Embarking on a cloud migration journey necessitates a robust understanding of DNS strategy. What is DNS strategy for cloud migration? It’s the strategic planning and execution of how your Domain Name System (DNS) infrastructure will transition to and function within a cloud environment. This critical aspect, often underestimated, significantly impacts application performance, security, and overall operational efficiency. Neglecting a well-defined DNS strategy can lead to downtime, performance bottlenecks, and security vulnerabilities, potentially hindering the success of your cloud migration initiative.
This comprehensive guide delves into the intricacies of DNS within the cloud context. We will explore DNS fundamentals, planning considerations, provider selection, hybrid cloud configurations, migration procedures, security measures, monitoring techniques, automation strategies, troubleshooting approaches, and the crucial impact of DNS on application performance. By understanding these elements, organizations can ensure a seamless and efficient cloud migration, maximizing the benefits of cloud computing.
Understanding DNS Fundamentals in Cloud Context

The Domain Name System (DNS) is a cornerstone of internet functionality, translating human-readable domain names into the numerical IP addresses that computers use to communicate. In the context of cloud migration, understanding DNS fundamentals is crucial for ensuring seamless application performance, high availability, and efficient resource management. Cloud environments introduce complexities and opportunities that necessitate a refined approach to DNS management, distinct from traditional on-premises implementations.
Core Components of DNS and Their Roles in Cloud Environments
DNS operates through a hierarchical, distributed database. Several key components work together to resolve domain names. Understanding these components is vital for effective cloud DNS management.
- DNS Resolvers: These are the clients that initiate DNS queries. They reside on end-user devices (e.g., laptops, smartphones) or within cloud infrastructure (e.g., virtual machines). When a user types a domain name into a web browser, the resolver queries DNS servers to obtain the corresponding IP address. In cloud environments, the resolver might be configured on a virtual machine instance or utilize a cloud provider’s DNS service.
- Recursive DNS Servers: Also known as resolving nameservers, these servers act as intermediaries between resolvers and authoritative nameservers. They receive DNS queries from resolvers and recursively query other DNS servers until they find the authoritative answer. Cloud providers often offer managed recursive DNS services to enhance performance and availability.
- Authoritative DNS Servers: These servers hold the definitive DNS records for a specific domain. They store information such as A records (mapping domain names to IP addresses), MX records (specifying mail servers), and CNAME records (creating aliases). In a cloud environment, authoritative DNS servers can be managed by the cloud provider or through third-party services. They are responsible for providing the correct IP addresses for cloud resources.
- DNS Records: These are the fundamental data units within the DNS system. They contain information about a domain and its associated resources. The following are common record types:
- A Record (Address Record): Maps a domain name to an IPv4 address.
- AAAA Record (Quad A Record): Maps a domain name to an IPv6 address.
- CNAME Record (Canonical Name Record): Creates an alias, mapping one domain name to another.
- MX Record (Mail Exchange Record): Specifies the mail servers responsible for handling email for a domain.
- TXT Record (Text Record): Stores arbitrary text, often used for verification purposes (e.g., SPF records for email authentication).
In cloud environments, the roles of these components remain the same, but their implementation and management often differ. Cloud providers offer managed DNS services that handle recursive queries, authoritative hosting, and record management, providing scalability, reliability, and simplified administration.
Comparison of Traditional DNS vs. Cloud-Based DNS Services
Traditional DNS implementations, typically deployed on-premises, differ significantly from cloud-based DNS services in terms of infrastructure, management, and features. The shift to cloud-based DNS offers several advantages.
| Feature | Traditional DNS | Cloud-Based DNS |
|---|---|---|
| Infrastructure | On-premises servers, requiring hardware, maintenance, and manual scaling. | Cloud-based, leveraging distributed infrastructure for high availability and scalability. Managed by the cloud provider. |
| Management | Manual configuration, updates, and monitoring. Requires dedicated IT staff. | Simplified management through web interfaces or APIs. Automated scaling and updates. |
| Scalability | Limited by hardware capacity and manual scaling processes. | Highly scalable, automatically adjusting to traffic demands. |
| Availability | Dependent on on-premises infrastructure and redundancy measures. Potential for single points of failure. | Built-in redundancy and distributed architecture, ensuring high availability. |
| Performance | Performance is influenced by the geographical location of DNS servers and network latency. | Global anycast networks, providing low-latency responses from geographically distributed servers. |
| Cost | Capital expenditure (CAPEX) for hardware and operational expenditure (OPEX) for maintenance and staffing. | Typically pay-as-you-go pricing model, reducing upfront costs and aligning costs with usage. |
Cloud-based DNS services leverage distributed infrastructure, such as anycast networks, to improve performance and availability. Anycast enables the same IP address to be announced from multiple geographically dispersed servers. This allows DNS queries to be routed to the closest available server, reducing latency and improving response times. Furthermore, cloud-based services often offer features like automated DNS record updates, DNSSEC support, and integrated monitoring tools, enhancing security and simplifying management.
Traditional DNS setups can be more difficult to scale and maintain, particularly as application demands increase.
Advantages of Using DNS in Cloud Infrastructure
Leveraging DNS in cloud infrastructure offers significant advantages in terms of performance, scalability, security, and cost efficiency. These advantages are key drivers for cloud adoption.
- Enhanced Performance: Cloud-based DNS services, with their global anycast networks, provide faster response times and improved user experience. By serving DNS requests from geographically distributed servers, the latency associated with DNS lookups is minimized.
- Improved Scalability: Cloud DNS services automatically scale to handle fluctuations in traffic. This ensures that DNS queries are resolved quickly, even during peak loads. For example, a website experiencing a sudden surge in traffic during a promotional campaign can rely on cloud DNS to handle the increased query volume without performance degradation.
- Increased Availability: Cloud DNS services are designed with high availability in mind. They often utilize redundant infrastructure and automated failover mechanisms to ensure that DNS queries are always answered, even in the event of server failures or network outages. This ensures that applications remain accessible.
- Simplified Management: Cloud DNS services offer user-friendly interfaces and APIs for managing DNS records. This simplifies the process of adding, updating, and deleting DNS records, reducing the administrative burden on IT staff. Automation features, such as the ability to automatically update DNS records based on changes in cloud infrastructure, further streamline management.
- Enhanced Security: Cloud DNS services often provide built-in security features, such as DNSSEC (DNS Security Extensions), to protect against DNS spoofing and other attacks. DNSSEC uses digital signatures to verify the authenticity of DNS data, ensuring that users are directed to the correct resources. DDoS protection is also commonly included, safeguarding against malicious traffic that can disrupt DNS services.
- Cost Efficiency: Cloud DNS services typically offer a pay-as-you-go pricing model, which allows organizations to pay only for the resources they consume. This can result in significant cost savings compared to traditional on-premises DNS implementations, which require upfront investments in hardware and ongoing maintenance costs.
Planning DNS for Cloud Migration
Migrating DNS to the cloud is a critical step in modernizing infrastructure and enhancing operational efficiency. However, it demands meticulous planning and a phased approach to minimize disruption and ensure a smooth transition. This section Artikels the preliminary steps, readiness assessments, and crucial considerations for a successful DNS cloud migration.
Initial Pre-Migration Steps
Before initiating the cloud migration, several preparatory steps are essential. These steps are designed to provide a comprehensive understanding of the current DNS landscape, enabling informed decision-making and mitigating potential risks.
- Inventory and Documentation: Conduct a thorough inventory of the existing DNS infrastructure. This includes identifying all authoritative and recursive DNS servers, DNS records (A, AAAA, CNAME, MX, TXT, etc.), zones, and their configurations. Comprehensive documentation, including IP addresses, server roles, and zone transfer settings, is crucial. This detailed understanding forms the baseline for the migration process.
