Physical to Virtual (P2V) migration, a cornerstone of modern IT infrastructure, represents a fundamental shift from the tangible to the virtual. This process involves converting physical servers, storage devices, and other hardware components into virtual machines (VMs) running on a virtualized environment. The motivation behind this transition is multi-faceted, driven by the need for improved resource utilization, enhanced operational efficiency, and increased agility in responding to evolving business demands.
Understanding the intricacies of P2V migration is crucial for organizations aiming to optimize their IT landscape and leverage the benefits of virtualization.
P2V migration offers significant advantages over maintaining physical hardware. It allows for consolidation of servers, reducing physical space requirements and energy consumption. It facilitates easier disaster recovery and business continuity planning, as VMs can be quickly restored from backups. Furthermore, P2V migration enables improved scalability, allowing businesses to rapidly provision and deprovision resources as needed. This overview will delve into the methods, processes, tools, and considerations involved in successful P2V migration projects, equipping readers with the knowledge to navigate this critical technological transition.
Overview of Physical to Virtual (P2V) Migration
Physical to Virtual (P2V) migration is the process of converting a physical server, including its operating system, applications, and data, into a virtual machine (VM). This transformation allows the server’s workload to run on a virtualized infrastructure, such as a hypervisor. This shift decouples the server’s operating environment from the underlying hardware, offering significant advantages in terms of resource utilization, management, and business continuity.
Fundamental Concept of P2V Migration
P2V migration essentially creates a digital replica of a physical server. This replica, the VM, can then operate on a virtualized environment, utilizing the resources of the host server. The process involves capturing the entire state of the physical server, including the boot sector, operating system, applications, data, and configurations. This “image” is then translated into a format compatible with the hypervisor, enabling it to function as a self-contained VM.
This VM can then be deployed and managed on the virtualized infrastructure.
History of P2V Migration
The concept of P2V migration emerged alongside the advancements in virtualization technology. Initially, virtualization was primarily used for testing and development environments. However, as hypervisor technology matured, the ability to migrate physical servers to virtual environments became a practical and valuable solution.
- Early Days (Late 1990s – Early 2000s): Early virtualization solutions, such as VMware’s ESX (and later ESXi) and Microsoft’s Virtual PC, provided the foundation for P2V. The migration process was often complex and manual, involving backups, re-installations, and manual configuration.
- Mid-2000s: The introduction of specialized P2V migration tools, such as VMware Converter and PlateSpin Migrate, simplified the process. These tools automated many of the steps, reducing the complexity and downtime associated with migration. This period saw increased adoption of virtualization and, consequently, P2V migration.
- Late 2000s – Present: P2V migration has become a mature technology, integrated into virtualization platforms. Tools offer enhanced features, including support for a wider range of operating systems, hardware configurations, and migration scenarios (e.g., online migration with minimal downtime). Cloud providers and enterprise solutions have incorporated P2V migration capabilities into their offerings.
Core Benefits of P2V Migration for Businesses
P2V migration offers several key advantages for businesses seeking to optimize their IT infrastructure. These benefits often result in significant cost savings and improved operational efficiency.
- Reduced Hardware Costs: Consolidating physical servers into virtual machines allows for better utilization of hardware resources. A single physical server can host multiple VMs, reducing the need to purchase and maintain numerous physical servers. This translates to lower capital expenditure (CAPEX) and operational expenditure (OPEX) related to hardware, power consumption, and cooling.
- Improved Resource Utilization: Virtualization enables dynamic allocation of resources, such as CPU, memory, and storage, to VMs based on their needs. This ensures that resources are used efficiently, preventing underutilization and improving overall performance. For example, a server that previously ran at 10% CPU utilization can be consolidated with other workloads on a single physical server, increasing its utilization and reducing waste.
- Simplified Management and Administration: Virtualized environments are easier to manage and administer than physical infrastructures. VMs can be easily provisioned, moved, and backed up. Centralized management tools provide a single point of control for managing the entire virtualized environment. This simplifies tasks such as patching, updates, and disaster recovery.
- Enhanced Disaster Recovery and Business Continuity: P2V migration facilitates the creation of redundant VMs that can be quickly restored in case of a hardware failure or disaster. VMs can be easily replicated and moved to different physical servers or even cloud environments, ensuring business continuity. The ability to create and test disaster recovery plans is also significantly improved.
- Increased Agility and Scalability: Virtualized environments offer greater flexibility and scalability. VMs can be easily scaled up or down to meet changing business needs. New VMs can be provisioned quickly, and resources can be dynamically allocated. This allows businesses to respond rapidly to market demands and opportunities.
- Improved Energy Efficiency: By consolidating workloads onto fewer physical servers, P2V migration reduces energy consumption and the associated carbon footprint. This contributes to cost savings and promotes environmentally sustainable practices.
Methods and Approaches for P2V Migration
Physical-to-Virtual (P2V) migration encompasses a range of methodologies, each with distinct characteristics impacting complexity, efficiency, and resource utilization. Selecting the optimal approach requires careful consideration of the source system’s characteristics, the target virtual environment, and the specific business requirements. The core methods employed typically involve either a direct copy of the physical system or a process of creating an image that can then be deployed to the virtual environment.
Understanding these methodologies and their associated trade-offs is crucial for a successful P2V migration.
Cloning Methods
Cloning methods involve creating a direct replica of the physical server’s operating system, applications, and data. This process typically creates a one-to-one copy of the physical machine’s storage and configuration. The primary advantage of cloning is its ability to preserve the exact state of the physical server at the time of the migration, minimizing the risk of application incompatibility. However, this approach can be resource-intensive and may require significant downtime.The cloning process can utilize different technologies.
- Disk Imaging: Disk imaging involves creating a bit-by-bit copy of the physical disk to a virtual disk. The image captures the entire contents of the physical disk, including the operating system, applications, and data. This method offers a comprehensive approach, ensuring that all aspects of the physical server are replicated in the virtual environment.
- File-Level Cloning: File-level cloning involves copying individual files and directories from the physical server to the virtual environment. This approach can be more efficient than disk imaging, especially when migrating a large number of files. However, it requires careful planning to ensure that all necessary files are copied and that application dependencies are maintained.
Imaging Methods
Imaging methods involve capturing a snapshot of the physical server’s operating system, applications, and data, creating a single file or set of files that can be deployed to a virtual machine. This process typically involves the use of specialized software tools that can create a system image.Imaging methods include the following approaches:
- Snapshot-Based Imaging: This method takes a snapshot of the physical server’s storage volumes. It is often used for quick backups and restores. The snapshot is then used to create a virtual machine. This approach can be relatively fast, but the resulting virtual machine may not be fully consistent if the physical server is active during the snapshot.
- Block-Level Imaging: Block-level imaging captures the data at the block level, creating a more granular copy of the physical server’s data. This approach can be more efficient than disk imaging, especially when migrating a large amount of data. The resulting image can then be used to create a virtual machine.
- Agent-Based Imaging: Agent-based imaging involves installing an agent on the physical server. The agent is responsible for capturing the data and sending it to the virtual environment. This approach can provide greater control over the migration process, but it requires the installation of an agent on the physical server.
