliance: Verify the licensing compliance for all software running on the VMs. This includes understanding the licensing terms and ensuring that the licenses are transferable to the cloud environment.
- Identify the licensing model for each software application.
- Determine if the licenses are portable to the cloud.
- Consider the costs of migrating licenses or acquiring new cloud-based licenses.
- Security Considerations: Evaluate the security implications of migrating the VMs to the cloud. This includes understanding the security features offered by the cloud provider and implementing appropriate security controls.
- Assess the cloud provider’s security posture and compliance certifications.
- Identify any required security configurations (firewalls, intrusion detection systems).
- Plan for the implementation of security best practices in the cloud environment.
Choosing a Cloud Provider and Service
Selecting the appropriate cloud provider and service is a pivotal decision in the virtual machine (VM) migration process. This choice significantly impacts performance, cost, security, and the overall success of the migration. The following sections provide a detailed examination of the critical factors to consider when selecting a cloud provider and the various services available for VM migration.
Factors for Cloud Provider Selection
Choosing a cloud provider involves careful consideration of various factors to ensure alignment with organizational needs and objectives. These factors encompass technical capabilities, cost structures, geographical presence, and service-level agreements (SLAs).
- Service Portfolio: The breadth and depth of services offered by a provider are crucial. Consider whether the provider offers services that align with your current and future needs, including compute, storage, networking, databases, and specialized services like machine learning and artificial intelligence. A comprehensive portfolio allows for greater flexibility and scalability. For example, Amazon Web Services (AWS) offers over 200 services, providing a wide range of options for various workloads.
- Pricing Models: Understanding the pricing models is vital for cost optimization. Cloud providers offer various pricing options, including pay-as-you-go, reserved instances, spot instances, and committed use discounts. Evaluate which model best suits your workload patterns and budget constraints. For example, Google Cloud provides sustained use discounts for resources used for a significant portion of the month.
- Geographical Availability: The location of data centers impacts latency, data residency, and compliance requirements. Choose a provider with data centers in regions that meet your geographical needs. Consider proximity to your users and any regulatory requirements related to data storage. Azure, for example, has a vast global network of data centers, offering regional availability for diverse workloads.
- Security and Compliance: Security is paramount. Assess the provider’s security certifications, compliance with industry standards (e.g., HIPAA, PCI DSS), and security features, such as encryption, access control, and threat detection. AWS, Azure, and Google Cloud all provide robust security features and support various compliance certifications.
- Performance and Reliability: Evaluate the provider’s performance metrics, including uptime, latency, and network bandwidth. Review their service-level agreements (SLAs) to understand the guarantees provided for availability and performance. Google Cloud, for instance, offers high availability with redundant infrastructure across multiple zones within a region.
- Support and Documentation: The availability of comprehensive documentation, technical support, and community resources is crucial for troubleshooting and resolving issues. Assess the quality of the provider’s documentation, the responsiveness of their support teams, and the availability of training resources. AWS, Azure, and Google Cloud all offer extensive documentation, support options, and community forums.
- Vendor Lock-in: Consider the potential for vendor lock-in. Assess the ease with which you can migrate your workloads to another provider if needed. Evaluate the use of open standards, portability of data, and the availability of tools to facilitate migration between providers.
Cloud Services for VM Migration
Cloud providers offer a range of services and tools to facilitate VM migration, simplifying the process and reducing downtime. These services can be categorized based on the migration approach, such as rehosting, replatforming, or refactoring.
- Migration Tools: Providers offer dedicated migration tools to automate and streamline the migration process. These tools typically support various migration strategies, including lift-and-shift (rehosting), where VMs are migrated as-is, and more complex approaches involving refactoring and replatforming.
- AWS: AWS provides AWS Migration Hub, which centralizes migration tracking, and AWS Application Migration Service (MGN), which enables lift-and-shift migrations.
- Azure: Azure offers Azure Migrate, a unified platform for discovery, assessment, and migration of on-premises servers, databases, and applications.
- Google Cloud: Google Cloud offers Migrate for Compute Engine, a solution for migrating VMs from various sources to Google Compute Engine.
- Compute Services: Cloud providers offer compute services for hosting migrated VMs. These services provide the infrastructure needed to run VMs, including virtual machines, storage, and networking.
- AWS: Amazon Elastic Compute Cloud (EC2) provides virtual machines with various instance types optimized for different workloads.
- Azure: Azure Virtual Machines provides virtual machines with flexible configuration options.
- Google Cloud: Google Compute Engine provides virtual machines with customizable configurations and various pricing options.
- Storage Services: Choosing the right storage service is important for performance, cost, and data durability.
- AWS: Amazon Elastic Block Storage (EBS) provides block storage for EC2 instances, while Amazon Simple Storage Service (S3) offers object storage for various data types.
- Azure: Azure Disk Storage provides block storage for Azure VMs, while Azure Blob Storage offers object storage.
- Google Cloud: Google Persistent Disk provides block storage for Compute Engine instances, while Google Cloud Storage provides object storage.
- Networking Services: Networking services are essential for connecting VMs to the internet and to other resources within the cloud.
- AWS: Amazon Virtual Private Cloud (VPC) provides a logically isolated network within AWS.
- Azure: Azure Virtual Network (VNet) provides a logically isolated network within Azure.
- Google Cloud: Google Virtual Private Cloud (VPC) provides a logically isolated network within Google Cloud.
- Database Migration Services: Some providers offer specialized services for migrating databases to the cloud.
- AWS: AWS Database Migration Service (DMS) facilitates the migration of databases to AWS.
- Azure: Azure Database Migration Service (DMS) facilitates the migration of databases to Azure.
- Google Cloud: Google Cloud offers a range of database migration options, including DMS for some databases.
Comparative Analysis of Pricing Models
Cloud providers utilize diverse pricing models for VM hosting, necessitating careful comparison to optimize costs. These models vary based on instance type, resource utilization, and commitment levels.
- Pay-as-you-go: This model charges for the resources consumed on an hourly or per-second basis. It offers flexibility but can be more expensive for sustained workloads.
- Reserved Instances/Committed Use Discounts: These models provide significant discounts in exchange for a commitment to use resources for a specific duration (typically one or three years). They are suitable for predictable workloads.
For example, AWS Reserved Instances can offer discounts of up to 75% compared to on-demand pricing, while Google Cloud offers committed use discounts that can reduce costs by up to 70%.
- Spot Instances/Preemptible VMs: These models offer significantly lower prices by utilizing spare compute capacity. However, instances can be terminated if the provider needs the capacity back. This model is suitable for fault-tolerant and non-critical workloads.
For example, AWS Spot Instances can provide discounts of up to 90% compared to on-demand pricing, and Google Cloud preemptible VMs can offer discounts of up to 80%.
- Pricing Tiers: Some providers offer tiered pricing based on resource usage, with lower per-unit costs for higher consumption levels. This model encourages scaling and can reduce costs for large-scale deployments.
- Examples:
- AWS: AWS provides a pricing calculator to estimate the cost of various instance types and configurations. They also offer a variety of pricing options like Savings Plans for flexible savings.
- Azure: Azure offers a pricing calculator and cost management tools to monitor and optimize spending.