- Performance Baseline Establishment: Establish a performance baseline for the existing DNS infrastructure. Monitor key metrics such as query response times, query volume, error rates, and server resource utilization (CPU, memory, network). This baseline serves as a reference point to measure the success of the migration and identify any performance degradations post-migration. Tools like `dig`, `nslookup`, and monitoring solutions like Prometheus with Grafana can be used for this purpose.
- Zone File Backup and Verification: Create a complete backup of all zone files. Verify the integrity of these backups to ensure they are consistent and can be successfully restored. This backup acts as a safety net, allowing for quick rollback in case of unforeseen issues during or after the migration. Test the restore process to confirm its functionality.
- Dependency Mapping: Identify all applications and services that rely on DNS. This includes internal applications, external services, and any dependencies on specific DNS records or configurations. Understanding these dependencies is vital for minimizing downtime and ensuring that all affected services are properly configured to use the new cloud-based DNS.
- Stakeholder Communication: Communicate the planned migration to all relevant stakeholders, including IT operations, application owners, and security teams. Provide a clear timeline, potential impact, and mitigation strategies. This proactive communication helps manage expectations and ensures everyone is aware of the changes.
DNS Infrastructure Readiness Checklist
Assessing the readiness of the current DNS infrastructure is a critical step. The following checklist helps evaluate the current state and identify any potential roadblocks before the migration.
- DNS Server Hardware and Software: Evaluate the hardware and software of the existing DNS servers. Determine if the hardware is adequately provisioned to handle the current and projected DNS traffic. Identify the operating system and DNS server software versions (e.g., BIND, Windows DNS). Assess their compatibility with cloud DNS providers, especially regarding features and supported record types.
- Network Configuration: Review the network configuration, including IP addressing, firewall rules, and network segmentation. Ensure that DNS traffic (port 53 UDP/TCP) is allowed between the current DNS servers and the cloud DNS provider’s servers. Analyze network latency and bandwidth to assess potential performance impacts.
- Security Posture: Evaluate the current security posture of the DNS infrastructure. This includes assessing the implementation of DNSSEC, protection against DDoS attacks, and access control mechanisms. Determine if the current security measures can be migrated to the cloud DNS provider or if additional security configurations are required.
- DNS Records and Zones: Review all DNS records and zones. Identify any complex configurations, such as wildcard records, dynamic DNS updates, or DNS-based traffic management. Ensure that the cloud DNS provider supports all required record types and features. Analyze the number of zones and records to assess potential scaling requirements.
- Monitoring and Alerting: Evaluate the existing monitoring and alerting setup. Determine if the current monitoring tools can be integrated with the cloud DNS provider’s monitoring capabilities. Establish a comprehensive monitoring plan to track DNS performance, availability, and security after the migration.
Choosing a Cloud DNS Provider: Critical Factors
Selecting the right cloud DNS provider is crucial for the success of the migration. Several critical factors should be considered during the selection process.
- Performance and Scalability: Evaluate the provider’s performance, including query response times, global network coverage, and ability to handle high query volumes. Assess the provider’s scalability to accommodate future growth in DNS traffic. Consider providers with geographically distributed DNS servers for improved performance and redundancy.
- Security Features: Prioritize providers with robust security features, including DDoS protection, DNSSEC support, and access control mechanisms. Ensure the provider offers features to mitigate DNS-based attacks and protect against unauthorized access. Evaluate the provider’s security certifications and compliance standards (e.g., ISO 27001, SOC 2).
- Ease of Use and Management: Assess the provider’s user interface, API, and automation capabilities. Consider providers with user-friendly interfaces, robust APIs for automation, and integration with popular cloud platforms. Evaluate the ease of managing DNS records, zones, and configurations.
- Pricing and Support: Compare pricing models and ensure they align with the organization’s budget and traffic patterns. Evaluate the provider’s support options, including documentation, support channels (e.g., email, phone, chat), and service level agreements (SLAs). Consider the availability of 24/7 support.
- Integration and Compatibility: Ensure the provider integrates seamlessly with the existing cloud infrastructure and other services. Evaluate the provider’s compatibility with the organization’s chosen cloud platform (e.g., AWS, Azure, GCP). Consider the availability of integrations with other services, such as content delivery networks (CDNs) and security information and event management (SIEM) systems.
- Features and Functionality: Assess the provider’s features and functionality, including support for various DNS record types, DNS-based traffic management, and advanced features such as DNS analytics. Evaluate the availability of features that can enhance performance, security, and manageability.
Selecting a Cloud DNS Provider
Choosing the right cloud DNS provider is a critical decision in cloud migration, directly impacting performance, cost, and operational efficiency. The selection process requires a thorough evaluation of various features, including pricing models, latency characteristics, feature sets, and scalability capabilities. This analysis ensures that the chosen provider aligns with the specific requirements of the cloud migration strategy, ultimately contributing to a successful and optimized cloud deployment.
Comparing Cloud DNS Provider Features
The selection of a cloud DNS provider necessitates a detailed comparison of their offerings. This comparison should consider several key factors to make an informed decision. The following table provides a comparative analysis of the leading cloud DNS providers, including AWS Route 53, Google Cloud DNS, and Azure DNS, across critical parameters.
| Feature | AWS Route 53 | Google Cloud DNS | Azure DNS |
|---|---|---|---|
| Pricing | Pay-as-you-go based on query volume, with options for hosted zones. Pricing varies depending on region and query type. | Pay-as-you-go based on query volume and hosted zone size. Offers tiered pricing based on usage. | Pay-as-you-go based on query volume. Pricing varies depending on zone type (public/private) and the number of DNS records. |
| Latency | Utilizes a global network of authoritative DNS servers. Generally offers low latency due to its extensive network infrastructure and Anycast routing. | Leverages Google’s global network and Anycast DNS. Provides low latency, benefiting from Google’s worldwide presence and optimized routing. | Employs Azure’s global network of DNS servers. Offers low latency, especially for resources deployed within the Azure infrastructure. |
| Features | Supports various DNS record types (A, AAAA, CNAME, MX, etc.), DNSSEC, traffic management (latency-based routing, failover, geolocation routing), and integration with other AWS services. Provides health checks for monitoring. | Supports standard DNS record types, DNSSEC, and integration with Google Cloud services. Offers features like DNS forwarding and DNS-over-HTTPS (DoH). | Supports standard DNS record types, DNSSEC, and integration with other Azure services. Offers private DNS zones and alias records for Azure resources. |
| Scalability | Designed for high availability and scalability. Can handle massive query volumes and provides automatic scaling. | Highly scalable and designed to handle large query volumes. Leverages Google’s infrastructure for automatic scaling. | Scalable and designed to handle significant query volumes. Automatically scales to meet demand. |
Choosing a Provider Based on Migration Needs
The selection of a cloud DNS provider should be driven by the specific needs of the cloud migration. Different migration scenarios necessitate different considerations.
- Geographic Distribution: For applications serving a global audience, a provider with a globally distributed network of DNS servers, like AWS Route 53 or Google Cloud DNS, is crucial for minimizing latency. Anycast routing is essential for optimal performance in such scenarios, as it directs users to the nearest available server.
- Integration with Cloud Services: If the cloud migration heavily relies on a specific cloud provider’s services, selecting the corresponding DNS provider can simplify integration and management. For instance, if migrating to AWS, Route 53 provides seamless integration with other AWS services, such as Amazon EC2 and Amazon S3. Similarly, Azure DNS integrates effectively with Azure resources.