Comparison of P2V Migration Approaches
The complexity of P2V migration varies significantly depending on the chosen method. Direct cloning, while potentially simpler to implement, can lead to extended downtime and increased resource consumption. Imaging approaches, while offering greater flexibility, often require more planning and specialized tools.The following table presents a comparative overview of the different P2V migration methods, outlining their key features:
| Migration Method | Description | Pros | Cons |
|---|---|---|---|
| Disk Imaging | Creates a bit-by-bit copy of the physical disk. | Comprehensive; preserves the exact state of the physical server. | Can be time-consuming; high resource consumption. |
| File-Level Cloning | Copies individual files and directories. | Potentially faster than disk imaging for large file sets. | Requires careful planning; potential for application incompatibility. |
| Snapshot-Based Imaging | Takes a snapshot of storage volumes. | Relatively fast; suitable for quick backups. | May result in inconsistent virtual machines if the physical server is active. |
| Block-Level Imaging | Captures data at the block level. | Efficient for large datasets; more granular control. | Requires specialized tools; potentially complex to implement. |
| Agent-Based Imaging | Uses an agent to capture and transfer data. | Greater control over the migration process. | Requires agent installation on the physical server; can introduce performance overhead. |
Preparing for P2V Migration
P2V migration, while offering numerous benefits, demands meticulous preparation. A well-defined pre-migration phase is crucial for minimizing risks, ensuring a smooth transition, and maximizing the chances of a successful outcome. This stage involves a comprehensive assessment of the existing physical infrastructure, detailed planning, and thorough data validation. Neglecting these steps can lead to significant downtime, data loss, and unforeseen compatibility issues.
Essential Steps in Pre-Migration Planning
Pre-migration planning is a systematic process designed to identify potential challenges and define the scope of the migration. It encompasses several key activities that contribute to the overall success of the project.
- Define Migration Scope: Clearly delineate the systems to be migrated. Determine which servers, applications, and data sets are included. This involves identifying dependencies between systems to ensure that the migration order does not disrupt business operations. For example, a database server might need to be migrated before the application servers that rely on it.
- Assess Resource Requirements: Estimate the necessary virtual machine (VM) resources, including CPU, memory, storage, and network bandwidth, based on the workloads of the physical servers. Overestimating resource needs can lead to wasted resources, while underestimating can cause performance bottlenecks. Consider using performance monitoring tools to gather historical data on resource utilization.
- Choose a Migration Method: Select the appropriate P2V migration method based on the environment, the existing infrastructure, and the desired downtime. Options include live migration, offline migration, and hybrid approaches. Live migration minimizes downtime, while offline migration is often simpler for less complex environments.
- Select a Target Platform: Determine the virtualization platform to be used, such as VMware vSphere, Microsoft Hyper-V, or others. Ensure compatibility between the physical environment and the target platform, including operating systems, drivers, and application compatibility.
- Develop a Migration Schedule: Create a detailed timeline outlining the steps involved, the duration of each task, and the expected completion date. The schedule should incorporate contingency plans to address potential delays or issues. Consider the impact of the migration on business hours and plan for minimal disruption.
- Establish a Communication Plan: Communicate the migration plan to all stakeholders, including IT staff, end-users, and management. Clearly Artikel the expected downtime, the steps involved, and the roles and responsibilities of each party. Regularly update stakeholders on the progress of the migration.
Assessing the Existing Physical Environment
A thorough assessment of the physical environment is paramount to understanding the current state of the infrastructure and identifying potential challenges. This process involves gathering information about the hardware, software, and network configuration of each server.
- Hardware Inventory: Compile a detailed inventory of the physical servers, including their make, model, CPU, memory, storage, and network adapters. This information is crucial for determining the compatibility of the hardware with the target virtualization platform and for estimating the resources needed for the VMs.
- Software Inventory: Create a comprehensive list of the software installed on each server, including the operating system, applications, and drivers. Identify any compatibility issues with the target virtualization platform. For instance, older operating systems may require specific drivers or configurations.
- Network Configuration Analysis: Document the network configuration, including IP addresses, subnet masks, default gateways, DNS servers, and VLAN settings. This information is essential for configuring the virtual network and ensuring connectivity after the migration.
- Performance Monitoring: Analyze the performance metrics of the physical servers, such as CPU utilization, memory usage, disk I/O, and network traffic. This data provides insights into the resource requirements of the VMs and helps identify potential performance bottlenecks.
- Dependency Mapping: Map the dependencies between servers and applications. Identify which servers rely on other servers and applications to ensure the migration order does not disrupt business operations. For example, a web server might depend on a database server.
- Security Assessment: Evaluate the security posture of the physical environment, including firewalls, intrusion detection systems, and access controls. Ensure that the security configuration is replicated in the virtual environment to maintain a secure environment.
Data Backup and Validation Checklist
A comprehensive data backup and validation process is crucial for protecting against data loss during the P2V migration. This checklist provides a structured approach to ensure data integrity and minimize the risk of data corruption.
- Full Data Backup: Perform a full backup of all data on the physical servers. Store the backup in a secure location, preferably offsite. Consider using a backup solution that supports incremental backups to minimize the impact on production systems.
- Backup Verification: Verify the integrity of the backup by restoring a test copy of the data. This confirms that the backup is complete and that the data can be successfully restored. Regularly test the restore process to ensure its effectiveness.
- Data Consistency Check: Validate the consistency of the data on the physical servers. Use database tools and file system utilities to check for errors and inconsistencies. Address any issues before starting the migration.
- Application-Specific Backup: Back up application-specific data, such as databases, configuration files, and application settings. This ensures that the applications can be restored in the virtual environment.
- Operating System Backup: Back up the operating system and associated configurations. This is important for ensuring the operating system can be restored if the migration fails.
- Backup Documentation: Document the backup process, including the backup solution, the backup schedule, and the location of the backups. This documentation is essential for restoring the data if needed.
- Checksum Verification: Calculate and verify checksums for critical data files. This helps to detect any data corruption during the migration process. Compare checksums before and after the migration.
- Data Integrity Testing: Perform data integrity tests on critical applications after the migration to ensure that the data has been migrated correctly. This includes testing database queries, running reports, and verifying application functionality.
Organizing Pre-Migration Tasks in Logical Order
Organizing the pre-migration tasks in a logical order streamlines the process and minimizes the risk of errors. A well-defined sequence ensures that all necessary steps are completed before the actual migration begins.
- Environment Assessment: Conduct a comprehensive assessment of the physical environment, including hardware, software, network, and performance metrics.
- Migration Planning: Define the migration scope, choose the migration method, select the target platform, and develop a detailed migration schedule.
- Resource Preparation: Prepare the target virtual environment, including creating VMs, configuring storage, and setting up the network.
- Data Backup and Validation: Perform a full data backup, verify the backup integrity, and validate data consistency.
- Pilot Migration (Optional): Conduct a pilot migration of a non-production server to test the migration process and identify any potential issues.
- Documentation and Communication: Document all aspects of the migration plan and communicate the plan to all stakeholders.
- Final Preparations: Ensure all necessary prerequisites are met before starting the migration, including verifying network connectivity and ensuring sufficient resources.
