Understanding what is the role of a cloud solution architect in migration is critical for any organization contemplating a move to the cloud. This pivotal role orchestrates the complex transition of on-premise infrastructure and applications to a cloud environment. The cloud solution architect acts as the strategic visionary, translating business needs into a robust, secure, and cost-effective cloud solution. Their expertise encompasses a broad spectrum of activities, from initial assessment and planning to post-migration optimization, ensuring a smooth and successful cloud journey.
The cloud solution architect’s responsibilities are multifaceted, spanning technical design, strategic planning, and stakeholder management. They are the bridge between business requirements and technological capabilities, guiding the migration process from conception to completion. Their proficiency in cloud technologies, architectural patterns, and security best practices is essential for navigating the complexities of cloud migration and maximizing the benefits of cloud adoption.
This includes understanding various migration strategies, designing the target cloud environment, overseeing implementation, and optimizing the environment post-migration.
Understanding the Cloud Solution Architect’s Role in Migration
The Cloud Solution Architect (CSA) plays a pivotal role in cloud migration projects, acting as a strategic advisor and technical leader. Their expertise is crucial for ensuring a successful transition, optimizing cloud infrastructure, and aligning the migration with business objectives. They bridge the gap between business requirements and technical implementation, guiding the entire process from planning to execution.
Core Responsibilities of a Cloud Solution Architect During Migration
The CSA’s responsibilities are multifaceted and span the entire migration lifecycle. These responsibilities are essential for ensuring the successful and efficient transition of an organization’s IT infrastructure to the cloud.
- Assessment and Planning: The CSA conducts a thorough assessment of the existing IT environment, including applications, infrastructure, and data. This involves identifying dependencies, potential risks, and compatibility issues. They then develop a comprehensive migration plan, outlining the scope, timeline, and resources required. This plan also includes choosing the appropriate migration strategy (rehost, replatform, refactor, repurchase, retire).
- Solution Design: The CSA designs the cloud solution architecture, selecting the appropriate cloud services and configurations based on the assessment findings and business requirements. This includes defining the network architecture, security protocols, storage solutions, and compute resources. They also create detailed diagrams and documentation to communicate the proposed solution.
- Technical Leadership and Guidance: The CSA provides technical leadership and guidance to the migration team, ensuring that the implementation aligns with the architectural design and best practices. They also assist with troubleshooting technical challenges and resolving conflicts. They are the primary point of contact for technical decisions.
- Cost Optimization: The CSA is responsible for optimizing cloud costs by selecting cost-effective cloud services, implementing resource utilization strategies, and monitoring cloud spending. They provide recommendations for right-sizing resources and utilizing reserved instances or savings plans. They also monitor the performance of the migrated applications and make adjustments to ensure optimal performance and cost efficiency.
- Security and Compliance: The CSA ensures that the cloud solution adheres to security best practices and compliance requirements. This includes implementing security controls, configuring access management, and establishing monitoring and auditing mechanisms. They are responsible for ensuring that the migrated environment meets the organization’s security and compliance standards.
- Governance and Monitoring: The CSA establishes governance policies and procedures for the cloud environment, ensuring that the solution is managed effectively and efficiently. This includes setting up monitoring and alerting systems to track the performance and availability of the migrated applications. They also create reports on cloud utilization and performance.
Contribution to Overall Migration Strategy
The CSA’s contributions are critical to the overall success of the migration strategy. Their strategic input and technical expertise ensure that the migration aligns with the business goals and delivers the desired outcomes.
- Alignment with Business Objectives: The CSA ensures that the migration strategy aligns with the organization’s business objectives. They understand the business requirements and translate them into technical solutions. They collaborate with stakeholders to define the desired outcomes of the migration.
- Risk Mitigation: The CSA identifies and mitigates potential risks associated with the migration. They develop contingency plans to address potential issues and ensure business continuity. They assess the potential impact of the migration on the business.
- Technology Selection: The CSA selects the appropriate cloud technologies and services based on the organization’s needs and requirements. They evaluate different cloud providers and services to determine the best fit. They provide recommendations on the optimal cloud infrastructure for the organization.
- Scalability and Performance Optimization: The CSA designs the cloud solution to ensure scalability and performance optimization. They consider the organization’s future growth and ensure that the cloud infrastructure can handle the increased workload. They design for high availability and disaster recovery.
- Cost Management and Optimization: The CSA focuses on cost management and optimization throughout the migration process. They identify opportunities to reduce cloud spending and optimize resource utilization. They develop strategies to minimize cloud costs.
Differences Between the Cloud Solution Architect’s Role and Other Roles
While the CSA collaborates with other roles in the migration process, their responsibilities and focus differ significantly. Understanding these differences is crucial for a well-coordinated and successful migration.
- Cloud Solution Architect vs. Migration Engineer: The CSA focuses on the overall design and strategy of the migration, while the migration engineer is responsible for the technical implementation. The CSA provides the blueprints, and the migration engineer executes them. The CSA focuses on the “what” and “why,” while the migration engineer focuses on the “how.” The migration engineer often handles the hands-on tasks like data migration, application deployment, and configuration.
- Cloud Solution Architect vs. Project Manager: The CSA focuses on the technical aspects of the migration, while the project manager focuses on the project management aspects. The project manager manages the timeline, budget, and resources, while the CSA focuses on the technical design and implementation. The project manager ensures the project stays on track, and the CSA ensures the technical solution is sound. The CSA works closely with the project manager to ensure that the technical aspects are aligned with the project plan.
- Cloud Solution Architect vs. Security Engineer: The CSA integrates security considerations into the overall architecture, while the security engineer specializes in implementing and maintaining security controls. The CSA ensures that security is considered in the design, while the security engineer implements the specific security measures. The security engineer focuses on the details of security implementation, such as firewalls, intrusion detection systems, and access controls.
- Cloud Solution Architect vs. Cloud Operations Engineer: The CSA focuses on the initial design and migration, while the cloud operations engineer focuses on the ongoing management and maintenance of the cloud environment. The CSA creates the initial cloud infrastructure, and the cloud operations engineer monitors and manages it. The cloud operations engineer ensures that the cloud environment is running smoothly and efficiently after the migration is complete.
Pre-Migration Assessment and Planning
The pre-migration assessment and planning phase is a critical stage in cloud migration projects. This phase involves a comprehensive evaluation of the existing on-premises infrastructure, applications, and business requirements to formulate a well-defined migration strategy. The Cloud Solution Architect (CSA) plays a pivotal role in this phase, guiding the process, ensuring a smooth transition, and maximizing the benefits of cloud adoption.
This proactive approach minimizes risks, optimizes resource utilization, and aligns the migration with the organization’s strategic goals.
Key Activities of a Cloud Solution Architect in Pre-Migration Assessment
The CSA’s responsibilities during the pre-migration assessment phase are multifaceted, encompassing technical, business, and strategic considerations. These activities collectively contribute to the development of a robust migration plan.
- Discovery and Information Gathering: The CSA begins by gathering comprehensive information about the client’s existing IT environment. This includes documenting hardware specifications, software versions, network configurations, security protocols, and application dependencies. This information is crucial for understanding the current state and identifying potential challenges.
- Application Portfolio Analysis: The CSA analyzes the client’s application portfolio, assessing each application’s suitability for cloud migration. This involves evaluating factors such as application architecture, complexity, criticality, and interdependencies. The analysis helps determine the most appropriate migration strategy for each application.