- Cost Optimization: The pricing models of DNS providers vary. Consider the anticipated query volume and the complexity of the DNS configuration. Pay-as-you-go models might be suitable for fluctuating workloads, while fixed-cost options could be beneficial for predictable traffic patterns. Regularly analyzing DNS usage and costs is important to identify opportunities for optimization.
- Security Requirements: Security features like DNSSEC are essential for protecting against DNS spoofing and other attacks. Ensure the provider offers robust security features that meet the organization’s security policies.
Impact of Provider Selection on Performance and Cost
The choice of a cloud DNS provider directly influences both performance and cost. Performance is primarily affected by latency, which is the time it takes for a DNS query to be resolved.
- Performance: A provider with a global network and Anycast routing will typically offer lower latency. Lower latency translates to faster website loading times and improved application responsiveness. For example, a study by Cedexis (now part of Catchpoint) demonstrated that DNS resolution time can significantly impact overall website performance. Choosing a provider with a strong presence in the regions where the application’s users are located can substantially improve the user experience.
- Cost: The cost of DNS services can vary significantly based on the provider’s pricing model, query volume, and feature set. A provider with a pay-as-you-go model may be cost-effective for low-traffic websites, but costs can escalate rapidly for high-traffic applications. It is crucial to analyze the expected traffic volume and choose a provider whose pricing model aligns with the anticipated usage.
For instance, using a provider with a tiered pricing structure can provide cost savings as the query volume increases.
The selection of a cloud DNS provider is a critical decision that requires careful consideration of various factors. By analyzing the features, pricing, latency, and scalability of different providers and aligning these factors with the specific requirements of the cloud migration, organizations can ensure optimal performance, cost efficiency, and operational success.
DNS Configuration for Hybrid Cloud Environments
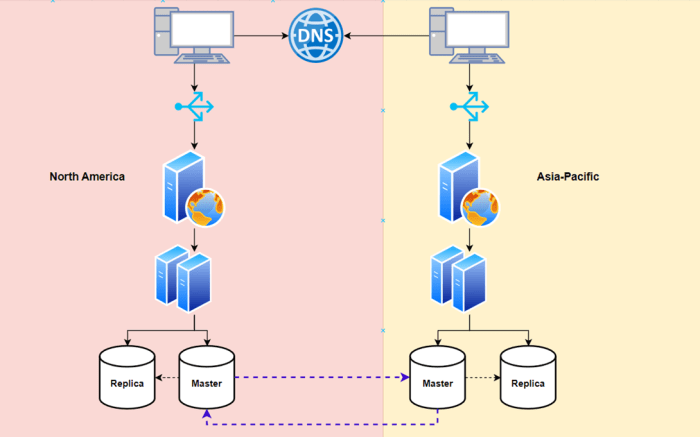
Integrating DNS across on-premises and cloud resources is crucial for maintaining consistent service discovery and application availability in hybrid cloud environments. This integration ensures that users and applications, regardless of their location, can seamlessly access resources hosted in either environment. This section details the strategies, configurations, and best practices for achieving effective DNS management in hybrid setups.
Strategies for Integrating DNS Across On-Premises and Cloud Resources
Effective integration of DNS in hybrid environments requires careful planning and the selection of appropriate strategies to ensure seamless name resolution. These strategies facilitate communication between on-premises and cloud resources, allowing for consistent access to applications and services.
- DNS Forwarding: This involves configuring on-premises DNS servers to forward requests for cloud-hosted resources to the cloud DNS provider. This allows on-premises clients to resolve cloud resource names without needing to be aware of the cloud’s specific DNS infrastructure. For example, an on-premises DNS server can be configured to forward all queries for the domain `cloud.example.com` to the cloud provider’s authoritative DNS servers.
This simplifies the on-premises DNS configuration.
- DNS Delegation: Delegation involves creating a zone in the on-premises DNS that points to the cloud DNS provider. This is similar to forwarding but offers more control. The on-premises DNS server acts as the authoritative server for a specific subdomain, delegating responsibility for name resolution within that subdomain to the cloud DNS provider. For instance, the `cloud.example.com` zone could be delegated to the cloud provider’s nameservers.
- Hybrid DNS Servers: Deploying DNS servers in both the on-premises and cloud environments allows for a more distributed and resilient DNS infrastructure. These servers can be configured to synchronize their zone data, ensuring consistency across both environments. This approach is beneficial for applications requiring low latency and high availability.
- Reverse DNS Integration: Configuring reverse DNS lookup (PTR records) across the hybrid environment is essential for tasks like troubleshooting and security. Ensure that both on-premises and cloud environments can resolve IP addresses to hostnames, facilitating easier identification of network traffic origins. For example, if an application in the cloud sends traffic to an on-premises server, the reverse DNS lookup should resolve the cloud instance’s IP address to its hostname.
Configuring Split-Horizon DNS for Hybrid Setups
Split-horizon DNS is a crucial technique for providing different DNS responses based on the source of the query. This is particularly useful in hybrid cloud environments where internal and external users may need to access the same resources using different IP addresses or service endpoints.
Split-horizon DNS is often achieved using multiple DNS views or zones. For example, you might have one view for internal users that provides private IP addresses for resources and another view for external users that provides public IP addresses or load balancer endpoints.
- Implementing Split-Horizon DNS: Implementing split-horizon DNS involves creating different DNS zones or views within the DNS server. Each view is configured to serve a different set of DNS records based on the source of the DNS query. This allows you to provide different answers to internal and external clients.
- Internal View: The internal view provides DNS records that resolve to the private IP addresses of resources within the on-premises or cloud environments. This view is used by internal users and applications.
- External View: The external view provides DNS records that resolve to the public IP addresses or load balancer endpoints of the same resources. This view is used by external users accessing the applications.
- Configuration Examples: Consider a hybrid application with a web server accessible both internally and externally. In a split-horizon configuration:
- Internal Users: When an internal user queries `webapp.example.com`, the internal view provides the private IP address of the web server.
- External Users: When an external user queries `webapp.example.com`, the external view provides the public IP address or the address of a load balancer.
- DNS Server Support: Several DNS server solutions, such as BIND (Berkeley Internet Name Domain) and Microsoft DNS, support split-horizon configurations through views or zones. Cloud-based DNS providers like Amazon Route 53, Google Cloud DNS, and Azure DNS also provide split-horizon capabilities through their managed DNS services.
Best Practices for Managing DNS in a Hybrid Cloud
Effective DNS management in a hybrid cloud environment requires adherence to specific best practices to ensure reliability, security, and maintainability. These practices help to mitigate potential issues and ensure optimal performance.
- Centralized DNS Management: Employing a centralized DNS management system helps simplify the administration and ensure consistency across both on-premises and cloud environments. This can be achieved through the use of a single DNS provider or a unified management interface.
- Automated DNS Updates: Implement automation to update DNS records whenever resources are provisioned, deprovisioned, or their IP addresses change. Automation reduces manual errors and improves the speed of DNS propagation. Consider using infrastructure-as-code (IaC) tools or scripting to manage DNS records.
- Monitoring and Alerting: Continuously monitor DNS performance and availability. Implement alerting to notify administrators of any issues, such as high query latency, failed resolutions, or DNS server outages. Monitoring tools can provide valuable insights into the health of your DNS infrastructure.
- Security Considerations: Secure DNS infrastructure by implementing DNSSEC (DNS Security Extensions) to protect against DNS spoofing and cache poisoning attacks. Regularly review and update DNS records to prevent unauthorized access to resources. Implement access control lists (ACLs) to restrict who can modify DNS records.
- Documentation: Maintain comprehensive documentation of your DNS configuration, including zone files, DNS server settings, and any automation scripts. This documentation is essential for troubleshooting, auditing, and ensuring consistency across your hybrid cloud environment.