The P2V Migration Process
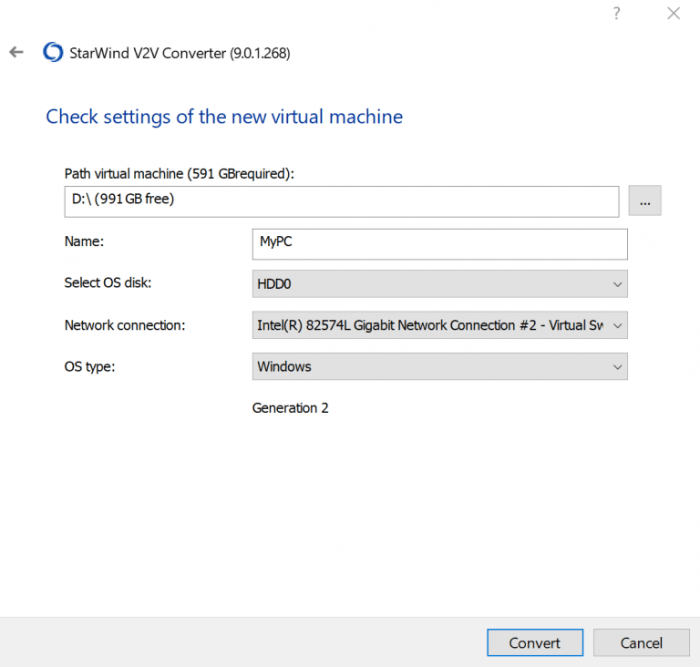
The successful migration from physical to virtual infrastructure hinges on a methodical, well-defined process. This process involves several key stages, from initial assessment and planning to the final verification and validation of the migrated virtual machines. Each step is crucial for minimizing downtime, ensuring data integrity, and maximizing the benefits of virtualization.
Step-by-Step Guide for Executing a P2V Migration
The P2V migration process is a multi-stage operation. Each stage requires meticulous planning and execution to ensure a smooth transition. The following steps Artikel a comprehensive guide for executing a P2V migration, emphasizing best practices and potential pitfalls.
- Assessment and Planning: This initial phase involves a thorough evaluation of the existing physical infrastructure. It’s critical to document the hardware specifications, operating systems, applications, and dependencies of each server. The network configuration, including IP addresses, DNS settings, and firewall rules, must also be meticulously documented. This assessment informs the selection of the appropriate P2V migration method and tools, and it defines the scope and timeline of the project.
- Tool Selection and Preparation: Based on the assessment, select the appropriate P2V migration tools. Common choices include VMware vCenter Converter, Microsoft System Center Virtual Machine Manager (SCVMM), and third-party solutions like Acronis Migrate Easy. Download and install the selected tools, ensuring they are compatible with the source and destination environments. Prepare the destination virtualization environment by configuring the virtual infrastructure, including the hypervisor, storage, and network settings.
- Agent Installation (if applicable): Some P2V migration tools require an agent to be installed on the physical server to facilitate the migration process. Install the agent on the physical server, following the tool’s specific instructions. The agent allows the tool to access the server’s data and perform the migration.
- Migration Execution: Initiate the P2V migration process using the selected tool. This typically involves specifying the source physical server, the destination virtual machine settings (e.g., CPU, memory, storage), and the network configuration. The tool then copies the necessary data from the physical server to the virtual machine. The migration can be performed online (with minimal downtime) or offline (requiring the server to be shut down during the migration).
- Post-Migration Configuration: After the migration is complete, configure the virtual machine to match the original physical server’s settings. This includes updating the IP address, hostname, and other network configurations, and installing any necessary drivers or software specific to the virtual environment.
- Testing and Verification: Thoroughly test the migrated virtual machine to ensure it functions correctly. Verify the applications, services, and data are accessible and working as expected. Conduct performance testing to ensure the virtual machine meets the required performance levels.
- Cutover and Production Deployment: Once the testing and verification are complete, plan the cutover to the production environment. This involves decommissioning the physical server and making the virtual machine the primary server. Schedule the cutover during a period of low activity to minimize disruption.
- Ongoing Management and Monitoring: After the migration, continuously monitor the virtual machine’s performance and availability. Implement a robust backup and disaster recovery plan to protect the virtual machine and its data. Regularly update the virtual machine’s operating system and applications to maintain security and stability.
Demonstration of Different Tools for the P2V Migration Process
Various tools are available to facilitate the P2V migration process. Each tool offers different features, functionalities, and complexities. The choice of tool depends on the specific requirements of the migration project. Here’s a demonstration of the use of common P2V migration tools.
- VMware vCenter Converter: VMware vCenter Converter is a free tool provided by VMware. It supports migrating both Windows and Linux physical servers to VMware virtual machines. The process involves installing the vCenter Converter client, specifying the source physical server, and configuring the destination virtual machine settings. The tool then copies the necessary data and converts the physical server into a virtual machine.
The user interface provides a progress bar and detailed logs.
- Microsoft System Center Virtual Machine Manager (SCVMM): SCVMM is a comprehensive management tool for Microsoft’s virtualization platform. It supports P2V migration of Windows servers. The process involves adding the physical server to SCVMM, creating a virtual machine template, and initiating the migration. SCVMM uses the Windows Volume Shadow Copy Service (VSS) to create a consistent copy of the physical server’s data. The user interface allows for monitoring the migration progress and managing the virtual machine.
- Acronis Migrate Easy: Acronis Migrate Easy is a commercial tool that provides P2V migration capabilities. It supports various operating systems and virtualization platforms. The process involves installing the Acronis software, selecting the source physical server, and specifying the destination virtual machine settings. Acronis offers features like disk cloning, system state transfer, and automated post-migration configuration. The tool provides a user-friendly interface and detailed reporting.
Explanation of the Process of Converting Physical Servers to Virtual Machines
Converting a physical server to a virtual machine involves several core processes, regardless of the specific tool used. The fundamental principle is to replicate the operating system, applications, data, and configuration of the physical server within a virtual environment.
- Image Creation: The migration process begins by creating an image of the physical server’s hard drive or partitions. This image contains all the data, including the operating system, applications, and user data. This image can be created using various methods, such as block-level cloning or file-based copying.
- Data Transfer: The image data is then transferred from the physical server to the destination virtual environment. This transfer can occur over the network or using removable storage media. The speed of the data transfer depends on the network bandwidth, the size of the data, and the migration tool’s efficiency.
- Virtual Machine Creation: A new virtual machine is created within the virtualization platform. The virtual machine’s hardware settings, such as CPU, memory, and storage, are configured to match the requirements of the physical server.
- Image Restoration: The image data is restored onto the virtual machine’s virtual hard drive. This process installs the operating system, applications, and data within the virtual environment.
- Configuration Adjustment: The virtual machine’s configuration is adjusted to ensure compatibility with the virtual environment. This includes installing the appropriate drivers for the virtual hardware and configuring the network settings.
- Boot and Verification: The virtual machine is then booted, and its functionality is verified. This includes testing the applications, services, and data to ensure they are working correctly.
Detailed Explanation of the Post-Migration Verification Procedures
Post-migration verification is a critical phase that ensures the successful transition of a physical server to a virtual machine. This phase involves a series of tests and checks to validate the integrity, functionality, and performance of the migrated virtual machine.
- Data Integrity Verification: The first step is to verify the integrity of the data. This involves comparing the data on the virtual machine with the data on the original physical server. This can be achieved by using checksums, hash values, or by manually comparing files and folders.