- Dependency Mapping: Understanding the dependencies between applications and infrastructure components is essential. The CSA maps these dependencies to identify potential risks and ensure that applications function correctly after migration. This mapping also helps in determining the order of migration.
- Cost Analysis and Optimization: The CSA conducts a cost analysis to estimate the total cost of ownership (TCO) of the existing on-premises infrastructure and compares it with the projected costs of the cloud environment. This analysis includes infrastructure costs, operational expenses, and potential cost savings. The CSA also identifies opportunities for cost optimization in the cloud.
- Security and Compliance Assessment: Security and compliance are paramount concerns during cloud migration. The CSA assesses the client’s current security posture and compliance requirements. This assessment helps in identifying potential security gaps and ensuring that the migrated environment meets the necessary compliance standards.
- Risk Assessment and Mitigation Planning: The CSA identifies potential risks associated with the migration process, such as data loss, downtime, and performance degradation. They develop mitigation strategies to minimize these risks. This includes creating a rollback plan in case of unforeseen issues.
- Migration Strategy Selection: Based on the assessment findings, the CSA selects the most appropriate migration strategy for each application. This strategy considers factors such as application complexity, business requirements, and cost considerations.
- Migration Plan Development: The CSA develops a detailed migration plan that Artikels the scope, timeline, resources, and budget for the migration project. This plan serves as a roadmap for the migration process.
Checklist of Questions for Assessing Client Infrastructure
A structured approach to assessing the client’s infrastructure is crucial for a successful migration. The following checklist provides a framework for the CSA to gather the necessary information and gain a comprehensive understanding of the client’s environment.
- Infrastructure:
- What is the current hardware infrastructure (servers, storage, network devices)?
- What are the specifications of each server (CPU, RAM, storage)?
- What is the network topology and bandwidth capacity?
- What is the current utilization of resources (CPU, memory, storage, network)?
- What is the disaster recovery and business continuity plan?
- Applications:
- What applications are currently running?
- What are the application dependencies and interrelationships?
- What are the application performance requirements (response time, throughput)?
- What is the application architecture (monolithic, microservices, etc.)?
- What are the application licensing requirements?
- Data:
- What databases are used?
- What is the volume of data stored?
- What are the data backup and recovery procedures?
- What are the data security and compliance requirements?
- What is the data retention policy?
- Security:
- What security measures are in place (firewalls, intrusion detection systems, etc.)?
- What are the authentication and authorization mechanisms?
- What are the compliance requirements (e.g., GDPR, HIPAA, PCI DSS)?
- What is the current vulnerability management program?
- What is the incident response plan?
- Business:
- What are the business objectives for cloud migration?
- What are the performance and scalability requirements?
- What is the budget for cloud migration?
- What is the timeline for cloud migration?
- What is the organizational structure and skill sets?
Migration Strategy Comparison Table (Example for AWS)
Different migration strategies offer varying benefits and drawbacks. The following table provides a comparative analysis of common migration strategies within the context of Amazon Web Services (AWS).
| Migration Strategy | Description | Benefits | Drawbacks | AWS Services (Examples) | Use Cases |
|---|---|---|---|---|---|
| Rehost (Lift and Shift) | Moving applications and infrastructure to the cloud without significant changes. | Fastest migration, minimizes initial investment, reduces risk. | Limited cloud optimization, potential for higher costs if not optimized, may not leverage cloud-native features. | EC2, EBS, VPC | Migrating virtual machines, legacy applications with minimal modifications. |
| Replatform (Lift, Tinker, and Shift) | Moving applications to the cloud with some optimizations, such as database migration. | Improved performance and scalability, moderate effort, cost savings. | Requires some application modification, potential for downtime. | EC2, RDS, Elastic Load Balancing | Migrating databases to managed services, optimizing application performance. |
| Refactor (Re-architect) | Re-architecting applications to leverage cloud-native features and services. | Significant performance and scalability improvements, cost optimization, full cloud benefits. | Most complex and time-consuming, requires significant investment, higher risk. | Lambda, ECS, EKS, DynamoDB | Building new applications, migrating complex applications to microservices. |
| Repurchase (Drop and Shop) | Replacing existing applications with cloud-native software-as-a-service (SaaS) solutions. | Reduced operational overhead, cost savings, rapid deployment. | Loss of control, potential vendor lock-in, limited customization. | Salesforce, ServiceNow, Microsoft 365 | Migrating CRM, ITSM, or productivity suites. |
| Retire | Eliminating unused or outdated applications. | Cost savings, reduced complexity, improved efficiency. | Requires careful analysis to identify candidates, potential for data loss if not handled properly. | N/A | Identifying and removing unused applications. |
Developing the Migration Strategy
The development of a robust migration strategy is a critical phase in any cloud adoption journey. A Cloud Solution Architect (CSA) leverages their expertise to analyze the existing environment, understand business requirements, and define a roadmap that minimizes risk, optimizes costs, and ensures a successful transition to the cloud. This involves a systematic approach that considers various factors and employs appropriate tools and techniques.
Determining the Best Migration Approach
The CSA’s role in determining the optimal migration approach is multifaceted and data-driven. It begins with a comprehensive assessment of the existing IT landscape, including applications, infrastructure, and data. This assessment informs the selection of a migration strategy tailored to the specific workload. The CSA evaluates several key aspects, including application dependencies, performance requirements, security considerations, and the organization’s tolerance for downtime.
For instance, a mission-critical application might necessitate a strategy that minimizes downtime, such as a “rehost” or “replatform” approach. Conversely, a less critical application could be migrated using a “lift and shift” strategy to expedite the process. The selection process also incorporates an understanding of the cloud provider’s services and capabilities, aligning the migration strategy with the available tools and resources to achieve the desired outcomes efficiently.
Factors Influencing the Choice of Migration Strategy
Several factors significantly influence the choice of a migration strategy, each contributing to the overall complexity and success of the cloud migration. Understanding these factors is crucial for the CSA in formulating a strategy that aligns with the organization’s goals and constraints.* Cost: Cloud migration costs are a primary consideration. The CSA evaluates the costs associated with each migration approach, including infrastructure costs, data transfer charges, and the resources required for the migration process.
Strategies like “rehosting” can be cost-effective in the short term, while “rearchitecting” might involve higher initial costs but offer long-term cost savings through optimized resource utilization and scalability.* Time: The time required to complete the migration is another critical factor. The CSA considers the project timeline, including the duration of the assessment, planning, execution, and validation phases.
Strategies like “lift and shift” are typically faster, while “rearchitecting” can be more time-consuming due to the need for application modifications. The chosen strategy should align with the organization’s desired timeframe for cloud adoption.* Complexity: The complexity of the migration process is directly related to the nature of the applications and infrastructure being migrated. Complex applications with numerous dependencies and integrations require a more intricate migration strategy.
The CSA assesses the application architecture, data volume, and network configuration to determine the appropriate level of complexity for the migration.* Business Impact: The potential impact of the migration on the business operations is a crucial factor. The CSA assesses the risk of downtime, data loss, and performance degradation. Strategies that minimize disruption to business operations, such as “replatforming” or “rearchitecting,” might be preferred for mission-critical applications.