- Disaster Recovery Planning: Include DNS in your disaster recovery plan. Ensure that DNS services can be restored quickly in case of an outage. This might involve having secondary DNS servers in different geographic locations or leveraging cloud-based DNS providers with high availability.
Migrating DNS Records
Migrating DNS records to a cloud provider is a critical step in the cloud migration process, impacting website availability and application performance. A well-executed migration minimizes disruption and ensures a smooth transition. This section details the procedures, best practices, and methods for a successful DNS record migration.
Procedures for Migrating DNS Records
The migration of DNS records involves several key steps, each crucial for maintaining service continuity. Failure to properly execute these steps can lead to significant downtime and user impact.
- Preparation and Planning: This phase involves a thorough assessment of the existing DNS infrastructure. Document all DNS records, including A, CNAME, MX, TXT, and any other relevant record types. Identify dependencies between records and applications. Select the cloud DNS provider and configure an account. This planning phase should also include setting up monitoring tools to track the performance of the DNS servers.
- Record Export: Export the DNS zone files from the current DNS provider. This typically involves using tools provided by the current provider or the use of standard utilities like `BIND`’s `named-checkconf` and `named-checkzone`. The exported data should be in a standard zone file format.
- Record Import: Import the exported DNS records into the new cloud DNS provider. This process often involves uploading the zone file directly or using APIs to programmatically create records. The cloud provider will then validate the records for syntax errors and compliance.
- Testing and Validation: Before making any changes to the authoritative nameservers, it is essential to test and validate the newly imported records. Use DNS lookup tools (e.g., `dig`, `nslookup`) to verify that the records resolve correctly. Ensure all records are resolving to the expected IP addresses and other values. Also, test the propagation of the records across different geographic locations.
- Nameserver Updates: Update the authoritative nameservers for the domain with the new cloud DNS provider’s nameservers. This is typically done through the domain registrar. The registrar will then update the root nameservers to point to the new authoritative nameservers.
- Monitoring and Optimization: After the migration, continuously monitor the performance of the DNS service. Track query response times, availability, and any error rates. Use monitoring tools to identify and resolve any performance issues. Optimize DNS settings, such as TTL values, to improve performance.
Step-by-Step Guide for Transferring Zone Files
Transferring zone files is a fundamental step in migrating DNS records. The process varies slightly depending on the existing DNS provider, but the core steps remain consistent.
- Identify the Current DNS Provider: Determine the current provider managing the DNS records for the domain. This information is available in the WHOIS records or through the domain registrar.
- Access the DNS Management Interface: Log in to the DNS management interface of the current provider. This interface allows for the export of the zone file.
- Export the Zone File: Locate the option to export the zone file. This may be labeled as “Export Zone File,” “Download Zone File,” or something similar. The file will typically be in a standard format, such as BIND format (.zone).
- Review the Zone File: Open the exported zone file in a text editor to review the contents. Ensure all records are present and accurate. Verify that there are no syntax errors.
- Prepare the Cloud DNS Provider: Log in to the cloud DNS provider’s management console. Create a new DNS zone for the domain.
- Import the Zone File: Upload the zone file to the cloud DNS provider. The provider will parse the file and create the corresponding DNS records. Some providers may also offer a “zone transfer” feature, which simplifies the process.
- Verify Record Import: After importing the zone file, verify that all records have been imported correctly. Use the cloud provider’s management interface or DNS lookup tools to confirm the records’ accuracy.
- Adjust TTL Values (Optional): Review and adjust the Time-To-Live (TTL) values for the records. Lower TTL values can speed up DNS propagation, but they also increase the load on the DNS servers.
Methods for Minimizing Downtime During DNS Migration
Minimizing downtime is a critical objective during DNS migration. Several strategies can be employed to reduce the impact on users.
- Pre-warming DNS: Before the actual migration, configure the new cloud DNS provider with the same DNS records as the existing provider. This process is called “pre-warming.”
- Lowering TTLs (Time-To-Live): Reduce the TTL values of DNS records before the migration. This allows DNS records to propagate faster, reducing the time it takes for changes to be reflected across the internet. The recommended minimum TTL is 60 seconds before migration, but ensure to revert back to the original settings after the migration is complete.
- Dual DNS Configuration: Maintain both the old and new DNS providers simultaneously for a short period during the migration. This can provide redundancy and minimize downtime. However, it is essential to synchronize the DNS records between the two providers to prevent inconsistencies.
- Phased Migration: If possible, migrate DNS records in phases. This allows for testing and validation of individual records or subdomains before migrating the entire domain. This approach reduces the risk of a complete outage.
- Monitoring and Alerting: Implement robust monitoring and alerting to detect any issues during the migration. Monitor DNS query response times, availability, and error rates. Set up alerts to notify administrators of any problems.
- Testing and Validation: Thoroughly test the DNS records before and after the migration. Use DNS lookup tools to verify that the records resolve correctly. Validate the records from different geographic locations to ensure global propagation.
- Rollback Plan: Develop a rollback plan in case of unexpected issues during the migration. The rollback plan should Artikel the steps to revert to the original DNS configuration quickly. Ensure that the rollback plan is tested and documented.
- Use of DNSSEC (Domain Name System Security Extensions): While not directly minimizing downtime, proper configuration of DNSSEC can help maintain the integrity of DNS records during the migration process. This provides an added layer of security and helps to prevent DNS spoofing attacks.
Implementing DNS Security Measures in the Cloud
The dynamic nature of cloud environments introduces new vulnerabilities to Domain Name System (DNS) security. Protecting DNS infrastructure in the cloud is critical for maintaining application availability, data integrity, and overall cybersecurity posture. This section explores common DNS security threats, best practices for cloud DNS security, and the benefits of DNSSEC implementation.
Common DNS Security Threats in Cloud Environments
Cloud environments, while offering scalability and flexibility, are susceptible to several DNS-related security threats. These threats can disrupt services, compromise data, and lead to significant financial and reputational damage. Understanding these threats is the first step toward implementing effective security measures.
- DNS Amplification Attacks: These attacks leverage open DNS resolvers to amplify the size of DNS responses, overwhelming the target server with traffic. Attackers send a small DNS query to an open resolver, which then responds with a much larger response to the victim server, leading to denial-of-service (DoS) or distributed denial-of-service (DDoS) conditions. The amplification factor can be significant, making mitigation challenging.
- DNS Spoofing/Cache Poisoning: Attackers inject false information into DNS caches, redirecting users to malicious websites or servers. This is achieved by sending crafted DNS responses before the legitimate response, poisoning the cache with incorrect IP address mappings. This can lead to phishing attacks, malware distribution, and data theft.
- DDoS Attacks: Cloud-based DNS services are attractive targets for DDoS attacks, aiming to exhaust resources and make services unavailable. These attacks can range from volumetric attacks (flooding the server with traffic) to application-layer attacks (targeting specific DNS functionalities). The scale and sophistication of DDoS attacks are constantly evolving.
- NXDOMAIN Attacks: Attackers flood the DNS server with queries for non-existent domain names (NXDOMAIN), aiming to consume resources and potentially cause a denial of service. These attacks can be particularly effective against DNS servers that do not properly handle NXDOMAIN responses.
- Zone Transfers: Unauthorized zone transfers can expose sensitive DNS records, including internal network configurations and hostnames, to attackers. This information can be used for reconnaissance and planning further attacks. Properly configured zone transfer restrictions are crucial.
- Man-in-the-Middle (MitM) Attacks: If the communication between the user and the DNS server is not secured, an attacker can intercept and modify DNS responses. This allows them to redirect traffic to malicious servers or intercept sensitive data.
Best Practices for Securing DNS in the Cloud
Implementing robust security practices is essential for mitigating the risks associated with DNS in the cloud. A layered approach, incorporating various security measures, provides the best protection.