- Google Cloud: Google Cloud provides a pricing calculator and cost optimization recommendations based on resource usage patterns.
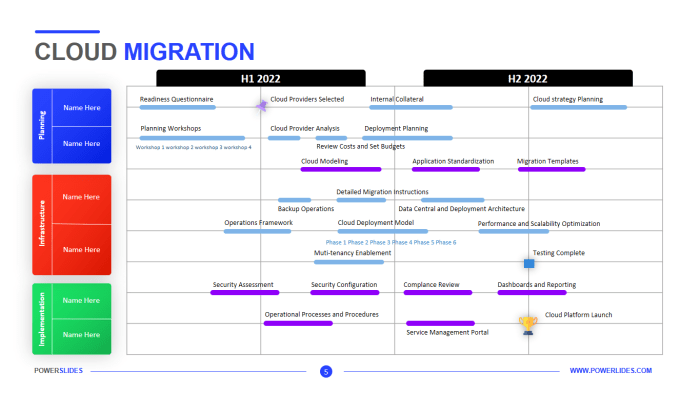
Planning the Migration Strategy
The successful migration of virtual machines (VMs) to the cloud hinges on a well-defined migration strategy. This phase involves carefully selecting the most appropriate approach based on the organization’s objectives, technical capabilities, and budgetary constraints. A comprehensive plan ensures minimal disruption, optimizes resource utilization, and aligns the migration with the overall business strategy.
Organizing Migration Strategies and Their Applicability
Several migration strategies exist, each with its own advantages and disadvantages. Understanding these options and their suitability for different VM scenarios is crucial for effective planning.The primary migration strategies include:
- Rehosting (Lift and Shift): This involves moving the VM to the cloud with minimal changes. It’s the fastest and simplest approach, suitable for VMs with minimal dependencies and where rapid migration is a priority. This is often used for disaster recovery scenarios or to quickly move workloads to the cloud without extensive re-engineering.
- Replatforming (Lift, Tinker, and Shift): This strategy involves making some cloud-specific optimizations, such as changing the operating system or database. It offers a balance between speed and optimization, often used when cloud-native services can improve performance or reduce costs. A typical example is migrating a database to a managed cloud database service.
- Refactoring (Re-architecting): This is the most complex and time-consuming strategy, involving significant code changes to take full advantage of cloud-native features. This is ideal for applications that require significant scalability, agility, or cost optimization. This approach is often used to transform monolithic applications into microservices architectures.
- Repurchasing: This involves replacing the existing application with a cloud-native Software-as-a-Service (SaaS) solution. It eliminates the need for infrastructure management and is ideal for applications where SaaS alternatives are available and meet business requirements. This strategy is attractive for applications like CRM or email.
- Retiring: This involves decommissioning the VM entirely. This is suitable for applications that are no longer needed or are being replaced by other solutions.
- Retaining: This involves keeping the VM on-premises. This is often chosen for compliance reasons or if the cost of migration outweighs the benefits.
The applicability of each strategy depends on various factors:
- Application Complexity: Simple applications are well-suited for rehosting, while complex applications benefit from refactoring.
- Business Requirements: Speed to market might favor rehosting, while scalability demands might necessitate refactoring.
- Technical Skills: Rehosting requires minimal technical expertise, while refactoring requires specialized cloud development skills.
- Budget: Rehosting is typically the least expensive, while refactoring is the most costly.
Selecting the Most Suitable Migration Strategy
Choosing the right migration strategy requires a thorough assessment of business requirements and technical constraints. A structured decision-making process is essential.The selection process should involve the following steps:
- Define Business Goals: Clearly articulate the desired outcomes of the migration, such as cost reduction, improved scalability, increased agility, or enhanced security.
- Assess the Current Environment: Analyze the existing VM infrastructure, including application dependencies, performance characteristics, and security requirements. This includes identifying critical dependencies, such as network configurations, data storage, and other connected services.
- Evaluate Migration Options: Assess the feasibility of each migration strategy based on the business goals and technical constraints. Consider factors like application compatibility, required development effort, and potential risks.
- Conduct a Cost-Benefit Analysis: Compare the costs and benefits of each migration strategy. This should include both the initial migration costs and the ongoing operational costs.
- Prioritize and Select: Prioritize the strategies based on the cost-benefit analysis and select the one that best aligns with the business goals and technical capabilities.
For example, consider a company with a legacy application running on a monolithic architecture. If the primary goal is to reduce operational costs and improve scalability, refactoring to a microservices architecture in the cloud might be the most suitable strategy, even though it is more complex and time-consuming. However, if the primary goal is to quickly move the application to the cloud to avoid on-premises infrastructure maintenance, rehosting might be a more appropriate initial step.
This can be followed by replatforming or refactoring later.
Creating a Project Plan
A well-defined project plan is essential for the successful execution of the migration strategy. It provides a roadmap for the migration process, ensuring that the project stays on track and within budget.The project plan should include the following components:
- Timelines: A detailed schedule outlining the tasks, milestones, and deadlines for each phase of the migration. This should include estimated start and end dates for each task.
- Resource Allocation: Identification of the resources required for the migration, including personnel, hardware, software, and budget. This includes specifying roles and responsibilities for each team member.
- Risk Management: Identification of potential risks and the development of mitigation strategies. This includes assessing the impact of potential risks, such as data loss, application downtime, and security breaches.
- Communication Plan: A plan for communicating project status, risks, and issues to stakeholders. This includes defining communication channels, frequency, and recipients.
- Testing and Validation: A plan for testing the migrated VMs to ensure they are functioning correctly and meeting performance requirements. This should include creating test cases, performing testing, and documenting results.
A typical project plan will involve these phases:
- Planning and Assessment: Defining the migration strategy, assessing the current environment, and creating the project plan.
- Preparation: Setting up the cloud environment, configuring networking, and preparing the VMs for migration.
- Migration: Executing the migration process, which may involve rehosting, replatforming, or refactoring.
- Testing and Validation: Testing the migrated VMs to ensure they are functioning correctly and meeting performance requirements.
- Cutover: Transitioning the workload from the on-premises environment to the cloud environment.
- Optimization and Monitoring: Optimizing the cloud environment for performance and cost, and monitoring the migrated VMs for performance and availability.
Effective risk management is crucial. For instance, data loss is a significant risk. Mitigation strategies include creating backups, validating data integrity after migration, and implementing disaster recovery plans. Another risk is application downtime. Strategies to mitigate this include using a phased migration approach, performing thorough testing, and having a rollback plan in place.
Preparing for the Migration
Prior to the commencement of the cloud migration process, a thorough preparation phase is crucial to ensure a smooth transition and minimize potential disruptions. This stage involves meticulous planning and execution across various domains, including network configuration, data security, and the development of a robust migration strategy. The following sections detail the essential steps required to prepare the on-premises environment for a successful cloud migration.
Preparing the On-Premises Environment
Preparing the on-premises environment involves several critical steps that lay the foundation for a successful cloud migration. These include network configuration adjustments, comprehensive data backups, and robust security hardening measures. Each of these elements plays a vital role in mitigating risks and ensuring data integrity throughout the migration process.