The chosen strategy should align with the organization’s business continuity requirements.* Skillset and Resources: The availability of in-house expertise and the resources required for the migration process influence the choice of strategy. The CSA assesses the organization’s existing skillset and identifies any gaps that need to be addressed. Strategies that require specialized skills, such as “rearchitecting,” might necessitate training or the involvement of external consultants.* Security and Compliance: Security and compliance requirements are critical considerations.
The CSA ensures that the migration strategy aligns with the organization’s security policies and regulatory obligations. The strategy should address data security, access control, and compliance with relevant industry standards.
Tools and Technologies for Migration
Cloud Solution Architects utilize a wide array of tools and technologies to facilitate the migration process. These tools are categorized by function, allowing the CSA to effectively manage different aspects of the migration, from initial assessment to post-migration validation.* Assessment Tools: These tools are used to analyze the existing on-premises environment and identify workloads suitable for migration.
Cloud Assessment Tools
These tools, offered by cloud providers like AWS (Migration Evaluator), Azure (Azure Migrate), and Google Cloud (Assessment and Planning), provide detailed insights into the existing infrastructure, application dependencies, and performance characteristics. They generate reports that help in planning the migration strategy.
Third-Party Assessment Tools
Tools like Cloudamize and Movere offer comprehensive assessment capabilities, providing detailed information about the IT environment, including hardware and software inventories, application dependencies, and cost estimations. These tools assist in identifying the optimal migration strategy and estimating the total cost of ownership (TCO) in the cloud.* Data Transfer Tools: These tools facilitate the transfer of data from the on-premises environment to the cloud.
Cloud Provider Data Transfer Services
AWS offers AWS Snowball and Snowmobile for large-scale data transfers. Azure provides Azure Data Box, and Google Cloud has Transfer Appliance. These services physically transport large datasets to the cloud, bypassing network limitations.
Network-Based Data Transfer Tools
Tools like AWS DataSync, Azure Data Box, and Google Cloud Storage Transfer Service facilitate data transfer over the network. They offer features like incremental data transfer, data compression, and encryption.
Third-Party Data Transfer Tools
Tools such as Veeam and Carbonite offer data migration and backup solutions that can be used to transfer data to the cloud.* Application Compatibility Tools: These tools assist in assessing and remediating application compatibility issues during migration.
Cloud Provider Compatibility Tools
AWS offers the AWS Application Migration Service, which automates the migration of applications. Azure provides the Azure Migrate service, which assesses application compatibility and recommends migration strategies. Google Cloud offers the Migrate to Virtual Machines service.
Third-Party Compatibility Tools
Tools like CloudEndure and VMware HCX provide application compatibility assessments and migration capabilities, including automated workload migration and replication.* Migration Orchestration and Automation Tools: These tools automate various aspects of the migration process, including server provisioning, application deployment, and data synchronization.
Cloud Provider Automation Tools
AWS CloudFormation, Azure Resource Manager, and Google Cloud Deployment Manager allow for infrastructure-as-code (IaC) deployments. These tools automate the creation and configuration of cloud resources.
Third-Party Automation Tools
Tools like Terraform and Ansible provide infrastructure automation capabilities, allowing for the automated provisioning and configuration of cloud resources across multiple cloud providers.* Monitoring and Management Tools: These tools provide ongoing monitoring and management of the migrated workloads.
Cloud Provider Monitoring Tools
AWS CloudWatch, Azure Monitor, and Google Cloud Monitoring provide comprehensive monitoring and logging capabilities. These tools enable real-time monitoring of application performance, resource utilization, and security events.
Third-Party Monitoring Tools
Tools like Datadog, New Relic, and Dynatrace provide advanced monitoring and analytics capabilities, offering insights into application performance and infrastructure health.
Designing the Target Cloud Environment
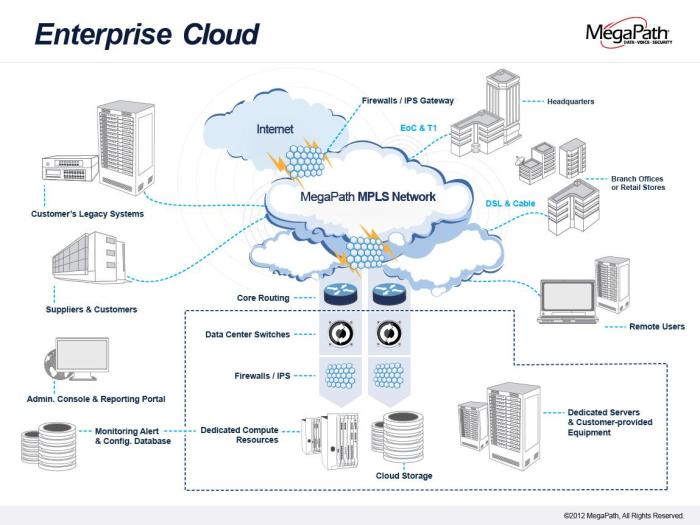
The Cloud Solution Architect (CSA) plays a pivotal role in designing the target cloud environment, a critical phase in any cloud migration strategy. This involves translating the pre-migration assessment findings and migration strategy into a concrete, operational blueprint for the cloud infrastructure. The design phase focuses on creating a secure, scalable, and cost-optimized environment that aligns with the business objectives and technical requirements of the migrated applications and data.
Security Considerations in Cloud Environment Design
Security is paramount in cloud environment design, requiring a layered approach that encompasses various aspects.
- Identity and Access Management (IAM): Implementing robust IAM controls is crucial. This involves defining roles and permissions based on the principle of least privilege, using multi-factor authentication (MFA), and regularly reviewing access rights. IAM services, such as AWS IAM, Azure Active Directory, or Google Cloud IAM, provide the necessary tools. For example, a financial institution migrating its core banking system would meticulously define roles like “Database Administrator,” “Application Developer,” and “Security Auditor,” each with precisely defined access to resources.
- Network Security: This encompasses securing network traffic both within the cloud environment and between the cloud and on-premises resources. This involves using virtual private clouds (VPCs), network firewalls, intrusion detection and prevention systems (IDS/IPS), and secure network protocols. For instance, a retail company migrating its e-commerce platform would segment its network into public and private subnets, utilizing a web application firewall (WAF) to protect against common web vulnerabilities.
- Data Encryption: Data encryption is vital, both in transit and at rest. This involves encrypting data stored in databases, object storage, and other storage services. Data in transit is secured using HTTPS, TLS/SSL protocols. Key management services (KMS) are used to manage encryption keys securely. A healthcare provider migrating patient data to the cloud would implement end-to-end encryption, ensuring data confidentiality and compliance with regulations like HIPAA.
- Compliance and Governance: Ensuring compliance with industry regulations and internal security policies is a critical security consideration. This includes using cloud services that meet specific compliance standards (e.g., PCI DSS, GDPR, ISO 27001) and implementing governance frameworks to enforce security policies. Using cloud-native security tools and services for monitoring and auditing is essential.
Scalability Considerations in Cloud Environment Design
Designing for scalability is crucial to ensure the cloud environment can handle fluctuating workloads and meet growing business demands.
- Horizontal Scaling: This involves adding more instances of compute resources (e.g., virtual machines, containers) to handle increased traffic. Cloud platforms offer auto-scaling capabilities that automatically adjust the number of instances based on predefined metrics (e.g., CPU utilization, network traffic). An e-commerce website during a holiday sales period would automatically scale up its web servers and application servers to accommodate the surge in customer traffic.