- Application Testing: Thoroughly test all applications installed on the virtual machine. Verify that the applications are launching correctly, that their functionality is working as expected, and that they can access the necessary data and resources. This testing should include functional testing, integration testing, and performance testing.
- Service Verification: Verify that all essential services are running correctly on the virtual machine. This includes services like DNS, DHCP, Active Directory, and database services. Check the service logs for any errors or warnings.
- Network Connectivity Testing: Test the virtual machine’s network connectivity. Verify that it can connect to the network, that it can access the internet, and that it can communicate with other servers and devices on the network. This can be achieved by using ping, traceroute, and other network diagnostic tools.
- Performance Testing: Conduct performance testing to assess the virtual machine’s performance. Monitor the CPU usage, memory usage, disk I/O, and network traffic to ensure that the virtual machine is meeting the required performance levels. Use performance monitoring tools to identify any bottlenecks or performance issues.
- Backup and Recovery Testing: Test the virtual machine’s backup and recovery procedures. Verify that the virtual machine can be backed up successfully and that it can be restored from a backup. This testing is essential for disaster recovery planning.
- Security Testing: Verify the security of the virtual machine. This includes checking the firewall settings, the antivirus software, and the security patches. Conduct vulnerability scans to identify any security vulnerabilities.
- User Acceptance Testing (UAT): Involve end-users in the testing process. Allow users to test the virtual machine and provide feedback on its functionality and usability. This helps to identify any issues that may not have been discovered during the initial testing phase.
Tools and Technologies for P2V Migration
P2V migration relies heavily on specialized tools and technologies that automate and streamline the complex process of transferring physical server workloads to virtual environments. These tools offer a range of functionalities, from initial assessment and planning to actual migration and post-migration validation. The choice of tool depends on factors such as the existing infrastructure, the target virtualization platform, the complexity of the workloads, and the desired level of automation.
Understanding the capabilities of these tools is crucial for a successful P2V migration.
Popular P2V Migration Tools
Several tools are widely used in P2V migrations, each offering a unique set of features and capabilities. These tools are typically categorized by their primary function, such as agent-based migration, agentless migration, or replication-based migration. The selection of the appropriate tool is influenced by the specific requirements of the migration project.
- VMware vCenter Converter: This tool is a free offering from VMware that allows the conversion of physical machines and third-party virtual machines to VMware virtual machines. It is a popular choice for its ease of use and broad compatibility.
- Microsoft System Center Virtual Machine Manager (SCVMM): SCVMM provides a comprehensive management solution for Microsoft’s virtualization platform, Hyper-V. It includes P2V migration capabilities, along with features for managing virtual machine lifecycles, resource allocation, and infrastructure monitoring.
- PlateSpin Migrate: Now part of Micro Focus, PlateSpin Migrate is a powerful migration tool that supports both P2V and V2V (Virtual to Virtual) migrations. It offers features like automated workload discovery, replication, and cutover, making it suitable for complex migration scenarios.
- Carbonite Migrate (formerly Double-Take Move): Carbonite Migrate offers real-time replication and migration capabilities. It minimizes downtime by continuously replicating data from the source server to the target environment, enabling a quick cutover.
- Parallels Virtuozzo Containers (formerly SWsoft): Parallels Virtuozzo Containers is designed for container-based virtualization. It provides a platform for consolidating and migrating applications and workloads into containers.
Functionalities of Each Tool and Their Capabilities
Each tool possesses specific functionalities designed to facilitate different aspects of the P2V migration process. These functionalities range from pre-migration assessments to post-migration validation, providing a comprehensive approach to workload conversion.
- VMware vCenter Converter: The primary function is to convert physical machines and third-party virtual machines into VMware virtual machines. Its capabilities include:
- Support for various operating systems, including Windows and Linux.
- Cloning of the physical machine’s disk and system state.
- Ability to convert running physical machines without requiring downtime.
- Conversion of third-party virtual machines (e.g., Hyper-V, Xen) to VMware format.
- Microsoft System Center Virtual Machine Manager (SCVMM): Provides a centralized management console for Hyper-V environments, with P2V migration capabilities:
- Automated discovery and assessment of physical servers.
- Agent-based and agentless migration options.
- Live migration of virtual machines.
- Integration with other System Center components for monitoring and management.
- PlateSpin Migrate: Offers comprehensive P2V and V2V migration capabilities:
- Automated workload discovery and assessment.
- Replication of data and system state.
- Support for a wide range of operating systems and virtualization platforms.
- Automated cutover and rollback capabilities.
- Network configuration during migration.
- Carbonite Migrate: Focuses on real-time replication and migration:
- Continuous replication of data from the source to the target.
- Minimized downtime during the cutover phase.
- Support for various operating systems and applications.
- Failover and failback capabilities.
- Parallels Virtuozzo Containers: Designed for container-based virtualization, enabling the migration of applications and workloads into containers:
- Container creation and management.
- Application packaging and migration into containers.
- Resource management and isolation within containers.
Comparison and Contrast of Migration Tools
The different P2V migration tools vary in their features, supported platforms, and overall complexity. Comparing these aspects allows for a more informed decision when selecting the appropriate tool for a particular migration project. A key consideration is the level of automation, the supported operating systems, and the target virtualization platform.
| Feature | VMware vCenter Converter | Microsoft SCVMM | PlateSpin Migrate | Carbonite Migrate | Parallels Virtuozzo Containers |
|---|---|---|---|---|---|
| Agent-Based Migration | Yes | Yes | Yes | Yes | No |
| Agentless Migration | Yes | Yes | Yes | No | Yes (container-based) |
| Replication | No | No | Yes | Yes (real-time) | No |
| Supported OS (Windows) | Yes | Yes | Yes | Yes | Yes |
| Supported OS (Linux) | Yes | Yes | Yes | Yes | Yes |
| Target Platform | VMware | Hyper-V | VMware, Hyper-V, others | Various | Containers |
| Cost | Free | Paid (part of System Center) | Paid | Paid | Paid |
Features of VMware vCenter Converter
VMware vCenter Converter offers a range of features that simplify the P2V migration process. These features contribute to its popularity as a free and easy-to-use tool.
- Support for various source types: The tool supports the conversion of physical machines, as well as third-party virtual machines, including those from Microsoft Hyper-V and Citrix XenServer. This versatility makes it suitable for diverse environments.
- Non-disruptive conversion: The tool can convert a running physical machine to a virtual machine without requiring downtime. This minimizes disruption to business operations during the migration process.
- Remote conversion: Allows the conversion of physical machines located remotely, enabling the migration of servers across different networks and geographical locations.
- Automated conversion process: Simplifies the conversion process by automating many of the manual steps involved. This reduces the potential for errors and streamlines the migration.
- Support for customization: Offers options to customize the virtual machine’s hardware configuration, such as the amount of RAM, CPU cores, and disk space, during the conversion process. This allows for optimization of the virtual machine’s performance.
- Wide compatibility: Supports a wide range of operating systems, including Windows and Linux distributions, making it adaptable to different server environments.
Challenges and Risks in P2V Migration
The transition from physical to virtual environments, while offering numerous benefits, presents a range of challenges and potential risks that must be carefully considered and proactively addressed. These issues can impact project timelines, budget, system performance, and data integrity. Understanding these challenges and risks is crucial for successful P2V migration and ensuring a stable and efficient virtualized infrastructure.