- Network Configuration: Proper network configuration is essential for enabling secure and efficient data transfer to the cloud. This involves evaluating and adjusting network settings to accommodate the new cloud environment.
- Firewall Rules: Review and update firewall rules to allow necessary traffic between the on-premises environment and the cloud provider’s network. Ensure that only authorized traffic is permitted, and unnecessary ports are closed to minimize the attack surface. For example, open ports for secure protocols such as HTTPS (port 443) and SSH (port 22, if required) while restricting access to less secure ports.
- VPN or Direct Connect: Establish a secure connection, such as a Virtual Private Network (VPN) or a direct connection, to facilitate data transfer. VPNs utilize encryption to secure data transmitted over the public internet, while direct connections provide a dedicated, high-bandwidth link for faster and more reliable data transfer. Choose the method that best suits the security and performance requirements of the migration.
- DNS Configuration: Configure DNS settings to resolve both on-premises and cloud resources correctly. This may involve updating DNS records to point to the new cloud-based services or setting up split-horizon DNS to manage internal and external DNS queries.
- Network Segmentation: Implement network segmentation to isolate different parts of the on-premises environment. This reduces the impact of a security breach and simplifies the migration process by allowing you to migrate segments of the network independently. For instance, separate the database servers from the application servers and web servers to reduce the attack surface.
- Data Backups: Creating comprehensive data backups is crucial for data protection and recovery. This ensures that data can be restored in case of any issues during or after the migration.
- Backup Strategy: Develop a robust backup strategy that includes full, incremental, and differential backups. Full backups create a complete copy of all data, while incremental backups only copy the data that has changed since the last backup. Differential backups copy the data that has changed since the last full backup.
- Backup Tools: Utilize reliable backup tools to perform data backups. These tools should support various backup types, encryption, and data compression. Consider using tools that can integrate with the cloud provider’s storage services for efficient backup storage and recovery.
- Backup Verification: Regularly verify the integrity of the backups by restoring data to ensure that the backup process is working correctly. This includes testing the restoration process to ensure data can be recovered in a timely manner.
- Data Retention Policy: Define a data retention policy to determine how long backups should be stored. This policy should consider regulatory requirements, business needs, and the cost of storage.
- Security Hardening: Security hardening involves implementing measures to protect the on-premises environment from security threats. This includes securing systems, applications, and data before migration.
- Vulnerability Scanning: Conduct regular vulnerability scans to identify and address security weaknesses. Use vulnerability scanning tools to scan systems and applications for known vulnerabilities.
- Patch Management: Implement a robust patch management process to ensure that all systems and applications are up-to-date with the latest security patches. This reduces the risk of exploitation by known vulnerabilities.
- Access Control: Implement strong access control measures to limit access to sensitive data and systems. This includes using strong passwords, multi-factor authentication, and role-based access control (RBAC).
- Intrusion Detection and Prevention: Deploy intrusion detection and prevention systems to monitor network traffic and detect malicious activity. These systems can alert administrators to potential security breaches and block malicious traffic.
- Security Audits: Conduct regular security audits to assess the effectiveness of security controls and identify areas for improvement. Security audits can help ensure that security policies and procedures are being followed.
Designing a Phased Migration Plan
A phased migration plan is crucial for minimizing disruption and ensuring a controlled transition to the cloud. This approach allows for testing and validation at each stage, reducing the risk of major failures. A well-defined plan considers the order of migration, the dependencies between applications, and the resources required at each stage.
- Assessment and Prioritization: Evaluate the existing IT infrastructure and prioritize applications and workloads for migration based on factors such as business criticality, complexity, and dependencies. Create a detailed inventory of all applications, their dependencies, and their resource requirements.
- Pilot Migration: Conduct a pilot migration of a small subset of applications or workloads to the cloud. This allows you to test the migration process, identify potential issues, and refine the migration plan before migrating the entire environment. The pilot migration should include testing the performance, functionality, and security of the migrated applications.
- Phased Rollout: Migrate applications and workloads in phases, based on the prioritization established in the assessment phase. Start with less critical applications and gradually move to more critical ones. This allows you to gain experience with the migration process and minimize the impact of any unforeseen issues.
- Testing and Validation: Thoroughly test and validate each phase of the migration to ensure that applications and workloads are functioning correctly in the cloud. This includes testing the performance, functionality, and security of the migrated applications.
- Monitoring and Optimization: Continuously monitor the performance and cost of the migrated applications in the cloud. Optimize the cloud environment based on performance data and cost analysis. Regularly review and update the migration plan to address any issues and improve the efficiency of the migration process.
Ensuring Data Synchronization and Integrity
Data synchronization and integrity are paramount during the migration process. Maintaining data consistency between the on-premises environment and the cloud environment is crucial to avoid data loss or corruption. Several methods can be employed to ensure data integrity and facilitate smooth data synchronization.
- Data Replication: Data replication involves copying data from the on-premises environment to the cloud environment in real-time or near real-time. This ensures that data is synchronized between the two environments.
- Database Replication: Implement database replication to synchronize data between on-premises and cloud-based databases. This can involve using native database replication features or third-party replication tools.
- File Synchronization: Use file synchronization tools to synchronize files and folders between the on-premises environment and the cloud. These tools can monitor changes to files and automatically synchronize them to the cloud.
- Change Data Capture (CDC): CDC is a technique that identifies and captures changes made to data in the on-premises environment. These changes are then applied to the cloud environment, ensuring that data is synchronized efficiently.
- Data Validation: Implement data validation checks to ensure that data is consistent between the on-premises and cloud environments. This involves comparing data sets and identifying any discrepancies.
- Checksum Verification: Use checksums to verify the integrity of data during the migration process. Calculate checksums for data sets and compare them after the data has been migrated to ensure that no data corruption has occurred.
- Data Comparison: Compare data sets between the on-premises and cloud environments to identify any discrepancies. This can involve using data comparison tools or custom scripts.
- Data Transformation: Transform data as needed during the migration process to ensure compatibility with the cloud environment. This may involve converting data formats, data types, or data structures.
- Testing and Monitoring: Regularly test and monitor data synchronization to ensure that data is being replicated correctly and that data integrity is maintained. This includes monitoring the performance of the replication process and verifying data consistency.
Selecting and Configuring Migration Tools
The selection and configuration of appropriate migration tools are critical steps in ensuring a successful virtual machine (VM) migration to the cloud. The right tools streamline the process, reduce downtime, and minimize potential risks. A thorough understanding of available options, their features, and limitations allows for informed decision-making, optimizing the migration strategy.
Identifying Available Migration Tools
Several tools are available for migrating VMs to the cloud, provided by cloud providers and third-party vendors. These tools offer various functionalities, ranging from basic data transfer to complex orchestration and automation capabilities.
- Cloud Provider Native Tools: Cloud providers like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) offer their own migration tools designed to facilitate migrations to their respective platforms. These tools often integrate seamlessly with the provider’s infrastructure and services.
- AWS: AWS provides tools like AWS Migration Hub, AWS Server Migration Service (SMS), and AWS Database Migration Service (DMS) for migrating servers, databases, and applications.