- Use a Reputable Cloud DNS Provider: Selecting a provider with built-in security features, such as DDoS protection, anycast DNS, and DNSSEC support, is crucial. Reputable providers often have dedicated security teams and robust infrastructure to defend against attacks.
- Implement DNSSEC (Domain Name System Security Extensions): DNSSEC adds a layer of security to DNS by digitally signing DNS records. This verifies the authenticity and integrity of DNS data, preventing cache poisoning and other attacks. DNSSEC is a fundamental security measure for cloud DNS.
- Enable DDoS Protection: Utilize DDoS mitigation services provided by the cloud provider or third-party vendors. These services can detect and mitigate DDoS attacks by filtering malicious traffic and absorbing the attack’s impact. The use of anycast DNS is a key component of effective DDoS mitigation.
- Restrict Zone Transfers: Configure DNS servers to only allow zone transfers from authorized servers. This prevents unauthorized access to DNS records and reduces the risk of information leakage. Implement access control lists (ACLs) to restrict zone transfers based on IP address or network range.
- Implement Rate Limiting: Rate limiting helps to prevent DNS amplification attacks and other forms of abuse by limiting the number of DNS queries a server will process from a single source within a specific timeframe. This can protect against both accidental and malicious traffic spikes.
- Monitor DNS Traffic: Regularly monitor DNS traffic for suspicious activity, such as unusually high query volumes, unexpected query types, or changes in DNS records. Use security information and event management (SIEM) tools to analyze logs and detect potential threats.
- Regularly Update DNS Software: Keep DNS server software up to date with the latest security patches to address known vulnerabilities. Vulnerabilities in DNS software are frequently exploited by attackers.
- Implement Access Control: Implement strong access controls to restrict who can make changes to DNS records. Use multi-factor authentication (MFA) for all administrative accounts. Follow the principle of least privilege.
- Use Firewalls: Implement firewalls to restrict access to DNS servers and protect them from unauthorized traffic. Configure firewall rules to allow only necessary traffic, such as DNS queries and responses.
- Implement Redundancy and Failover: Deploy DNS servers in a redundant configuration to ensure high availability. If one server fails, the others can continue to provide DNS services. Use a geo-diverse anycast network for improved resilience.
Benefits of Using DNSSEC in a Cloud Context
DNSSEC provides several significant benefits, particularly in a cloud environment where security and availability are paramount. These benefits enhance the trustworthiness and resilience of DNS services.
- Protection Against Cache Poisoning: DNSSEC digitally signs DNS records, allowing resolvers to verify the authenticity of the data. This prevents attackers from injecting false information into the DNS cache, protecting users from being redirected to malicious websites.
- Improved Data Integrity: DNSSEC ensures that DNS data has not been tampered with during transit. This prevents attackers from modifying DNS records to redirect traffic or launch other attacks.
- Enhanced Trust: By providing verifiable DNS data, DNSSEC enhances the trust that users have in the cloud services they are accessing. This is particularly important for e-commerce sites and other applications that handle sensitive information.
- Mitigation of DNS Spoofing Attacks: DNSSEC prevents attackers from spoofing DNS responses, ensuring that users are directed to the correct servers. This is crucial for preventing phishing attacks and other forms of online fraud.
- Improved Security Posture: Implementing DNSSEC significantly strengthens the overall security posture of cloud infrastructure. It provides a critical layer of defense against a wide range of DNS-based attacks.
- Compliance with Security Standards: Many industry regulations and security standards require the use of DNSSEC to protect sensitive data. Implementing DNSSEC helps organizations meet these compliance requirements.
- Integration with Cloud Services: Most cloud DNS providers offer DNSSEC support, making it easy to integrate DNSSEC into existing cloud infrastructure. This allows organizations to quickly and easily secure their DNS services.
DNS Monitoring and Performance Optimization
Effective DNS management in a cloud environment necessitates continuous monitoring and optimization. Proactive monitoring identifies performance bottlenecks, security vulnerabilities, and potential points of failure. Optimization strategies enhance DNS response times, ensuring a seamless user experience and efficient resource utilization. This section details tools, techniques, and strategies for achieving optimal DNS performance and scalability in the cloud.
Tools and Techniques for Monitoring DNS Performance
Comprehensive DNS monitoring involves the collection and analysis of various metrics to assess performance, availability, and security. Several tools and techniques facilitate this process, providing insights into DNS behavior and enabling informed decision-making.
- DNS Query Logging: Enabling DNS query logging within the cloud DNS provider (e.g., Amazon Route 53, Google Cloud DNS, Azure DNS) captures detailed information about each DNS query. This data includes the querying client’s IP address, the requested domain name, the query type (A, AAAA, MX, etc.), the response code (NOERROR, NXDOMAIN, SERVFAIL, etc.), and the response time. Analyzing these logs reveals query patterns, identifies slow-performing queries, and detects potential malicious activity.
For instance, an unusual spike in NXDOMAIN responses might indicate a denial-of-service (DoS) attempt.
- Synthetic Monitoring: Synthetic monitoring, also known as active monitoring, involves simulating DNS queries from various locations to proactively assess DNS resolution performance. This technique provides insights into DNS response times, availability, and the consistency of DNS resolution across different geographic regions. Tools like Pingdom, Dynatrace, and ThousandEyes offer synthetic DNS monitoring capabilities, allowing users to configure probes that regularly query specific domain names and report on performance metrics.
A geographically diverse set of probes is crucial for accurately assessing the user experience.
- Real User Monitoring (RUM): Real User Monitoring (RUM) passively collects performance data from actual user interactions with a website or application. RUM tools, often implemented through JavaScript agents embedded in web pages, measure DNS resolution times as part of the overall page load time. This provides a realistic view of DNS performance from the end-user perspective, capturing the impact of DNS performance on the user experience.
Tools like New Relic and Datadog offer RUM capabilities that include DNS performance metrics.
- Performance Testing Tools: Dedicated performance testing tools, such as `dig` and `nslookup` (command-line utilities), and more sophisticated tools like `dnsperf`, are essential for evaluating DNS server performance. These tools allow administrators to simulate a high volume of DNS queries to assess the server’s capacity and identify potential bottlenecks. `dnsperf` is particularly useful for benchmarking DNS servers and analyzing their performance under load, helping to identify the maximum query rate (QPS) the server can handle.
- Availability Monitoring: Monitoring the availability of DNS servers is crucial for ensuring continuous service. This can be achieved through health checks and alerts configured within the cloud provider’s services. These checks regularly verify the accessibility of the DNS servers and trigger alerts when failures are detected. These alerts allow for prompt intervention and minimize downtime. For example, Route 53’s health checks can monitor the health of DNS endpoints, and Azure DNS offers monitoring and alerting capabilities through Azure Monitor.
Methods for Optimizing DNS Response Times
Optimizing DNS response times is critical for improving website performance and user experience. Several strategies can be implemented to reduce latency and ensure faster DNS resolution.
- Leveraging DNS Caching: Caching DNS records reduces the load on authoritative DNS servers and accelerates DNS resolution. This can be achieved through several methods:
- Browser Caching: Web browsers cache DNS records for a specified time (TTL). When a user revisits a website, the browser can retrieve the IP address from its cache, avoiding a new DNS query.
- Recursive Resolvers: Recursive DNS resolvers (e.g., those provided by ISPs or public DNS services like Google Public DNS or Cloudflare) cache DNS records, serving as intermediaries between the user and the authoritative DNS servers. Using a fast and reliable recursive resolver can significantly improve DNS resolution times.
- CDN Caching: Content Delivery Networks (CDNs) often cache DNS records along with content. This allows users to be directed to the CDN’s edge servers closest to their location, reducing latency.