- Vertical Scaling: This involves increasing the resources allocated to individual instances (e.g., increasing CPU, memory, or storage). Vertical scaling is often used for database servers or other resources that require more processing power.
- Load Balancing: Distributing traffic across multiple instances of an application or service is critical for ensuring high availability and performance. Load balancers distribute incoming traffic across healthy instances, and automatically reroute traffic away from failing instances. A video streaming service would use load balancers to distribute user requests across multiple content delivery network (CDN) servers, ensuring smooth streaming for all users.
- Database Scaling: Databases often require specific scaling strategies. This includes techniques like read replicas, sharding, and database clustering to handle increased read and write loads. A social media platform would use database sharding to distribute data across multiple database instances, improving performance and scalability.
- Stateless vs. Stateful Applications: Designing applications to be stateless is a key consideration for scalability. Stateless applications do not store any client-specific data on the server, making them easier to scale horizontally. Stateful applications, which store client-specific data on the server, require more complex scaling strategies, such as session affinity or shared storage.
Cost Optimization Considerations in Cloud Environment Design
Optimizing costs is a crucial aspect of cloud environment design, as cloud services are billed based on usage.
- Right-Sizing Resources: Choosing the appropriate size of compute instances, storage, and other resources based on actual needs. This prevents over-provisioning and reduces unnecessary costs. Analyzing historical usage data to identify optimal resource sizes is critical.
- Reserved Instances/Committed Use Discounts: Utilizing reserved instances or committed use discounts offered by cloud providers can significantly reduce compute costs for predictable workloads. This involves committing to using a specific amount of compute resources for a defined period.
- Spot Instances/Preemptible VMs: Leveraging spot instances or preemptible VMs (where available) can reduce compute costs for fault-tolerant and non-critical workloads. These instances offer significant discounts compared to on-demand instances, but can be terminated by the cloud provider if the spot price exceeds the user’s bid.
- Storage Tiering: Using different storage tiers (e.g., hot, cold, archive) based on data access frequency. Data that is frequently accessed should be stored in hot storage, while infrequently accessed data can be moved to cheaper cold or archive storage tiers.
- Automation and Infrastructure as Code (IaC): Automating infrastructure provisioning and management using IaC tools can streamline operations, reduce manual effort, and improve cost efficiency. IaC allows for the consistent and repeatable deployment of infrastructure resources.
- Monitoring and Cost Management Tools: Implementing robust monitoring and cost management tools to track resource usage, identify cost optimization opportunities, and set up budgets and alerts. Cloud providers offer native tools for cost management.
Architectural Patterns for Cloud Migrations
Several architectural patterns are commonly employed during cloud migrations, each with its own strengths and weaknesses.
- Rehosting (Lift and Shift): This involves migrating applications to the cloud with minimal changes to the existing architecture. This is often the fastest and simplest approach, suitable for applications that are not heavily dependent on on-premises infrastructure. The primary advantage is speed, while the disadvantage is that it may not fully leverage cloud-native features.
- Replatforming (Lift, Tinker, and Shift): This involves making some modifications to the application to take advantage of cloud-native features, such as managed databases or object storage. This is a more involved approach than rehosting, but it can improve performance and reduce operational overhead.
- Refactoring (Re-architect): This involves redesigning and rewriting the application to take full advantage of cloud-native services and architectures, such as serverless computing, microservices, and containerization. This is the most complex and time-consuming approach, but it can result in significant improvements in scalability, performance, and cost efficiency.
- Repurchasing (Replace): This involves replacing the existing application with a cloud-native software-as-a-service (SaaS) solution. This is a quick and cost-effective approach, but it may not be suitable for all applications or business requirements.
- Retiring: This involves decommissioning applications that are no longer needed or relevant. This can be a cost-saving measure and can simplify the overall IT environment.
Diagram of a Multi-Tier Application Migrated to the Cloud
Below is a detailed description of a diagram illustrating a multi-tier application migrated to the cloud.The diagram depicts a typical three-tier web application (web tier, application tier, and database tier) migrated to a cloud environment, using AWS as the example. The architecture is designed for scalability, high availability, and security.
Overall Structure: The diagram shows a clear separation of concerns across the three tiers. Arrows indicate the flow of traffic and data between components.
Web Tier: The web tier is responsible for handling user requests and presenting the user interface.
- Load Balancer: A highly available Elastic Load Balancer (ELB) sits in front of the web servers, distributing incoming traffic across multiple instances. The ELB ensures high availability by automatically routing traffic away from unhealthy instances.
- Auto Scaling Group (ASG): The web servers are managed by an Auto Scaling Group (ASG), which automatically scales the number of web server instances based on demand (e.g., CPU utilization, network traffic). This ensures the application can handle fluctuations in user traffic.
- Web Server Instances: Multiple EC2 instances (virtual machines) running the web server software (e.g., Apache, Nginx) and serving the application’s web pages. These instances are deployed across multiple Availability Zones (AZs) within a region to ensure high availability.
Application Tier: The application tier contains the business logic and application code.
- Auto Scaling Group (ASG): Similar to the web tier, the application servers are also managed by an Auto Scaling Group (ASG), which scales the number of instances based on demand.
- Application Server Instances: Multiple EC2 instances running the application server software (e.g., Tomcat, JBoss) and executing the application’s business logic. These instances are also deployed across multiple Availability Zones (AZs) for high availability.
- Security Group: Security groups are used to control inbound and outbound traffic to the application servers, allowing only authorized traffic to access the application.
Database Tier: The database tier stores and manages the application’s data.
- Managed Database Service (e.g., RDS): The diagram utilizes a managed database service, such as Amazon RDS (Relational Database Service), which simplifies database management tasks like patching, backups, and scaling. The specific database engine (e.g., MySQL, PostgreSQL, Oracle) is selected based on the application’s requirements.
- Multi-AZ Deployment: The database is deployed in a multi-AZ configuration to ensure high availability. This means that the database has a primary instance and a standby replica in different Availability Zones. If the primary instance fails, the standby replica automatically takes over, minimizing downtime.
- Security Group: A security group is used to restrict access to the database to only the application servers.
Other Components:
- Virtual Private Cloud (VPC): The entire architecture is deployed within a VPC, providing a logically isolated network environment. The VPC allows for the creation of subnets, security groups, and other network resources.
- Object Storage (e.g., S3): Object storage (e.g., Amazon S3) is used for storing static content, such as images, videos, and documents. This offloads storage from the web servers and provides scalability and durability.
- Content Delivery Network (CDN): A CDN (e.g., Amazon CloudFront) is used to cache static content closer to users, improving website performance and reducing latency.
- Monitoring and Logging: Monitoring and logging services (e.g., Amazon CloudWatch) are used to monitor the performance and health of the application and infrastructure, enabling proactive issue detection and resolution.
Security Considerations:
- Network Security: The architecture employs security groups to control traffic flow between different components.
- Data Encryption: Data in transit is secured using HTTPS/TLS, and data at rest is encrypted using encryption options provided by the cloud services (e.g., RDS encryption, S3 encryption).
- IAM: IAM roles are used to grant permissions to different components and users, ensuring the principle of least privilege.
Cost Optimization:
- Right-Sizing: The use of Auto Scaling Groups allows for automatic scaling of resources based on demand, optimizing resource utilization and cost.