- Azure: Azure offers Azure Migrate for assessing and migrating on-premises servers, databases, and applications to Azure. Azure Database Migration Service (DMS) focuses on database migrations.
- GCP: GCP provides tools like Migrate for Compute Engine for migrating VMs to Google Compute Engine and the Database Migration Service for database migrations.
- Third-Party Migration Tools: Numerous third-party vendors offer migration tools that support migrations to various cloud platforms. These tools often provide advanced features and functionalities, such as agentless migration, application-aware migration, and automated testing.
- Examples: Tools from vendors like VMware (VMware HCX), Carbonite (Double-Take Move), and CloudEndure (now part of AWS) offer specialized migration capabilities.
- Open-Source Migration Tools: Some open-source tools are available, offering flexibility and customization options. These tools may require more technical expertise to configure and manage.
- Examples: Tools like Virt-manager and libvirt can be used for basic VM migrations.
Configuring and Using AWS Migration Hub
AWS Migration Hub acts as a central point to track the progress of migrations across various AWS services and third-party tools. It simplifies the migration process by providing a unified view of the migration status. This section provides a step-by-step guide for configuring and using AWS Migration Hub, focusing on its role in orchestrating migrations.
- Prerequisites: Ensure you have an active AWS account and the necessary permissions to access AWS Migration Hub and the target migration services.
- Accessing AWS Migration Hub: Log in to the AWS Management Console and navigate to the AWS Migration Hub service.
- Creating a Migration Project: Create a new migration project within Migration Hub. Provide a descriptive name and a brief description of the project. This helps organize and track different migration efforts.
- Selecting Migration Tools: Choose the migration tools you plan to use. Migration Hub integrates with various AWS services and third-party tools. Select the appropriate tools based on your migration requirements.
- Discovering and Assessing: If you are migrating servers, use AWS Application Discovery Service to discover your on-premises environment. This service collects information about your servers, including their configuration and resource utilization. This information is crucial for planning and estimating migration costs.
- Planning and Grouping: Organize the discovered servers into migration groups based on application dependencies, business requirements, or other criteria. This facilitates managing and tracking the migration of related workloads.
- Initiating Migration: Depending on the selected migration tools, you can initiate the migration process from Migration Hub. For example, if using AWS Server Migration Service (SMS), you would configure SMS to replicate your on-premises servers to AWS.
- Monitoring Progress: Monitor the migration progress within Migration Hub. The dashboard provides real-time updates on the status of each migration, including the number of servers migrated, the amount of data transferred, and any errors encountered.
- Managing and Tracking: Use Migration Hub to track the status of all your migrations, including the tools used, the source and target environments, and the progress of each migration. The Migration Hub dashboard provides a consolidated view of all migration activities, allowing you to identify potential bottlenecks or issues.
- Post-Migration Validation: After the migration is complete, validate the migrated servers and applications in the target environment. This involves verifying that the applications are functioning correctly, the data is consistent, and the performance meets the required standards.
Comparing Migration Tool Features, Benefits, and Limitations
Choosing the right migration tool requires a careful evaluation of its features, benefits, and limitations. The following table provides a comparative analysis of several popular migration tools, including cloud provider native tools and third-party solutions. This comparison helps in making informed decisions based on specific migration requirements.
| Tool | Features | Benefits | Limitations |
|---|---|---|---|
| AWS Migration Hub |
|
|
|
| Azure Migrate |
|
|
|
| VMware HCX |
|
|
|
| CloudEndure (AWS) |
|
|
|
Performing the Migration
The actual migration phase marks the transition of virtual machines (VMs) from the on-premises environment to the cloud. This stage demands meticulous execution, ongoing monitoring, and rigorous validation to ensure data integrity, application functionality, and minimal downtime. The success of this phase hinges on the pre-migration planning and the chosen migration strategy.
Steps for Migrating a VM to the Cloud Using a Chosen Tool
The specific steps for migrating a VM depend on the chosen migration tool and the selected cloud provider. However, a generalized approach can be Artikeld, assuming the use of a common tool such as AWS Server Migration Service (SMS) or Azure Migrate, or a similar solution.
- Initiating the Migration Process. This typically involves selecting the source VM(s) within the migration tool’s interface. Parameters such as the source environment (e.g., VMware, Hyper-V), target cloud region, and migration type (e.g., cold migration, live migration) are configured. For instance, when using AWS SMS, you’d select the source environment, install the SMS Connector in your VMware vCenter, and define the target AWS region and instance type.
- Replication Setup and Configuration. The migration tool establishes a replication process, copying the VM’s data to the cloud environment. This process can be either initial bulk transfer or incremental replication. The tool will continuously replicate data changes to keep the target environment synchronized. For example, Azure Migrate uses agent-based replication, requiring the installation of an agent on the source VM to track changes and replicate them to Azure.
- Synchronization and Cutover. After the initial replication, the tool performs a final synchronization to ensure the target VM has the most up-to-date data. Then, the cutover process begins. This involves shutting down the source VM, performing the final data synchronization, and starting the target VM in the cloud. The cutover process needs to be carefully scheduled to minimize downtime.
- Post-Migration Configuration. Once the VM is running in the cloud, it may require additional configuration. This includes updating the operating system, installing drivers, and configuring network settings to ensure proper functionality within the cloud environment. Network configuration is often a critical step, involving adjustments to virtual network settings, security groups, and DNS records.
Monitoring the Migration Process and Troubleshooting Common Issues
Continuous monitoring is critical during the migration to identify and resolve any issues that may arise. Robust monitoring tools and strategies are essential to maintain the integrity of the migration.
- Monitoring Metrics. Key metrics to monitor during migration include data transfer rates, replication progress, CPU and memory utilization on both source and target VMs, and network latency. Cloud providers offer dashboards and monitoring tools that provide real-time visibility into these metrics. For instance, AWS CloudWatch can be used to monitor the performance of the migration tasks performed by AWS SMS.
- Error Logging and Alerting. Implement error logging and alerting mechanisms to quickly identify and respond to any failures or anomalies. The migration tool should generate detailed logs that provide insights into the cause of any errors. Set up alerts to notify administrators of critical events, such as replication failures or performance degradation.
- Troubleshooting Common Issues. Common issues include network connectivity problems, insufficient resources in the cloud environment, and compatibility issues. Troubleshooting typically involves reviewing logs, verifying network configurations, and ensuring that the target environment has adequate resources. For example, if a migration fails due to network connectivity issues, the logs may reveal that the source VM cannot reach the replication endpoint.
- Resource Utilization Analysis. Closely observe the resource utilization of the source and target VMs. This will provide insights into performance bottlenecks. Inadequate resources on the target VM can lead to poor performance.
Testing and Validating the Migrated VMs in the Cloud Environment
Thorough testing and validation are crucial steps to confirm that the migrated VMs function correctly in the cloud environment. This process assures the integrity of applications and data.
- Functional Testing. Conduct functional testing to verify that all applications and services running on the migrated VMs are operating as expected. This includes testing core application features, verifying user access, and ensuring that data is correctly processed and stored. For example, if migrating a web application, test user login, data submission, and content rendering.