Compatibility Issues
One of the most significant challenges in P2V migration is ensuring compatibility between the physical hardware, the operating system, applications, and the virtualized environment. Incompatibilities can manifest in various forms, leading to system instability, performance degradation, and application malfunctions.
- Hardware Incompatibility: The physical hardware components, such as network interface cards (NICs), storage controllers, and other peripherals, must be compatible with the virtualization platform’s hypervisor. Some older or specialized hardware might not have drivers or support in the virtual environment. This can lead to significant performance bottlenecks or complete failure to boot the virtual machine. For instance, an older server with a proprietary RAID controller might not function correctly when migrated to a VMware environment if the appropriate drivers are unavailable.
- Operating System Compatibility: The operating system of the physical server must be supported by the chosen virtualization platform. Some older operating systems might not be fully compatible or may require specific configurations and patches to function correctly in a virtualized environment. Lack of support can expose the virtual machine to security vulnerabilities. For example, migrating a Windows Server 2003 instance to a modern hypervisor without proper preparation could result in significant security risks due to the lack of security updates.
- Application Compatibility: Applications running on the physical server need to be compatible with the virtualized environment. Some applications are tightly coupled with the physical hardware or require specific drivers that might not be available in the virtual environment. Compatibility issues can lead to application crashes, performance problems, or data corruption. For instance, a database application optimized for a specific physical server configuration might experience performance degradation or data integrity issues after migration.
- Driver Issues: Proper driver support is crucial for the functionality of virtual machines. Incorrect or missing drivers for virtual hardware can lead to performance problems or prevent the virtual machine from functioning. In some cases, incorrect driver installation can result in a blue screen of death (BSOD) or other system errors.
Performance Degradation
Performance degradation is a common risk associated with P2V migration. While virtualization can provide resource optimization, it can also introduce performance bottlenecks if not properly planned and executed.
- Resource Contention: Virtual machines share the physical server’s resources, including CPU, memory, storage, and network bandwidth. If the physical server is oversubscribed or if virtual machines are not properly configured, resource contention can lead to performance degradation for all virtual machines. For example, if multiple virtual machines are CPU-intensive, they might compete for CPU cycles, resulting in slower response times for each virtual machine.
- Storage I/O Bottlenecks: Storage I/O performance is a critical factor in virtual machine performance. If the storage subsystem is not properly configured or if the virtual machines generate a high volume of I/O operations, it can lead to significant performance bottlenecks. For example, if multiple virtual machines are accessing the same storage LUN simultaneously, the I/O performance can be significantly impacted, leading to slow application response times.
- Network Bandwidth Limitations: Network bandwidth can also become a bottleneck in a virtualized environment. If the physical server’s network interface card (NIC) is not fast enough to handle the network traffic generated by all virtual machines, it can lead to performance degradation. For example, if multiple virtual machines are transferring large files simultaneously, the network bandwidth can become saturated, leading to slow file transfer speeds.
- Hypervisor Overhead: The hypervisor itself consumes resources to manage the virtual machines. This overhead can impact the performance of the virtual machines. The extent of the overhead depends on the type of hypervisor, the number of virtual machines, and the workload of the virtual machines.
Data Loss and Corruption
Data loss and corruption are critical risks associated with P2V migration. These issues can result from various factors, including migration errors, storage failures, and application-related problems.
- Migration Errors: Errors during the P2V migration process can lead to data loss or corruption. This can be caused by various factors, such as incorrect configuration settings, network connectivity issues, or software bugs. For example, if a migration tool fails to copy all the data from the physical server to the virtual machine, it can lead to data loss.
- Storage Failures: Storage failures can lead to data loss or corruption. If the storage subsystem fails during or after the P2V migration process, it can result in the loss of all the data stored on the virtual machine. For example, if a hard drive fails on the physical server during the migration process, it can lead to data loss.
- Application-Related Problems: Applications can also contribute to data loss or corruption. If an application is not properly configured or if it has software bugs, it can lead to data corruption. For example, if a database application is not properly shut down before the migration process, it can lead to data corruption.
- Backup and Recovery Failures: If backups are not performed correctly or if the recovery process fails, it can lead to data loss. Proper backup and recovery procedures are essential to protect data in case of any failure.
Security Vulnerabilities
Virtualization introduces new security challenges that must be addressed to protect the virtualized environment.
- Hypervisor Vulnerabilities: The hypervisor itself can have vulnerabilities that can be exploited by attackers. These vulnerabilities can be used to gain access to the virtual machines or to compromise the entire virtualized environment. Regular patching and security updates are essential to mitigate these risks.
- Virtual Machine Security: Virtual machines are just like physical servers and are vulnerable to the same security threats, such as malware, viruses, and unauthorized access. Proper security measures, such as firewalls, intrusion detection systems, and anti-virus software, must be implemented to protect the virtual machines.
- Network Security: Virtual machines share the same network infrastructure as physical servers. This can increase the risk of network attacks. Proper network security measures, such as network segmentation, access control lists (ACLs), and intrusion detection systems (IDS), must be implemented to protect the virtualized environment.
- Data Security: Data stored on virtual machines must be protected from unauthorized access. Encryption, access control, and data loss prevention (DLP) measures must be implemented to protect sensitive data.
Downtime and Business Disruption
P2V migration can lead to downtime and business disruption if not properly planned and executed.
- Planned Downtime: The migration process itself requires downtime, as the physical server needs to be taken offline to be converted into a virtual machine. The duration of the downtime depends on the size of the server, the migration method used, and the complexity of the environment.
- Unplanned Downtime: Unexpected issues during the migration process can lead to unplanned downtime. These issues can be caused by various factors, such as hardware failures, software bugs, or human error.
- Application Downtime: Applications running on the physical server need to be taken offline during the migration process. This can lead to application downtime and business disruption.
- User Impact: Users may experience performance degradation or application unavailability during the migration process. Communication and proper planning are crucial to minimize user impact.
Mitigation Strategies
Effective strategies are essential to mitigate the challenges and risks associated with P2V migration.
- Thorough Planning and Assessment: A detailed plan should be created, including a comprehensive assessment of the existing physical environment, including hardware, operating systems, applications, and network configurations. This assessment should identify potential compatibility issues, performance bottlenecks, and security vulnerabilities.
- Pilot Migration: Perform a pilot migration of a test server or a non-critical application to identify and address any issues before migrating the entire environment. This allows for refining the migration process and reducing the risk of problems during the production migration.
- Choosing the Right Tools and Technologies: Select the appropriate P2V migration tools and technologies based on the specific requirements of the environment. Consider factors such as ease of use, compatibility, performance, and security features.
- Data Backup and Recovery: Implement a robust data backup and recovery strategy to protect data from loss or corruption. This should include regular backups, offsite storage, and a tested recovery plan.
- Testing and Validation: Thoroughly test and validate the virtual machines after the migration process to ensure they are functioning correctly. This should include testing application functionality, performance, and security.
- Performance Monitoring and Optimization: Implement performance monitoring tools to monitor the performance of the virtual machines and identify any bottlenecks. Optimize the virtual machines by adjusting resource allocation, storage configurations, and network settings.
- Security Hardening: Implement security best practices to protect the virtualized environment. This should include patching the hypervisor, implementing firewalls, intrusion detection systems, and anti-virus software, and configuring secure network settings.