- Optimizing DNS Record TTLs: The Time-To-Live (TTL) value specifies how long a DNS record is cached by resolvers. Adjusting TTL values can influence the balance between propagation time and cache freshness.
- Lower TTLs: Lower TTL values (e.g., 300 seconds or less) can lead to faster propagation of DNS changes but may increase the load on authoritative servers. This is useful for dynamic environments where frequent changes are expected.
- Higher TTLs: Higher TTL values (e.g., 3600 seconds or more) reduce the load on authoritative servers and improve resolution times for frequently accessed records. However, it may take longer for changes to propagate.
- Balancing Act: The optimal TTL value depends on the specific use case and the frequency of DNS record changes. Careful consideration is needed to find the right balance.
- Using a Fast and Reliable DNS Provider: Selecting a cloud DNS provider with a robust infrastructure and high availability is crucial. Factors to consider include:
- Global Presence: A provider with a geographically distributed network of DNS servers reduces latency for users worldwide.
- Performance Metrics: Review the provider’s performance metrics, such as query response times and uptime, to assess their reliability.
- Scalability: The provider must be able to handle a high volume of DNS queries and accommodate future growth.
- Implementing DNS Prefetching: DNS prefetching is a technique where the browser proactively resolves DNS records for links on a web page before the user clicks on them. This can significantly reduce the perceived page load time. The `rel=”dns-prefetch”` tag is used in HTML to instruct the browser to prefetch DNS records.
- Optimizing DNS Record Configuration: Proper configuration of DNS records can improve performance. This includes:
- Avoiding Excessive DNS Records: Minimize the number of DNS records to reduce the size of DNS responses.
- Using CNAME Records Judiciously: CNAME records can add an extra lookup step. Use them carefully and avoid chaining multiple CNAME records.
- Implementing DNSSEC: DNS Security Extensions (DNSSEC) add a layer of security to DNS by verifying the authenticity of DNS responses. While DNSSEC adds a small amount of overhead, it protects against DNS spoofing attacks.
Strategies for Handling DNS Scalability Challenges
As cloud environments grow, DNS scalability becomes increasingly important. Several strategies can be employed to ensure DNS infrastructure can handle increased traffic and maintain optimal performance.
- Using a Scalable Cloud DNS Provider: Choose a cloud DNS provider with a proven track record of handling large volumes of traffic. Providers like Amazon Route 53, Google Cloud DNS, and Azure DNS are designed for scalability and offer features like:
- Global Anycast Network: Anycast routing distributes DNS queries across a network of geographically distributed servers, ensuring that users are directed to the closest available server.
- Automatic Scaling: Cloud DNS providers automatically scale their infrastructure to handle fluctuations in traffic.
- High Availability: These providers offer high availability, with multiple redundant servers and failover mechanisms.
- Implementing DNS Load Balancing: DNS load balancing distributes DNS queries across multiple servers, preventing any single server from becoming overloaded. This can be achieved using:
- Round-Robin DNS: A simple method where DNS queries are distributed in a cyclical manner across multiple IP addresses.
- Weighted Round-Robin DNS: Allows administrators to assign weights to each server, directing a larger proportion of traffic to more capable servers.
- Geographic DNS: Directs users to the closest available server based on their geographic location.
- Caching DNS Records Effectively: As discussed previously, effective caching is crucial for scalability. This includes:
- Optimizing TTLs: Set appropriate TTL values for DNS records to balance propagation time and cache efficiency.
- Leveraging CDN Caching: CDNs cache DNS records along with content, reducing the load on authoritative DNS servers.
- Monitoring and Alerting: Implement robust monitoring and alerting to proactively identify and address potential scalability issues. This includes:
- Monitoring DNS Query Volume: Track the number of DNS queries per second (QPS) to identify trends and potential bottlenecks.
- Monitoring DNS Response Times: Track DNS response times to detect performance degradation.
- Setting Alerts: Configure alerts to trigger when performance metrics exceed predefined thresholds.
- Planning for Growth: Proactively plan for future growth by:
- Estimating Future Traffic: Forecast future DNS query volume based on expected website traffic and application usage.
- Selecting Scalable DNS Services: Choose DNS services that can scale to meet future demands.
- Regular Capacity Planning: Regularly review DNS infrastructure capacity and make adjustments as needed.
Automation and Scripting for DNS Management
Automating DNS management is crucial for efficient cloud migration and ongoing operational effectiveness. It reduces manual effort, minimizes human error, and enables rapid response to changes in the cloud environment. Automation facilitates scalability, improves reliability, and ensures consistent configuration across all DNS zones and records.
Demonstrating the Use of Automation Tools for DNS Record Management
Several automation tools are available for managing DNS records. These tools streamline the process of creating, modifying, and deleting DNS records, thereby significantly reducing the time and effort required for DNS administration. The selection of a suitable tool depends on factors such as the cloud provider, the complexity of the DNS infrastructure, and the level of customization required. Cloud providers often offer native automation capabilities integrated with their DNS services.
These capabilities allow users to manage DNS records programmatically through APIs, command-line interfaces (CLIs), and infrastructure-as-code (IaC) tools. Third-party tools provide additional functionalities, such as multi-cloud DNS management, advanced monitoring, and enhanced security features.
- Cloud Provider Native Tools: Amazon Route 53, Google Cloud DNS, and Azure DNS provide APIs, CLIs (e.g., AWS CLI, gcloud, az), and integration with IaC tools like Terraform and CloudFormation. These tools allow programmatic control over DNS records, including record creation, modification, and deletion. For example, using the AWS CLI, a user can create an A record with a specific IP address for a domain.
- Infrastructure-as-Code (IaC) Tools: Terraform, Ansible, and similar tools enable the definition and management of DNS infrastructure as code. Users can define their DNS configuration in configuration files, and these tools automate the deployment and management of the DNS infrastructure. This approach promotes version control, repeatability, and consistency.
- Third-Party Tools: Tools such as NS1 and Dyn (now Oracle Dyn) offer advanced features, including traffic management, global server load balancing (GSLB), and intelligent DNS routing. These tools often provide robust APIs and integrations with other automation platforms.
Providing Examples of Scripts for Automating DNS Tasks (e.g., Record Updates, Zone File Synchronization)
Scripting plays a critical role in automating DNS tasks. Scripts automate repetitive tasks, ensuring consistency and efficiency. They can be used to update DNS records, synchronize zone files, and perform other management operations. The scripting language chosen depends on the environment and the administrator’s preferences. Python, Bash, and PowerShell are commonly used.
- Updating DNS Records: A Python script using the AWS SDK for Python (Boto3) can be used to update an A record in Route 53. The script would authenticate with AWS, retrieve the existing record set, and update it with the new IP address. This eliminates the need for manual updates via the AWS console or CLI.
- Zone File Synchronization: A Bash script can be used to synchronize zone files between primary and secondary DNS servers. The script could use tools like `rsync` or `scp` to copy zone files from the primary server to the secondary servers, ensuring data consistency. The script could also trigger a reload of the DNS server configuration on the secondary servers after the synchronization.
- Automated DNS Record Creation: A PowerShell script could be written to automate the creation of DNS records based on data retrieved from a database or a configuration file. This is particularly useful in dynamic environments where new servers are frequently deployed.