- Reserved Instances/Savings Plans: Reserved instances or savings plans can be used to reduce the cost of compute resources.
- Storage Tiering: S3 provides different storage tiers (e.g., Standard, Intelligent-Tiering, Glacier) to optimize storage costs based on data access frequency.
Implementation and Execution
The Implementation and Execution phase marks the transition from planning to the actual migration of workloads to the cloud. This stage is critical, as it directly impacts the success of the migration and the realization of the anticipated benefits. The Cloud Solution Architect (CSA) plays a central role during this phase, ensuring the migration strategy is executed effectively, efficiently, and with minimal disruption to business operations.
Their responsibilities encompass oversight, coordination, and proactive problem-solving to navigate the complexities inherent in migrating to a cloud environment.
Oversight of the Migration Process
The CSA’s primary responsibility during implementation is to oversee the entire migration process, acting as a central point of contact and ensuring all activities align with the pre-defined strategy. This involves several key aspects.
- Monitoring Progress: Continuously monitoring the migration progress against the established timelines and milestones is crucial. This includes tracking the migration of individual applications, data sets, and infrastructure components. The CSA utilizes dashboards and reporting tools to visualize the progress and identify potential bottlenecks or delays. An example is the use of project management software, such as Jira or Azure DevOps, to track tasks, dependencies, and resource allocation.
- Resource Management: The CSA ensures the appropriate resources, including personnel, tools, and budget, are available to support the migration activities. This involves coordinating with different teams, such as the application development team, the infrastructure team, and the security team, to ensure everyone is aligned and working towards the same goals. This includes making sure all necessary licenses are acquired.
- Quality Assurance: Implementing and overseeing quality assurance measures to ensure the migrated workloads function as expected in the cloud environment is critical. This includes performing thorough testing, such as functional testing, performance testing, and security testing, to validate the migrated applications. The CSA collaborates with the quality assurance team to define test cases, interpret test results, and address any issues identified during testing.
- Risk Management: Proactively identifying and mitigating risks associated with the migration process is essential. The CSA utilizes risk assessment methodologies to identify potential issues, such as data loss, downtime, or security vulnerabilities. Based on the risk assessment, the CSA develops mitigation plans, such as data backup strategies, failover mechanisms, and security protocols, to minimize the impact of any potential disruptions.
Communication and Collaboration
Effective communication and collaboration are paramount to a successful migration. The CSA facilitates communication between various stakeholders and ensures everyone is informed about the migration progress, any issues, and the required actions.
- Stakeholder Communication: The CSA regularly communicates with stakeholders, including business leaders, IT managers, and application owners, to provide updates on the migration progress, highlight any risks or challenges, and seek feedback. This involves creating regular reports, holding status meetings, and using communication channels, such as email, instant messaging, and project management platforms.
- Team Coordination: The CSA facilitates communication and collaboration among the different teams involved in the migration process, such as the application development team, the infrastructure team, and the security team. This includes organizing regular meetings, establishing clear communication channels, and defining roles and responsibilities for each team member.
- Issue Resolution: The CSA acts as a central point of contact for resolving issues that arise during the migration process. This involves troubleshooting technical problems, coordinating with different teams to find solutions, and escalating issues to the appropriate level of management if necessary. The CSA also documents the issues and their resolutions to prevent similar issues from recurring in the future.
- Change Management: Implementing and managing changes to the migration plan is necessary as new information emerges or unexpected challenges arise. The CSA manages changes by documenting the changes, assessing their impact, and communicating them to the stakeholders. This includes implementing a change management process to ensure changes are properly authorized, tested, and implemented.
Common Challenges and Mitigation Strategies
The implementation phase can present various challenges. The CSA anticipates these and develops mitigation strategies.
- Downtime: Minimizing downtime during the migration is a critical concern. The CSA employs several strategies to mitigate downtime risks.
- Phased Migration: Implementing a phased migration approach, where workloads are migrated in stages, allows for minimizing the impact on business operations. For example, migrating non-critical applications first, and then gradually migrating critical applications.
- Data Replication: Implementing data replication mechanisms to ensure data is continuously synchronized between the on-premises environment and the cloud environment. This allows for a quick failover to the cloud in case of an outage.
- Testing and Validation: Performing thorough testing and validation of the migrated applications to ensure they function correctly in the cloud environment.
- Data Loss: Preventing data loss during the migration is a top priority.
- Data Backup and Recovery: Implementing robust data backup and recovery strategies to ensure data can be restored in case of any data loss. This includes backing up data before the migration, during the migration, and after the migration.
- Data Integrity Checks: Performing data integrity checks to ensure the data is accurately migrated to the cloud environment. This includes verifying the data size, checksums, and other data attributes.
- Data Encryption: Encrypting data at rest and in transit to protect data from unauthorized access.
- Security Vulnerabilities: Addressing security vulnerabilities is crucial to protect the migrated workloads from threats.
- Security Assessment: Conducting security assessments to identify and address any security vulnerabilities in the cloud environment.
- Security Best Practices: Implementing security best practices, such as multi-factor authentication, intrusion detection systems, and security information and event management (SIEM) tools.
- Compliance: Ensuring compliance with relevant security regulations and standards, such as HIPAA, PCI DSS, and GDPR.
- Cost Overruns: Controlling costs during the migration is essential to ensure the project stays within budget.
- Cost Optimization: Implementing cost optimization strategies, such as right-sizing instances, using reserved instances, and leveraging cost management tools.
- Monitoring and Reporting: Continuously monitoring cloud spending and generating reports to track cost trends.
- Budget Management: Establishing a clear budget and monitoring spending against the budget to ensure the project stays within financial constraints.
Post-Migration Optimization and Management
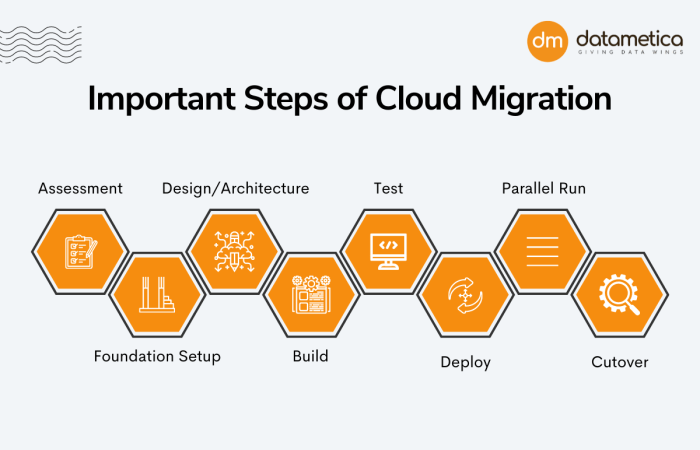
The cloud solution architect’s involvement doesn’t cease with the successful migration of workloads. Post-migration optimization and management are crucial phases for ensuring the migrated environment functions optimally, efficiently, and securely. This involves continuous monitoring, performance tuning, cost management, and security enhancements to maximize the benefits of the cloud infrastructure.
Cloud Solution Architect’s Responsibilities After Migration Completion
The Cloud Solution Architect (CSA) plays a critical role in post-migration activities. These responsibilities are ongoing and require a proactive approach to ensure the cloud environment meets business objectives.