- Communication and Training: Communicate with stakeholders and provide training to the IT staff on the new virtualized environment. This ensures that everyone is aware of the changes and can effectively manage and support the virtual machines.
Examples of Failures and How to Avoid Them
Learning from past failures is crucial for successful P2V migration projects.
- Example 1: A company attempted to migrate a large database server to a virtual environment without proper assessment of the storage subsystem. The migration resulted in significant performance degradation due to insufficient I/O throughput. Avoidance: A detailed assessment of the storage requirements of the database server should have been performed before the migration. Proper storage configuration, including the use of SSDs or other high-performance storage solutions, would have prevented the performance degradation.
- Example 2: A company migrated a physical server running an older operating system to a virtual environment without ensuring compatibility. The migration resulted in system instability and application crashes due to driver incompatibilities and lack of support. Avoidance: Before migration, compatibility testing should have been conducted to ensure that the operating system and applications were compatible with the virtual environment.
Upgrading the operating system or choosing a different virtualization platform with better support for the older OS would have been necessary.
- Example 3: A company performed a P2V migration without proper backup and recovery procedures. A storage failure occurred after the migration, resulting in the loss of all the data stored on the virtual machine. Avoidance: A comprehensive backup and recovery plan should have been implemented before the migration. Regular backups, offsite storage, and a tested recovery plan would have prevented the data loss.
- Example 4: A company migrated a physical server without adequately planning for network changes. The migration resulted in network connectivity issues and application downtime. Avoidance: A detailed network plan should have been created before the migration, including IP address assignments, DNS configuration, and firewall rules. Testing network connectivity before migrating the server would have prevented the network issues.
Post-Migration Activities and Optimization
The successful completion of a Physical-to-Virtual (P2V) migration marks a significant milestone, but it is not the endpoint. Post-migration activities are crucial for ensuring the virtualized environment operates efficiently, securely, and meets the business’s performance requirements. These activities encompass performance tuning, ongoing monitoring, and proactive management, all contributing to the long-term success and return on investment of the virtualization initiative.
Neglecting these steps can lead to performance bottlenecks, security vulnerabilities, and ultimately, a diminished user experience.
Performance Tuning and Optimization
Following the P2V migration, optimizing the performance of the virtual machines (VMs) is paramount. This involves analyzing resource utilization, identifying bottlenecks, and implementing adjustments to enhance efficiency. Several factors can influence VM performance, including CPU, memory, storage I/O, and network bandwidth. Careful consideration and strategic adjustments across these areas are essential.
The initial step involves conducting a comprehensive performance assessment.
This assessment should utilize monitoring tools to gather data on key performance indicators (KPIs) such as CPU utilization, memory consumption, disk I/O latency, and network throughput. The data collected provides a baseline for understanding the VM’s current performance profile and identifying areas that require optimization.
Once performance baselines are established, further analysis is necessary to pinpoint specific bottlenecks. For instance, if CPU utilization is consistently high, it may indicate a need to allocate more virtual CPUs (vCPUs) to the VM, or to optimize the applications running within the VM.
Similarly, high disk I/O latency could suggest that the VM is competing for storage resources, necessitating storage optimization.
Optimization often involves a combination of techniques. These may include right-sizing VMs (allocating appropriate resources based on workload demands), implementing storage optimization strategies (such as storage tiering or data deduplication), and optimizing network configurations (to ensure sufficient bandwidth and low latency).
The following table provides a detailed overview of optimization methods, structured in a responsive table format for improved readability across various devices.
The table includes the method, a brief description, and potential benefits.
| Optimization Method | Description | Potential Benefits |
|---|---|---|
| Right-Sizing VMs | Adjusting the allocation of virtual resources (CPU, memory, storage) to match the workload demands of the VM. This involves analyzing historical resource utilization and adjusting the VM’s configuration accordingly. | Improved resource utilization, reduced operational costs, and enhanced performance. For example, a VM consistently using only 20% of its allocated CPU resources can be reduced, freeing up resources for other VMs. |
| Storage Optimization | Implementing strategies to improve storage performance. This can include using faster storage tiers (e.g., SSDs), implementing data deduplication to reduce storage footprint, and optimizing storage I/O configurations. | Reduced latency, improved I/O throughput, and increased storage capacity. For example, migrating a database VM to an SSD-based storage tier can significantly improve query performance. |
| Network Optimization | Configuring network settings to ensure optimal network performance. This includes optimizing virtual network interface card (vNIC) settings, configuring network quality of service (QoS), and ensuring sufficient network bandwidth. | Reduced network latency, improved throughput, and enhanced application responsiveness. For instance, implementing QoS can prioritize network traffic for critical applications. |
| Application Optimization | Optimizing the applications running within the VMs to improve performance. This can involve tuning application settings, optimizing database queries, and upgrading application versions. | Improved application performance, reduced resource consumption, and enhanced user experience. For example, optimizing database queries can significantly reduce the time it takes to retrieve data. |
Importance of Ongoing Monitoring and Management
Continuous monitoring and proactive management are critical for maintaining a healthy and efficient virtualized environment post-migration. This involves the constant collection and analysis of performance data, the identification of potential issues before they escalate, and the implementation of preventative measures to maintain optimal performance and security.
Regular monitoring allows administrators to detect performance degradation, identify security threats, and ensure that the virtualized environment aligns with business requirements.
Monitoring tools provide real-time insights into the status of VMs, host servers, and the underlying infrastructure. These tools collect data on various metrics, including CPU utilization, memory usage, disk I/O, network traffic, and security events.
Effective monitoring involves establishing performance baselines, setting up alerts and notifications, and regularly reviewing performance reports. Performance baselines serve as a reference point for measuring changes over time, helping to identify trends and anomalies.
Alerts can be configured to notify administrators when specific thresholds are exceeded, such as high CPU utilization or excessive disk I/O latency.
Proactive management involves taking steps to address identified issues and prevent potential problems. This may include right-sizing VMs, optimizing storage configurations, patching security vulnerabilities, and adjusting network settings. Proactive management ensures that the virtualized environment remains stable, secure, and capable of meeting the evolving needs of the business.
Regular audits and reviews of the virtualized environment are essential. These audits should assess the performance, security, and compliance of the VMs and the underlying infrastructure. The findings of these audits should be used to inform ongoing optimization efforts and to ensure that the virtualized environment remains aligned with industry best practices and regulatory requirements.
Best Practices for Optimizing Virtual Machine Performance
Implementing best practices is key to maximizing the performance of virtual machines. These practices cover a range of areas, from resource allocation to storage configuration and application optimization. Adhering to these guidelines helps ensure that VMs operate efficiently and provide a positive user experience.
One of the foundational best practices is to properly size VMs. This involves carefully analyzing the resource requirements of each workload and allocating appropriate resources, such as vCPUs, memory, and storage.
Over-provisioning resources can lead to wasted capacity and increased costs, while under-provisioning can result in performance bottlenecks and application slowdowns.
Utilizing the correct storage configuration is another critical aspect of VM performance optimization. This involves selecting the appropriate storage tier based on the workload’s I/O requirements. For example, high-I/O workloads, such as databases, benefit significantly from faster storage tiers like SSDs.
Other storage considerations include using RAID configurations to protect data and optimize performance.