Example Python script for updating an A record in Route 53 (Simplified):
import boto3 def update_a_record(domain_name, record_name, new_ip): client = boto3.client('route53') zone_id = 'YOUR_ZONE_ID' # Replace with your Zone ID try: response = client.change_resource_record_sets( HostedZoneId=zone_id, ChangeBatch= 'Changes': [ 'Action': 'UPSERT', 'ResourceRecordSet': 'Name': record_name, 'Type': 'A', 'TTL': 300, 'ResourceRecords': [ 'Value': new_ip , ], , ] ) print(f"Successfully updated record_name to new_ip") except Exception as e: print(f"Error updating record: e") if __name__ == "__main__": update_a_record("example.com", "www.example.com", "192.0.2.100") Note: This is a simplified example. Replace placeholders with your actual values. Ensure that the IAM role or user has the necessary permissions to modify Route 53 records.
Elaborating on the Benefits of Automating DNS Operations
Automating DNS operations offers numerous advantages, including improved efficiency, reduced errors, and enhanced scalability. Automation reduces the manual effort required for DNS management, allowing administrators to focus on other tasks. It minimizes the potential for human error, which can lead to downtime or security vulnerabilities.
- Reduced Manual Effort and Time Savings: Automating DNS tasks significantly reduces the time and effort required for DNS management. Tasks such as record updates and zone file synchronization, which could take hours to perform manually, can be completed in seconds or minutes using automated scripts.
- Minimized Human Error: Automation eliminates the risk of human error, such as typos or incorrect IP addresses, which can lead to DNS resolution failures. Automated scripts ensure that DNS records are updated consistently and accurately.
- Improved Scalability and Responsiveness: Automation enables DNS infrastructure to scale rapidly to meet changing demands. New DNS records can be created automatically when new servers or services are deployed, and DNS configurations can be updated quickly in response to traffic spikes or other events.
- Enhanced Consistency and Reliability: Automated processes ensure consistent DNS configurations across all environments. Version control systems, used with IaC tools, ensure that the DNS configuration is reproducible and that changes can be tracked and rolled back if necessary. This improves the overall reliability of the DNS infrastructure.
- Increased Security: Automating DNS management can improve security by enabling the consistent application of security policies and by reducing the attack surface. Scripts can be used to automatically apply security updates and to detect and respond to DNS attacks.
Troubleshooting Common DNS Issues in the Cloud
Cloud migration, while offering numerous benefits, can introduce complexities, particularly concerning Domain Name System (DNS) configurations. DNS, the backbone of internet navigation, is crucial for translating human-readable domain names into IP addresses. Issues with DNS can disrupt application availability, hinder user experience, and compromise security. This section delves into common DNS problems encountered during and after cloud migration, providing a troubleshooting guide and diagnostic tools to effectively address these challenges.
Common DNS Issues During and After Cloud Migration
Several recurring issues can plague DNS performance during and after a cloud migration. Understanding these issues is the first step towards effective troubleshooting.
- Propagation Delays: Changes to DNS records, such as updates to IP addresses or changes in authoritative name servers, require time to propagate across the internet. This delay, known as propagation delay, can lead to users being directed to outdated or incorrect resources. The extent of the delay depends on the Time-To-Live (TTL) settings configured for the DNS records and the caching behavior of recursive resolvers.
- Incorrect DNS Record Configuration: Misconfigurations in DNS records are a common source of problems. Typos, incorrect IP addresses, or missing records can prevent users from accessing cloud-hosted resources. This can include issues with A records (mapping domain names to IPv4 addresses), AAAA records (mapping domain names to IPv6 addresses), CNAME records (creating aliases), and MX records (specifying mail servers).
- DNS Resolution Failures: DNS resolution failures occur when a DNS server cannot resolve a domain name to an IP address. This can be caused by various factors, including network connectivity problems, DNS server outages, or incorrect DNS settings on the client or server side.
- DNS Server Performance Issues: The performance of DNS servers can be affected by factors such as high traffic loads, hardware limitations, or inefficient configurations. Slow DNS server responses can lead to slow website loading times and poor application performance.
- Security Issues: Cloud environments are attractive targets for cyberattacks. DNS can be exploited through attacks like DNS spoofing, DNS amplification, and DDoS attacks targeting DNS servers. These attacks can lead to service disruptions and data breaches.
- Hybrid Cloud DNS Conflicts: When migrating to a hybrid cloud environment, conflicts can arise between on-premises and cloud-based DNS configurations. This can lead to inconsistencies in DNS resolution, especially if DNS records are not synchronized properly.
Troubleshooting Guide for Resolving DNS-Related Problems
Effective troubleshooting requires a systematic approach. This guide Artikels a structured process for diagnosing and resolving DNS-related issues in the cloud.
- Verify Basic Connectivity: Before delving into DNS-specific issues, confirm that the basic network connectivity is functioning correctly. This includes checking that the client machine can reach the cloud environment and that there are no network outages. Use tools like `ping` to test basic connectivity.
- Check DNS Record Configuration: Review the DNS records for accuracy. Ensure that the records are correctly configured, including IP addresses, hostnames, and record types. Verify that the TTL settings are appropriate for the environment.
- Use DNS Lookup Tools: Employ DNS lookup tools to diagnose resolution issues. These tools query DNS servers and provide information about DNS records, server responses, and propagation status. Tools like `dig`, `nslookup`, and online DNS checkers are useful.
- Check DNS Server Health: Monitor the health and performance of the DNS servers. Ensure that the servers are responsive and not overloaded. Check for any error messages or performance bottlenecks.
- Investigate Propagation Delays: Understand and account for DNS propagation delays. Use DNS propagation checkers to monitor the propagation of DNS changes across the internet. Configure appropriate TTL values to minimize the impact of propagation delays.
- Examine DNS Server Logs: Analyze DNS server logs for error messages, warnings, and performance metrics. These logs provide valuable insights into DNS resolution failures and other issues.
- Test DNS Resolution from Multiple Locations: Test DNS resolution from different geographic locations to identify any regional DNS problems. This helps determine if the issue is specific to a certain area or network.
- Review Firewall and Security Settings: Ensure that firewall rules and security settings are not blocking DNS traffic. DNS uses UDP port 53, so ensure that this port is open for both inbound and outbound traffic.
- Contact Cloud Provider Support: If the issue persists, contact the cloud provider’s support team for assistance. They can provide specialized support and help diagnose complex DNS problems.
Examples of Diagnostic Tools for DNS Troubleshooting
A variety of tools are available to aid in the diagnosis of DNS problems. Selecting the right tools is crucial for efficient troubleshooting.
- `dig` (Domain Information Groper): `dig` is a command-line tool available on most Unix-like systems. It allows users to query DNS servers and retrieve detailed information about DNS records.
Example: `dig example.com` returns information about the A record for example.com. `dig @8.8.8.8 example.com MX` queries Google’s DNS server (8.8.8.8) for the MX records of example.com.
- `nslookup` (Name Server Lookup): `nslookup` is another command-line tool used to query DNS servers. It provides a simpler interface than `dig` but can still be useful for basic DNS lookups.
Example: `nslookup example.com` resolves example.com using the default DNS server. `nslookup example.com 8.8.8.8` resolves example.com using Google’s DNS server.
- Online DNS Checkers: Numerous online DNS checkers allow users to check DNS records and propagation status from various locations. These tools are often easier to use than command-line tools.
Example: DNS Checker ([https://dnschecker.org/](https://dnschecker.org/)) can be used to check the propagation of DNS records globally.
- Network Monitoring Tools: Network monitoring tools can be used to monitor DNS server performance and identify bottlenecks. These tools provide real-time data on DNS query response times, traffic volume, and error rates.
Example: Tools like SolarWinds Network Performance Monitor or Nagios can monitor DNS server health and performance.
- DNS Propagation Checkers: These tools are designed specifically to track the propagation of DNS changes across the internet. They query multiple DNS servers around the world and report on the status of DNS record updates.
Example: Whatsmydns.net ([https://www.whatsmydns.net/](https://www.whatsmydns.net/)) provides a global view of DNS propagation.