- Performance Testing. Perform performance testing to assess the performance of the migrated VMs under load. This involves simulating user traffic and measuring response times, throughput, and resource utilization. Performance testing helps identify any performance bottlenecks and ensures that the VMs can handle the expected workload. Tools such as JMeter or LoadView can be employed for this purpose.
- Security Testing. Conduct security testing to ensure that the migrated VMs are secure and that all security configurations are correctly applied. This includes vulnerability scanning, penetration testing, and verifying that security groups and network access controls are properly configured.
- Disaster Recovery Testing. Test disaster recovery procedures to ensure that the migrated VMs can be recovered in case of a failure. This involves simulating a disaster scenario and verifying that the backup and recovery processes work as expected.
- User Acceptance Testing (UAT). Involve end-users in the testing process to validate that the migrated VMs meet their requirements. This helps identify any usability issues and ensures that the migration has been successful from the end-user’s perspective.
Post-Migration Optimization
Post-migration optimization is a critical phase in cloud migration, focusing on refining the performance, cost-efficiency, and security of migrated virtual machines (VMs). This stage involves a series of iterative assessments and adjustments to ensure the cloud environment operates optimally and aligns with business objectives. Successful optimization maximizes the benefits of cloud adoption, including scalability, agility, and cost savings.
Performance Optimization Strategies
Optimizing the performance of migrated VMs involves several key strategies. These strategies ensure VMs operate efficiently, leveraging the cloud’s resources effectively.
- Resource Monitoring and Analysis: Continuous monitoring of VM resource utilization is essential. Tools like cloud provider’s built-in monitoring services (e.g., AWS CloudWatch, Azure Monitor, Google Cloud Monitoring) provide detailed metrics on CPU usage, memory consumption, disk I/O, and network traffic. Analyzing these metrics identifies performance bottlenecks and areas for improvement. For instance, if a VM consistently experiences high CPU utilization, it may indicate the need for a larger instance size or code optimization.
- Instance Sizing and Scaling: Selecting the appropriate instance size for each VM is crucial. Over-provisioning leads to unnecessary costs, while under-provisioning impacts performance. Right-sizing involves analyzing historical resource usage data to determine the optimal instance type and size. Cloud providers offer various instance types optimized for different workloads (e.g., compute-optimized, memory-optimized, storage-optimized). Furthermore, implementing auto-scaling policies allows the cloud environment to dynamically adjust the number of instances based on demand, ensuring optimal performance and cost efficiency.
- Storage Optimization: Selecting the right storage type and optimizing storage configurations can significantly impact VM performance. Cloud providers offer various storage options, including SSDs (Solid State Drives) for high-performance workloads, and HDDs (Hard Disk Drives) for less demanding applications. Optimizing storage configurations, such as disk striping or caching, can improve I/O performance. For example, migrating a database server to SSD-backed storage can dramatically reduce query response times.
- Network Optimization: Network latency and throughput are critical for VM performance. Optimizing network configurations involves selecting the appropriate network tiers, enabling network acceleration features (e.g., accelerated networking), and ensuring proper network security group configurations. For example, placing VMs in close proximity to other services they interact with, or leveraging content delivery networks (CDNs) for geographically distributed applications, can reduce latency and improve user experience.
- Application and Code Optimization: Beyond infrastructure-level optimization, application-level performance tuning is essential. This includes optimizing application code, database queries, and caching mechanisms. Profiling application code identifies performance bottlenecks, such as inefficient algorithms or database queries. Optimizing these areas can lead to significant performance improvements. For instance, optimizing database queries can reduce the load on the database server and improve application response times.
Cost Optimization Techniques
Cost optimization is an integral part of post-migration activities. It involves strategies to reduce cloud spending without compromising performance or availability.
- Cost Monitoring and Reporting: Implementing robust cost monitoring and reporting is the foundation of cost optimization. Cloud providers offer cost management tools that provide detailed insights into spending patterns, broken down by services, regions, and resources. Regularly reviewing these reports helps identify areas where costs can be reduced. For instance, setting up alerts for unexpected cost spikes can help prevent runaway spending.
- Right-Sizing and Instance Selection: As discussed in performance optimization, right-sizing VMs and selecting the appropriate instance types directly impacts cost. Choosing smaller instance sizes when possible, and utilizing instance families optimized for specific workloads (e.g., general purpose, compute-optimized) can significantly reduce costs. Regularly reviewing instance usage and rightsizing as needed is crucial.
- Reserved Instances and Savings Plans: Cloud providers offer various pricing models to help reduce costs. Reserved instances and savings plans provide significant discounts in exchange for committing to a certain level of resource usage over a period of time (e.g., one or three years). Analyzing workload patterns and purchasing reserved instances or savings plans can lead to substantial cost savings. For example, if a VM is expected to run continuously for three years, purchasing a reserved instance can result in a significant discount compared to on-demand pricing.
- Spot Instances and Preemptible VMs: Spot instances (AWS) and preemptible VMs (Google Cloud) offer significantly lower prices compared to on-demand instances, but with the potential for interruption. These are suitable for fault-tolerant workloads that can handle interruptions. Leveraging spot instances or preemptible VMs for non-critical workloads can lead to significant cost savings. For example, running a batch processing job on spot instances can reduce the cost compared to using on-demand instances.
- Storage Tiering and Data Lifecycle Management: Cloud providers offer different storage tiers with varying costs. Utilizing lower-cost storage tiers for infrequently accessed data can reduce storage costs. Implementing data lifecycle management policies automatically moves data between storage tiers based on access frequency. For example, archiving older data to a cheaper storage tier (e.g., AWS Glacier, Azure Archive Storage, Google Cloud Storage Nearline/Coldline) can reduce storage costs.
Cloud-Native Services and Feature Implementation
Leveraging cloud-native services and features enhances the functionality, scalability, and resilience of the VM infrastructure.
- Containerization and Orchestration: Migrating applications to containers (e.g., Docker) and using container orchestration platforms (e.g., Kubernetes) enables greater portability, scalability, and efficiency. Containers package applications and their dependencies, making them easier to deploy and manage. Kubernetes automates the deployment, scaling, and management of containerized applications. For example, migrating a web application to Kubernetes allows for automated scaling based on traffic demand.
- Serverless Computing: Utilizing serverless computing services (e.g., AWS Lambda, Azure Functions, Google Cloud Functions) for specific tasks can reduce operational overhead and costs. Serverless functions execute code without requiring the provisioning or management of servers. This is suitable for event-driven applications or tasks that are not continuously running. For instance, using a serverless function to process image uploads can eliminate the need for a dedicated VM for image processing.
- Managed Databases: Migrating to managed database services (e.g., AWS RDS, Azure SQL Database, Google Cloud SQL) simplifies database management and reduces operational overhead. Managed databases provide features such as automated backups, patching, and scaling. This allows for more focus on application development rather than database administration. For example, migrating a MySQL database to a managed service can reduce the administrative burden and improve database availability.
- Managed Messaging and Queuing: Utilizing managed messaging and queuing services (e.g., AWS SQS, Azure Service Bus, Google Cloud Pub/Sub) enables asynchronous communication between application components. This improves application resilience and scalability. These services provide reliable message delivery and decoupling of application components. For instance, using a message queue for processing orders allows for asynchronous processing and improved application responsiveness.