Optimizing the network configuration is crucial for ensuring efficient communication between VMs and other network resources. This involves configuring virtual network interface cards (vNICs) with appropriate settings, such as jumbo frames and VLANs. Network segmentation can improve security and reduce network congestion.
Regularly updating and patching the operating systems and applications within the VMs is essential for security and performance.
Security patches address vulnerabilities that can be exploited by attackers, while performance updates can improve application efficiency and reduce resource consumption.
Finally, implementing resource management techniques is critical. This includes using features like dynamic resource allocation, which automatically adjusts resource allocation based on workload demands. Using virtualization platform features such as Distributed Resource Scheduler (DRS) can automatically balance workloads across the available physical hosts.
Security Considerations in P2V Migration
Physical-to-Virtual (P2V) migration, while offering numerous benefits, introduces new security challenges and complexities. Successfully navigating these challenges requires a proactive and comprehensive approach to security planning, implementation, and ongoing management. Failure to adequately address security concerns can expose virtualized environments to vulnerabilities, potentially leading to data breaches, service disruptions, and reputational damage. This section explores the security implications of P2V migration, provides recommendations for securing virtualized environments, and emphasizes the importance of implementing security best practices throughout the migration lifecycle.
Security Implications of P2V Migration
P2V migration inherently alters the attack surface of an IT infrastructure. Moving from a physical to a virtual environment introduces several security implications that must be carefully considered.* Increased Attack Surface: Virtualization can expand the attack surface due to the consolidation of multiple workloads on a single physical host. A successful attack on the hypervisor or a compromised virtual machine (VM) can potentially impact multiple VMs.
Hypervisor Vulnerabilities
The hypervisor, the software layer that manages VMs, becomes a critical security component. Vulnerabilities in the hypervisor can be exploited to gain control over guest operating systems and access sensitive data. Examples of such vulnerabilities include flaws in the hypervisor’s memory management or networking stack.
VM Sprawl and Configuration Errors
Rapid VM deployment and a lack of proper management can lead to VM sprawl, where VMs are created without adequate security configurations. Misconfigured VMs, such as those with weak passwords, outdated software, or improperly configured network settings, become easy targets for attackers.
Network Segmentation Challenges
Virtual networks, while offering flexibility, can also complicate network segmentation. Without proper configuration, VMs on the same physical host may be able to communicate with each other without traversing traditional network security controls.
Data Security Concerns
Migrating data to a virtual environment necessitates secure storage and access controls. Inadequate data protection mechanisms can lead to data breaches, especially if the virtual environment is not properly secured.
Recommendations for Securing Virtualized Environments
Securing a virtualized environment requires a multi-layered approach that encompasses various aspects of security. Implementing the following recommendations is crucial for minimizing risks and protecting sensitive data.* Secure the Hypervisor: The hypervisor is the foundation of the virtualized environment. Securing it is paramount. This involves:
Regularly patching the hypervisor to address known vulnerabilities.
Configuring the hypervisor with strong passwords and access controls.
Implementing network segmentation to isolate the hypervisor from guest VMs.
Monitoring hypervisor logs for suspicious activity.
Harden Guest Operating Systems
Each guest operating system (OS) running on a VM must be hardened to minimize its attack surface. This includes:
Applying the latest security patches and updates.
Disabling unnecessary services and features.
Implementing strong password policies and access controls.
Regularly reviewing and updating security configurations.
Implement Network Segmentation
Network segmentation is crucial for isolating VMs and limiting the impact of a security breach.
Create separate virtual networks for different workloads and security zones.
Use firewalls to control traffic flow between virtual networks.
Implement intrusion detection and prevention systems (IDS/IPS) to monitor network traffic for malicious activity.
Secure Storage and Data Encryption
Protecting data at rest and in transit is essential.
Encrypt data stored on virtual disks.
Implement secure storage protocols, such as iSCSI or Fibre Channel, with appropriate access controls.
Regularly back up VMs and data to ensure business continuity.
Implement Strong Access Controls
Restricting access to VMs and virtual resources is critical for preventing unauthorized access.
Use multi-factor authentication (MFA) for all administrative accounts.
Implement role-based access control (RBAC) to grant users only the necessary permissions.
Regularly review and audit user access rights.
Monitor and Audit
Continuous monitoring and auditing are essential for detecting and responding to security incidents.
Implement security information and event management (SIEM) systems to collect and analyze security logs.
Regularly audit security configurations and access controls.
Establish incident response plans to address security breaches effectively.
Importance of Implementing Security Best Practices During and After Migration
Security is not a one-time task but an ongoing process that must be integrated throughout the entire P2V migration lifecycle. Implementing security best practices during and after the migration is critical for ensuring a secure and resilient virtualized environment.* Pre-Migration Security Assessment: Before starting the migration, conduct a thorough security assessment of the physical environment. This assessment should identify existing vulnerabilities, security gaps, and potential risks that need to be addressed during the migration process.
Secure Migration Process
The migration process itself should be secure. This includes:
Using secure migration tools and protocols.
Encrypting data during the migration process.
Verifying the integrity of migrated data.
Post-Migration Security Validation
After the migration, validate the security posture of the virtualized environment. This includes:
Testing the effectiveness of security controls.
Conducting vulnerability scans and penetration testing.
Reviewing security logs and audit trails.
Ongoing Security Management
Security is an ongoing process.
Regularly patch and update the hypervisor and guest operating systems.
Monitor the virtualized environment for suspicious activity.
Continuously review and improve security configurations.
Stay informed about the latest security threats and vulnerabilities.
Security Best Practices
- Patching and Updates: Regularly apply security patches and updates to the hypervisor, guest operating systems, and all associated software. This is a fundamental practice, as patching addresses known vulnerabilities that attackers can exploit.
- Strong Authentication: Implement strong authentication mechanisms, including multi-factor authentication (MFA), for all administrative and user accounts. MFA significantly reduces the risk of unauthorized access.
- Network Segmentation: Divide the virtual network into logical segments to isolate workloads and limit the impact of security breaches. Use firewalls and access control lists (ACLs) to control traffic flow between segments.
- Data Encryption: Encrypt data at rest and in transit to protect sensitive information from unauthorized access. Encryption prevents data breaches even if storage devices are compromised.
- Regular Backups and Disaster Recovery: Implement a robust backup and disaster recovery plan to ensure business continuity. Regular backups allow for data recovery in case of a security incident or system failure.
- Security Auditing and Monitoring: Implement continuous security monitoring and auditing to detect and respond to security threats. Use SIEM systems to collect and analyze security logs, and establish incident response plans to address security breaches effectively.
- Vulnerability Scanning and Penetration Testing: Conduct regular vulnerability scans and penetration testing to identify and address security weaknesses. These tests help proactively identify vulnerabilities before attackers can exploit them.
- Least Privilege Access: Grant users only the minimum necessary privileges to perform their tasks. This limits the potential damage that can be caused by a compromised account.
Use Cases and Real-World Examples of P2V Migration
P2V migration, when implemented strategically, provides tangible benefits across various industries. Analyzing real-world examples allows for a deeper understanding of how businesses leverage this technology to achieve their operational and strategic objectives. The following sections detail specific case studies and demonstrate the versatility and impact of P2V migration.
Successful P2V Migration Projects
Successful P2V migrations are characterized by careful planning, execution, and post-migration optimization. These projects often involve significant improvements in resource utilization, cost savings, and business agility. Several companies have demonstrated proficiency in P2V migration, achieving notable results.