DNS and Application Performance: Impact and Strategies
The Domain Name System (DNS) plays a critical, often invisible, role in application performance. Delays in DNS resolution directly translate into delays in users accessing applications, impacting the overall user experience and potentially affecting business metrics. Understanding this relationship and implementing strategies to optimize DNS performance is essential for ensuring application responsiveness and maintaining a positive user experience, particularly in cloud environments where DNS is often a foundational service.
Relationship Between DNS Performance and Application Performance
The connection between DNS and application performance is fundamentally linked to the time it takes to resolve a domain name to an IP address. This process, known as DNS resolution, is a prerequisite for any user to connect to an application. The slower the DNS resolution, the longer the user waits before the application starts to load.
- DNS Resolution Process: When a user attempts to access an application (e.g., by typing a URL into a web browser), the following steps occur:
- The browser checks its local cache for the IP address associated with the domain name.
- If not found, the browser queries the operating system’s DNS resolver (usually provided by the Internet Service Provider – ISP).
- The resolver, in turn, queries a series of DNS servers, starting with root servers, then Top-Level Domain (TLD) servers, and finally, authoritative DNS servers.
- The authoritative DNS server provides the IP address of the requested domain.
- This IP address is then used by the browser to establish a connection with the application server.
- Impact of DNS Latency: Any delay in any of these steps contributes to overall DNS latency. This latency directly impacts the following:
- Page Load Times: Longer DNS resolution times increase the time it takes for a web page to load. This is especially noticeable for applications with multiple external resources (images, scripts, etc.) that require individual DNS lookups.
- User Experience: Slow application loading leads to a poor user experience, which can result in higher bounce rates, lower engagement, and lost conversions.
- Application Performance Metrics: Monitoring DNS performance is critical for understanding the overall application performance. Slow DNS resolution can mask other performance bottlenecks, making it difficult to diagnose and resolve issues.
- Example Scenario: Consider a web application that uses a CDN (Content Delivery Network). If the DNS resolution for the CDN’s domain is slow, it will take longer for the user’s browser to locate the CDN servers. This can negate the benefits of the CDN, such as reduced latency due to geographically distributed servers, and negatively impact the user experience.
Strategies for Improving DNS Performance to Enhance Application Responsiveness
Optimizing DNS performance involves a multi-faceted approach, focusing on minimizing latency and ensuring high availability. Several strategies can be employed to achieve this goal.
- Choose a Fast and Reliable DNS Provider: Selecting a DNS provider with a global network of servers, low latency, and high uptime is crucial. Cloud DNS providers like Amazon Route 53, Google Cloud DNS, and Azure DNS offer robust infrastructure and features designed for performance and scalability. Consider the following when choosing a provider:
- Geographic Proximity: Servers located closer to your users will generally result in faster resolution times.
- Anycast Routing: Anycast routing allows a single IP address to be advertised from multiple locations, enabling DNS queries to be routed to the nearest available server.
- Performance Benchmarks: Compare the performance of different providers using publicly available DNS performance tests.
- Implement DNS Caching: Caching DNS records at various levels can significantly reduce the number of DNS queries that need to be made.
- Browser Caching: Web browsers cache DNS records for a certain period (TTL – Time To Live). This can be configured by the DNS server.
- Operating System Caching: The operating system’s DNS resolver also caches records.
- Recursive DNS Servers: Recursive DNS servers (provided by ISPs or public DNS services like Google Public DNS or Cloudflare) cache DNS records to speed up resolution for their users.
The `TTL` value, configured in the DNS records, determines how long a DNS record is cached. A shorter TTL allows for faster propagation of DNS changes, but can also lead to more frequent queries. A longer TTL can improve performance by reducing the number of queries but delays the propagation of changes.
- Optimize DNS Records: Properly configuring DNS records can improve performance and resilience.
- Use DNS records like A, AAAA, and CNAME records effectively: Avoid unnecessary CNAME records that add extra lookups. Use A records for direct IP address mapping whenever possible.
- Implement DNSSEC: DNS Security Extensions (DNSSEC) adds a layer of security to DNS by verifying the authenticity and integrity of DNS data, preventing DNS spoofing attacks. While DNSSEC adds a small overhead to the resolution process, the security benefits often outweigh the performance impact.
- Use DNS Load Balancing: Distribute traffic across multiple servers using DNS-based load balancing, ensuring high availability and improved response times. This is particularly useful for applications that experience high traffic volumes.
- Monitor DNS Performance: Regularly monitor DNS performance to identify and address potential issues.
- Use DNS monitoring tools: Tools like Pingdom, Dyn (now Oracle Cloud DNS), and SolarWinds provide real-time monitoring of DNS resolution times, uptime, and other key metrics.
- Track DNS resolution times: Monitor the time it takes for DNS queries to be resolved from various geographic locations.
- Analyze DNS query patterns: Identify any unusual query patterns that might indicate a performance problem or a potential security threat.
Impact of DNS Latency on User Experience
DNS latency directly affects user experience. The longer the user waits for DNS resolution, the longer they perceive the application to be slow or unresponsive.
- Perceived Performance: Even a small delay in DNS resolution can significantly impact a user’s perception of an application’s speed. Users are more likely to abandon a website or application if it takes too long to load.
- Conversion Rates: Slow application loading times can negatively impact conversion rates. For e-commerce sites, for example, even a one-second delay in page load time can lead to a significant drop in sales.
- User Engagement: Slow DNS resolution can lead to decreased user engagement. Users may spend less time on the site or use the application less frequently if they experience frequent delays.
- Search Engine Ranking: Google and other search engines consider website speed as a ranking factor. Slow DNS resolution can negatively impact a website’s search engine ranking, leading to reduced organic traffic.
- Example: Consider an e-commerce website with a slow DNS provider. A user clicks on a product link, but the page takes several seconds to load due to slow DNS resolution. The user may become frustrated and leave the site before the page fully loads, resulting in a lost sale. In contrast, a website with a fast DNS provider would load the page quickly, providing a better user experience and increasing the likelihood of a purchase.
Wrap-Up
In conclusion, a well-defined DNS strategy is paramount for a successful cloud migration. From understanding the core components of DNS to implementing robust security measures and optimizing performance, each step plays a vital role in ensuring a smooth transition and sustained operational excellence. By adopting the best practices Artikeld in this guide, organizations can navigate the complexities of cloud DNS, enhance application responsiveness, and ultimately, achieve their cloud computing objectives.
The strategic deployment of DNS in the cloud not only facilitates migration but also underpins long-term scalability, security, and performance gains.
FAQ Overview
What is the primary advantage of using cloud-based DNS?
Cloud-based DNS offers superior scalability, performance, and reliability compared to traditional DNS, enabling faster resolution times and improved application availability, along with enhanced security features.
How does DNSSEC improve DNS security in the cloud?
DNSSEC (Domain Name System Security Extensions) adds a layer of cryptographic security to DNS, protecting against cache poisoning and man-in-the-middle attacks by verifying the authenticity and integrity of DNS records.
What are the key considerations when choosing a cloud DNS provider?
Key considerations include pricing, latency, features (e.g., traffic management, DDoS protection), scalability, geographical reach, and the provider’s support for specific cloud services and integrations.
What is split-horizon DNS, and why is it used in hybrid cloud environments?
Split-horizon DNS provides different DNS responses depending on the location of the request (e.g., internal vs. external networks), allowing for the secure and efficient management of resources in hybrid cloud setups.
How can I minimize downtime during a DNS migration?
Minimizing downtime involves careful planning, pre-migration testing, a phased rollout, reducing the TTL (Time to Live) values of your DNS records before the migration, and using a provider that supports features like DNS pre-warming and zero-downtime migrations.