- API Gateway and Microservices Architecture: Implementing an API gateway and adopting a microservices architecture improves application flexibility and scalability. An API gateway manages API traffic, provides security features, and enables service discovery. Microservices architecture breaks down applications into smaller, independent services. This enables independent scaling and faster development cycles. For example, using an API gateway to manage API requests for a mobile application improves security and performance.
Post-Migration Security Assessments and Best Practices
Post-migration security assessments and adherence to best practices are essential to ensure the security of the cloud environment.
- Security Audits and Penetration Testing: Conducting regular security audits and penetration testing helps identify vulnerabilities and weaknesses in the cloud environment. Security audits assess the configuration of security controls, compliance with security standards, and overall security posture. Penetration testing simulates real-world attacks to identify vulnerabilities. For instance, performing penetration testing on a web application can identify vulnerabilities that could be exploited by attackers.
- Identity and Access Management (IAM) Review: Reviewing and refining IAM policies ensures that users and applications have only the necessary access permissions. This follows the principle of least privilege. Regularly reviewing IAM policies helps prevent unauthorized access and data breaches. For example, reviewing IAM policies to ensure that users do not have excessive permissions on critical resources.
- Vulnerability Scanning and Patch Management: Implementing vulnerability scanning and patch management processes is crucial for addressing security vulnerabilities. Vulnerability scanning identifies vulnerabilities in the operating systems, applications, and configurations. Patch management ensures that security patches are applied promptly to address known vulnerabilities. For instance, using a vulnerability scanner to identify and remediate vulnerabilities in the operating system of a VM.
- Network Security Configuration: Reviewing and optimizing network security configurations, such as security groups, firewalls, and network access control lists (ACLs), is essential. These configurations control network traffic and protect resources from unauthorized access. For example, configuring security groups to restrict inbound traffic to only necessary ports and protocols.
- Data Encryption and Compliance: Ensuring data is encrypted both in transit and at rest is critical for data security. Implementing encryption protects sensitive data from unauthorized access. Adhering to relevant compliance regulations (e.g., GDPR, HIPAA) is also essential. For example, encrypting data stored in cloud storage and implementing data loss prevention (DLP) measures.
Security Considerations
Migrating virtual machines to the cloud necessitates a robust security strategy to protect sensitive data and maintain operational integrity. Cloud environments introduce new threat vectors and require a proactive approach to security management. This section Artikels crucial security best practices and implementation guidelines for cloud-based VMs.
Security Best Practices for Securing VMs in the Cloud
Implementing robust security practices is essential to protect cloud-based virtual machines from various threats. This involves a multi-layered approach that encompasses network security, access control, data protection, and continuous monitoring. The following points detail essential best practices.
- Implement Strong Authentication and Authorization: Utilize multi-factor authentication (MFA) to verify user identities and restrict access based on the principle of least privilege. This reduces the attack surface by limiting the impact of compromised credentials.
- Regularly Patch and Update Operating Systems and Applications: Implement a consistent patching schedule to address known vulnerabilities. Automated patching solutions can streamline this process, reducing the time between vulnerability disclosure and remediation.
- Encrypt Data at Rest and in Transit: Employ encryption to protect data from unauthorized access, both when stored within the VM and when transmitted across the network. Utilize industry-standard encryption algorithms like AES-256.
- Enable Intrusion Detection and Prevention Systems (IDPS): Deploy IDPS solutions to monitor network traffic and VM activity for malicious behavior. These systems can detect and respond to potential threats in real-time.
- Implement a Web Application Firewall (WAF): Protect web applications running on VMs from common web-based attacks, such as cross-site scripting (XSS) and SQL injection.
- Regularly Back Up Data and Test Recovery Procedures: Implement a robust backup strategy to ensure data availability in the event of a disaster or security breach. Regularly test the recovery process to ensure its effectiveness.
- Conduct Regular Security Audits and Penetration Testing: Perform periodic security assessments to identify vulnerabilities and weaknesses in the VM environment. Penetration testing can simulate real-world attacks to evaluate the effectiveness of security controls.
- Monitor Logs and Alerts: Centralize and analyze logs from VMs and security systems to detect suspicious activity. Configure alerts to notify security teams of potential threats.
- Choose a Cloud Provider with Strong Security Compliance: Ensure the cloud provider complies with relevant security standards and regulations, such as ISO 27001 and SOC 2. This can provide a baseline level of security assurance.
Configuring Network Security Groups and Firewalls
Network security groups and firewalls are fundamental components of cloud security, controlling network traffic flow to and from VMs. Properly configuring these elements is crucial to prevent unauthorized access and mitigate potential threats. Here are some guidelines for effective implementation.
- Use Network Security Groups (NSGs) or Security Groups: NSGs act as virtual firewalls, allowing you to control inbound and outbound traffic at the subnet or VM level. Define rules to permit only necessary traffic and deny all other traffic.
- Implement a Defense-in-Depth Strategy: Combine NSGs with other security measures, such as host-based firewalls, to create a layered security approach. This increases the resilience of your environment.
- Follow the Principle of Least Privilege: Grant only the minimum necessary access to resources. For example, only allow specific IP addresses or ranges to access a VM.
- Segment Your Network: Divide your network into subnets and apply different security policies to each segment. This limits the impact of a security breach by containing the affected area.
- Regularly Review and Update Firewall Rules: Periodically review your firewall rules to ensure they are still relevant and effective. Remove any unnecessary rules and update rules as needed to reflect changes in your environment.
- Enable Logging and Monitoring: Configure logging for firewall rules to track network traffic and identify potential security incidents. Monitor logs for suspicious activity and unusual traffic patterns.
- Consider Using a Web Application Firewall (WAF): If your VMs host web applications, deploy a WAF to protect against common web-based attacks.
Implementing Access Control and Identity Management for Cloud VMs
Managing access to cloud VMs is a critical aspect of security. Implementing robust access control and identity management mechanisms ensures that only authorized users and systems can access sensitive resources. The following points Artikel methods for effective implementation.
- Use Role-Based Access Control (RBAC): Assign users roles that define their permissions and access rights. This simplifies access management and reduces the risk of privilege escalation.
- Implement Multi-Factor Authentication (MFA): Require users to verify their identities using multiple factors, such as a password and a one-time code from an authenticator app.
- Centralize Identity Management: Integrate your cloud environment with a centralized identity provider, such as Active Directory or a cloud-based identity service, to manage user accounts and access across all resources.
- Regularly Review User Access: Conduct periodic reviews of user access to ensure that permissions are still appropriate. Revoke access for users who no longer require it or have left the organization.
- Enforce Strong Password Policies: Implement strong password policies, including minimum length requirements, password complexity, and regular password changes.
- Monitor User Activity: Monitor user activity to detect suspicious behavior, such as unusual login attempts or access to sensitive resources.
- Use Just-in-Time (JIT) Access: Grant temporary access to resources only when needed. This reduces the attack surface and limits the potential impact of compromised credentials.