- Performance Monitoring and Tuning: Continuously monitor the performance of migrated applications and infrastructure components. This includes identifying performance bottlenecks, optimizing resource allocation, and implementing scaling strategies to handle fluctuating workloads. The CSA uses performance monitoring tools and analyzes metrics such as CPU utilization, memory usage, network latency, and database query times.
- Cost Optimization: Regularly analyze cloud spending and identify opportunities to reduce costs. This involves right-sizing instances, leveraging reserved instances or savings plans, deleting unused resources, and optimizing storage configurations. The CSA works with finance teams to develop cost models and forecasts.
- Security Management and Compliance: Ensure the ongoing security of the cloud environment. This includes implementing security best practices, monitoring for threats, and ensuring compliance with relevant regulations. The CSA configures security tools, manages access controls, and conducts regular security audits.
- Resource Management: Oversee the allocation and utilization of cloud resources. This includes managing instance sizes, storage volumes, and network configurations. The CSA uses automation tools to provision and de-provision resources as needed.
- Disaster Recovery and Business Continuity: Maintain and test disaster recovery plans to ensure business continuity. This involves configuring backup and recovery mechanisms, testing failover procedures, and ensuring data replication. The CSA designs and implements disaster recovery strategies that align with business requirements.
- Documentation and Knowledge Transfer: Maintain comprehensive documentation of the cloud environment, including architecture diagrams, configuration details, and operational procedures. The CSA provides knowledge transfer to the operations team to ensure they can effectively manage the cloud environment.
- Continuous Improvement: Identify opportunities for continuous improvement in the cloud environment. This involves evaluating new cloud services, implementing new technologies, and refining existing processes. The CSA stays abreast of industry best practices and cloud innovations.
Step-by-Step Procedure for Optimizing the Migrated Environment
Optimizing a migrated environment for performance and cost efficiency is an iterative process that requires a systematic approach. The following steps Artikel a practical procedure.
- Establish Baseline Performance Metrics: Before optimization, establish baseline performance metrics for all critical applications and infrastructure components. This involves collecting data on CPU utilization, memory usage, disk I/O, network latency, and database query times. This baseline will serve as a reference point for measuring the impact of optimization efforts.
- Implement Performance Monitoring: Deploy comprehensive performance monitoring tools to continuously track key performance indicators (KPIs). These tools should provide real-time insights into the performance of applications and infrastructure. Configure alerts to notify administrators of performance degradation or resource exhaustion.
- Analyze Performance Bottlenecks: Regularly analyze performance data to identify bottlenecks. This may involve using profiling tools to pinpoint slow-running code, analyzing database query performance, or examining network latency. Address bottlenecks by optimizing code, scaling resources, or reconfiguring infrastructure components.
- Right-Size Resources: Evaluate the current resource allocation for each instance and service. Identify instances that are over-provisioned and right-size them to match actual workload demands. This can lead to significant cost savings without impacting performance.
- Implement Auto-Scaling: Configure auto-scaling rules to automatically adjust the number of instances based on demand. This ensures that applications can handle fluctuating workloads without manual intervention. Auto-scaling can help to optimize both performance and cost.
- Optimize Storage Configurations: Choose the appropriate storage types for each workload. Consider using tiered storage solutions to balance performance and cost. Regularly review storage usage and delete unused data.
- Optimize Database Performance: Fine-tune database configurations to improve query performance. This may involve optimizing database indexes, caching frequently accessed data, and optimizing database queries. Consider using database-specific optimization tools.
- Implement Cost Monitoring: Implement cost monitoring tools to track cloud spending. Set up alerts to notify administrators of unexpected cost increases. Analyze cost reports to identify areas where costs can be reduced.
- Leverage Reserved Instances and Savings Plans: Explore the use of reserved instances or savings plans to reduce cloud costs. These options provide discounts on compute resources in exchange for a commitment to use those resources for a specific period.
- Automate Optimization Tasks: Automate routine optimization tasks, such as right-sizing instances and deleting unused resources. Use scripting and automation tools to streamline the optimization process.
Performance and Cost Metrics Comparison: On-Premise vs. Cloud
The following table provides a comparative analysis of performance and cost metrics between an on-premise environment and a migrated cloud environment, using hypothetical sample data. The values presented are illustrative and can vary significantly based on specific workloads and cloud provider selections.
| Metric | On-Premise Environment | Cloud Environment (Post-Migration) | Units | Notes |
|---|---|---|---|---|
| Average CPU Utilization | 60 | 45 | % | Indicates improved resource efficiency in the cloud. |
| Average Memory Utilization | 75 | 60 | % | Lower memory usage in the cloud environment, due to right-sizing. |
| Network Latency (Application) | 150 | 80 | ms | Reduced latency due to optimized network configurations in the cloud. |
| Database Query Time | 800 | 450 | ms | Faster query performance due to database optimization in the cloud. |
| Monthly Compute Cost | $10,000 | $7,500 | USD | Cost savings achieved through right-sizing and resource optimization. |
| Monthly Storage Cost | $2,000 | $1,800 | USD | Lower storage costs due to optimized storage configurations. |
| Downtime per Year | 48 | 8 | Hours | Reduced downtime due to improved infrastructure reliability and disaster recovery in the cloud. |
| Number of IT Staff Required | 5 | 3 | FTE | Reduced operational overhead due to cloud management tools and automation. |
Security Considerations in Cloud Migration
Cloud migration presents a significant opportunity to enhance an organization’s security posture, but it also introduces new security challenges. A Cloud Solution Architect (CSA) plays a critical role in navigating these complexities, ensuring data protection, compliance, and business continuity throughout the migration lifecycle. This involves proactively identifying and mitigating risks associated with data movement, access control, and the target cloud environment’s security configurations.
Identifying Security Considerations for Cloud Migration
A thorough understanding of security considerations is paramount for a successful cloud migration. The CSA must address several key areas to maintain a robust security posture.
- Data Security: Protecting data at rest, in transit, and in use is a fundamental requirement. This involves implementing encryption, data loss prevention (DLP) mechanisms, and robust key management practices. The CSA must assess the sensitivity of the data being migrated and select appropriate security controls based on the data classification.
- Identity and Access Management (IAM): Securely managing user identities and controlling access to cloud resources is crucial. The CSA needs to define and implement IAM policies that adhere to the principle of least privilege, granting users only the necessary permissions to perform their tasks. This includes implementing multi-factor authentication (MFA) and regularly reviewing access rights.
- Network Security: Protecting the network perimeter and securing communication between cloud resources and on-premises systems is essential. The CSA must design and implement network security controls such as firewalls, intrusion detection and prevention systems (IDS/IPS), and virtual private networks (VPNs).
- Compliance and Governance: Ensuring compliance with relevant industry regulations and internal security policies is a critical aspect of cloud migration. The CSA must understand the compliance requirements applicable to the organization and implement security controls to meet those requirements. This may involve utilizing cloud-specific compliance tools and services.
- Vulnerability Management: Regularly identifying and addressing vulnerabilities in cloud resources is crucial for preventing security breaches. The CSA should implement vulnerability scanning and patching processes to proactively identify and remediate security weaknesses.
- Incident Response: Having a well-defined incident response plan is essential for effectively handling security incidents. The CSA must work with the security team to develop and implement an incident response plan that Artikels the steps to be taken in the event of a security breach.