- Example 1: Large Retail Chain. A major retail chain, facing escalating hardware costs and the need for improved disaster recovery capabilities, initiated a P2V migration project. The company migrated its physical servers, which supported point-of-sale (POS) systems, inventory management, and customer relationship management (CRM) applications, to a virtualized environment. This transition allowed the retail chain to consolidate its server infrastructure, reducing hardware footprint and associated energy consumption.
Furthermore, the virtualized environment facilitated the implementation of a robust disaster recovery plan, ensuring business continuity in the event of a system failure. The project resulted in a 30% reduction in server hardware costs and a 25% improvement in recovery time objective (RTO).
- Example 2: Financial Services Firm. A financial services firm, dealing with the complexities of regulatory compliance and the need for enhanced security, undertook a P2V migration. The firm virtualized its critical financial applications, including trading platforms and client data servers. This migration enhanced the firm’s ability to meet stringent compliance requirements by providing a more secure and easily auditable infrastructure. The virtualized environment also simplified the process of implementing security patches and updates, mitigating potential vulnerabilities.
The firm experienced a 40% reduction in IT administration overhead and a significant improvement in its ability to meet regulatory deadlines.
- Example 3: Healthcare Provider. A healthcare provider, seeking to improve patient care and streamline IT operations, migrated its physical servers to a virtualized infrastructure. The migration included servers supporting electronic health records (EHR) systems, medical imaging applications, and patient portals. This allowed the healthcare provider to centralize its IT resources, improve data accessibility, and enhance the scalability of its systems. The project resulted in improved system performance, reduced downtime, and enhanced data security, ultimately leading to better patient care and operational efficiency.
Specifically, the provider noted a 20% reduction in system downtime and a 15% improvement in application response times.
Benefits of P2V Migration in Different Industries
P2V migration offers tailored benefits across various sectors, addressing unique challenges and opportunities. These benefits are often categorized as cost reduction, improved operational efficiency, enhanced business continuity, and increased agility. The applicability of these benefits varies depending on the industry’s specific needs and priorities.
- Manufacturing: P2V migration can improve the efficiency of manufacturing operations by virtualizing servers that support production planning, supply chain management, and inventory control. This leads to reduced downtime, optimized resource allocation, and improved responsiveness to market demands. For instance, a manufacturing company could reduce its server infrastructure costs by 20% and improve its production uptime by 15%.
- Healthcare: Healthcare providers benefit from P2V migration through improved data security, enhanced system availability, and streamlined IT management. Virtualizing servers that host electronic health records (EHRs), medical imaging applications, and patient portals facilitates better patient care, reduces operational costs, and ensures regulatory compliance. A healthcare provider can achieve a 25% reduction in IT operational costs and improve data security compliance.
- Education: Educational institutions can leverage P2V migration to optimize IT resources, improve application performance, and reduce operational costs. Virtualizing servers that support student information systems, learning management systems, and research applications enhances the educational experience and improves administrative efficiency. An educational institution can expect a 15% reduction in IT infrastructure costs and improved application performance.
- Financial Services: Financial institutions benefit from P2V migration through enhanced security, improved compliance, and streamlined IT operations. Virtualizing servers that support trading platforms, client data servers, and financial applications enhances data security, improves regulatory compliance, and reduces operational costs. A financial services firm can achieve a 30% reduction in IT administration overhead and improved compliance.
- Retail: Retail businesses can improve efficiency and reduce costs by virtualizing servers that support point-of-sale (POS) systems, inventory management, and customer relationship management (CRM) applications. This improves operational efficiency, reduces hardware footprint, and enhances disaster recovery capabilities. A retail chain can achieve a 20% reduction in server hardware costs and improved business continuity.
Descriptive Information for a P2V Migration Scenario
Consider a mid-sized e-commerce company, “OnlineSales Inc.”, experiencing rapid growth. Its physical server infrastructure, supporting its website, database, and order processing applications, is struggling to keep up with increasing traffic and transaction volumes. The company faces frequent system outages during peak hours, resulting in lost sales and customer dissatisfaction. Additionally, the existing infrastructure is complex and difficult to manage, leading to high IT administration costs.The company decides to implement a P2V migration strategy to address these challenges.
The migration process involves the following steps:
- Assessment and Planning: OnlineSales Inc. begins by assessing its current physical server infrastructure, identifying the servers to be migrated, and determining the compatibility of the existing applications with the virtualized environment. This phase includes a detailed inventory of hardware, software, and network configurations.
- Selection of Virtualization Platform: The company selects a virtualization platform, such as VMware vSphere or Microsoft Hyper-V, based on its requirements and budget. This selection involves considering factors such as scalability, performance, and management capabilities.
- Server Migration: The physical servers are migrated to virtual machines (VMs) on the chosen virtualization platform. This process involves creating virtual machine images of the physical servers and transferring the data and applications. The migration is performed in a phased approach to minimize disruption to the e-commerce operations.
- Testing and Validation: After the migration, the virtual machines are thoroughly tested to ensure that all applications and services function correctly. This includes testing for performance, security, and disaster recovery capabilities.
- Post-Migration Optimization: OnlineSales Inc. optimizes the virtualized environment by fine-tuning resource allocation, implementing performance monitoring, and establishing backup and disaster recovery procedures. This includes monitoring resource utilization, identifying bottlenecks, and adjusting resource allocation to optimize performance.
The illustration would depict the transformation of the company’s IT infrastructure. The initial state shows a series of physical servers, each dedicated to a specific function (web server, database server, application server, etc.), connected to a network switch and storage devices. The next stage, the migration process, is illustrated through arrows and diagrams. This phase shows the physical servers being replicated or “cloned” into virtual machines.
These virtual machines are then hosted on a virtualized environment. The final state depicts a consolidated environment with virtual machines running on a smaller number of physical servers, utilizing shared resources, and a centralized management console. The illustration includes visual representations of the reduction in hardware footprint, improved resource utilization, and the implementation of a robust disaster recovery plan, demonstrating the benefits of P2V migration.
The visual representation underscores the shift from a hardware-centric to a software-defined infrastructure, highlighting the agility and scalability gained through virtualization.
Final Thoughts
In conclusion, P2V migration is more than just a technical procedure; it is a strategic initiative that empowers organizations to transform their IT infrastructure. By understanding the core concepts, methodologies, and potential challenges, businesses can successfully migrate their physical assets to virtual environments. The careful planning, execution, and ongoing optimization discussed throughout this guide are key to realizing the full potential of virtualization, fostering greater efficiency, resilience, and adaptability.
Embracing P2V migration represents a pivotal step towards a more flexible, cost-effective, and future-proof IT ecosystem.
Clarifying Questions
What are the primary benefits of P2V migration?
The primary benefits include reduced hardware costs, improved resource utilization, enhanced disaster recovery capabilities, increased agility, and simplified management.
What are the common methods used for P2V migration?
Common methods include cloning, imaging, and using specialized P2V migration tools that automate the conversion process.
What are the key considerations during pre-migration planning?
Key considerations include assessing the existing physical environment, backing up data, validating data integrity, and planning for post-migration activities.
What are the potential risks associated with P2V migration?
Potential risks include data loss, application compatibility issues, performance degradation, and downtime during the migration process.