- Automate Access Management: Automate the provisioning and deprovisioning of user accounts and access rights to streamline the process and reduce the risk of errors.
Cost Management and Optimization
Migrating virtual machines to the cloud necessitates a proactive approach to cost management. Cloud environments offer flexible pricing models, but without careful monitoring and optimization, costs can quickly escalate. This section details strategies for controlling cloud expenses, optimizing resource utilization, and comparing the financial implications of on-premises versus cloud hosting.
Monitoring and Managing Cloud Costs
Effective cost management begins with robust monitoring and analysis. Cloud providers offer various tools for tracking spending, but supplementary strategies are crucial for comprehensive cost control.
- Utilizing Cloud Provider Tools: Cloud platforms provide built-in cost management dashboards. These tools offer real-time cost tracking, spend forecasting, and budget alerts. They allow users to filter costs by service, resource, and region, enabling granular analysis. For instance, AWS Cost Explorer, Azure Cost Management, and Google Cloud Billing dashboards offer these functionalities.
- Implementing Cost Allocation Tags: Tagging resources with relevant metadata, such as department, project, or application, allows for detailed cost allocation. This enables organizations to understand where costs are incurred and identify areas for optimization. Cost allocation tags facilitate the breakdown of spending by business units, enabling chargeback mechanisms.
- Setting Budgets and Alerts: Establishing budgets and setting up alerts helps prevent unexpected cost overruns. Cloud providers allow users to define spending thresholds and receive notifications when these thresholds are approached or exceeded. This proactive approach ensures that cost overruns are addressed promptly.
- Regular Cost Reports and Analysis: Regularly reviewing cost reports and conducting detailed cost analysis is crucial. This involves identifying cost drivers, analyzing trends, and pinpointing areas where optimization is possible. Automating report generation and distribution streamlines the process.
- Leveraging Third-Party Cost Management Tools: Several third-party tools provide advanced cost management capabilities, including anomaly detection, automated recommendations, and cross-cloud cost analysis. These tools often integrate with multiple cloud providers and offer more sophisticated features than native tools.
Cost Optimization Techniques
Cost optimization is a continuous process that involves refining resource utilization to minimize expenses. Several techniques can be employed to achieve significant cost savings.
- Right-Sizing Virtual Machines: Right-sizing involves selecting the appropriate instance size for the workload. This prevents over-provisioning, where resources are allocated beyond what is necessary, leading to unnecessary costs. Tools like AWS Compute Optimizer, Azure Advisor, and Google Cloud’s recommendations can help identify underutilized instances and suggest appropriate sizes.
- Automated Scaling: Implementing automated scaling adjusts resources based on demand. This ensures that resources are available when needed but scaled down during periods of low activity, reducing costs. Auto-scaling policies can be configured to respond to metrics like CPU utilization, network traffic, or memory usage.
- Reserved Instances and Committed Use Discounts: Cloud providers offer discounts for committing to a certain level of resource usage over a specified period. Reserved instances (AWS), Azure Reserved Virtual Machine Instances, and sustained use discounts (Google Cloud) provide significant cost savings compared to on-demand pricing.
- Using Spot Instances and Preemptible VMs: Spot instances (AWS) and preemptible VMs (Google Cloud) offer substantial discounts in exchange for the potential for the instance to be terminated. These are suitable for fault-tolerant workloads that can handle interruptions.
- Optimizing Storage Costs: Selecting the appropriate storage tier based on data access frequency is crucial. For example, infrequently accessed data can be stored in cheaper tiers like AWS S3 Glacier or Azure Archive Storage. Regularly reviewing storage usage and deleting unnecessary data can also reduce costs.
- Data Transfer Optimization: Minimizing data transfer costs is essential. This includes optimizing data transfer patterns, using content delivery networks (CDNs) for content delivery, and ensuring data is transferred within the same region to avoid inter-region transfer charges.
Cost-Benefit Analysis: On-Premises vs. Cloud VM Hosting
A comprehensive cost-benefit analysis is crucial when evaluating the financial implications of migrating VMs to the cloud. This analysis should consider both the initial and ongoing costs associated with each option.
On-Premises:
- Capital Expenditures (CAPEX): Includes hardware costs (servers, storage, networking equipment), software licenses, and data center infrastructure (power, cooling).
- Operational Expenditures (OPEX): Includes IT staff salaries, power and cooling costs, data center rent or mortgage, hardware maintenance, and software licensing fees.
- Advantages: Full control over infrastructure, potentially lower long-term costs if resource utilization is high and predictable.
- Disadvantages: High upfront costs, requires significant IT expertise, limited scalability and flexibility, risk of hardware obsolescence.
Cloud VM Hosting:
- Operational Expenditures (OPEX): Pay-as-you-go pricing based on resource consumption (compute, storage, networking), data transfer costs, and managed service fees.
- Advantages: No upfront capital expenditure, scalable and flexible, reduced IT staff requirements, access to advanced services.
- Disadvantages: Ongoing operational costs, vendor lock-in potential, reliance on internet connectivity, potential for cost overruns if not managed effectively.
Comparison: The cloud typically offers lower initial costs and greater scalability. However, ongoing costs can be higher if resources are not managed effectively. The total cost of ownership (TCO) depends on factors such as resource utilization, the duration of usage, and the pricing models selected. In many cases, cloud migration reduces IT infrastructure costs and increases operational agility.
For example, a small-to-medium-sized business (SMB) might spend $10,000-$50,000 upfront for hardware and software licensing on-premises, along with significant ongoing operational costs. Cloud services can be significantly lower upfront costs, and offer increased flexibility to scale resources. The savings may not be immediate, but over time the cloud offers reduced TCO.
Monitoring and Management in the Cloud
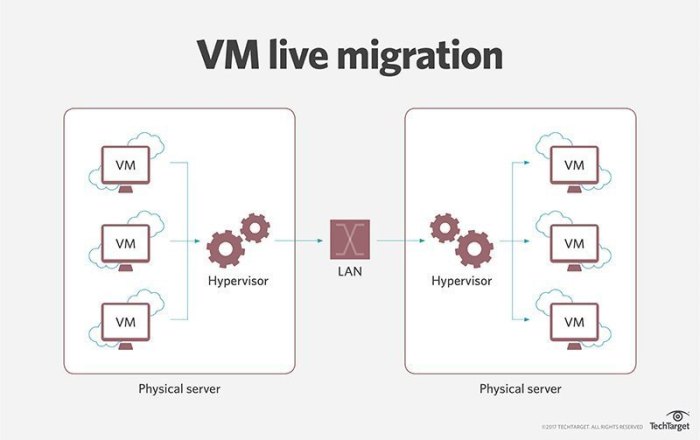
Effective monitoring and management are crucial for maintaining the performance, security, and cost-effectiveness of virtual machines (VMs) migrated to the cloud. This involves proactively observing system behavior, automating routine tasks, and establishing robust disaster recovery and business continuity plans. Implementing these practices ensures operational efficiency and minimizes potential disruptions.
Monitoring VM Performance and Health
Monitoring the performance and health of cloud-based VMs is a continuous process that provides real-time insights into their operational status. This involves collecting and analyzing various metrics to identify potential issues, optimize resource allocation, and ensure optimal performance.