- Cost Optimization: Security should be implemented without excessive costs. The CSA needs to balance security requirements with cost considerations, selecting cost-effective security solutions.
Implementing Security Best Practices in the Target Cloud Environment
Implementing security best practices in the target cloud environment is essential for a secure and successful cloud migration. This involves configuring various security controls and leveraging cloud-native security services.
- Encryption: Implementing encryption for data at rest and in transit is a fundamental security practice. This can be achieved using cloud-native encryption services or third-party solutions. For example, AWS provides services like KMS (Key Management Service) for managing encryption keys, and Azure offers Azure Key Vault.
- IAM Best Practices: Following IAM best practices, such as the principle of least privilege, is crucial. This involves granting users only the necessary permissions to perform their tasks. Regularly reviewing and auditing access rights is also essential.
- Network Segmentation: Segmenting the cloud network into different zones based on functionality and security requirements can help limit the impact of a security breach. This can be achieved using virtual networks and security groups.
- Web Application Firewall (WAF): Protecting web applications from common web attacks, such as SQL injection and cross-site scripting, is critical. Implementing a WAF can help mitigate these threats. Cloud providers like AWS and Azure offer WAF services.
- Security Information and Event Management (SIEM): Integrating a SIEM solution to collect, analyze, and correlate security logs from various sources can help detect and respond to security incidents. Cloud providers often integrate with or offer SIEM solutions.
- Regular Security Assessments: Conducting regular security assessments, such as penetration testing and vulnerability scanning, is essential for identifying and addressing security weaknesses. These assessments should be performed throughout the migration process and after migration is complete.
- Data Loss Prevention (DLP): Implementing DLP measures to prevent sensitive data from leaving the cloud environment or being accessed by unauthorized users. This can include data classification, monitoring, and access control policies.
Visual Representation of Security Considerations in the Migration Process
A flowchart illustrating the security considerations at each stage of the migration process can provide a clear understanding of the CSA’s role in ensuring security.The flowchart starts with the
- Pre-Migration Assessment and Planning* phase. Here, the CSA
- identifies data sensitivity and compliance requirements*. This feeds into the
- Developing the Migration Strategy* phase, where the CSA
- defines security policies and selects security tools*. Next, in the
- Designing the Target Cloud Environment* phase, the CSA
- configures network security, IAM policies, and encryption*. The
- Implementation and Execution* phase sees the CSA
- implementing security controls and testing security configurations*. Finally, in the
- Post-Migration Optimization and Management* phase, the CSA
- monitors security posture, performs regular security assessments, and implements incident response*. This is an ongoing process, with feedback loops to continuously improve security. The key security areas – data security, IAM, network security, compliance, vulnerability management, incident response, and cost optimization – are considered at each stage, influencing the decisions and actions taken.
Cost Management in Cloud Migration
The Cloud Solution Architect (CSA) plays a critical role in managing the financial aspects of cloud migration, ensuring cost-effectiveness and maximizing the return on investment (ROI). This involves a multifaceted approach, from initial cost estimation and strategy development to ongoing optimization and governance. Effective cost management is essential for preventing unexpected expenses and realizing the full benefits of cloud adoption.
Estimating Total Cost of Ownership (TCO)
Accurate TCO estimation is fundamental to a successful cloud migration. It provides a comprehensive view of all costs associated with IT infrastructure and services, both before and after the migration. This allows for informed decision-making and the identification of potential cost savings.The process involves evaluating several key areas:
- Pre-Migration Costs: These costs include the current on-premises infrastructure expenses.
- Migration Costs: These are expenses directly related to the migration process.
- Post-Migration Costs: These represent the ongoing costs of operating in the cloud environment.
To calculate TCO, the CSA must consider both direct and indirect costs:
- Direct Costs: These are easily quantifiable and include hardware, software licenses, data center space, power, and IT staff salaries.
- Indirect Costs: These are less tangible but still contribute to the overall cost. Examples include downtime, security breaches, and the opportunity cost of IT staff time.
The CSA employs various tools and methodologies for TCO estimation:
- Assessment Tools: These tools, often provided by cloud vendors or third-party providers, analyze existing infrastructure to estimate cloud resource requirements and associated costs.
- Cost Modeling: Cost models predict the ongoing cloud costs based on factors such as compute, storage, networking, and data transfer.
- Benchmarking: Comparing costs with industry averages or similar organizations can help validate cost estimates.
The TCO calculation typically involves a detailed breakdown:
- On-Premises TCO: This calculation involves summing up all direct and indirect costs related to the existing on-premises environment over a defined period, such as three or five years.
- Cloud TCO: This involves estimating the costs for cloud resources, migration expenses, and ongoing operational costs. It also considers potential cost savings from reduced hardware maintenance, power consumption, and IT staff overhead.
TCO = Hardware Costs + Software Costs + Data Center Costs + IT Staff Costs + Power Costs + Migration Costs + Cloud Resource Costs + Operational Costs – Potential Savings
A comparison of the on-premises TCO and the cloud TCO reveals the potential cost benefits of cloud migration. Example: A company with an on-premises infrastructure spends $1 million annually on hardware, software licenses, and IT staff. A CSA, using assessment tools and cost modeling, estimates that migrating to the cloud will cost $500,000 annually for cloud resources and operational expenses.
This initial comparison shows a potential annual cost saving of $500,000. However, the CSA must also factor in migration costs and any potential increase in operational complexity.
Cost Optimization Strategies
After the migration, the CSA focuses on ongoing cost optimization. This is a continuous process of identifying and implementing strategies to reduce cloud spending without compromising performance or security.The CSA employs several key cost optimization strategies:
- Right-Sizing Resources: This involves analyzing resource utilization and adjusting the size of virtual machines, storage, and other cloud resources to match actual needs. Over-provisioning can lead to unnecessary costs.
- Reserved Instances and Savings Plans: Cloud providers offer discounted pricing for reserved instances and savings plans, which commit to using specific resources for a defined period. The CSA can analyze workload patterns and recommend appropriate reservation strategies.
- Automated Scaling: Implementing automated scaling policies allows resources to scale up or down based on demand, optimizing resource utilization and cost.
- Storage Tiering: Utilizing different storage tiers based on data access frequency can significantly reduce storage costs. For example, infrequently accessed data can be moved to lower-cost storage tiers.
- Cost Monitoring and Reporting: Implementing robust cost monitoring and reporting tools provides visibility into cloud spending. The CSA can use these tools to identify cost anomalies and areas for optimization.
- Deleting Unused Resources: Regularly identifying and deleting unused resources, such as idle virtual machines or orphaned storage volumes, can prevent unnecessary charges.
- Optimizing Data Transfer: Data transfer costs can be significant. The CSA can optimize data transfer by using content delivery networks (CDNs) and minimizing data transfer between regions.
- Negotiating with Cloud Providers: As a cloud environment grows, the CSA can negotiate with cloud providers for better pricing and discounts.
Example: A company uses Amazon Web Services (AWS) and has several virtual machines (VMs) that are consistently underutilized. The CSA identifies these VMs and recommends right-sizing them to smaller instance types, resulting in a 20% reduction in compute costs. Furthermore, the CSA identifies that the company has large amounts of infrequently accessed data stored on expensive storage tiers. The CSA recommends moving this data to a lower-cost storage tier, resulting in a 30% reduction in storage costs.