- Performance Metrics: Key performance indicators (KPIs) offer a quantitative view of VM performance.
- CPU Utilization: Percentage of CPU processing time utilized by the VM. High utilization can indicate a need for increased resources or optimization.
- Memory Utilization: Percentage of memory being used. Insufficient memory can lead to performance degradation and application errors.
- Disk I/O: Rate of data transfer to and from the disk. High I/O can indicate disk bottlenecks.
- Network I/O: Rate of data transfer over the network. High network I/O might indicate network congestion or application performance issues.
- Health Checks: These checks ensure the VM and its associated services are functioning correctly.
- System Logs: Examination of system logs for errors, warnings, and informational messages. This helps in identifying and troubleshooting problems.
- Application Monitoring: Monitoring the performance and availability of applications running on the VM.
- Service Availability: Verification that critical services are running and accessible.
- Alerting and Notifications: Establishing a system for alerts based on predefined thresholds. This facilitates prompt responses to critical issues.
- Thresholds: Setting thresholds for performance metrics (e.g., CPU utilization exceeding 80%).
- Alerting Mechanisms: Configuring alerts via email, SMS, or other notification systems.
- Incident Response: Defining procedures for responding to alerts, including escalation paths and troubleshooting steps.
- Monitoring Tools: Cloud providers offer various monitoring tools, alongside third-party solutions.
- Cloud Provider Tools: Examples include AWS CloudWatch, Azure Monitor, and Google Cloud Operations Suite. These tools provide built-in dashboards, metrics collection, and alerting capabilities.
- Third-Party Tools: Solutions like Datadog, New Relic, and Prometheus offer advanced monitoring features, including custom dashboards, integration with various services, and more sophisticated alerting capabilities.
Using Cloud-Based Management Tools
Cloud-based management tools automate tasks and streamline operations, enhancing efficiency and reducing manual effort. These tools provide centralized control and automation capabilities.
- Automation and Orchestration: Automating repetitive tasks to improve operational efficiency and reduce the risk of human error.
- Infrastructure as Code (IaC): Using tools like Terraform or AWS CloudFormation to define and manage infrastructure as code. This allows for repeatable and consistent deployments.
- Configuration Management: Tools like Ansible, Chef, or Puppet to automate configuration and software deployment on VMs.
- Workflow Automation: Automating complex tasks through workflow engines, such as those available in cloud provider services or third-party solutions.
- Configuration Management: Maintaining consistent configurations across all VMs.
- Configuration Drift Detection: Monitoring for changes in VM configurations that deviate from the defined baseline.
- Compliance Enforcement: Ensuring VMs adhere to security and regulatory compliance standards.
- Patch Management: Automating the process of patching and updating VMs to maintain security and stability.
- Patch Deployment: Scheduling and deploying patches to VMs.
- Vulnerability Scanning: Regularly scanning VMs for vulnerabilities and applying necessary patches.
- Cost Management: Optimizing resource usage to reduce cloud costs.
- Resource Optimization: Identifying and eliminating underutilized resources.
- Cost Tracking and Analysis: Monitoring cloud spending and identifying areas for cost reduction.
- Right-Sizing: Adjusting VM sizes based on actual resource usage.
- Cloud Provider Tools:
- AWS Systems Manager: Offers automation, patching, and configuration management for EC2 instances.
- Azure Automation: Provides automation and configuration management services for Azure VMs.
- Google Cloud Automation: Offers similar services for managing and automating Google Cloud VMs.
Creating a Plan for Disaster Recovery and Business Continuity
A well-defined disaster recovery (DR) and business continuity (BC) plan is essential to ensure the availability and resilience of cloud-based VMs in the event of failures or disasters. This plan Artikels strategies for data protection, rapid recovery, and continuous operation.
- Data Backup and Recovery: Protecting data through regular backups and establishing recovery procedures.
- Backup Strategies: Implementing strategies such as full, incremental, and differential backups.
- Backup Storage: Choosing a suitable storage location for backups, considering factors such as cost, performance, and durability.
- Recovery Procedures: Defining the steps required to restore data and VMs in the event of a failure.
- Replication: Creating copies of VMs and data in a different availability zone or region to ensure high availability.
- Asynchronous Replication: Replicating data with a slight delay, suitable for non-critical applications.
- Synchronous Replication: Replicating data in real-time, suitable for critical applications.
- Failover and Failback: Defining procedures for automatically switching to a secondary environment in the event of a failure (failover) and returning to the primary environment when the issue is resolved (failback).
- Failover Scenarios: Identifying potential failure scenarios and defining failover procedures for each.
- Testing and Validation: Regularly testing failover and failback procedures to ensure they function correctly.
- Business Continuity Planning: Developing strategies to maintain business operations during and after a disaster.
- Recovery Time Objective (RTO): The maximum acceptable time to restore operations after a disaster.
- Recovery Point Objective (RPO): The maximum acceptable data loss in the event of a disaster.
- Testing and Training: Regularly testing the DR/BC plan and training personnel on their roles and responsibilities.
- Cloud Provider Services:
- AWS: AWS provides services like AWS Backup, Amazon S3 for backup storage, and AWS Site Recovery for disaster recovery.
- Azure: Azure offers Azure Backup, Azure Site Recovery, and Azure Resource Manager for DR and BC.
- Google Cloud: Google Cloud provides Cloud Storage for backup and Cloud Disaster Recovery for DR solutions.
Final Conclusion
In conclusion, migrating virtual machines to the cloud is a transformative process that demands careful planning, strategic execution, and continuous optimization. By meticulously following the Artikeld steps – from understanding the cloud migration process and assessing your current environment to selecting the right tools and optimizing post-migration performance – organizations can successfully transition their VMs to the cloud. This strategic move unlocks benefits like enhanced scalability, improved cost efficiency, and increased agility, enabling businesses to thrive in today’s dynamic digital landscape.
The cloud migration journey, though complex, offers significant rewards for those who approach it with diligence and a commitment to best practices.
Questions Often Asked
What is the difference between rehosting and replatforming?
Rehosting, also known as “lift and shift,” involves moving VMs to the cloud with minimal changes. Replatforming, on the other hand, involves making some changes to the application to leverage cloud-native features, but without a complete code rewrite.
How do I choose the right migration strategy?
The best strategy depends on your business requirements, technical constraints, and the current state of your VMs. Consider factors such as application complexity, budget, and desired level of cloud integration.
What are the key considerations for data synchronization during migration?
Data synchronization ensures data consistency between your on-premises environment and the cloud. Consider using tools that support incremental backups and continuous replication to minimize downtime and data loss. Assess the volume of data, network bandwidth, and the need for real-time data synchronization.
How can I ensure data security during the migration process?
Implement strong encryption for data in transit and at rest. Use secure network configurations, access controls, and identity management. Regularly audit security settings and follow best practices for cloud security.
What are the primary cost optimization strategies after migration?
Optimize your instance sizes (right-sizing), utilize automated scaling, and leverage reserved instances or savings plans. Regularly monitor your cloud spending and identify areas for cost reduction. Implement a cost governance policy to track and control spending.