These strategies demonstrate how the CSA can proactively manage cloud costs.
Communication and Stakeholder Management
The successful migration to the cloud hinges not only on technical proficiency but also on effective communication and stakeholder management. A Cloud Solution Architect (CSA) acts as a crucial bridge, translating complex technical details into understandable information for diverse audiences. This involves proactively managing expectations, providing timely updates, and fostering a collaborative environment throughout the migration lifecycle. Failing to do so can lead to misunderstandings, delays, and ultimately, project failure.
Communicating the Migration Plan and Progress
The CSA must clearly articulate the migration plan and ongoing progress to stakeholders, tailoring the communication style to each audience’s needs and level of technical understanding. This involves creating various communication channels and utilizing appropriate tools to ensure information dissemination.
- Defining Communication Channels: Establishing clear communication channels is essential. These channels may include regular project meetings, email updates, status reports, and dedicated communication platforms like Slack or Microsoft Teams. The CSA should define the frequency and purpose of each channel. For example, weekly project meetings could provide a comprehensive overview of progress, while email updates might be used for urgent notifications.
- Creating a Communication Matrix: A communication matrix identifies the key stakeholders, their information needs, the communication frequency, and the preferred communication method. This matrix ensures that the right information reaches the right people at the right time. For instance, executive stakeholders might require high-level summaries of progress and risk assessments, while technical teams need detailed technical specifications and implementation updates.
- Utilizing Visual Aids: Complex technical information can be simplified through the use of visual aids such as diagrams, charts, and dashboards. For example, a Gantt chart can visually represent the project timeline and milestones. A network diagram can illustrate the architecture of the target cloud environment. Dashboards can track key performance indicators (KPIs) such as migration progress, cost savings, and performance metrics.
- Translating Technical Jargon: The CSA must translate technical jargon into plain language that non-technical stakeholders can understand. This involves avoiding overly complex terminology and providing clear explanations of technical concepts. For example, instead of using terms like “virtual machine instances” or “load balancing,” the CSA might describe them as “servers in the cloud” or “distributing traffic to ensure website availability.”
- Providing Regular Status Updates: Regular status updates are critical for keeping stakeholders informed of the project’s progress, risks, and issues. These updates should include a summary of completed tasks, upcoming milestones, any identified risks, and proposed mitigation strategies. The frequency of these updates will depend on the project’s complexity and the stakeholders’ needs.
Best Practices for Stakeholder Management
Effective stakeholder management is a proactive process that involves understanding stakeholder needs, managing expectations, and building strong relationships. This approach helps to minimize conflicts, foster collaboration, and ensure project success.
- Identifying Stakeholders: The first step is to identify all stakeholders involved in the cloud migration project. This includes executives, IT managers, application owners, security teams, and end-users. The CSA should document each stakeholder’s role, interests, and communication preferences.
- Understanding Stakeholder Needs: The CSA should understand each stakeholder’s specific needs and concerns. This involves conducting interviews, surveys, and workshops to gather information about their expectations, priorities, and potential roadblocks.
- Managing Expectations: Realistic expectations should be set regarding the project timeline, budget, and potential challenges. The CSA should proactively communicate any risks or issues that may impact the project.
- Building Relationships: Establishing strong relationships with stakeholders is crucial. This involves being responsive to their concerns, providing timely updates, and fostering a collaborative environment. The CSA should act as a trusted advisor and advocate for the project.
- Addressing Concerns and Resolving Conflicts: Proactively addressing stakeholder concerns and resolving conflicts quickly is essential. The CSA should be prepared to mediate disputes and find solutions that meet the needs of all parties.
- Providing Training and Support: Offering training and support to stakeholders is crucial, particularly end-users. This ensures a smooth transition to the cloud environment. Training might cover new applications, processes, and security protocols. Support can include documentation, help desks, and dedicated support teams.
- Gathering Feedback: Regularly gathering feedback from stakeholders is essential for continuous improvement. The CSA should solicit feedback on the project’s progress, communication effectiveness, and any areas for improvement.
Sample Communication Plan Template
A communication plan provides a structured approach to keeping stakeholders informed throughout the cloud migration project. This plan should be tailored to the specific project and stakeholders involved.
Project: [Project Name]
Date: [Date]
| Stakeholder | Information Needs | Communication Frequency | Communication Method | Owner |
|---|---|---|---|---|
| Executive Sponsor | High-level project status, budget updates, risk assessments | Monthly | Executive Summary Report, Project Meetings | Cloud Solution Architect |
| IT Manager | Technical progress, infrastructure updates, resource allocation | Weekly | Status Reports, Project Meetings, Email Updates | Cloud Solution Architect |
| Application Owner | Application migration progress, potential impact on application performance | Weekly | Status Reports, Project Meetings, Email Updates | Cloud Solution Architect |
| Security Team | Security configurations, compliance updates, vulnerability assessments | Bi-weekly | Status Reports, Security Audits, Email Updates | Cloud Solution Architect, Security Architect |
| End-Users | Training on new applications, support resources, downtime notifications | As needed | Training Sessions, Email Notifications, Help Desk | Training Team, IT Support |
Key Communication Channels:
- Project Meetings: Weekly meetings to review progress, discuss issues, and make decisions.
- Status Reports: Weekly reports summarizing project progress, risks, and issues.
- Email Updates: Regular email updates providing information on key milestones and announcements.
- Dedicated Communication Platform (e.g., Slack): Used for real-time communication, questions, and quick updates.
Escalation Path:
- Issue: [Describe the issue.]
- Escalation Point: [Name and contact information.]
- Timeline for Response: [Specify the timeframe.]
Note: This is a sample communication plan template. The specific details should be tailored to the specific cloud migration project and its stakeholders.
Ultimate Conclusion
In conclusion, the cloud solution architect is the linchpin of a successful cloud migration, wielding expertise in planning, design, implementation, and optimization. Their role is paramount in ensuring a seamless transition, leveraging cloud technologies to achieve business objectives, enhance security, and optimize costs. The architect’s ability to manage stakeholders, mitigate risks, and drive innovation makes them indispensable in the evolving landscape of cloud computing.
By understanding and appreciating the multifaceted responsibilities of the cloud solution architect, organizations can significantly increase their chances of a successful cloud migration and realize the full potential of cloud technologies.
Question Bank
What are the key differences between a Cloud Solution Architect and a Cloud Engineer?
A Cloud Solution Architect focuses on high-level design, strategy, and stakeholder communication. A Cloud Engineer is responsible for the hands-on implementation, configuration, and maintenance of cloud infrastructure and services based on the architect’s designs.
How does a Cloud Solution Architect handle security concerns during migration?
The architect incorporates security best practices throughout the migration process, including designing secure network configurations, implementing identity and access management, data encryption, and compliance considerations. They also work with security teams to ensure the migrated environment meets the organization’s security policies.
What is the role of a Cloud Solution Architect in cost optimization?
The architect analyzes the current infrastructure, recommends cost-effective cloud services, and designs the architecture to minimize expenses. They also implement strategies such as right-sizing resources, utilizing reserved instances, and monitoring cloud spending.
How does the architect choose the right migration strategy?
The architect evaluates factors like application dependencies, business requirements, cost constraints, and time to determine the most suitable migration approach (rehost, replatform, refactor, etc.). They then align the migration strategy with the organization’s goals and resources.